In today’s interconnected world, where technology pervades every aspect of our lives. The rise of cyber threats has become an alarming reality. As malicious actors continue to develop sophisticated methods to breach security defenses. It has become imperative to employ advanced technologies to counter these threats. One such technology that is revolutionizing the field of cybersecurity is Artificial intelligence (AI). In this blog, we will explore what AI is, how it benefits cybersecurity, and the challenges and risks associated with its implementation.
What is AI?
Artificial Intelligence in Cybersecurity refers to developing computer systems capable of performing tasks that typically require human intelligence. AI systems are designed to learn from experience, adapt to new data, and make decisions. These are done to take action to achieve specific goals. Machine learning, a subset of AI, enables systems to learn and improve from data. Implement data without explicit programming automatically. AI algorithms can analyze vast amounts of data, recognize patterns, and make predictions or take actions based on the insights derived.
AI in Cybersecurity
Artificial Intelligence in Cybersecurity has emerged as a game-changer in the field of cybersecurity, providing advanced capabilities to enhance threat detection, vulnerability management, and network security. By leveraging machine learning algorithms and predictive analysis, AI-powered systems can detect and mitigate cyber threats in real time, even before they can cause significant damage. These systems continuously analyze network traffic, user behavior, and system interactions, identifying anomalies and potential security risks. Additionally, AI automates vulnerability management processes, streamlining tasks such as vulnerability scanning, risk assessment, and patch management. This enables organizations to prioritize and address vulnerabilities efficiently, reducing the window of opportunity for attackers.
Benefits of Artificial Intelligence in Cybersecurity
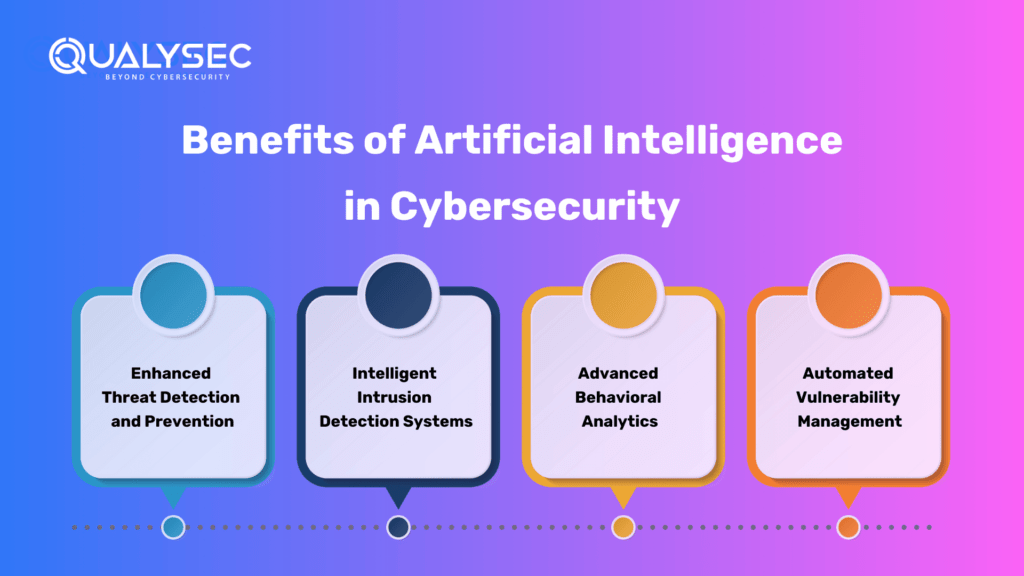
- Enhanced Threat Detection and Prevention: AI brings unparalleled capabilities to the threat detection and prevention field. Machine learning algorithms enable AI-powered systems to analyze vast amounts of data, identify patterns, and detect anomalies in real-time, even before they can cause considerable damage.
- Intelligent Intrusion Detection Systems: AI-powered IDS solutions can analyze network traffic, identify suspicious activities, and differentiate between normal and malicious behavior. By continuously learning and adapting to new attack vectors, AI-driven IDS systems significantly reduce false positives and provide more accurate threat alerts.
- Advanced Behavioral Analytics: AI-based behavioral analytics solutions analyze user behavior, establishing a baseline for each user. Deviations from this baseline can be flagged as potential security risks, enabling proactive measures to mitigate threats like insider breaches or compromised accounts.
- Automated Vulnerability Management: AI streamlines vulnerability management processes by automating tasks such as vulnerability scanning, risk assessment, and patch management. AI algorithms efficiently scan systems and applications for vulnerabilities, prioritize them based on severity, and recommend appropriate remediation actions.
Incorporating Artificial Intelligence in Cybersecurity into these areas of cybersecurity provides several advantages. It enables organizations to stay one step ahead of cyber threats, identify vulnerabilities before they are exploited, and respond quickly and effectively to incidents. AI’s ability to process vast amounts of data in real-time greatly enhances the efficiency and accuracy of security operations, freeing up human resources for more complex tasks.
Challenges and Risk: Artificial Intelligence in Cybersecurity
There are certain Challenges, especially due to Artificial Intelligence in cybersecurity, such as adversarial attacks, data privacy concerns, and limitations in AI technology that must be addressed. Adversaries can exploit AI techniques to develop more sophisticated attacks, and organizations must ensure transparent and ethical implementation of AI algorithms. Some of them are:
| Challenges and Risks | Description |
| Adversarial Attacks | Adversaries can use AI to develop more sophisticated attacks, leveraging the same AI technologies employed by defenders. This creates a constant cat-and-mouse game between attackers and cybersecurity professionals. |
| Data Privacy and Ethics | The use of AI in cybersecurity involves handling vast amounts of data, raising concerns about data privacy and ethical considerations. Organizations must ensure transparency, fairness, and protection of personal information when implementing AI solutions. |
| False Positives and Negatives | AI systems are fallible and may produce false positives or negatives. Relying solely on AI for decision-making without human oversight can lead to potential errors and missed security threats. |
The Not-so-Perfect AI
It’s important to acknowledge that Artificial Intelligence in cybersecurity is not perfect. It has certain limitations and challenges that need to be considered, including:
Lack of Contextual Understanding
AI systems may struggle to understand the contextual nuances that humans can readily grasp. They rely heavily on patterns and correlations within the data they are trained on, which can lead to misinterpretation of information. This limitation can sometimes result in inaccurate decisions or false positives/negatives.
Bias and Fairness
AI algorithms are only as unbiased as the data they are trained on. If the training data contains preferences or reflects societal prejudices, AI systems can perpetuate or amplify those biases, leading to unfair outcomes or discriminatory practices. It is crucial to ensure that the training data is diverse and representative of the intended user population to mitigate biases.
Interpretability and Explainability
Some AI algorithms, such as deep learning neural networks, are complex and often considered “black boxes” since they lack transparency in decision-making processes. It can be challenging to understand why an AI system arrived at a particular conclusion or prediction. This lack of interpretability and explainability can pose challenges in building trust and verifying the reliability of AI-driven cybersecurity systems.
Adversarial Attacks
Adversaries can exploit vulnerabilities in AI systems. This can be done by intentionally manipulating input data to deceive the algorithms or trigger incorrect responses. This field of research is known as adversarial attacks. This highlights the need for ongoing efforts to develop robust defenses against such attacks and to enhance the security of AI-driven cybersecurity solutions continually.
Overreliance and Human Oversight
While AI can automate and augment cybersecurity processes, complete reliance on AI without human oversight can be risky. Humans play a crucial role in understanding the context, interpreting complex situations, and making judgment calls that AI systems may not be capable of. It is essential to strike a balance between AI-driven automation and human expertise in cybersecurity operations.
Qualysec, The Perfect Solution
Qualysec is a leading provider of Cybersecurity and compliance management solutions. Their platform allows companies to conduct continuous monitoring, vulnerability assessment, and compliance management across their entire IT infrastructure with the help of AI.
Qualysec follows a comprehensive methodology that involves a combination of manual and automated testing techniques and AI to ensure maximum coverage of vulnerabilities. They also provide detailed reports that include a prioritized list of vulnerabilities, along with recommendations for remediation.
They work closely with organizations to understand their unique needs.
Qualysec offers various services, which include:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The methodologies offered by Qualysec are particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by opting for Qualysec as a reliable service provider, businesses can ensure the safety of their web applications.
Hence, choose Qualysec for a comprehensive and reliable vulnerability scanning report. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.-
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Conclusion
Artificial intelligence is reshaping the field of cybersecurity, empowering organizations to combat the growing sophistication of cyber threats. From enhanced threat detection to intelligent intrusion detection systems and automated vulnerability management. AI-driven solutions are revolutionizing the way we protect our digital assets. However, it is vital to address the challenges and risks associated with AI. Such as adversarial attacks, data privacy concerns, and the limitations of AI technology itself. By leveraging the benefits of AI while remaining vigilant and ensuring responsible and ethical implementation, we can harness its power to build a more secure digital future.
There are several types of Pen testing Solutions one might need, and vulnerability scanners, including network scanners, host scanners, application scanners, cloud scanners, and wireless scanners. Each with its own set of benefits and use cases. Additionally, both internal and external vulnerability scanners are necessary. These cover all devices and systems that are accessible from within and outside of an organization’s network. We are always ready to help, talk to our Experts and fill out your requirements.
Cloud Security Service is in the boom after the intervention of AI in the world of Cybersecurity, Check out the Top 8 Cloud Security Service Providers of 2025.
Frequently Asked Questions
Q: What is artificial intelligence (AI) in the context of cybersecurity?
A: Artificial intelligence refers to the development of computer systems that possess the ability to learn from data, adapt to new information, and make intelligent decisions or take actions to achieve specific goals in the realm of cybersecurity.
Q: How does AI benefit cybersecurity?
A: AI offers several benefits in cybersecurity, such as enhanced threat detection and prevention, intelligent intrusion detection systems, advanced behavioral analytics, automated vulnerability management, and improved network security and management. Hence, these capabilities help organizations proactively defend against cyber threats and respond more effectively to security incidents.
Q: What is predictive analysis in cybersecurity?
A: Predictive analysis in cybersecurity involves using AI algorithms to analyze historical data, identify patterns, and make predictions about potential cyber threats.
Q: Is AI technology flawless in cybersecurity?
A: No, AI technology is not flawless. While it offers significant advantages, there are challenges and limitations to consider. Hence, these include the lack of contextual understanding, potential biases in AI algorithms, interpretability and explainability issues, vulnerability to adversarial attacks, and the need for human oversight to ensure accurate and reliable decision-making.
Q: How does AI address the evolving nature of cyber threats?
A: AI excels in adapting to the evolving nature of cyber threats. Machine learning algorithms can continuously learn from new data, detect anomalies, and identify emerging attack patterns.































































































































































































































































































































































































































































































































0 Comments