API penetration testing is a proactive security measure aimed at identifying vulnerabilities and weaknesses in the APIs of an application or system. It involves simulating various attack scenarios to evaluate the API’s resilience against potential threats. By conducting these tests, organizations can fortify their APIs, reducing the risk of data breaches and other security incidents.
The Importance of API Penetration Testing
In today’s interconnected digital landscape, APIs serve as the backbone of many applications, allowing them to communicate and share data seamlessly. However, this interconnectedness also makes APIs a prime target for cyberattacks. That’s where API penetration testing plays a crucial role. Beyond identifying vulnerabilities, it helps organizations understand the potential impact of an API breach and how to mitigate it effectively.
API penetration testing not only focuses on the technical aspects but also considers the business implications of a breach. For instance, a compromised API can lead to unauthorized access to sensitive data, financial losses, and damage to an organization’s reputation. By performing thorough penetration testing, companies can gain insights into the overall security posture of their APIs, enabling them to make informed decisions about risk management and resource allocation.
The Process of API Penetration Testing
API penetration testing typically follows a structured process. First, a comprehensive inventory of APIs within the system is compiled, including their functionalities and access points. Next, potential threats and vulnerabilities are identified, encompassing common issues like injection attacks, authentication flaws, and data exposure. Afterward, a series of controlled attacks and security assessments are executed to assess how the APIs respond to various scenarios.
Penetration testers use a combination of automated tools and manual testing techniques to uncover vulnerabilities. They may attempt to manipulate input data, bypass authentication mechanisms, and test the API’s resistance to brute-force attacks.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Why API Penetration Testing Matters
APIs serve as a bridge between different software components, making them a prime target for cyberattacks. Failure to secure APIs can result in data breaches, unauthorized access, and financial losses. API penetration testing helps organizations:
1. Identify vulnerabilities before attackers can exploit them
API vulnerabilities can be elusive and challenging to detect through traditional security measures. Penetration testing takes a proactive approach by simulating real-world attacks, helping organizations find and fix weaknesses before malicious actors can exploit them. This early detection can prevent potentially devastating breaches.
2. Ensure compliance with security standards and regulations
Many industries and regions have specific security standards and regulations that organizations must adhere to. API penetration testing can help businesses ensure compliance with these requirements. By demonstrating a commitment to security through testing and remediation, companies can avoid legal repercussions and regulatory fines.
3. Enhance user trust by demonstrating a commitment to security
In an era where data breaches and cyberattacks are frequent headlines, user trust in digital services is paramount. When organizations invest in API penetration testing, they send a clear message to their users that security is a top priority. This commitment to safeguarding sensitive data can enhance user confidence and loyalty.
4. Prevent data leaks and maintain data integrity
APIs often handle sensitive data, including personal information and financial records. A breach or data leak through an API can have severe consequences, including reputational damage. API penetration testing helps organizations prevent data leaks, maintain data integrity, and protect their customers’ information.
5. Proactively address emerging threats
The threat landscape is constantly evolving, with new attack techniques and vulnerabilities emerging regularly. API penetration testing allows organizations to stay ahead of these threats by regularly assessing their APIs and adapting their security measures accordingly.
Common API Vulnerabilities
APIs are a critical part of modern software systems, but they can also be a source of vulnerabilities if not properly secured. API penetration testing helps identify and address these vulnerabilities to ensure the integrity and security of an organization’s data and services. Here are some common API vulnerabilities that testing aims to uncover:
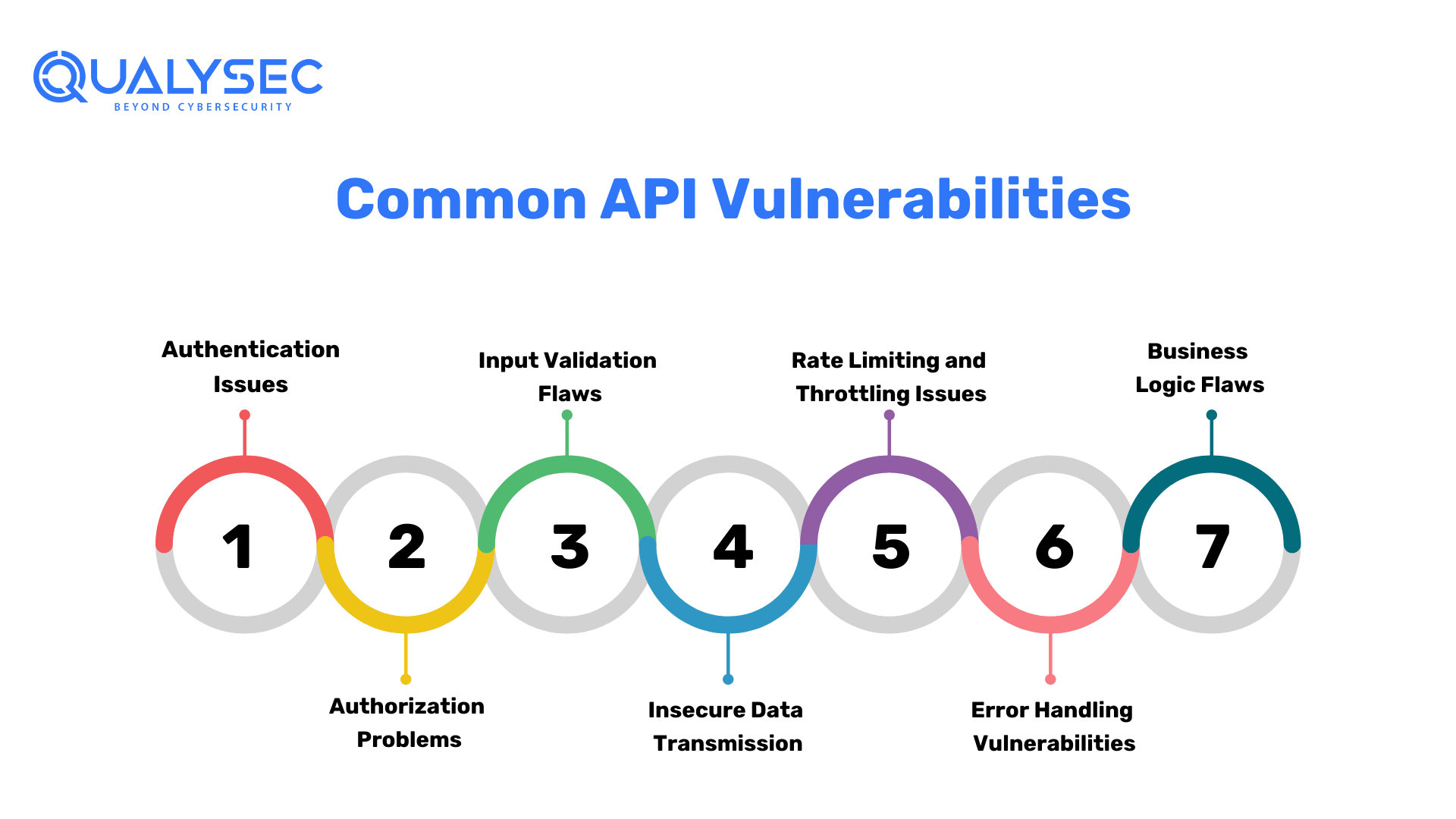
3.1. Authentication Issues
Weak or improper authentication mechanisms can allow unauthorized users to gain access to sensitive data or functionalities. API penetration testing assesses the strength of authentication methods, such as password policies, token-based authentication, or multi-factor authentication. It aims to identify weaknesses that could be exploited by attackers to gain unauthorized access.
3.2. Authorization Problems
Inadequate authorization checks may permit authenticated users to perform actions they shouldn’t. For example, a user with basic access permissions should not be able to access admin-level functionality. API penetration testing helps ensure that proper authorization controls are in place to prevent unauthorized access and actions.
3.3. Input Validation Flaws
Insufficient input validation can lead to injection attacks, such as SQL injection or cross-site scripting (XSS). Testing aims to identify and rectify input validation issues by assessing how the API handles different types of input, including malicious input designed to exploit vulnerabilities. By identifying and fixing these flaws, organizations can prevent attackers from injecting malicious code or commands through the API.
3.4. Insecure Data Transmission
APIs often transmit sensitive data, and if that data is not properly protected during transmission, it can be intercepted by attackers. API penetration testing evaluates the security of data transmission mechanisms, such as the use of encryption protocols like TLS/SSL. Ensuring secure data transmission is crucial to prevent data leaks and maintain confidentiality.
3.5. Rate Limiting and Throttling Issues
APIs can be vulnerable to abuse if they lack proper rate-limiting and throttling mechanisms. Without these controls, attackers can overwhelm the API with excessive requests, leading to service disruptions or resource exhaustion. API penetration testing assesses the effectiveness of rate limiting and throttling measures to prevent abuse and ensure fair access to resources.
3.6. Error Handling Vulnerabilities
Insecure error handling can provide attackers with valuable information about the API’s internal workings, potentially aiding them in crafting more targeted attacks. Testing looks for vulnerabilities in error handling processes to ensure that error messages do not reveal sensitive information and that errors are handled securely.
3.7. Business Logic Flaws
Beyond technical vulnerabilities, API penetration testing also examines business logic flaws. These flaws may allow attackers to manipulate the API in unintended ways to achieve unauthorized outcomes. Testing helps identify and address these flaws to ensure that the API operates as intended.
By addressing these common API vulnerabilities through penetration testing, organizations can bolster the security of their APIs and reduce the risk of data breaches, unauthorized access, and other security incidents.
The API Penetration Testing Process
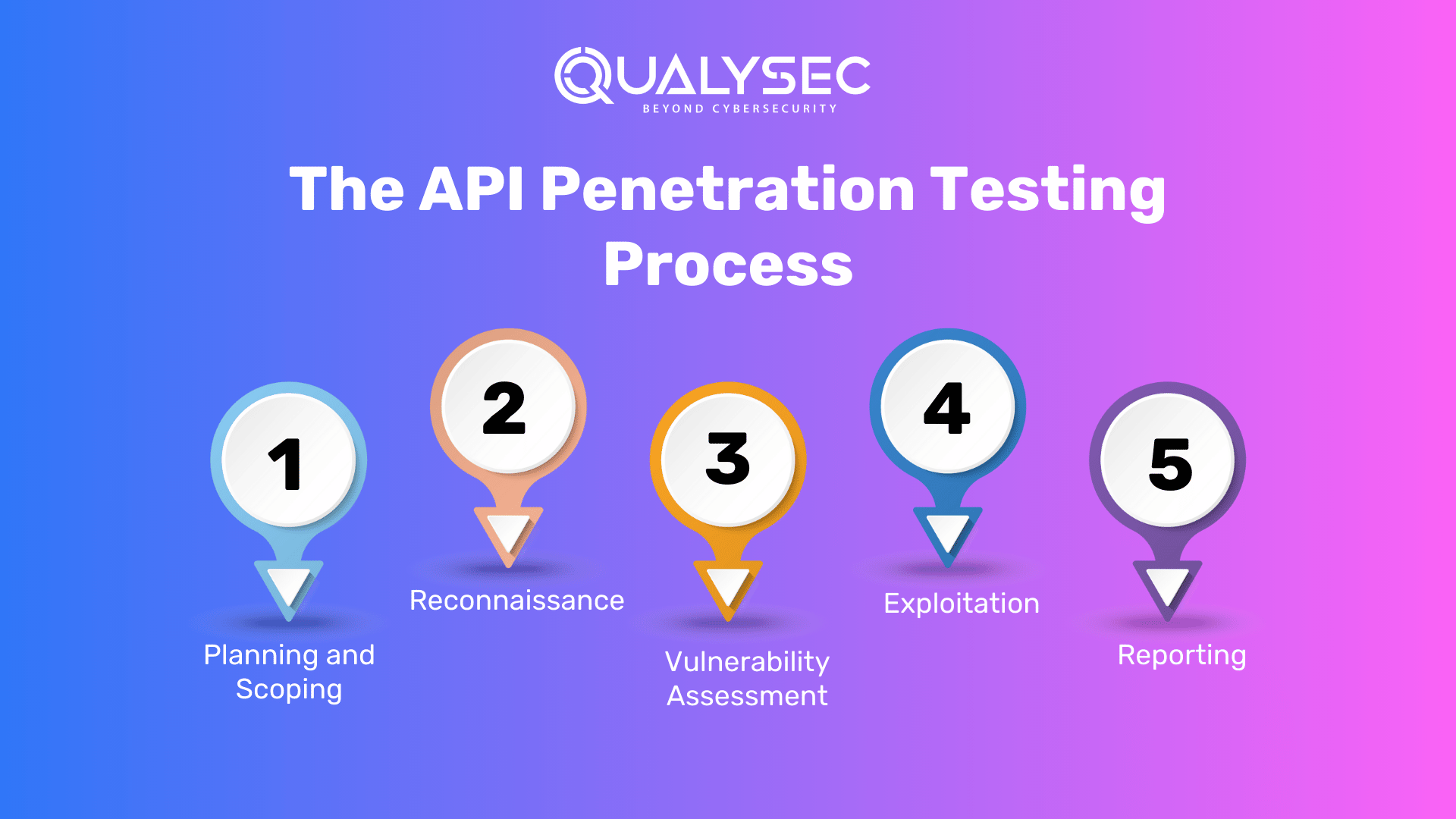
API penetration testing is a systematic approach to assess the security of APIs and identify vulnerabilities. It consists of several well-defined phases to ensure a thorough evaluation of an API’s security posture:
4.1. Planning and Scoping
The first step in API penetration testing is to define the scope, objectives, and constraints of the test. This phase involves:
- Identifying which APIs will be tested: Determine which APIs are in scope and should be evaluated for vulnerabilities.
- Defining objectives: Specify the goals of the test, such as identifying authentication weaknesses, authorization issues, or input validation flaws.
- Setting constraints: Establish any limitations or constraints that may affect the testing process, such as testing during non-production hours to avoid disrupting services.
4.2. Reconnaissance
During the reconnaissance phase, testers gather information about the APIs and their endpoints. This information helps testers understand the API’s architecture, interactions, and potential vulnerabilities. Activities in this phase may include:
- Identifying API endpoints: Document all the endpoints and functionalities provided by the API.
- Understanding data flow: Analyze how data flows between the API and other components of the system.
- Mapping dependencies: Identify third-party services or components that the API relies on.
- Collecting documentation: Review API documentation, if available, to understand expected behaviors and potential security features.
4.3. Vulnerability Scanning
In this phase, specialized tools and techniques are used to scan the APIs for vulnerabilities. Common vulnerabilities that are assessed include improper authentication, authorization issues, input validation flaws, and more. Key activities in this phase involve:
- Automated scanning: Use vulnerability scanning tools to identify common security issues.
- Manual testing: Conduct manual testing to uncover vulnerabilities that automated tools may miss.
- Authentication testing: Assess the strength of authentication mechanisms.
- Authorization testing: Evaluate whether users can access only authorized resources.
4.4. Exploitation
Once vulnerabilities are identified, the exploitation phase involves attempting to exploit these vulnerabilities to assess their severity and potential impact. This phase helps determine how easily an attacker could exploit a vulnerability and what the consequences would be. Activities may include:
- Attempting to bypass authentication: Test if it’s possible to gain unauthorized access.
- Exploiting input validation flaws: Try to inject malicious data or code.
- Assessing the impact: Understand what an attacker could do if they successfully exploited a vulnerability.
4.5. Reporting
The final phase of API penetration testing involves documenting and reporting the findings. A comprehensive report is compiled, which includes details on the vulnerabilities discovered, their potential impact on the system, and recommended remediation steps. The report serves as a valuable resource for organizations to improve their API security. It should include:
- Vulnerability descriptions: Clearly articulate the identified vulnerabilities.
- Risk assessment: Evaluate the potential impact of each vulnerability.
- Remediation recommendations: Provide guidance on how to address and mitigate the identified issues.
- Executive summary: Summarize the key findings and their significance for decision-makers.
By following this structured API penetration testing process, organizations can systematically evaluate and improve the security of their APIs, reducing the risk of security breaches and data exposure.
Here is a Table Explaining the API Penetration Testing Process :
| Phase | Description |
|---|---|
| 4.1. Planning and Scoping | Defining the scope, objectives, and constraints of the test is crucial. Determine which APIs will be tested and what types of attacks will be simulated. |
| 4.2. Reconnaissance | Gather information about the APIs, endpoints, and potential vulnerabilities. This phase helps testers understand the API’s architecture. |
| 4.3. Vulnerability Scanning | Use specialized tools to scan for vulnerabilities like improper authentication, authorization issues, and input validation flaws. |
| 4.4. Exploitation | Attempt to exploit identified vulnerabilities to assess their severity and potential impact. |
| 4.5. Reporting | Compile a comprehensive report detailing the vulnerabilities discovered, their potential impact, and recommended remediation steps. |
Qulysec: The Best API Penetration Testing Service Provider

Qualysec is a cybersecurity company founded in 2020 that has quickly become one of the most trusted names in the industry. The company provides services such as VAPT, security consulting, and incident response.
Although Qualysec’s Oppressional office is in India, Qualysec’s extensive knowledge and expertise in cybersecurity testing services have earned a reputation among the Best API Penetration Testing Service Providers.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The Qualysec team is made up of seasoned offensive specialists and security researchers who collaborate to give their clients access to the most recent security procedures and approaches. They provide VAPT services using both human and automated equipment.
In-house tools, adherence to industry standards, clear and simple findings with reproduction and mitigation procedures, and post-assessment consulting are all features of Qualysec’s offerings.
The solution offered by Qualysec is particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by doing routine penetration testing, businesses may see weaknesses and fix them before thieves attack them.
As a result, Qualysec is rated as the best of the best API Penetration Testing Service Providers.
Tools for API Penetration Testing
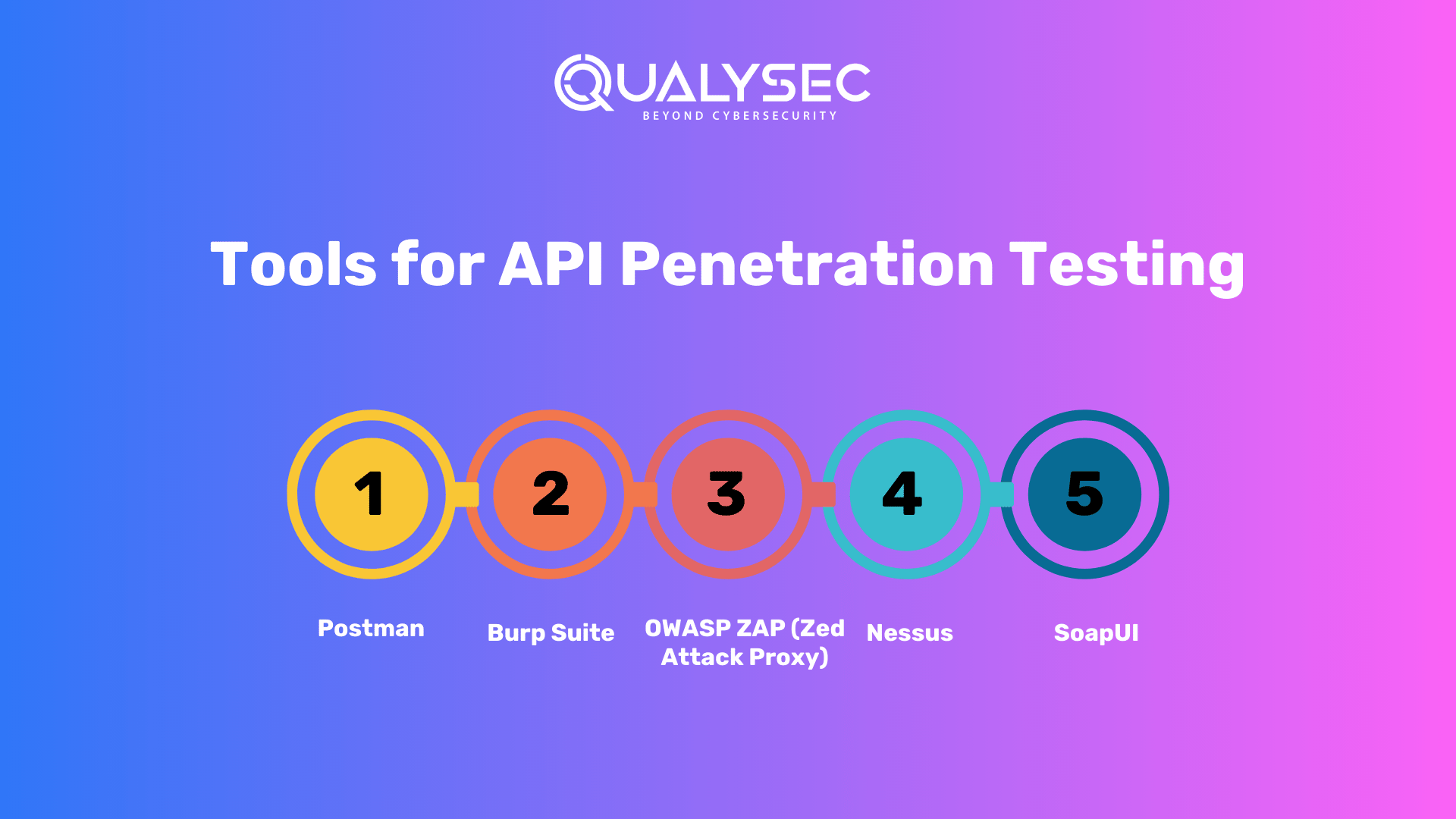
1. Postman:
- Overview: Postman is a popular API development and testing tool. While it’s primarily used for API development, it can also be valuable for penetration testing.
- Features: Postman provides a user-friendly interface to send requests, view responses, and perform various API testing tasks. You can create and run test suites, automate API tests, and inspect API payloads.
- Use Case: Penetration testers can use Postman to send different types of requests, manipulate input data, and analyze responses. It’s especially useful for testing API functionality and input validation.
2. Burp Suite:
- Overview: Burp Suite is a comprehensive web application security testing tool, and it includes features for API testing.
- Features: Burp Suite offers a wide range of tools, including a proxy, scanner, intruder, and repeater. These can be adapted for API testing to capture and manipulate API traffic, identify vulnerabilities, and perform automated scans.
- Use Case: Penetration testers often use Burp Suite to intercept and inspect API requests and responses, conduct security assessments, and identify vulnerabilities such as authentication issues, authorization problems, and input validation flaws.
3. OWASP ZAP (Zed Attack Proxy):
- Overview: OWASP ZAP is an open-source web application security testing tool that also supports API testing.
- Features: ZAP provides functionality for automated scanning, manual testing, and fuzzing. It allows users to intercept API traffic, modify requests and responses, and identify vulnerabilities.
- Use Case: Penetration testers can use ZAP to actively scan APIs for known vulnerabilities, perform brute-force attacks, and analyze API behaviors for security weaknesses.
4. Nessus:
- Overview: Nessus is a vulnerability assessment tool that can be used for API penetration testing by scanning for known vulnerabilities in APIs and their underlying infrastructure.
- Features: Nessus includes a vast database of known vulnerabilities and can perform network-based scans to identify weaknesses in APIs and associated services.
- Use Case: Penetration testers can use Nessus to assess the security of APIs indirectly by scanning the network for vulnerabilities that may affect API endpoints or the infrastructure that supports them.
5. SoapUI:
- Overview: SoapUI is a specialized API testing tool, particularly useful for testing SOAP and REST APIs.
- Features: SoapUI allows testers to create and execute API test cases, automate API tests, and generate comprehensive test reports. It supports both functional and load testing.
- Use Case: Penetration testers can utilize SoapUI to simulate various API attacks, test for input validation issues, and evaluate API responses for security weaknesses.
These tools serve different purposes and have their strengths and weaknesses. The choice of tool depends on the specific requirements of the API penetration testing project, the type of APIs being tested (SOAP, REST, etc.), and the tester’s familiarity with the tool. In many cases, a combination of these tools may be used to provide comprehensive coverage and depth in API security assessments.
Best Practices for API Security
API security is crucial to protect sensitive data and ensure the integrity of systems. Here are some best practices to enhance API security:
6.1. Implement Proper Authentication
- Use strong authentication methods, such as OAuth 2.0 or API keys, to verify the identity of users and systems accessing the API.
- Employ multi-factor authentication (MFA) for added security, especially for privileged operations.
6.2. Enforce Strong Authorization
- Implement role-based access control (RBAC) to ensure that users can only perform actions they are authorized for.
- Use fine-grained permissions to restrict access to specific API endpoints and functionalities.
6.3. Validate Input Data
- Thoroughly validate and sanitize input data to prevent injection attacks, such as SQL injection or cross-site scripting (XSS).
- Implement input validation rules at both the API level and the application level to mitigate security risks.
6.4. Encrypt Sensitive Data
- Ensure that sensitive data transmitted via APIs is encrypted using strong encryption algorithms like TLS/SSL to protect it from eavesdropping.
- Use encryption for data at rest to safeguard stored information.
6.5. Regularly Update and Patch
- Keep APIs and related software up to date with security patches to address known vulnerabilities.
- Establish a patch management process to promptly apply security updates.
6.6. Implement Rate Limiting and Throttling
- Protect APIs from abuse by implementing rate limiting and throttling mechanisms. This prevents brute-force attacks and resource exhaustion.
- Monitor API usage and set limits based on expected traffic patterns.
6.7. Audit and Monitor API Activity
- Implement comprehensive logging and monitoring of API activity to detect and respond to suspicious or unauthorized access.
- Use intrusion detection systems (IDS) and security information and event management (SIEM) solutions for real-time monitoring.
6.8. Secure API Documentation
- Protect API documentation from unauthorized access, as it may reveal sensitive information about the API’s endpoints and behaviors.
- Provide only essential information in public documentation and restrict access to more detailed documentation.
6.9. Implement Web Application Firewalls (WAFs)
- Deploy Web Application Firewalls to inspect and filter incoming API traffic for known attack patterns and anomalies.
- Configure WAFs to block malicious requests and protect APIs from common attacks.
6.10. Conduct Regular Security Testing
- Perform API penetration testing and security assessments regularly to identify and address vulnerabilities.
- Automate security testing as part of the development and deployment pipeline.
6.11. Educate Developers and Users
- Train developers and API consumers on security best practices, including secure coding techniques and responsible API usage.
- Foster a security-aware culture within the organization.
By following these best practices, organizations can strengthen their API security posture and reduce the risk of security breaches, data leaks, and unauthorized access. API security should be an integral part of the overall cybersecurity strategy.
Challenges and Pitfalls in API Penetration Testing
API penetration testing is a crucial aspect of securing digital systems, but it comes with its share of challenges and potential pitfalls. Here are some common challenges and how to address them:
7.1. False Positives
One of the primary challenges in API penetration testing is dealing with false positives. Penetration testing tools may occasionally generate alerts for vulnerabilities that do not actually exist. This can result in wasted time and resources if these alerts are not carefully examined. To address false positives:
- Manual Verification: Skilled penetration testers should manually verify the findings to distinguish genuine vulnerabilities from false positives. This involves reviewing the context in which the vulnerability was reported and conducting further testing if necessary.
- Fine-Tuning: Regularly fine-tune and adjust the testing tools to reduce false positives. Customize the tool’s configurations to match the specifics of the API being tested.
7.2. Rate Limiting
Implementing rate limiting for APIs is a crucial defense against certain types of attacks, such as brute force attacks or denial-of-service attempts. However, configuring rate limiting correctly can be challenging:
- Configuration Complexity: Setting the right rate limits for different endpoints and user roles can be complex. It’s essential to strike a balance between security and usability.
- Testing Real-World Scenarios: Ensure that rate-limiting configurations are tested against realistic usage patterns to prevent false positives or negatives. Consider load testing to determine the optimal rate limits.
7.3. Logging and Monitoring
Effective logging and real-time monitoring are essential for detecting and responding to security incidents promptly. However, several challenges can hinder these efforts:
- Volume of Data: APIs can generate a significant volume of logs and monitoring data, making it challenging to identify relevant security events.
- Proper Configuration: Ensuring that logging and monitoring are correctly configured is crucial. Misconfigurations can lead to missed security incidents.
- Integration: Integrating logging and monitoring solutions with other security tools and incident response processes can be complex but is essential for a coordinated response to security threats.
Addressing these challenges requires a combination of technical solutions, skilled personnel, and ongoing vigilance. Regular training and staying updated on the latest developments in API security can help penetration testers and security professionals effectively navigate these challenges and pitfalls.
API Penetration testing Pitfalls Table
Here’s a table summarizing the challenges and pitfalls associated with API penetration testing:
| Challenge or Pitfall | Description |
|---|---|
| 7.1. False Positives | API penetration testing tools may generate false positives, indicating vulnerabilities that don’t actually exist. This can lead to wasted time and resources and requires manual verification to confirm vulnerabilities. |
| 7.2. Rate Limiting | Implementing rate limiting for APIs is essential to mitigate some types of attacks, such as brute force, but it must be configured correctly. Incorrect configuration can either hinder legitimate users or fail to deter attackers effectively. |
| 7.3. Logging and Monitoring | Effective logging and real-time monitoring are essential components of API security. Failure to establish proper logging and monitoring practices can result in delayed or ineffective incident detection and response, potentially allowing attackers to persist undetected. |
Benefits of API Penetration Testing
API penetration testing is a proactive approach to security assessment that brings several significant advantages to organizations:
1. Enhanced Security Posture:
- API penetration testing helps organizations identify and address vulnerabilities and weaknesses in their APIs. By proactively identifying and fixing security issues, the overall security posture of the organization is strengthened. This reduces the likelihood of successful cyberattacks and data breaches.
2. Compliance with Industry Standards:
- Many industries and regions have specific security standards and regulations that organizations must adhere to. API penetration testing assists in achieving compliance by identifying and mitigating security vulnerabilities and weaknesses. This helps organizations avoid legal repercussions, regulatory fines, and reputational damage associated with non-compliance.
3. Reduced Risk of Data Breaches:
- One of the primary benefits of API penetration testing is the reduced risk of data breaches. By uncovering and fixing vulnerabilities before malicious actors can exploit them, organizations can prevent unauthorized access to sensitive data. This proactive approach is crucial in safeguarding valuable customer information and intellectual property.
4. Protection of Brand Reputation:
- Data breaches and security incidents can severely damage an organization’s reputation. API penetration testing demonstrates a commitment to security and responsible data handling to customers, partners, and stakeholders. This, in turn, enhances trust and protects the brand’s reputation.
5. Cost Savings:
- Detecting and addressing security vulnerabilities early in the development process or in existing systems is generally more cost-effective than dealing with the aftermath of a security breach. API penetration testing helps organizations identify and remediate vulnerabilities before they lead to costly security incidents.
6. Prevention of Financial Losses:
- Security breaches often result in significant financial losses, including the costs associated with incident response, legal actions, regulatory fines, and loss of business. API penetration testing can help prevent these financial losses by identifying and mitigating security risks before they are exploited.
7. Competitive Advantage:
- Demonstrating a commitment to security through API penetration testing can give organizations a competitive advantage. Customers and partners are more likely to trust and do business with companies that prioritize data security and privacy.
In summary, API penetration testing is a strategic investment in an organization’s security and risk management efforts. It not only helps identify vulnerabilities but also provides a pathway to compliance, risk reduction, and enhanced reputation in an increasingly interconnected and data-driven world.
Latest Penetration Testing Report

Conclusion
API penetration testing stands as a pivotal pillar in contemporary cybersecurity. It is a proactive and methodical approach to identifying and mitigating vulnerabilities within your APIs, thereby safeguarding your digital assets and upholding the trust of your users. It’s important to recognize that security is not a one-time endeavor but an ongoing commitment.
In an ever-evolving digital landscape where threats constantly adapt and grow in sophistication, regular API penetration testing is indispensable. It equips organizations with the insights needed to stay ahead of emerging security challenges, enabling them to fortify their defenses and maintain the integrity of their systems and data.
By embracing API penetration testing as an integral part of your security strategy, you not only mitigate the risks of data breaches and cyberattacks but also signal your dedication to protecting your customers, partners, and stakeholders. In doing so, you not only enhance your organization’s resilience but also bolster your competitive edge in an increasingly interconnected and security-conscious world.
FAQs
Q1. How often should API penetration testing be conducted?
API penetration testing should be conducted regularly. This should be done ideally after significant updates to your APIs, and at least annually. This frequency ensures that you can address evolving security threats promptly and effectively.
Q2. Can API penetration testing be automated?
Yes, API penetration testing can include automation, but it’s crucial to remember that automation alone may not catch all vulnerabilities. Manual testing, with a human’s discerning eye, remains essential to identify nuanced and complex security issues.
Q3. What is the cost of API penetration testing?
The cost of API penetration testing varies based on factors like the complexity of your APIs, the scope of testing, and the chosen testing methodologies. It’s important to view this cost as an investment in security. Addressing vulnerabilities proactively can help prevent potentially costly data breaches and their associated consequences.
Q4. Are there industry-specific API security standards?
Yes, various industries have specific API security standards and regulations. For example, the healthcare sector is subject to the Health Insurance Portability and Accountability Act (HIPAA), while the financial industry follows the Payment Card Industry Data Security Standard (PCI DSS). These standards provide industry-specific guidelines for securing APIs and sensitive data.
Q5. How can I choose the right API penetration testing tool for my organization?
Choosing the right API penetration testing tool depends on factors such as your organization’s budget, the complexity of your APIs, and the expertise of your security team. Consider whether the tool aligns with your specific testing requirements and whether it provides the flexibility and features needed to address your API security challenges effectively.




































































































































































































































































































































































































































































































































0 Comments