Developing an application is one of the most lucrative methods to expand your business in this digital age. However, there is also a huge risk of cyber threats, which are always evolving. Penetration testing for applications is a security testing method that helps businesses discover potential vulnerabilities present in their applications and fix them before a hacker exploits them.

In this blog, we will learn about penetration testing, why it should be done for applications, and the steps involved in it.
What is Penetration Testing for Applications
As the impact of cyberattacks increases, the need for cybersecurity also equally increases. Penetration testing for applications is a process of finding weak points through which cyberattacks can happen. Penetration testers mimic real-world cyberattacks on the application to check where the fault lies that hackers could exploit. In contrast to vulnerability scanning using automated tools, application penetration testing human skills and expertise to discover security flaws.
Manual penetration testing for applications not only detects vulnerabilities but also provides detailed guidelines to remediate them. In addition to that, it also provides no false results as opposed to automated scanning. Businesses can effectively know all the security flaws and fix them before any harm is caused to them.
Why Conduct Penetration Testing for Applications
As per a study, the annual average cost of cybercrimes was $8.4 trillion in 2022, which is predicted to hit more than $3 trillion in 2027. Penetration testing helps businesses find what flaws lie in their application’s security before any hacker does any malicious activity. Penetration testing is possibly the best way to test the effectiveness of your application’s security against various cyber threats. Let’s dive into the benefits of conducting penetration testing for applications.

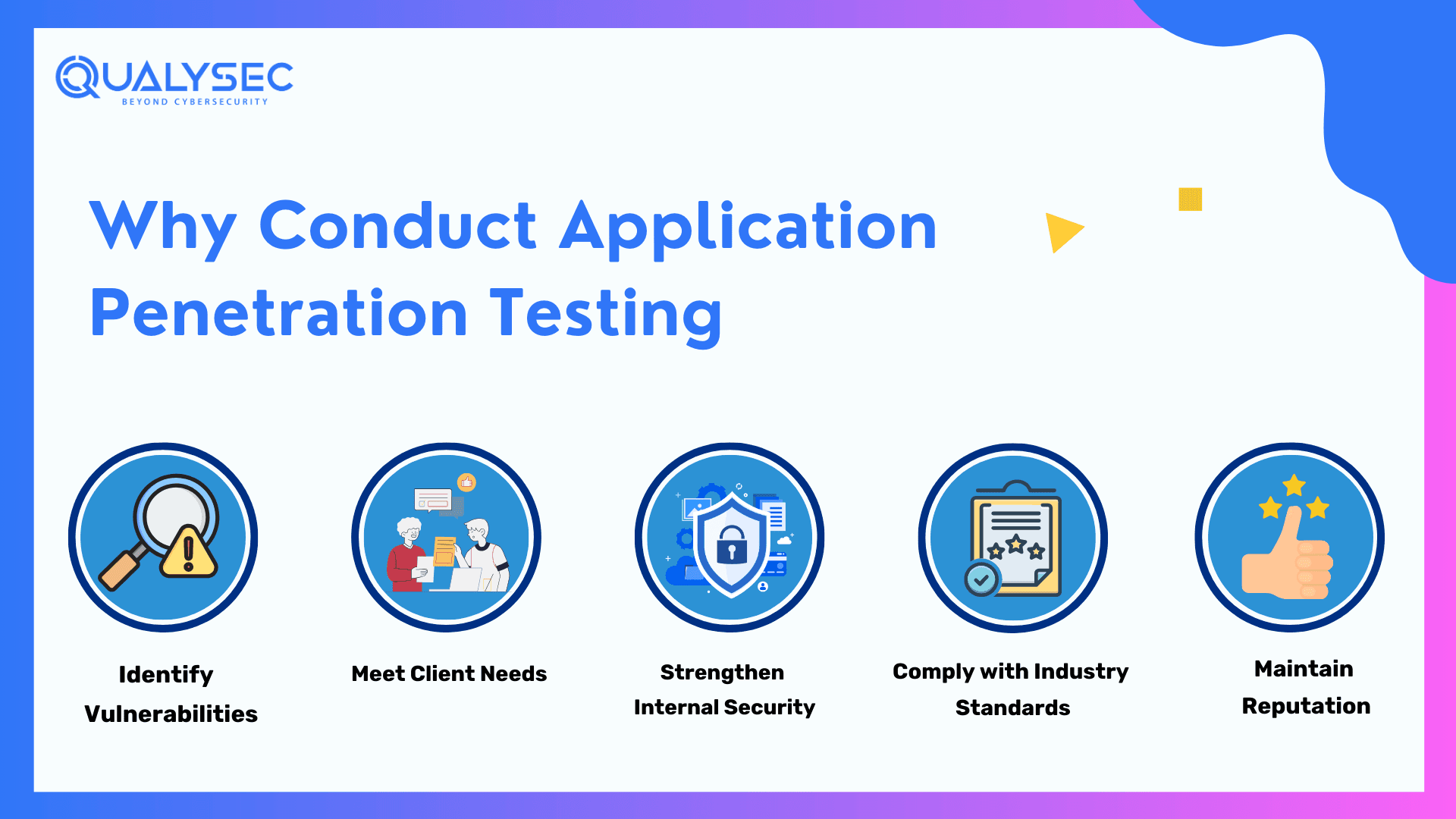
Identify Vulnerabilities
Organizations perform Application Penetration Testing to identify vulnerabilities before hackers or cyber attackers can exploit them. By simulating real-world attack scenarios, such as SQL injection or cross-site scripting, penetration testers discover weaknesses in the application’s defenses. As a result, organizations can fix those weaknesses quickly and reduce the risk of security breaches and data loss.
In addition to that, identifying vulnerabilities early helps organizations prioritize security measures and allocate their resources effectively to strengthen their application’s overall security posture.
Meeting Client Needs
For any business, meeting the client’s needs is something that needs to be fulfilled. Clients are more likely to choose a provider that prioritizes security and takes necessary steps to safeguard their interests. They expect their data and other digital assets to be secure while using your application, making security testing essential.
By conducting Penetration testing for applications, organizations can demonstrate their commitment to the security of client’s information. This not only builds trust but also ensures you share a long-lasting business relationship.
Internal Security
By identifying vulnerabilities early in the application, penetration testers help strengthen the overall security of the internal network. In other words, penetration testing for applications protects sensitive data, intellectual property, and other digital assets from various internal and external threats.
Additionally, it helps organizations detect gaps in their security measures so that they can implement necessary controls to mitigate them effectively. Ultimately, investing in penetration testing is essential to secure the organization’s resources and maintain business continuation swiftly.
Compliance with Industry Standards
Penetration testing is often mandatory by various industry standards, such as PCI DSS, HIPAA, or GDPR, to ensure proper security of sensitive data and personal information. Not meeting these can result in hefty fines, legal consequences, and reputational damage.
By conducting Application Penetration Testing, organizations can comply with these industry standards effectively. Moreover, by doing penetration tests regularly, organizations can align their security measures with the industry’s best practices and stay ahead of evolving regulatory requirements.
Maintain Reputation
A positive and strong reputation is very important in a competitive business environment and maintaining it requires good security measures. Penetration testing helps organizations sustain their reputation by identifying and fixing potential security risks before they can be exploited by hackers.
By investing in penetration testing for applications, organizations can show that they are committed to protecting their customer’s data and maintaining the trust of their stakeholders. As a result, it enhances brand reputation and credibility among partners, customers, and investors.
A good penetration testing company that offers cost-effective solutions for applications is hard to find. So, now that you have found one, waste no time contacting us.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Different Types of Penetration Testing for Applications
There are basically 3 types of penetration testings:
-
- White box
- Black box
- Grey box
Each penetration test differs in its approaches and the amount of information provided to the testers. However, the ultimate goal of each type of penetration test is to detect vulnerabilities present in the current security measures.
Black Box Penetration Testing
Also known as closed box or external penetration testing. In black box penetration testing for applications, the testers are given little to no information regarding the internal structure of the application. It requires a high level of programming knowledge and is probably the best approach to test the overall security posture of the application.
Black box pentesting can take up to six to seven weeks to complete, making it the longest type of penetration test. This, however, depends on the scope of the project.
White Box Penetration Testing
Also known as open box or internal penetration testing, white box penetration testing for applications is where the tester has full knowledge and access to the source and environment. The goal of white box pentesting is to conduct an in-depth security audit of the application and provide the tester with as much information as possible.
However, since the testers have all the working knowledge of the application, they cannot mimic how hackers would approach, those who don’t have any information. As a result, there is a high chance of many vulnerabilities being missed.
Grey Box Penetration Testing
In grey box penetration testing for applications, the tester has partial information and access to the application. The penetration tester has limited but more than just an outside understanding of the target application.
One of the main benefits of grey box penetration testing is that it provides a more focused and comprehensive assessment of the tested environment. It is typically done in the early stages of the development to know what type of vulnerability could be present and they can get converted into potential security risks.
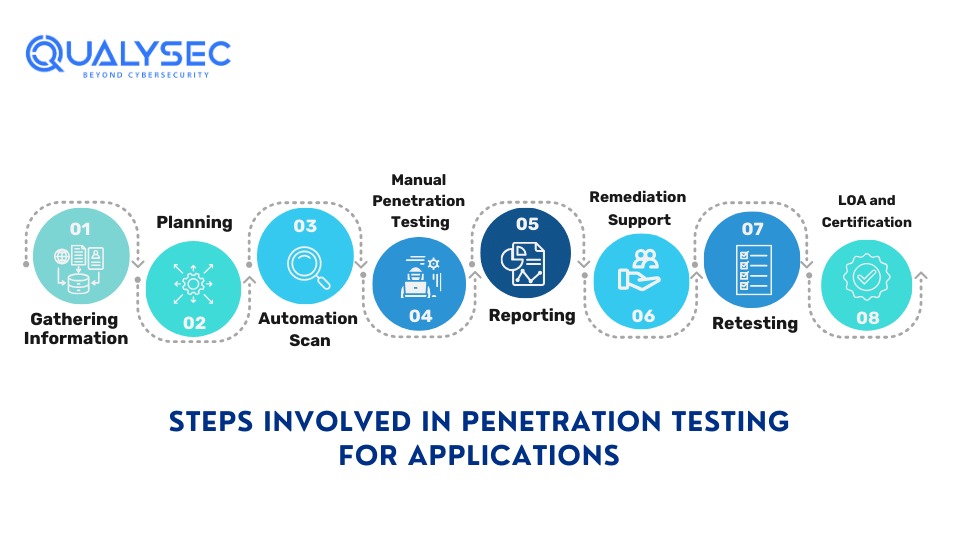
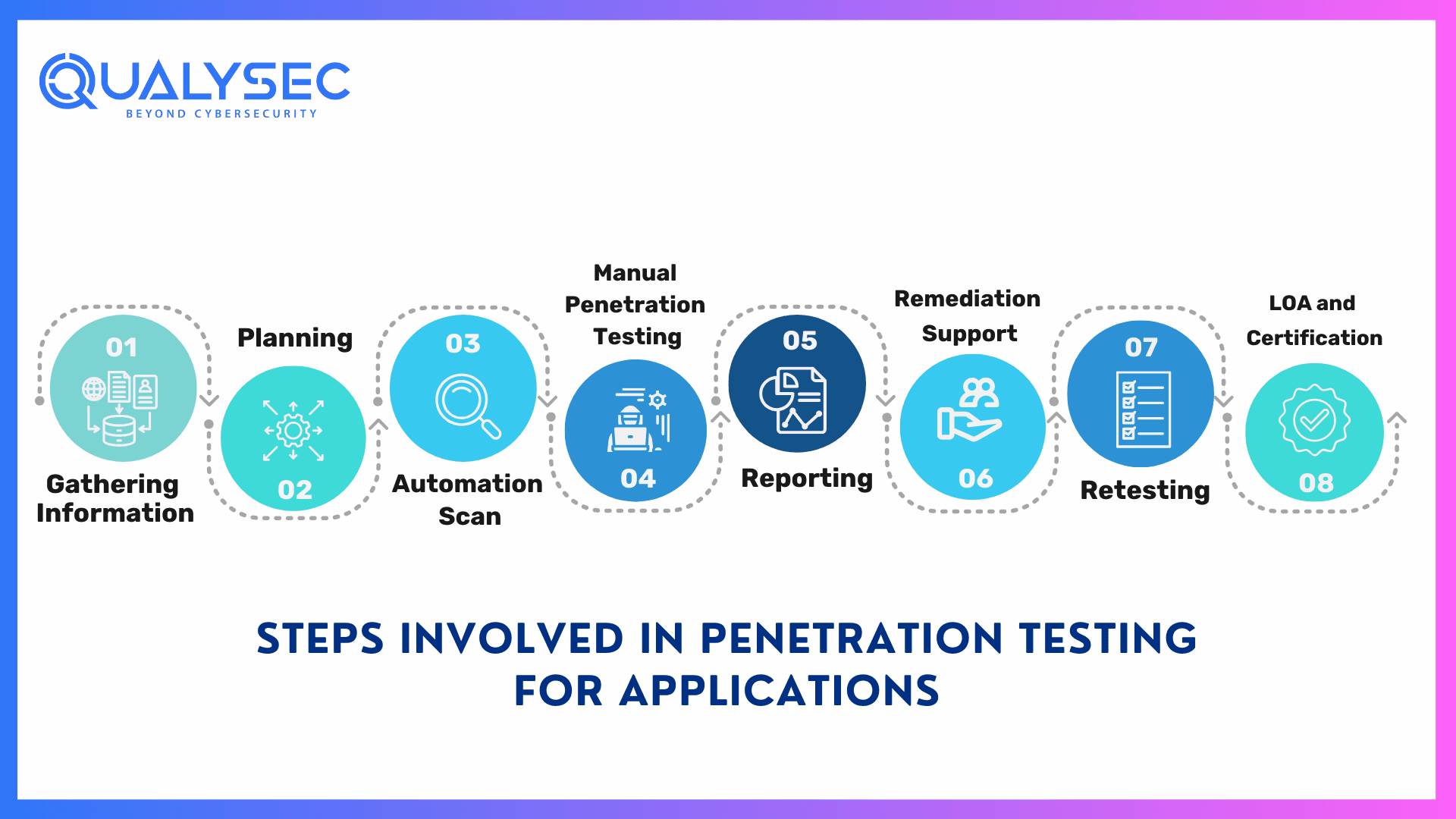
Steps Involved in Penetration Testing for Applications
There are typically eight Penetration testing steps involved in conducting application pen testing to identify and mitigate vulnerabilities. These methods assess the application security by simulating real-world cyberattacks and providing reports and certification for the organization’s benefit.
