Vulnerability testing in cyber security is the process of testing applications, networks, and other digital systems to find security vulnerabilities that can lead to cyberattacks. Even the most secure IT systems can have vulnerabilities that can expose them to hackers. Constantly changing threat landscape, AI tools, and lack of security measures all call for regular vulnerability testing.
One of the biggest cyberattacks occurred on the Group Health Cooperative of South-Central Wisconsin (GHC-SCW) recently. In January 2024, a hacker gang breached their network and stole the personal and medical information of over 500,000 individuals.
With roughly 2,200 attacks occurring every day, organizations need to prioritize vulnerability testing in cyber security to find entry points that cause these attacks. This blog will discuss this cybersecurity practice in detail, including its significance, tools, and processes.
What is Vulnerability Testing in Cyber Security?
Vulnerability testing, also called vulnerability assessment or scanning, is a cybersecurity practice of identifying, evaluating, and assessing vulnerabilities or flaws in applications, networks, and other digital assets.
Vulnerability testing in cyber security aims to identify security weaknesses that hackers can exploit for unauthorized access. Additionally, the test provides actionable insights to address the found vulnerabilities.
The process uses various tools and techniques to scan and analyze the target environment for potential vulnerabilities. This may include automated scanning tools, manual penetration testing, code reviews, etc.
The main objective of cybersecurity vulnerability testing is to identify security vulnerabilities like misconfigurations, insufficient access controls, insecure network protocols, lack of authentication and authorization, or known weaknesses in software components.
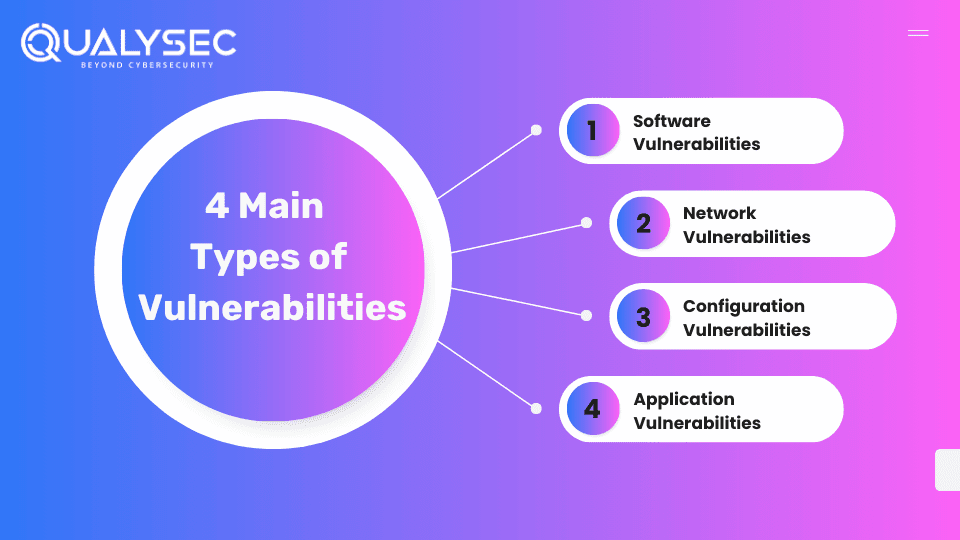
What are the 4 Main Types of Vulnerabilities in Cyber Security?
We need to understand the types of vulnerability testing in cyber security to protect applications and data from attacks. Regular vulnerability testing can help prevent these issues and protect the digital assets of the business.
- Software Vulnerabilities: These are flaws or weaknesses in a software system that can be exploited by attackers. These may include code errors, bugs, or outdated software that hasn’t been patched.
- Network Vulnerabilities: These are weaknesses in a network’s infrastructure, such as insecure network configurations, unprotected wireless connections, and outdated protocols. Attackers can exploit these vulnerabilities to launch DDoS attacks or steal data.
- Configuration Vulnerabilities: These occur when systems are improperly configured, making them more prone to attacks. Common configuration issues include weak permissions, default settings, and unnecessary services. Attackers might exploit these weaknesses to gain unauthorized access or control.
- Application Vulnerabilities: These are the flaws within software applications (both web and mobile) that can be exploited. There are various application vulnerabilities, such as SQL injection, cross-site scripting (XSS), and buffer overflows.
What is the Difference Between a PenTest & a Vulnerability Test?
Pen tests (or penetration tests) and vulnerability tests are often confused with the same service. While both these tests aim to find security vulnerabilities in digital systems, their approaches and techniques are different. Vulnerability assessment and penetration testing in cyber security are crucial for identifying weaknesses.
