Application security testing tools are used to find vulnerabilities in software applications quickly and effectively. No matter how far technology evolves, there will be those who will try to hack into the applications. This is where application security testing /application penetration testing is done with the help of tools.
84% of cyber-attacks happen on the application layer. Since most organizations use and develop software applications, its security should be the biggest priority. And what better way to secure applications than by performing security testing?
With a wide range of application security testing tools available, it can be confusing for developers, testers, and IT leaders to know which tool addresses which issues. This blog is going to simplify this concern and also provide the different types and the right ways to choose a tool.
What is Application Security Testing?
Application security testing (AST) is the process of identifying security vulnerabilities in software applications to make them strong against cyber threats. It is a proven way that help applications be more resilient against cyberattacks.
Application Security Testing is done for:
Earlier, security testing was mostly manual, but with the advancement of technology, certain tools have emerged that have made the testing process quick. The best form of application security testing is penetration testing, which uses both manual skills and automated scanning tools.
2 Major Types of Application Security Testing:
- Static Application Security Testing (SAST): It involves examining the source code, bytecode, or binary code of an app for vulnerabilities, without executing the application.
- DAST (Dynamic Application Security Testing): It is a method of evaluating the security of an application in its running phase, without the knowledge of its internal code or structure, by simulating real-world attack scenarios.
What are Application Security Testing Tools?
Application security testing tools are specialized tools designed to identify security flaws and vulnerabilities in software applications. These tools ensure the data and resources present in the applications are protected from attackers.
Whether it’s web applications, mobile applications, or cloud applications, security testing tools’ main goal is to find conceivable flaws that could lead to unauthorized access, data breaches, and reputational damage.
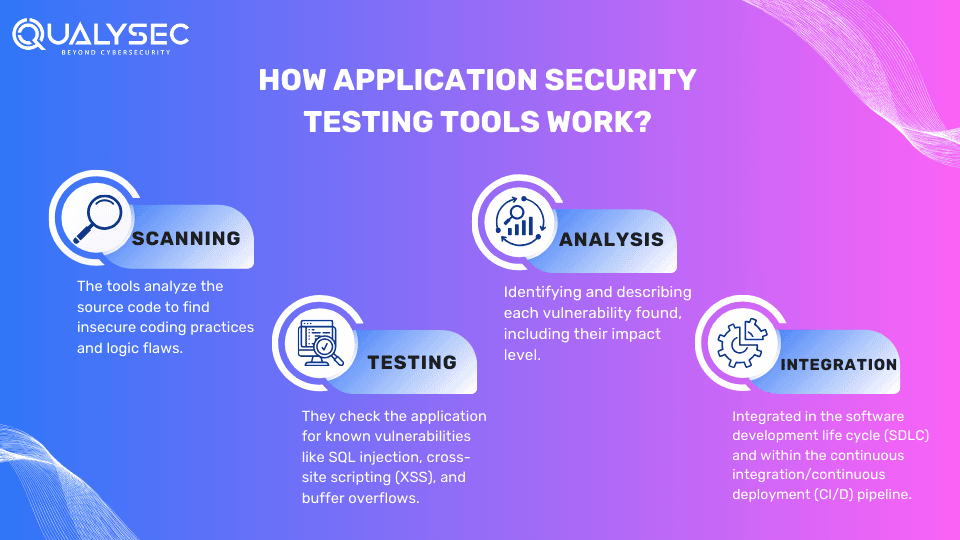
Importance of Security Testing Tools for Applications
AST tools are important assets in ensuring the working and reliability of software applications. Here are 7 benefits of using application security testing tools:
1. Detect Vulnerabilities Early
By integrating, AST tools identify security flaws early in the development process. Therefore, it allows developers to fix the issues before the application is released and becomes a major problem. This early detection of vulnerabilities reduces the cost and resources needed to address them as compared to fixing them after the application is deployed.
2. Prevent Cyber Attacks
By identifying potential threats such as SQL injection and cross-site scripting (XSS), AST tools help protect applications from being exploited. As a result, this helps prevent unauthorized access, data breaches, and other cyberattacks that could harm the applications and their users.
3. Comply with Industry Standards
Many industry standards and government policies have mandated security testing to protect user data. For example, GDPR, ISO 27001, SOC 2, HIPAA, PCI DSS, etc. Not complying with these standards can result in legal issues, fines, and penalties. AST tools help ensure applications meet these standards by identifying potential vulnerabilities. Additionally, meeting these standards also boosts the organization’s credibility and trustworthiness.
4. Enhance Application Security
By regularly testing and identifying vulnerabilities, AST tools help strengthen the overall security of applications. Applications with updated security build user trust, as they feel safe while storing their details and continue to use them securely.
5. Continuous Monitoring
Cybersecurity threats are always changing and getting more powerful. Application security testing tools provide ongoing security assessments even after an application is released to the market. This continuous monitoring helps identify and address new emerging threats and ensures the applications remain safe over time.
6. It is Cost-Effective
Finding and addressing security vulnerabilities through application security testing tools requires less investment. Additionally, AST tools prevent security breaches, which reduces the financial impact associated with data loss, downtime, and reputational damage.
7. Better Development Practices
Constantly using AST tools encourages developers to follow secure coding practices by integrating them into the software development lifecycle (SDLC). This integration creates a culture of security awareness, making security a priority in each stage of the development process.
Types of Application Security Testing Tools
Application security testing (AST) tools come in various types, each having a specific purpose. Here are the main types:
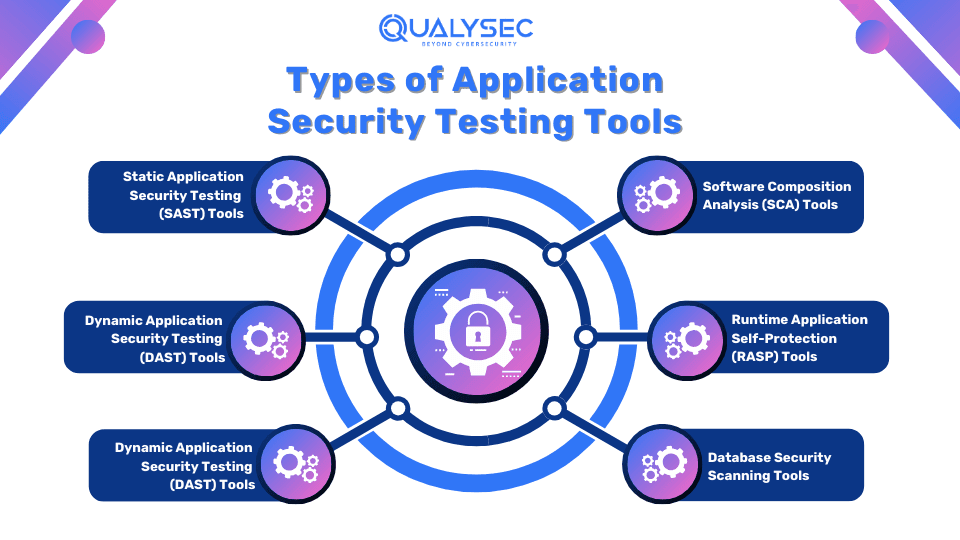
1. Static Application Security Testing (SAST) Tools
SAST tools analyze the application’s source code, bytecode, or binary code for vulnerabilities without executing the code. They examine the code’s structure, syntax, and logic to identify potential security issues such as insecure coding practices, hard-coded secrets, and compliance issues.
- Usage: Detects security issues early in the development process.
2. Dynamic Application Security Testing (DAST) Tools
DAST tools test the application while it is running to identify vulnerabilities that occur after the application is deployed. They simulate real-world attacks on a live application to detect security issues such as injection flaws, authentication and authorization problems, and insecure configurations. They do not require access to the source code.
- Usage: Simulated real-world attacks to find security vulnerabilities and runtime issues.
3. Interactive Application Security Testing (IAST) Tools
They combine features of both SAST and DAST tools by analyzing the application in real-time execution. IAST tools provide detailed insights into the application’s security posture by connecting runtime data with static analysis. As a result, this offers a comprehensive view of security issues in the application.
- Usage: Provides detailed insights into vulnerabilities by monitoring the application in real-world conditions.
4. Software Composition Analysis (SCA) Tools
SCA tools identify vulnerabilities in the open-source and third-party components used in the application. They scan for outdated or insecure libraries and frameworks and check for compliance. SCA tools provide alerts and recommendations for updates or patches.
- Usage: Ensures the third-party components integrated into the applications are secure.
5. Runtime Application Self-Protection (RASP) Tools
RASP tools monitor and protect software applications in real-time from within the application itself. They alter the execution flow of the application to prevent exploitation of the threats. As a result, it helps provide an immediate response to emerging threats and enhances the application’s resilience to attacks.
- Usage: Provides immediate responses to identified threats while the application is running.
6. Database Security Scanning Tools
Database security scanning tools identify vulnerabilities and misconfigurations in database configurations, schemas, and query logs. They check for security issues such as weak passwords, unpatched database software, and excessive privileges. Additionally, they also help comply with respective industry regulations.
- Usage: Ensures the databases are secure and compliant with industry standards.
Curious to see what a real application security testing report looks like? Tap the link below and download one for you!
Latest Penetration Testing Report

How to Choose The Best Security Testing Tools for Applications?
With so many varieties of application testing tools available with varied purposes, it can be hard to choose the one that’s right for you. However here are some tips that can help you choose the correct one:
- Effectiveness: Can the AST tool find everything you need? Can it crawl and scan JavaScript-heavy SPAs? Can it run verified scans? Can it be customized to safely integrate into each of your unique applications?
- Accuracy: If the developers or security engineers can’t trust the results they get from the tool, it would require them to manually check and validate them. This can be expensive and time-consuming. Therefore, check for features like proof-based scanning that prevent false positives.
- Easily Deployable: Often companies struggle to deploy the security testing tools after they acquire them. Look for tools that offer effective mitigation in a matter of days, if not hours.
- Visibility and Flexibility: Some tools cover a small section of the overall attack surface, such as SAST tools which are limited to specific languages and code constraints. Can the result of the tools be a part of your vulnerability management process? Can you use it as a security measure for the entire organization?
- Workflow Integration: AST tools need to integrate efficiently into the development workflows. Choose a tool that will fit into your existing processes and toolchains. Ensure that not only it can run tests in the SDLC but also at multiple points across it.
Top 10 Security Testing Tools for Applications
While you can find several application security testing tools, here are some widely used ones for software applications:

1. Burp Suite
Burp Suite is a comprehensive tool for web application security testing that scans for vulnerabilities like SQL injection and cross-site scripting (XSS). It provides detailed reports to help developers fix issues before deployment.
2. Netsparker
Netsparker is an automated web application security scanner that identifies vulnerabilities such as injection flaws and broken authentication. With its proof-based scanning technology, it offers easy-to-understand reports for quick remediation by developers.
3. OWASP ZAP
OWASP ZAP is an open-source tool that scans web apps for common security issues like XSS and CSRF. It is both an automated tool and an ideal solution for manual penetration testing.
4. W3af
W3af is a free web application attack and audit framework. It detects vulnerabilities like SQL injection and directory traversal. As a result, it helps developers secure their applications against common threats with its user-friendly interface.
5. Nmap
Nmap (Network Mapper) is a network scanning tool used to discover hosts and services on a network. It detects open ports and assesses network security, providing valuable information on network operating systems and firewalls.
6. Nikto
Nikto is a web server scanner that identifies potential security risks and misconfigurations such as multiple index files and HTTP server options. It checks for outdated software versions and performs version-specific scans.
7. Metasploit
Metasploit is a top penetration testing framework that helps identify and exploit vulnerabilities in network services. It offers a wide range of modules for testing and validating security controls, which helps in the assessment and improvement of application defenses.
8. Pacu
Pacu is a security testing tool for assessing the security of AWS environments. It automates various AWS attacks and security assessments, which helps organizations identify and mitigate risks associated with cloud application deployments.
9. Drozer
Drozer is a comprehensive security testing tool for Android applications. It identifies vulnerabilities such as insecure data storage and improper permissions. Hence, providing developers with insights to improve the security of their mobile apps.
10. MobSF
MobSF (Mobile Security Framework) is an open-source automated mobile application security testing tool. It analyzes Android and iOS apps for security issues like insecure data storage and vulnerable communication channels.
Get our simple, expert-made Web Security Checklist to spot risks and secure your app fast.

Conclusion
Integrating these application security testing tools into the development process will save you time and effort by identifying vulnerabilities early. However, before investing in security testing tools, you should have some knowledge of how they function, and which one is right for you. After you start using AST tools, they will produce a lot of results, and someone should be there to manage and act on them.
Additionally, the one big con of AST tools is that they work under a specified script. This means, they can detect known vulnerabilities easily and quickly but don’t work well will changing threats. Also, they may generate false positives. So, it is advised to combine AST tools with manual penetration testing for applications to get hidden vulnerabilities and comprehensive results.
Want to Perform both automated vulnerability scanning with AST tools and manual penetration testing in a packaged deal? Choose our team of experienced ethical hackers and secure your application today! Tap the link below and talk to our security expert!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQs
Q: Which tool is best for security testing?
A: Generally, software testing tools like Burp Suite, Metasploit, and MobSF are used to test applications for security vulnerabilities.
Q: What are VAPT tools?
A: VAPT tools are those that automatically detect vulnerabilities in a system and generate penetration testing reports. They help find security flaws that hackers could exploit for their gain, thus enhancing application security.
Q: What is application scanning?
A: Application scanning is a dynamic application security testing (DAST) tool that conducts in-depth security assessments of your custom-built web application. Hence, it allows a deeper security coverage of your assets.
Top Company Choose Qualysec for their Pentesting need































































































































































































































































































































































































































































































































0 Comments