© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions

With data breaches costing $4.45 million on average and around 343 million victims of cyberattacks in 2023, cybersecurity is more important than ever before. Businesses must ensure that their sensitive data is safe and protected from various cyberattacks. Within cybersecurity services, penetration testing is the top choice for securing organizations from data breaches and reputational damage. However, with so many penetration testing service providers available, how can you be sure you’re choosing the right one to fulfill your security testing requirements?
In this blog, we will provide the right direction that will help you choose the right penetration testing vendor. In addition to that a list of top penetration testing companies in the USA.
Penetration Testing or pen testing is a security measure where a cybersecurity expert uses real-world attacks to find vulnerabilities in a digital environment such as applications, networks, etc. The purpose of penetration testing is to identify security flaws or weak points in the defense system that hackers could take advantage of.
Some organizations may have a dedicated security team. However, a third-party cybersecurity firm should conduct penetration testing. This is because they have almost no knowledge of your internal security system and can mimic the techniques real hackers use. Additionally, their pentesting reports are also necessary to meet regulatory compliance.
By identifying vulnerabilities before hackers do, penetration testing enhances your overall security. Here are a few reasons to hire the right penetration testing service provider:
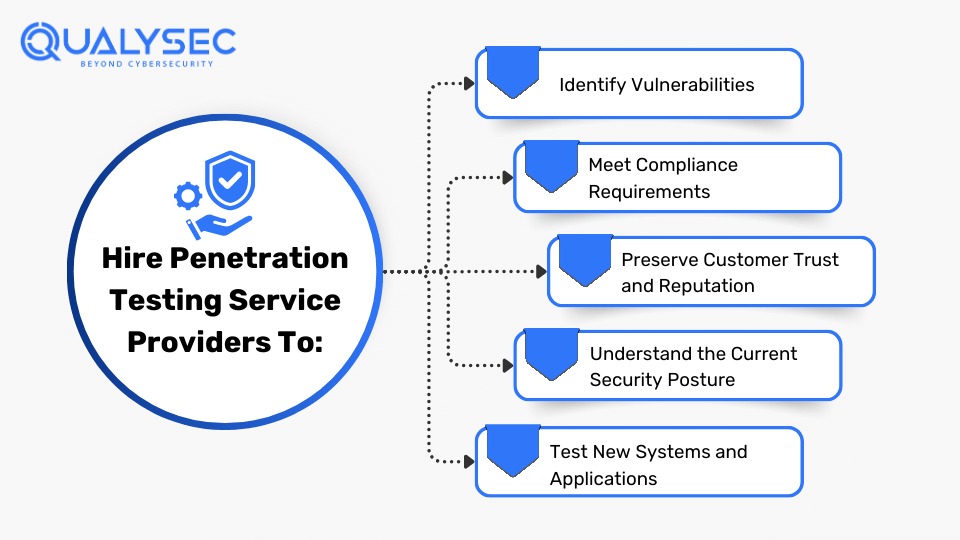
Unauthorized access and data breaches happen through vulnerabilities present in security measures. Penetration testing detects and fixes these vulnerabilities before cybercriminals do and saves you from great loss.
Many industry regulations and data protection laws like GDPR, SOC 2, HIPAA, and PCI DSS mandate regular security assessments. Penetration testing helps ensure these compliances, avoiding hefty fines and legal consequences.
Customers trust organizations with their data and a data breach can break this trust. However, regular penetration testing showcases your commitment to keeping the customer data safe and maintaining your reputation.
Penetration tests provide vital information about your organization’s current security posture. It helps you assess the ability of your security to defend against real-world cyber threats and understand where you need to improve.
Whenever your organization develops a new application or joins a new network, penetration testing can help ensure they are safe right from the start. As a result, it reduces the risk of launching insecure products.
Choosing the right penetration testing service provider is like choosing a skilled guardian to secure your castle. They help you stand strong against evolving cyber threats and provide peace of mind in an increasingly vulnerable digital landscape.
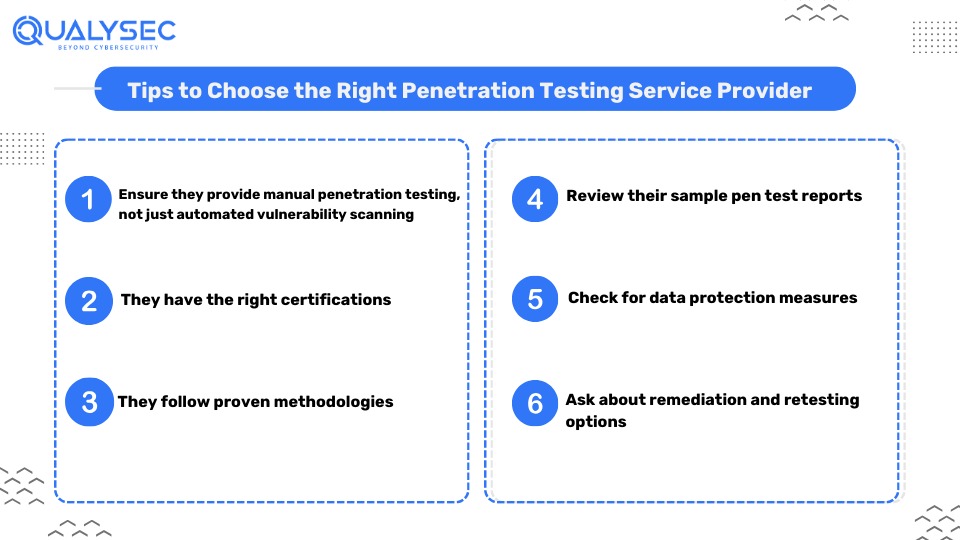
Some cybersecurity companies might provide automated vulnerability scanning under the disguise of penetration testing. You need to understand that there is a huge difference between automated vulnerability scanning and manual penetration testing.
Manual penetration testing requires a skilled tester to find and exploit vulnerabilities effectively. However, automated vulnerability scanning involves automated scanners that operate with a fixed pattern to identify potential weaknesses, providing mostly false narratives.
Manual testing is far superior to its automated counterpart. So, even if they offer automated vulnerability scanning, make sure the provider you choose also offers manual penetration testing.
There are multiple penetration testing certifications that cybersecurity professionals can possess. Some are well-respected in the industry as they focus on practical and hands-on assessments. At the same time, others do not truly measure a candidate’s ability to perform penetration tests and security audits effectively.
Here are some common certifications that ensure a penetration tester is skilled enough to conduct penetration tests.