A pen test is an in-depth hands-on process by an ethical hacker that tries to identify and exploit vulnerabilities in a system. A vulnerability test is an automated scanning of applications and systems that looks for potential vulnerabilities.
Let’s check out the brief differences.
| Aspect | Pen Test | Vulnerability Test |
| Purpose | Simulates real-world attacks to identify exploitable vulnerabilities. | Scans systems to identify known vulnerabilities without exploiting them. |
| Depth of Testing | Deep and thorough, which involves manual testing and exploitation techniques. | Broad and automated. Focuses on identifying as many vulnerabilities as possible |
| Approach | Offensive – Simulating techniques of real attackers. | Defensive – More focus on identifying and reporting potential vulnerabilities. |
| Tools Used | Manual tools and techniques, along with automated tools | Mostly automated tools and scanners. |
| Skills Required | Requires skilled testers with high knowledge of hacking techniques. | Can be conducted by individuals with less hacking skills using automated tools. |
| Results | Detailed report on exploitable vulnerabilities, along with their impact level and remediation methods. | List of identified vulnerabilities, often with remediation advice. |
| Frequency | Usually conducted 1 – 2 times a year. | Performed more frequently, once every month or two. |
| Focus Areas | Includes both known and unknown vulnerabilities, including testing the resilience of the system against attacks. | Primarily focuses on known vulnerabilities and misconfigurations |
How Does Vulnerability Testing Work?
Vulnerability testing in cybersecurity involves using automated scanning tools to find security vulnerabilities in digital assets, such as applications, networks, cloud, APIs, etc.
The automated tool thoroughly analyses the target system and offers a detailed report after completion. This report includes the vulnerabilities found and actionable recommendations to address and mitigate these threats.
These tools have extensive databases with information about known vulnerabilities (such as misconfigurations and information disclosure). As a result, they can effectively pinpoint potential vulnerabilities across the system architecture, including networks, applications, containers, and data.
Vulnerability Testing Process
- Planning/Scoping: The first step of vulnerability testing is to outline the goals of the test clearly. This includes the objectives of the test, such as identifying vulnerabilities, assessing risk levels, and enhancing overall security.
- Asset Discovery: This step involves figuring out which applications or networks to test. This is easier said than done because many organizations lack visibility into their digital assets. However, the good news is automated scanning makes this asset discovery part easier.
- Vulnerability Scanning: Automated scanners or tools are used to scan the target environment and detect security vulnerabilities. While automated tools are quick and effective, they might miss a large number of vulnerabilities, which additionally require manual penetration testing.
- Reporting: After the scanning is complete, the tools generate a report that includes details of all vulnerabilities found. Using a severity-based ranking system, the tools categorize the vulnerabilities, helping developers to address critical vulnerabilities first.
- Remediation: Developers use the vulnerability testing report to gain knowledge about all the security weaknesses the system has. Then they start the remediation or patching process, starting from the critical to low ones. Regular testing can help developers create secure applications.
Want to perform vulnerability scanning and penetration testing for your applications? We have secured over 450 assets of over 110 different clients worldwide. Get comprehensive security testing for all your prized digital assets today! Talk to our security expert by clicking the link below.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Top 5 Methods for Vulnerability Testing in Cyber Security
There are different areas where you can conduct vulnerability testing in cybersecurity. However, there are 5 most crucial methods where organizations must conduct regular testing, such as:
1. Network Testing
A network-based vulnerability testing identifies vulnerabilities in network infrastructure, such as firewalls and other network components. These assessments typically involve using specialized software tools to scan the network for security weaknesses. These tools may use various methods to detect vulnerabilities, such as:
- port scanning
- vulnerability scanning
- password cracking
- network mapping
2. Application Testing
It is the process of examining security weaknesses in software applications ( both mobile & website vulnerability tests ). It typically involves testing the application for known vulnerabilities like misconfigurations and injection attacks. Application testing is primarily conducted by combining both automated scanning and manual penetration testing.
Common application vulnerabilities include:
- Broken Access Control
- Cryptographic Failures
- Security Misconfiguration
- Outdated Components
- Identification and Authentication Failures
- Insecure Logging and Monitoring
3. API Testing
It is performed to identify and address potential security risks in application programming interfaces (APIs). The process detects vulnerabilities in the API’s design, implementation, and deployment. The end goal is to ensure that the API is secure and resilient against cyberattacks.
4. Cloud Testing
A cloud-based vulnerability testing involves detecting vulnerabilities in cloud infrastructure and services, such as:
- Amazon Web Services (AWS)
- Microsoft Azure
- Google Cloud Platform (GCP)
Since cloud computing stores sensitive data and is used in most business operations, regular testing is required to protect the environment from malicious actors.