Gathering Information
The first step of penetration testing is to gather as much information as possible about the tested application. This is where the organization provides necessary information to the pen test team. Using the information, the pen testers start planning the different approaches and tools they are going to use.
Planning
The penetration testers set their goals by conducting an in-depth analysis of the application’s technicality and functionality. Through proper research and approach, the pen testers customize their approach to target specific vulnerabilities in the application.
A well-informed testing strategy is created that describes the scope, methodology, and criteria. Along with that, the organization may also provide a high-level checklist that would help the testers through the entire testing process.
Automation Scan
Next, vulnerability scans are done using automated penetration testing tools. These tools can detect potential vulnerabilities present at the surface level of the application. This technique offers a quick and thorough assessment and remediation of penetration testing for applications.
Manual Penetration Testing
Though automated scans can discover vulnerabilities present in the application, they cannot identify more complex and severe security flaws. Skilled cybersecurity professionals use their expertise to manually test the application for hidden vulnerabilities.
Reporting
After all the automated scans and manual testing are done, the penetration team creates a detailed report. This report will include a summary of the tests, vulnerabilities identified, and steps to fix them. The testing team then shares this report with the organization which will help their development team to enhance their security posture.
Want to see what a penetration testing report looks like? Well, now you can with just a click!
Latest Penetration Testing Report

Remediation Support
After getting the penetration testing report, the development team needs help in fixing the security flaws, then the testers can guide them through consultation calls. In fact, most of the time, they ask for direct engagement to fix the found vulnerabilities.
Retesting
After all the necessary remediation is complete, the penetration testing team retests the application to ensure all the mitigation techniques work. After all the retests are done, the testing team generates a final report for the organization.
LOA and Certification
Along with the pentesting report, the penetration testing company will also provide a Letter of Attestation (LOA) and certificate. This certificate is necessary to comply with the required industry standards. It will also provide proof that you have conducted penetration testing for the application and that you prioritize the security of your customer’s data and information.
Penetration testing tools for Applications
There is an array of Penetration testing tools available for application security testing, here is a list of the most popular and effective tools among them:
-
- Metasploit
- Wireshark
- Burp Suite
- Sqlmap
- Nmap
- Nessus
- W3af
- Nikto
Conclusion
With constantly evolving cyber threats, organizations should effectively identify and address vulnerabilities to protect their applications from unauthorized access and data breaches. Penetration testing for applications is the best method to achieve this, along with complying with the necessary industry standards.
Penetration testing helps organizations by enhancing internal security measures and meeting client requirements. By conducting regular penetration tests for their applications and other digital assets, organizations can mitigate security risks effectively and build trust with clients and stakeholders. If you want profitable and long-term success for your applications, regular penetration testing should be a priority.
FAQs
Q: What is application penetration testing?
A: Application penetration testing involves mimicking real cyberattacks to identify and mitigate vulnerabilities present in software applications. It can fix security flaws and improve the overall security posture of the application.
Q: Why is application penetration testing important?
A: Regular application penetration testing is important for multiple reasons such as:
-
- Identifying and fixing vulnerabilities in the application
- Enhancing the security posture of the application
- Meeting the client’s needs
- Complying with necessary industry standards
Q: How many types of penetration testing are there?
A: There are three types of penetration testing for applications:
-
- Black box
- White box
- Grey box
Q: What is the first step of penetration testing?
A: The first step of penetration testing for applications is to gather as much information about the application’s technicality as possible. Along with that, defining the scope and setting clear goals for the penetration tests.































































































































































































































































































































































































































































































































0 Comments