Web Application Penetration Testing is a critical process used to evaluate the security of web applications and identify potential vulnerabilities that could be exploited by malicious actors. In today’s digital landscape, where cyber threats are constantly evolving, conducting regular penetration tests has become essential to safeguard sensitive data and ensure the integrity of web applications.
What is Web Application Penetration Testing?
Web Application Penetration Testing, often referred to as “pen testing,” is a controlled and methodical approach to assess the security of web applications. Skilled security professionals, known as penetration testers or ethical hackers, employ various tools and techniques to replicate real-world attack scenarios. By adopting the mindset of a potential attacker, they aim to identify security flaws and vulnerabilities that could lead to unauthorized access, data breaches, or service disruptions.
Types of Penetration Testing for Web Applications
- Black Box Testing: In this approach, the tester has no prior knowledge of the web application’s internal workings. They attempt to identify vulnerabilities solely through external interactions, mimicking an attacker with limited information. While this method provides a realistic assessment of external threats, it may not uncover all possible vulnerabilities within the application.
- White Box Testing: In contrast, white box testing grants the tester full knowledge of the application’s architecture and source code. This allows for a more comprehensive assessment, simulating an attacker with insider knowledge. White box testing is especially valuable for assessing internal security mechanisms and identifying hidden vulnerabilities.
- Grey Box Testing: A combination of black and white box testing, grey box testing provides the tester with partial information about the application. This reflects scenarios where some internal knowledge is available to attackers. Grey box testing strikes a balance between realism and depth of assessment, making it a practical approach in many situations.
Difference between Web Application Testing and Penetration Testing
Web Application Testing, often known as functional testing, is performed to check if an application meets its intended functionality. It focuses on user interface testing, performance, and usability. On the other hand, Penetration Testing specifically targets security vulnerabilities to assess the application’s resilience against attacks. While functional testing ensures the application works as intended, penetration testing goes beyond and aims to expose and fix security weaknesses.
| Aspect | Web Application Testing | Penetration Testing |
|---|---|---|
| Purpose | Check application functionality | Identify security vulnerabilities |
| Focus | User interface, performance, usability | Application security |
| Testing Objective | Validate intended functionality | Assess resilience against attacks |
| Scope | Functional aspects of the application | Security weaknesses |
| Methodology | Functional testing methodologies | Ethical hacking techniques |
| Outcome | Verification of intended behavior | Uncovering and fixing vulnerabilities |
| Testing Depth | Surface-level checks | In-depth security assessment |
| Impact on Security | Limited security assessment | Comprehensive security evaluation |
| Mitigation Focus | Usability and performance improvements | Security enhancements and fixes |
| Timing | Performed during development and after | Ongoing and periodic assessments |
| Goal | Ensure usability and functionality | Enhance application security |
What is Web Application Vulnerability Scanning vs. Penetration Testing?
Web Application Vulnerability Scanning involves using automated tools to scan an application for known security issues, such as outdated software versions or common misconfigurations. It provides a quick overview of potential vulnerabilities but lacks the depth and human intuition that penetration testing offers.
On the other hand, Penetration Testing employs a manual approach, allowing testers to uncover more complex and unknown vulnerabilities. The combination of automated scanning and human-driven testing provides a more comprehensive understanding of an application’s security posture.
Understanding Web Application and API Security
Web Application Security encompasses all measures taken to protect web applications from threats and attacks. As web applications increasingly rely on Application Programming Interfaces (APIs) to interact with external services and systems, API Security has become a crucial aspect of overall web application security.
APIs can be prone to vulnerabilities like insufficient authentication, authorization flaws, and inadequate input validation. Ensuring the security of APIs is essential to prevent data leaks and unauthorized access to sensitive information.
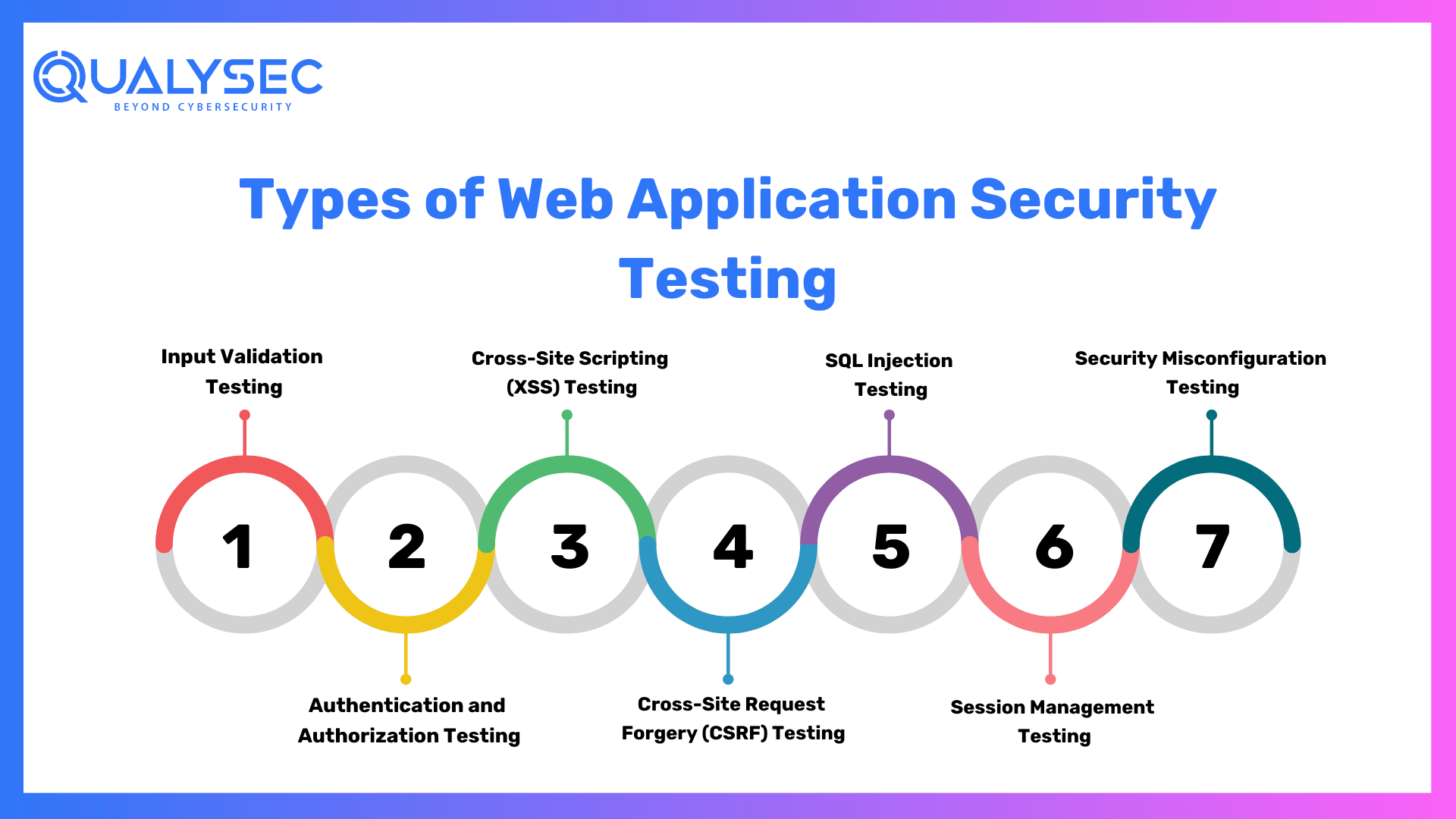
Types of Web Application Security Testing
- Input Validation Testing: This verifies if the application adequately validates user inputs, preventing potential code injection attacks such as SQL injection or Cross-Site Scripting (XSS).
- Authentication and Authorization Testing: Evaluate the effectiveness of the application’s login and access control mechanisms, ensuring that only authorized users can access specific resources and functionalities.
- Cross-Site Scripting (XSS) Testing: Identifies vulnerabilities that allow attackers to inject malicious scripts into web pages viewed by other users. XSS attacks can lead to the theft of user data and the hijacking of user sessions.
- Cross-Site Request Forgery (CSRF) Testing: Checks for weaknesses that enable attackers to trick users into executing unintended actions on the application. CSRF attacks can lead to actions performed on behalf of authenticated users without their consent.
- SQL Injection Testing: Detects vulnerabilities that could lead to unauthorized access to the application’s database. Proper input validation and parameterized queries are crucial to mitigate the risk of SQL injection attacks.
- Session Management Testing: Evaluates the security of user sessions and ensures that session-related information remains protected. Weak session management can lead to session hijacking and unauthorized access.
- Security Misconfiguration Testing: Identifies potential misconfigurations that could expose sensitive data or weaken the application’s security. Proper configuration of web servers, databases, and other components is essential to prevent unauthorized access.
Resources and Tools for Further Learning
1. Online Communities and Forums:
- OWASP (Open Web Application Security Project) Community
- Reddit’s r/AskNetsec for cybersecurity discussions and questions
2. Useful Web Application Security Tools:
When it comes to ensuring the security of web applications, there are several useful tools available that can assist in identifying vulnerabilities and enhancing overall protection. Here are some of the most popular and effective web application security tools:
- Burp Suite: Burp Suite is a leading web vulnerability scanner and penetration testing tool. It offers various modules for scanning, crawling, and manipulating web applications. The tool helps identify common vulnerabilities like SQL injection, Cross-Site Scripting (XSS), and more.
- OWASP ZAP (Zed Attack Proxy): ZAP is a free, open-source web application security scanner maintained by the Open Web Application Security Project (OWASP). It enables automated scanning for vulnerabilities and offers an interactive proxy to inspect and modify HTTP/HTTPS requests.
- Nikto: Nikto is a web server scanner designed to detect potential security issues and outdated software versions on web servers. It checks for common misconfigurations and security flaws that could be exploited by attackers.
- Netsparker: Netsparker is an automated web vulnerability scanner that scans for various vulnerabilities and issues. It offers a user-friendly interface and detailed reports for easy analysis.
- Metasploit: Metasploit is a penetration testing framework that allows security professionals to test the security of web applications and network infrastructures. It provides a wide range of tools for exploiting vulnerabilities and conducting penetration tests.
Qualysec: Your Trusted Partner for Web Application Penetration Testing
Qualysec, A Cybersecurity company founded in 2020 is a leading cybersecurity provider. Qulaysec is also known for its renowned cutting-edge technology and expertise in cybersecurity assessments. With a team of skilled professionals, Qulaysec offers a comprehensive range of services, including various vulnerability assessments and penetration testing.
What sets Qulaysec apart is its commitment to staying ahead of the curve in terms of emerging threats and advanced hacking techniques. They employ state-of-the-art tools and methodologies to ensure thorough and accurate assessments. Qulaysec’s team of experienced professionals brings a wealth of knowledge and a human touch to their engagements. This in turn helps foster collaboration and deliver actionable insights.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
Hence, choose Qualysec for comprehensive and reliablecloud penetration testing. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Conclusion
Web Application Penetration Testing is a vital component of any robust cybersecurity strategy. By identifying and addressing vulnerabilities proactively, organizations can safeguard their web applications and protect sensitive data from potential cyber threats. Regular testing and continuous improvement are key to maintaining a secure online presence.
Remember, as technology evolves, new threats will emerge, and staying informed about the latest security practices and tools is essential for effective Web Application Penetration Testing. If you’re interested in a career in cybersecurity, diving deeper into this field can open up exciting opportunities to make a positive impact in the digital world.
Qualysec has a successful track record of serving clients and providing web application penetration testing across a range of industries such as IT. Their expertise has helped clients identify and mitigate vulnerabilities, prevent data breaches, and improve their overall security posture.
When it comes to comprehensive cybersecurity audits, Qualysec is the organization to go with. Their cost of VAPT guide helps clients make informed decisions by understanding the various factors that affect the cost by clicking here.
FAQs on Web Application Penetration Testing
1. What is the main purpose of Web Application Penetration Testing?
Web Application Penetration Testing aims to identify security vulnerabilities and weaknesses in web applications to prevent potential cyberattacks and data breaches.
2. How is Web Application Penetration Testing different from regular functional testing?
Functional testing ensures the application works as intended, focusing on usability and performance. Penetration testing specifically targets security flaws to assess an application’s resilience against attacks.
3. Can automated tools replace manual penetration testing?
While automated tools like vulnerability scanners are useful for quick assessments, manual penetration testing provides a more comprehensive evaluation, uncovering complex and previously unknown vulnerabilities.
4. How often should organizations conduct Web Application Penetration Tests?
Penetration tests should be performed regularly, especially after significant changes to the application or infrastructure. Ideally, organizations should conduct tests at least annually or when major updates occur.
5. Are there any legal and ethical considerations when conducting penetration tests?
Yes, penetration testing should always be performed with proper authorization from the application owner. Ethical considerations include ensuring no harm is caused to the system and obtaining informed consent.
































































































































































































































































































































































































































































































































0 Comments