Mobile applications have become an integral part of our daily lives, but their widespread usage also makes them an attractive target for cybercriminals. Mobile application security testing plays a vital role in identifying vulnerabilities and ensuring the protection of sensitive user data. In this blog, we will explore the concept of mobile application security testing, its significance, key criteria, and the process of performing effective testing. Additionally, we will address common FAQs related to mobile app security testing.
What Is Mobile Application Security Testing?
Mobile application security testing refers to the process of assessing and evaluating the security posture of mobile applications. It involves identifying vulnerabilities, weaknesses, and security loopholes that could potentially be exploited by attackers. By conducting comprehensive security testing, organizations can proactively identify and mitigate security risks, thereby safeguarding user data and ensuring the overall integrity of the mobile app.
Why Is Mobile App Security Testing Important?
- Protecting User Data: Mobile apps often handle sensitive user information such as personal data, financial details, and login credentials. Mobile app security testing helps identify vulnerabilities that could lead to unauthorized access and data breaches, ensuring the protection of user data.
- Preventing Malicious Activities: Mobile apps can be susceptible to various security threats, including code injection, data leakage, insecure data storage, and insecure communication channels. By conducting security testing, organizations can identify and address these vulnerabilities, preventing malicious activities and unauthorized access to the app’s functionalities.
Criteria for Mobile Application Security Testing
When performing mobile application security testing, several key criteria should be considered to ensure comprehensive coverage:
- Authentication and Authorization: Testing the app’s authentication mechanisms, password policies, session management, and user access controls to ensure that only authorized users can access the app’s functionalities and data.
- Data Storage and Encryption: Assessing how sensitive data is stored, encrypted, and protected both in transit and at rest. This includes evaluating secure storage practices, encryption algorithms, and secure key management.
- Network Communication: Testing the security of network communication channels to ensure the use of secure protocols (such as HTTPS) and protection against potential eavesdropping, man-in-the-middle attacks, and data tampering.
- Input Validation and Output Encoding: Verifying that the app properly validates user input to prevent common security vulnerabilities like SQL injection, cross-site scripting (XSS), and command injection. Additionally, assessing how the app encodes and sanitizes output to prevent injection attacks and data leakage.
- Secure Session Management: Evaluating how the app manages user sessions, including session timeouts, secure session token generation, and protection against session hijacking or fixation attacks.
Understanding Mobile App Security Issues
Android vs iOS: Both Android and iOS platforms have their unique security considerations. Understanding these differences is crucial when conducting mobile app security testing
| Platform | Issue |
| Android | Android apps are more susceptible to security risks due to factors like fragmented device ecosystems, side-loading of apps, and app permissions. Security testing for Android should include evaluating app permissions, secure storage practices, and protection against common Android-specific vulnerabilities. |
| iOS | While iOS has a more controlled ecosystem, security testing should focus on areas like data encryption, secure inter-app communication, and secure app distribution through the App Store. Additionally, testing should consider potential jailbreaking or bypassing of device restrictions. |
Mobile Application Security Testing as a Solution
Mobile application security testing serves as a proactive approach to identifying vulnerabilities and mitigating security risks. By implementing regular testing practices, organizations can:
- Identify and address security vulnerabilities early in the development lifecycle.
- Enhance the overall security posture of the app, ensuring the protection of user data.
- Maintain compliance with regulatory standards and industry best practices.
- Establish trust and credibility with app users, resulting in increased user adoption and customer satisfaction.
Significance of Mobile Application Security Testing
- Protect User Data: Mobile apps often handle sensitive user data such as personal information, financial details, and login credentials. Conducting security testing helps identify vulnerabilities that could potentially expose this data to unauthorized individuals or hackers.
- Safeguard Business Reputation: A security breach can severely damage a company’s reputation, resulting in a loss of user trust and customer loyalty. Thorough security testing helps prevent such breaches and ensures the integrity and reliability of the mobile app.
- Compliance with Regulations: Depending on the industry and geographical location, mobile apps may need to comply with specific security and privacy regulations. Conducting security testing helps identify compliance gaps and ensures adherence to relevant standards and guidelines.
- Prevent Financial Losses: Mobile app security breaches can lead to significant financial losses, ranging from direct financial theft to legal liabilities and recovery costs. By identifying and fixing security vulnerabilities, organizations can mitigate the risk of financial losses.
How to Perform Mobile Application Security Testing
Performing effective mobile application security testing involves the following steps:
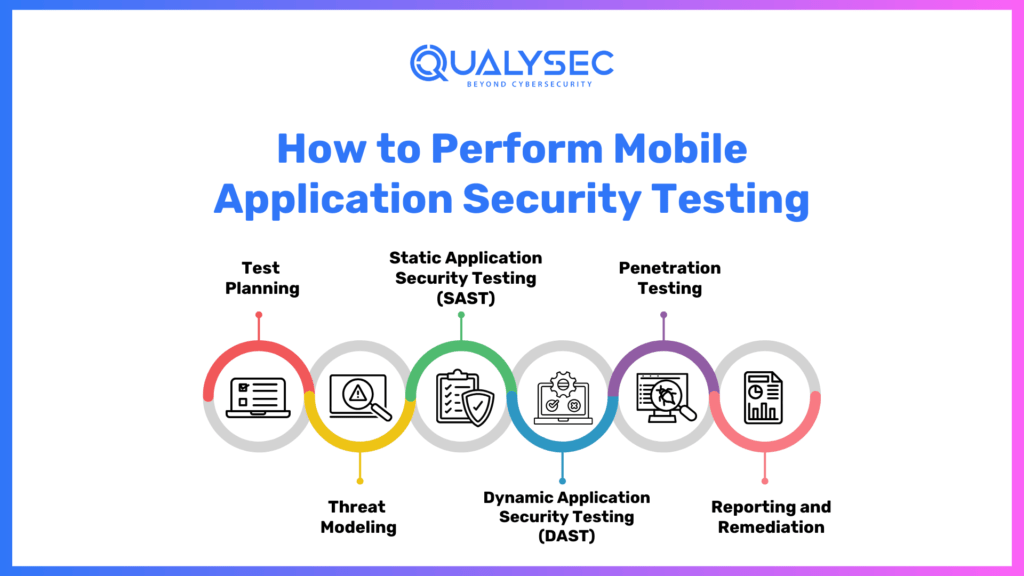
- Test Planning: Define the scope, objectives, and testing methodologies for the security assessment.
- Threat Modeling: Identify potential threats, attack vectors, and security risks specific to the mobile app.
- Static Application Security Testing (SAST): SAST involves analyzing the application’s source code or binary without executing it. Automated tools can help identify common vulnerabilities, coding errors, and insecure coding practices. SAST should be performed during the development phase and at regular intervals throughout the app’s lifecycle.
- Dynamic Application Security Testing (DAST): DAST involves testing the application in a runtime environment. It helps identify vulnerabilities related to user inputs, server-side processing, and network communications. DAST tools simulate real-world attacks and provide insights into potential security weaknesses.
- Penetration Testing: Conduct ethical hacking activities to actively exploit vulnerabilities and validate the effectiveness of existing security controls.
- Reporting and Remediation: Document the findings, including identified vulnerabilities, their impact, and recommendations for remediation. Implement necessary security measures to address the identified vulnerabilities.
Qualysec, The Pentesting Service Provider
Qualysec is a leading provider of Cybersecurity and compliance management solutions. Their platform allows companies to conduct continuous monitoring, vulnerability assessment, and compliance management across their entire IT infrastructure with the help of AI.
Qualysec follows a comprehensive methodology that involves a combination of manual and automated testing techniques and AI to ensure maximum coverage of vulnerabilities. They also provide detailed reports that include a prioritized list of vulnerabilities, along with recommendations for remediation.
They work closely with organizations to understand their unique needs.
Qualysec offers various services which include:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The methodologies offered by Qualysec for Mobile Application Security Testing are particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by opting for Qualysec as a reliable service provider, businesses can ensure the safety of their web applications.
Hence, choose Qualysec for a comprehensive and reliable vulnerability scanning report. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.-
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Conclusion
Mobile application security testing is crucial for safeguarding user data, preventing malicious activities, and maintaining the integrity of mobile apps. By adhering to key criteria, understanding platform-specific considerations, and following a comprehensive testing process, organizations can identify and mitigate security risks effectively. Prioritizing mobile app security testing ensures user trust, regulatory compliance, and a robust security posture, ultimately leading to the success and longevity of mobile applications.
There are several types of Pen testing Solutions one might need, and vulnerability scanners, including network scanners, host scanners, application scanners, cloud scanners, and wireless scanners. Each with its own set of benefits and use cases. Additionally, both internal and external vulnerability scanners are necessary. These cover all devices and systems that are accessible from within and outside of an organization’s network. We are always ready to help, talk to our Experts and fill out your requirements.
Cloud Security Service is in the boom after the intervention of AI in the world of Cybersecurity, Check out how Artificial intelligence (AI) is creating an impact on the cybersecurity industry, explore by checking out our article “Impacts of AI on Cybersecurity“.
Frequently Asked Questions
Q. What types of vulnerabilities can mobile application security testing uncover?
Ans. It can uncover various vulnerabilities, including insecure data storage, insecure communication, weak authentication mechanisms, insufficient authorization controls, input validation issues, and insecure coding practices.
Q. When should mobile application security testing be performed?
Ans. It should be performed throughout the development lifecycle, starting from the early stages of app design and continuing through development, testing, and post-deployment maintenance. Regular testing helps identify and address vulnerabilities as the app evolves.
Q. Can automated tools replace manual testing in mobile app security testing?
Ans. Automated tools are useful for static and dynamic analysis, but they should be complemented by manual testing. Manual testing allows testers to uncover complex vulnerabilities and assess the app’s overall security from a human perspective.
Q. How often should mobile app security testing be conducted?
Ans. Mobile app security testing should be conducted regularly, especially after significant updates, code changes, or the addition of new features. Additionally, regular testing should be performed to ensure ongoing security and address emerging threats.
Q. Is it possible to achieve 100% security through mobile application security testing?
Ans. While mobile application security testing is crucial for identifying vulnerabilities, it cannot guarantee 100% security. It is essential to implement appropriate security measures, regularly update the app, and stay informed about emerging threats to maintain a strong security posture.
































































































































































































































































































































































































































































































































0 Comments