When choosing the best penetration testing service provider, it is important to ensure they follow the best practices and proven methodologies. Some of the popular methodologies include:

Ask the penetration testing company to provide sample reports, letters of attestation, and other deliverables they might have. These documents are needed to see how good their findings are and how in-depth their testing is. Check for clear and actionable suggestions on fixing vulnerabilities. The quality of the report is very important, as it is the main thing you’ll get from your penetration testing service.
Wondering what a real penetration testing report looks like? Well, now you can with just a click!
Surprisingly many cybersecurity service providers do not have strong data protection measures in place and lack the necessary certifications to prove that they can handle data without any risk.
When choosing a penetration testing vendor, it’s important to make sure they follow strict data protection and security rules. Look for service providers with certifications like ISO 27001 or SOC 2, which ensure they safely handle sensitive data.
While all penetration testing reports mention remediation steps, you can ask the service provider whether they are willing to help with fixing the found vulnerabilities. Penetration testing service provider like Qualysec offers remediation help online or over consultation calls. This extra step can save time and fix the security gaps effectively.
In addition, make sure the service provider has the option of retesting after the initial pen test has been performed. Retesting validates if the remediation steps have worked and whether the vulnerabilities were fixed or not. Any penetration testing company who are willing to establish a long-term partnership will most likely include the option of retesting.
Here are the top five companies that provide the best penetration testing services in the USA.
Despite having headquarters in India, Qualysec Technologies leads in providing robust penetration testing services in the USA. They are one of the very few companies in the world that follow process-based penetration testing, instead of traditional pentesting. With their hybrid approach to vulnerability assessment and penetration testing (VAPT), they have completed over 350 assessments, with 90+ clients, in over 18 different countries. What’s more interesting is that their clients have not yet recorded a single data breach for the applications they have secured!
With experienced cybersecurity professionals and an affordable pricing plan, they are the best choice for a long-term penetration testing partner.
Looking to team up with the best penetration testing service provider? Click below to fix an appointment with Qualysec Technologies!
Fortinet is a leading cyber security service provider globally. It offers a wide range of products and services to protect organizations from cyber threats, including penetration testing. They have been recognized as a leader in Gartner’s Magic Quadrant for Network Firewalls and Unified Threat Management, among others. Established in 2000, the company has built a strong reputation for its innovative approach to cybersecurity.
Palo Alto Networks is a leading cybersecurity company that provides advanced security solutions. With cutting-edge technology and innovative approaches to cybersecurity, they have created a global presence for themselves. Their penetration testing services are designed to identify vulnerabilities in systems, networks, and applications, helping clients enhance their defenses. In addition to that, they also provide Attack Surface Assessment, Breach Readiness Review, Compromise Assessment, Cyber Risk Assessment, M&A Cyber Due Diligence, and more.
CrowdStrike is a top cybersecurity company dedicated to stopping breaches and protecting businesses and organizations worldwide. With their cloud-native platform, Falcon, they offer a comprehensive set of solutions to defend against cyber threats. Their innovative technology has garnered numerous awards and recognitions, including being named a leader in endpoint security by industry analysts. Their services include penetration testing, endpoint protection, threat intelligence, incident response, and managed services.
With a rich history spanning over three decades, Checkpoint has consistently delivered innovative cybersecurity products and services. Checkpoint’s comprehensive suite of services covers network security, cloud security, endpoint security, and mobile security, ensuring holistic protection for businesses of all sizes. Their penetration testing services offer thorough assessments to identify vulnerabilities and bolster defenses effectively.
Choosing the best penetration testing service provider can be a complex task. With a market full of company options, clients have limited guidance in selecting a penetration test provider that perfectly fits their needs. It is crucial to look beyond the surface and focus on factors such as certifications, methodologies, and comprehensive pen test reports while selecting a provider.
The best penetration testing company is the one that can tailor its approach to your unique requirements. This includes not just identifying vulnerabilities but also suggesting steps to fix them effectively. By following the tips mentioned above and the list of top penetration testing companies in the USA, you should be able to find the one that fits you the best.
A: Generally, a third-party cybersecurity company that focuses on penetration testing services is eligible to conduct pen tests. However, it is important to check their credentials before choosing the one for your business.
A: A penetration test or pen test is an authorized security attempt that involves simulating real attacks on applications or networks to evaluate its security defenses. Penetration testers use a variety of tools and manual testing techniques to find and exploit vulnerabilities present in a system.
A: Consider these factors while choosing the right penetration testing provider:





Plot No:687, Near Basudev Wood Road,
Saheed Nagar, Odisha, India, 751007
No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions


No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions