Blockchain pentesting tests blockchain apps and networks to find security vulnerabilities that hackers can exploit. It helps secure data stored in the blocks from various cyber threats.
Technology is advancing every day, with new applications and platforms being produced to tackle the problems of existing systems. Industries like fintech, crypto, and healthcare use Blockchain technology to store data (especially transaction information).
According to Chainalysis, in 2022 over $3.8 billion of cryptocurrency was stolen from users. Although blockchain’s security is amongst the best, they are not unhackable. As a result, regular blockchain pen tests are required to prevent breaches.
In this blog, we will discuss blockchain pentesting in detail, what it is, how it is performed, and why companies using blockchain should make it a priority.
What is Blockchain?
Since it is practically a new technology that isn’t followed by most individuals on the planet, we will give a brief definition.
Blockchain is like a spreadsheet that stores transaction data in the form of blocks, which are linked with each other. When you make a transaction of, let’s say Bitcoins, a new block is created having the details of the transaction. This new block is linked to your previous ones, which then makes a “chain” of blocks.
Blockchain technology is a significant part of Web3 that is mostly a one-on-one interaction. As a result, this makes blockchain one of the most secure forms of technology to store sensitive data (still breachable though).
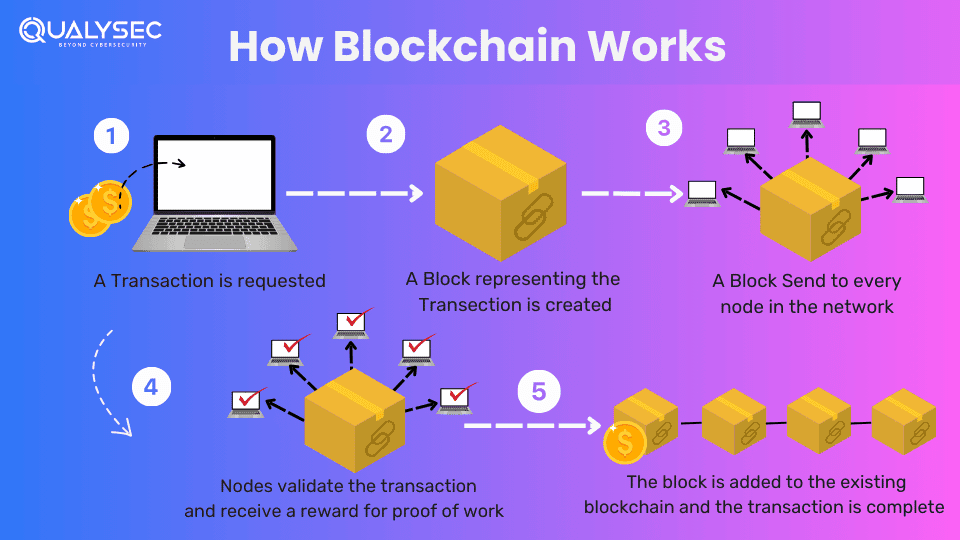
What is Blockchain Pentesting?
Blockchain pentesting or penetration testing is the process of simulating real attacks on blockchain apps to find security vulnerabilities. Even though blockchain is by far the most secure form of data storage, attackers are always looking for new ways to breach them, and are also getting success, in some cases.
The testers behave like real hackers and exploit the coding errors to break into the network. If they are successful in breaching, then it is a security flaw that needs to be fixed. As a result, this helps organizations to build a technology that is secure with connected devices.
Pen testers (a.k.a ethical hackers) try to find security loopholes in the network, contracts, and architecture of the apps. The main goal of blockchain penetration testing is to check whether their security measures are strong enough to block an attack.
Blockchain Security Vulnerabilities
So far, some major vulnerabilities consistently appear in blockchain protocols. These security issues affect project managers, developers, stakeholders, and the entire blockchain network, causing significant damage to its ecosystem.
Blockchain vulnerabilities can be divided into several parts, such as:
1. Smart Contract Vulnerabilities
- Reentrancy Attacks: These attacks allow untrusted external code to be executed within the contract.
- Integer Overflow and Underflow: These vulnerabilities can lead to incorrect calculations in the apps.
- Access Control Issues: Lead to unauthorized access to the apps.
- Logic Flaws: These help attackers change the behavior of the contracts in the blockchain.
2. Consensus Mechanism Weaknesses
- 51% Attack: This is when a single miner/entity controls more than 50% of the network’s mining hashrate, which can lead to double-spending and other malicious activities.
- Sybil Attack: A large number of fake identities take control of the network.
3. Network Vulnerabilities
- DDoS Attack: Distributed Denial of Service (DDoS) attacks disrupt the network by inserting huge amounts of traffic in the network.
- P2P Network Attacks: Manipulate peer-to-peer communication to disrupt the network.
4. Node-Level Vulnerabilities
- Outdated Software: Outdated or unpatched software can be exploited for various cyberattacks.
- Misconfiguration: Nodes that are not correctly configured can become entry points for attackers.
5. Cryptographic Vulnerabilities
- Weak Key Management: Without sufficient key management mechanisms, they can get exposed to the attackers.
- Insufficient Encryption: Lack of encryption allows attackers to access, read, and steal sensitive data.
6. API Vulnerabilities
- Insecure Endpoints: Insecure APIs might have weak endpoints that can grant unauthorized access to attackers.
- Improper Data Handling: The APIs have poor storage and transmission of data.
The Importance of Blockchain Pentesting
While blockchain companies boast highly about their application’s security, each vulnerability should be carefully considered. Blockchain penetration testing is probably the only way one can test each emerging vulnerability and fix it before an attacker exploits it.
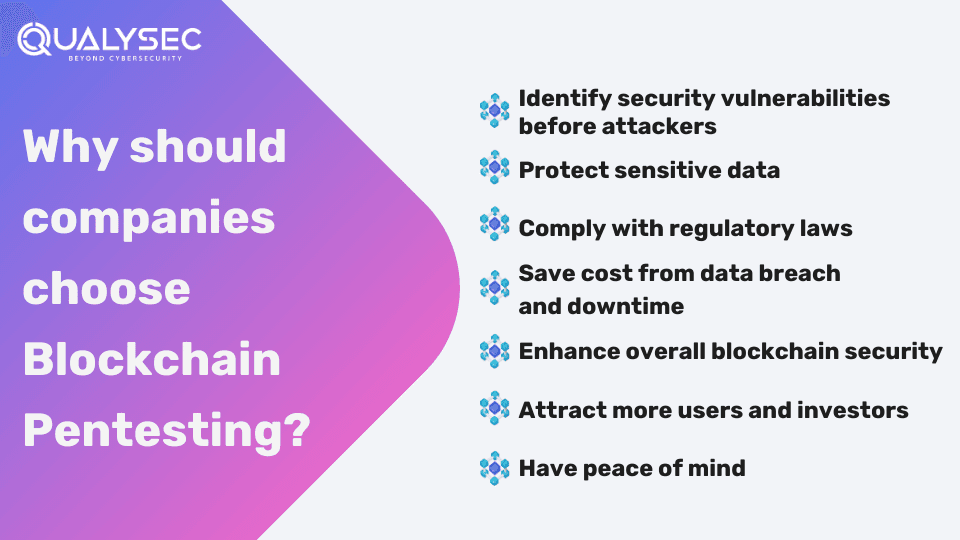
Blockchain penetration testing is important for the following reasons:
- Assured Security: It helps identify security weaknesses before attackers, making the system more secure.
- Data Protection: It secures sensitive data stored on the blockchain by preventing unauthorized access and data breaches.
- Build Trust: Regular pen testing shows your commitment to security. As a result, it builds trust with users, stakeholders, and partners.
- Regulatory Compliance: Penetration testing helps blockchain companies comply with mandatory data protection laws like GDPR, HIPAA, ISO 27001, etc.
- Reliable System: By identifying and fixing vulnerabilities, penetration testing minimizes the risk of downtime and service disruptions, making the system more reliable.
Benefits of Blockchain Pentesting
- Active Risk Management: By addressing vulnerabilities before attackers exploit them, companies can reduce the impact of security incidents.
- Better Security Posture: By continuously evaluating and strengthening blockchain security measures, pentesting helps companies stay ahead of emerging cyber threats.
- Enhanced Reputation: A secure blockchain system enhances the company’s reputation and credibility. As a result, you can attract more users and investors.
- Save Cost: By identifying vulnerabilities early, companies can save significant costs that may have been lost through data breaches, legal fees, and damage control.
- Peace of Mind: Knowing that your blockchain system is tested and secure gives you and your users peace of mind. Additionally, you can focus on innovation and business goals without worrying about security risks.
7 Key Areas of Focus in Blockchain Pentesting
There are a few areas where pen testers need to prioritize their focus in the blockchain, such as:
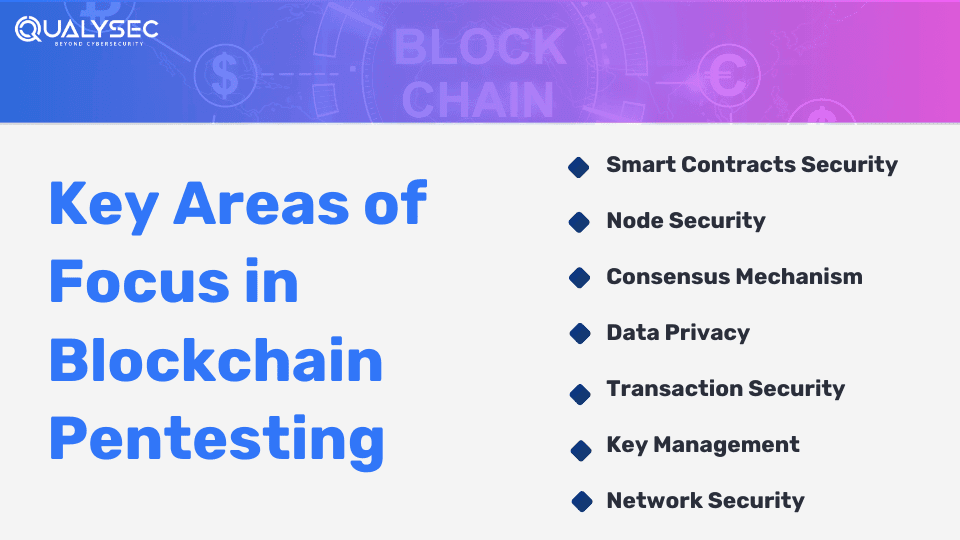
1. Smart Contracts Security
Check the code thoroughly for potential vulnerabilities such as reentancy or overflow issues. This ensures the contracts function properly and cannot be exploited. As a result, it enhances the system’s reliability.
2. Node Security
Configure nodes in the blockchain to withstand various types of attacks. This enhances the network’s resilience against cyber threats and offers a sense of security among the users.
3. Consensus Mechanism
Here the pen testers identify, and address vulnerabilities required to secure the network. This ensures safe and reliable transactions for all parties involved.
4. Data Privacy
Blockchain attacks mostly happen to steal data. Data privacy involves implementing robust security measures like encryption and access controls to protect data from unauthorized access. This assures users that their information is safe, which, in turn, builds loyalty and credibility.
5. Transaction Security
This involves employing effective measures such as cryptography and multi-signature transactions to secure financial transactions against fraud or illegal modifications. This helps users feel that their funds are secure and protected.
6. Key Management
Encryption keys are important to access and read data. Key management involves implementing strict protocols to protect these keys from cyber threats. Thus, securing user accounts and assets in applications.
7. Network Security
Once attackers get hold of the network, they can basically access everything in the blockchain. Network security involves deploying robust defenses such as firewalls and network access controls to shield the network from attackers for smooth and uninterrupted services.
Methodologies in Blockchain Pentesting
While different blockchain pentesting companies follow different steps, the core process remains the same. Here’s Qualysec’s blockchain penetration testing process:
- Information Gathering: We collect as much information about your Blockchain application as possible. Either you provide us with the necessary information, or we gather them from publicly available web pages.
- Planning/Scoping: We make a clear plan about how we are going to conduct the test. Additionally, we will specify which vulnerability we are going to target and what you can expect from the test.
- Automated Vulnerability Scanning: We use automated vulnerability scanners, such as XYZ Blockchain Tester and ABC CryptoScanner to find known vulnerabilities on the surface level.
- Manual Penetration Testing: Here we manually test the application in-depth to find all hidden vulnerabilities, along with those that are missed by the scanners.
- Reporting: We document all the vulnerabilities we found, along with their impact level and remediation measures. We then share this report with the development team.
- Remediation: If required, we help the development team locate and fix the vulnerabilities we found over consultation calls.
- Retest: We then retest the blockchain application to check whether all the security patches are implemented effectively or not. We also share a final report with you that includes the summary of the test.
- LoA/Security Certificate: The letter of attestation (LoA) is proof that you have successfully conducted pretesting. You can share this LoA with your shareholders or use it for compliance needs.
Do you want to secure your application from emerging security vulnerabilities? Conduct penetration testing with us and discover what flaws lie with your application. We follow a process-based pentesting method and have secured over 450 applications. Talk to our cybersecurity expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Best Practices for Effective Blockchain Pentesting
Blockchain penetration testing best practices identify vulnerabilities in nodes, smart contracts, consensus mechanisms, and networks. Here is a list of blockchain pentesting best practices:
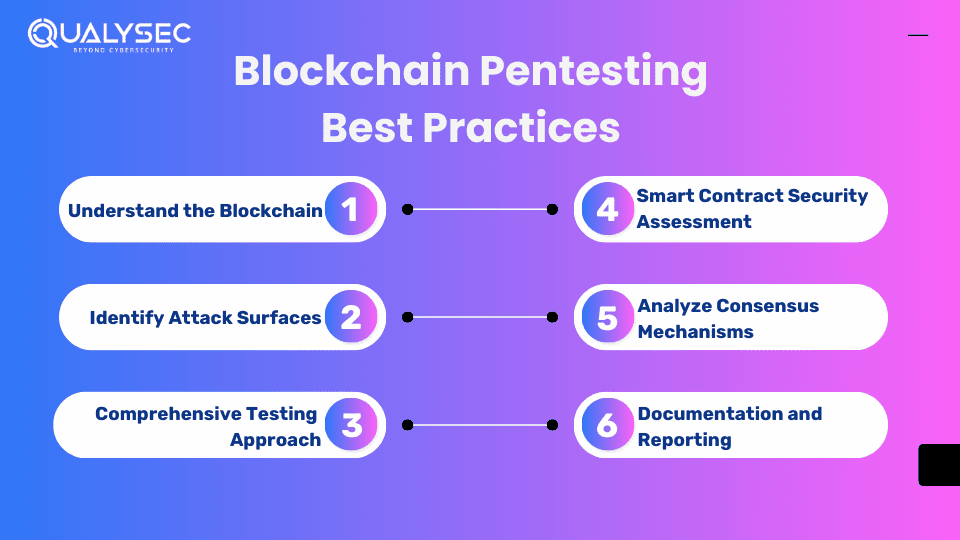
- Understand the Blockchain: Before starting pen testing, it is important to understand the fundamentals of blockchain technology. This includes its components, policies, and security measures.
- Identify Attack Surfaces: Identify the areas through which attackers can gain unauthorized access within the blockchain network, such as smart contracts, nodes, and communication channels.
- Comprehensive Testing Approach: Use a thorough testing approach that covers both the blockchain network and its components, including exchanges, wallets, and decentralized applications (DApps).
- Smart Contract Security Assessment: Analyze smart contracts for vulnerabilities such as overflow, reentrancy, and permission issues. Use both automated scanning tools and manual testing for in-depth analysis.
- Analyze Consensus Mechanisms: Check the resilience of the blockchain network’s consensus mechanism against various attacks, such as Sybil attacks or 51% attacks. Test how the network maintains consensus under different conditions.
- Documentation and Reporting: Document the summary and findings of the pen test in a detailed and easy-to-read manner. It should include the vulnerabilities found during the process, how they were exploited, and recommended remediation measures.
Would you like to see a real pen test report? Click the link below and download one in no time!
Latest Penetration Testing Report

Conclusion
Blockchain technology is going to be the future of transaction data storage. With blockchain applications increasing now and then, the demand to secure these applications is also increasing. Blockchain pentesting is the only process through which you can find the security vulnerabilities present in your application. What we have discussed in this blog is just the surface, as penetration testing and blockchain technology are more complex.
With the help of Qualysec Technologies, you can secure your blockchain applications effectively. Till now, there hasn’t been a single data breach from the 450 apps we have secured worldwide. Contact us and secure your business today!
FAQs
Q: How many times should I conduct blockchain pentesting?
A: For a secure application, you should perform blockchain pentesting at least 1 – 2 times a year. While more than that is welcome but less than this can be risky mong emerging cyber threats.
Q: What are the methods of blockchain pentesting?
A: Methods of blockchain pentesting include:
- Information Gathering
- Planning/Scoping
- Automated Vulnerability Scanning
- Manual Penetration Testing
- Reporting
- Remediation Support
- Retesting
- Letter of Attestation (LOA)/Security Certificate
Q: Can blockchain pentesting prevent all cyberattacks?
A: While blockchain penetration testing helps find security vulnerabilities, it can’t guarantee to prevent all cyberattacks. However, it can significantly reduce the likelihood of cyberattacks happening by mitigating potential entry points.






























































































































































































































































































































































































































































































































0 Comments