© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions

With most business operations switching to cloud computing for scalability, storage, and convenience, its security has become a top priority. Infrastructure security in cloud computing is about protecting applications and data stored in the cloud from external and internal attacks.
As per the latest survey, 82% of data breaches involve cloud environments. Additionally, IBM revealed that an average data breach costs companies $4.35 million. This shows how cloud cyberattacks can significantly affect an organization.
This blog highlights the key areas of cloud infrastructure security, its techniques, and the tools for the best outcomes. If you are a cloud service provider or a cloud computing user, you should know what security threats are common in these environments and how to prevent them.
Cloud infrastructure security protects computing environments, applications, and confidential data from cyber threats by implementing authentication measures and limiting user’s access to the resources.
A comprehensive cloud infrastructure security includes a broad set of policies, technologies, techniques, and applications. It includes certain security measures that help detect and mitigate vulnerabilities that may result in unauthorized access and data breaches. For example, data encryption, endpoint security, identity and access management (IAM), penetration testing, and more.
Infrastructure Security in cloud computing Helps With:
Overall, the main goal of cloud infrastructure security is to protect this virtual environment from a range of potential security threats by implementing the necessary measures. With more than 92% of organizations using cloud computing globally, it is important to prioritize cloud security to continue business operations smoothly.
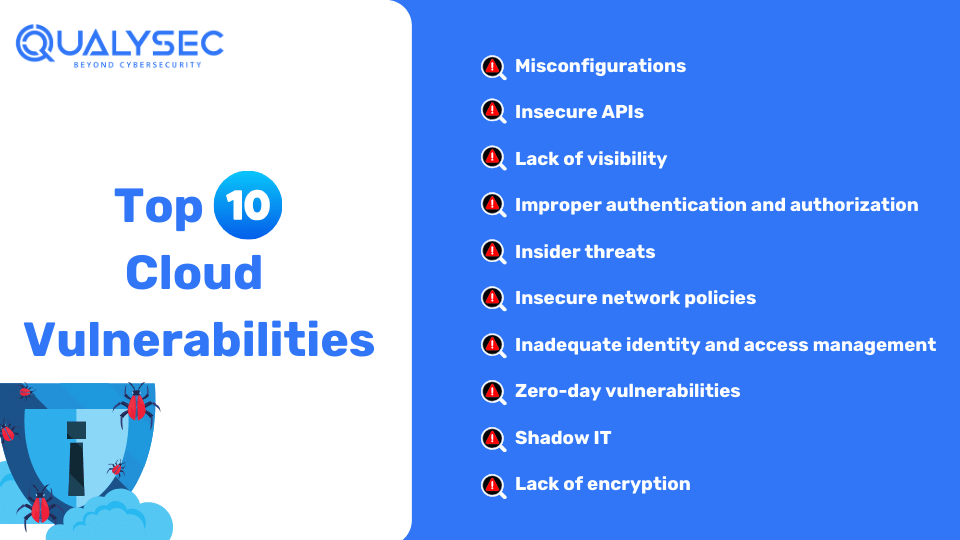
To secure a cloud environment, it is necessary to control who can access the data and applications. The 5 main components of infrastructure security in cloud computing are:
Identity and access management (IAM) is a security measure that involves who can access cloud resources and what activities they can perform. IAM systems can implement security policies, manage user identities, track all logins, and do more operations.
IAM mitigates insider threats by implementing least privilege access and segregating duties. Additionally, it can also help detect unusual behavior and provide early warning signs of potential security breaches.
Network security in the cloud means protecting the confidentiality and availability of data as it moves across the network. As data reaches the cloud by traveling over the internet, network security becomes more critical in a cloud environment.
Security measures for networks include firewalls and virtual private networks (VPN), among others. However, all cloud providers offer a virtual private cloud (VPC) feature for organizations that allows them to run a private and secure network within their cloud data center.
Data security in the cloud involves protecting data at rest, in transit, and in use. It includes various measures such as encryption, tokenization, secure key management, and data loss prevention (DLP). Additional data security measures include adding access controls and secure configuration to cloud databases and cloud storage buckets.
Moreover, data protection laws also play a critical role in protecting cloud data. Industry regulations like GDPR, ISO 27001, HIPAA, etc. mandate organizations to have proper security measures to protect user data in the cloud.
Endpoint security focuses on securing user devices or endpoints that are used to access the cloud, such as smartphones, laptops, and tablets. With new working policies like remote work and Bring Your Own Device (BYOD), endpoint security has become a vital aspect of cloud infrastructure security.
Organizations must ensure that users access their cloud resources with secured devices. Endpoint security measures include firewalls, antivirus software, and device management solutions. Additionally, it may include measures like user training and awareness to avoid potential security threats.
Cloud application security is probably the most critical part of cloud infrastructure security. It involves securing applications in the cloud against various security threats like cross-site scripting (XSS), Cross-Site Request Forgery (CSRF), and injection attacks.
Cloud applications can be secured through various ways such as secure coding practices, vulnerability scanning, and penetration testing. Additionally, measures like web application firewalls (WAF) and runtime application self-protection (RASP) can provide added layers of security.
Cloud infrastructure security tools protect sensitive data, detect and respond to security threats, and ensure regulatory compliance in cloud-based systems. Here are the top tools for cloud infrastructure security:

AWS Security Hub centralizes visibility and offers actionable insights in security alerts. Additionally, it helps organizations strengthen their cloud posture with advanced threat intelligence, automated compliance checks, and seamless integration with other security tools.
Microsoft Azure Security Center is a cloud-native security management tool that provides continuous security monitoring, threat detection, and actionable recommendations to improve Azure environments. It uses machine learning and behavioral analytics to help identify and respond to potential threats and ensure compliance with industry standards.
Google Cloud Security Command Center offers centralized access to cloud security solutions. As a result, it allows the organization to have complete visibility and control over the resources and services on Google Cloud Platform (GCP). Its wide range of capabilities includes advanced threat detection technologies, real-time insights, and security analytics.
Cisco Cloudlock is an advanced cloud security platform that operates natively on the cloud. It offers comprehensive data protection, access controls, and threat intelligence. It offers security measures to various cloud applications, especially for Software-as-a-Service (SaaS).
IBM Cloud Pak for Security is an integrated security platform for cloud environments that offers threat intelligence, security analytics, and automation functionalities. As a result, it helps organizations to effectively detect, investigate, and respond to security threats in both cloud and hybrid environments. Additionally, it used advanced analytics and AI-driven insights for better cloud security.
To protect data and applications in the cloud environment, organizations can implement these foundational (yet advanced) techniques:

The goal of encryption is to make data unreadable for those who access it. Once data is encrypted, only authorized users i.e. individuals with decryption keys will be able to read it. Since encrypted data is useless, it cannot be stolen or used to carry out other attacks.
You can encrypt data while it is stored (at rest) and also when it is transferred from one location to another (in transit). This technique is critical when transferring data, sharing information, or securing communication between different processes.
We have already established this above as a key component of infrastructure security in cloud computing. The purpose of IAM tools is to authorize user identity and deny access to unauthorized parties. IAM checks the user’s identity and determines whether the user is allowed to access the cloud resources or not.
Since IAM protocols are not based on the device or location used while attempting to log in, they are highly useful in keeping cloud infrastructure secure.
Key capabilities of IAM tools:
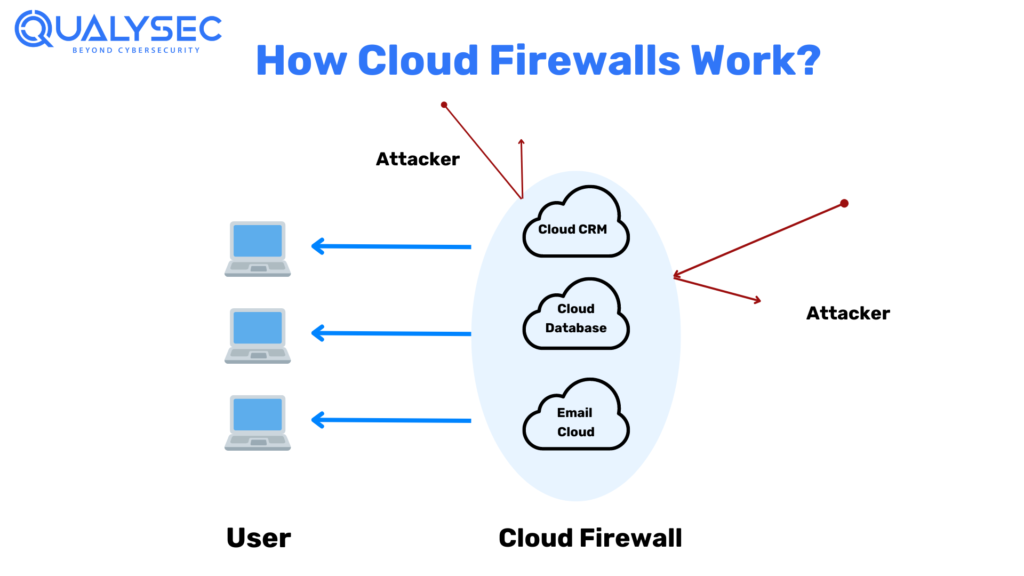
Just like traditional firewalls, cloud firewalls are a shield around the cloud infrastructure that filters malicious traffic. Additionally, it helps prevent cyberattacks like DDoS attacks, vulnerability exploitation, and malicious bot activity. There are basically 2 types of cloud firewalls:
A virtual private cloud (VPC) provides a private cloud environment for a public cloud domain. Additionally, a VPC creates highly configurable sections of a public cloud. This means you can access VPC resources on demand and scale up as per your needs.
To secure your VPC, you can use certain security groups. Each security group acts as a virtual firewall that controls the traffic flow in and out of the cloud. However, these groups can be implemented at the instance level and not at the subnet level.
Cloud penetration testing is a technique to find vulnerabilities present in a cloud environment by simulating real attacks. Organizations can appoint third-party penetration testing companies to conduct the testing on their cloud applications.
Penetration testers (a.k.a ethical hackers) use a process to check each part of the application to find where the security flaws lie. They document each vulnerability they find, along with their impact level, and also provide recommendations for remediations.
Cloud Penetration Testing offers you:
Want to find the security flaws in your cloud infrastructure? Do accurate cloud penetration testing with our help? We follow a process-based hybrid pentest approach. Click the link below and talk to our cybersecurity expert now!

Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
To secure data and applications in a cloud environment, you need to understand the common security threats and how to address them. With most companies using cloud computing for critical business operations, they should, without a doubt, prioritize its security.
By using effective cloud security measures like data encryption and identity and access management (IAM), companies can prevent unauthorized access to sensitive data. Additionally, by conducting penetration testing, you can enhance the infrastructure security in cloud computing.
A: Infrastructure security in cloud computing refers to measures to protect critical assets and resources in the cloud from potential security threats.
A: You can secure cloud infrastructure by implementing certain security measures, such as:
A: Cloud infrastructure refers to the components present/required to provide various cloud computing services. For example, storage, networking, computing power, and an interface that allows users to access virtual resources.

Pabitra Sahoo is a cybersecurity expert and researcher, specializing in penetration testing. He is also an excellent content creator and has published many informative content based on cybersecurity. His content has been appreciated and shared on various platforms including social media and news forums. He is also an influencer and motivator for following the latest cybersecurity practices.





Plot No:687, Near Basudev Wood Road,
Saheed Nagar, Odisha, India, 751007
No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions


No: 72, OJone India, Service Rd, LRDE Layout, Doddanekundi, India,560037
© 2024 Qualysec.com Disclaimer Privacy Policy Terms & Conditions