5. Database Testing
In database testing, the tools meticulously analyze databases for security weaknesses. They check for weak authentication mechanisms, misconfigurations, outdated software versions, and improper access controls. Additionally, they check whether proper encryption measures are implemented or not. Detected vulnerabilities are documented in a report that is promptly addressed to shield databases.
Ever wished to see a vulnerability test report? We provide you with one of our sample reports from one of our existing clients. Tap the link below and download!
Latest Penetration Testing Report

What are the Best Vulnerability Testing Tools?
Organizations use a wide variety of vulnerability testing tools to ensure they are getting full coverage. Over the years, there have been many different scanners, with different options and features. However, here is a list of the best ones:
1. Burp Suite
A comprehensive security testing tool for web applications, known for its powerful scanner and user-friendly interface. It includes various features, such as automated scanning, live traffic analysis, and a suite of tools for hands-on testing.
2. Netsparker
An automated web application security scanner that detects a wide range of vulnerabilities, such as SQL injection and XSS. It provides detailed reports with proof of exploitation and gets easily integrated into development workflows.
3. Metasploit
An open-source vulnerability testing framework that helps find and exploit vulnerabilities. It includes a huge library of exploits, payloads, and auxiliary modules, which allow security professionals to simulate real-world attacks.
4. MobSF
A mobile vulnerability testing tool that scans Android and iOS apps for security weaknesses. It performs static and dynamic analysis, providing insights into different app security issues, such as insecure data storage and code vulnerabilities.
5. Nessus
A popular vulnerability scanner to identify and fix network security issues. It covers a wide range of vulnerabilities, such as missing patches, configuration errors, and compliance issues. Additionally, it offers detailed remediation guidance.
6. Nmap
Nmap is a network scanning tool used for discovering hosts and services on a computer network. It provides various features like host discovery, port scanning, and service detection. As a result, it helps administrators understand their network’s security posture.
7. OWASP ZAP
An open-source web application security scanner designed for finding known and exploitable vulnerabilities. It includes automated scanners as well as a set of tools for manual testing, making it suitable for both beginners and professionals.
8. W3af
A web application attack and audit framework (w3af) that helps identify and exploit vulnerabilities. It offers a range of plugins for different types of security checks and can also be integrated with various other tools to enhance testing capabilities.
How To Choose the Best Vulnerability Testing Company?
With regulatory compliances like GDPR, PCI DSS, HIPAA, and ISO 27001 mandating security testing for applications that store user data, it is therefore crucial to choose the right vulnerability testing provider. Here are a few factors that you need to consider:
- Experience and Expertise: Look for companies with a proven track record and specialized knowledge in vulnerability testing.
- Comprehensive Services: Ensure they offer a full range of vulnerability testing services, including network, application, and mobile security.
- Certifications and Standards: Verify if they follow industry standards and hold relevant certifications, such as OSCP, CREST, etc.
- Client Reviews and Testimonials: Check for positive feedback and case studies from previous clients.
- Tools and Technologies: Assess the quality and range of tools they use for testing vulnerabilities.
- Customization: Ensure they can tailor their testing approach to fit your specific needs and environment.
- Reporting and Recommendations: Look for detailed reports with clear recommendations for fixing vulnerabilities.
- Communication and Support: Evaluate the quality of support they provide throughout the testing process.
- Cost and Value: Compare pricing models and ensure you get good value for the services offered.
Conclusion
Vulnerability testing in cyber security is a crucial part of identifying and mitigating security weaknesses in applications, networks, and other digital systems. As the threat landscape continuously evolves with sophisticated attack methods and advanced tools, regular vulnerability testing is now more important for organizations.
While selecting the right vulnerability testing provider, make sure you check their extensive services, reviews, and tools they use. Additionally, combining vulnerability scans with manual penetration testing offers a comprehensive security analysis – also keep this in mind while choosing a security testing provider.
FAQs
Q: Who performs vulnerability testing?
A: Anyone who knows how to use automated vulnerability scanners can perform vulnerability testing. However, one should have relevant certifications to conduct an in-depth analysis or manual penetration testing. These individuals are also called pen testers or ethical hackers.
Q: Which tool is used to perform a vulnerability test?
A: Various tools can be used to perform a vulnerability test, such as:
- Burp Suite
- Nessus
- OWASP ZAP
- MobSF
- Nmap
Q: What do you mean by vulnerability in cybersecurity?
A: In cybersecurity, a vulnerability refers to a flaw or weakness in an application, network, or system that could be exploited by a hacker for unauthorized access or data breaches. These vulnerabilities can arise from various sources like bugs, misconfigurations, outdated systems, insufficient security protocols, weak passwords, etc.























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments