DAST tools are used to detect security vulnerabilities in web applications and APIs while running. Dynamic application security testing or DAST is the process of using automated tools to simulate real attacks on applications to find security flaws.
With the striking rate at which applications are being attacked, their security has become a top priority for companies. In fact, 91% of web applications faced some sort of data breach in the past few years. This is in a time where the average data breach costs $4.45 million. Unreal right?
To prevent web application breaches, DAST is an essential part of cybersecurity. To help organizations, we have created this comprehensive blog that lists top DAST tools and highlights their importance.
What are DAST Tools?
Dynamic Application Security Testing Tools are software testing tools used to find security vulnerabilities in a web application. They are designed to analyze the application during runtime, interact with their interface just like an attacker would, and attempt to find exploitable vulnerabilities.
Dynamic security testing tools do not need access to the web application’s source code. They play a vital role in the software development lifecycle (SDLC), especially in the testing phase, where they help detect and fix vulnerabilities before the application is deployed. As a result, it not only secures the application production but also saves valuable time and resources.
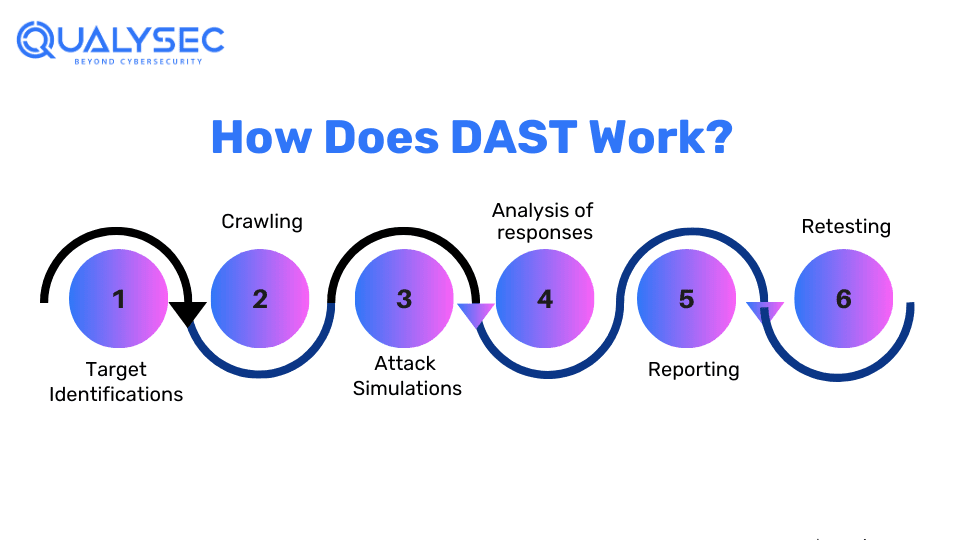
Key Features of DAST Tools:
- Black-Box Testing Approach: DAST tools use a black-box testing approach where the testers have no knowledge or access to the target application.
- Runtime Issue Detection: DAST tools examine applications during their runtime for vulnerabilities such as session management, misconfigurations, and data leakage.
- Crawling and Attack Simulation: Crawling refers to identifying possible entry points by navigating through the app’s interface. A combination of crawling and real attack simulation allows DAST tools to offer a comprehensive assessment.
- Detailed Reporting: Reports of DAST tools include the vulnerabilities identified, their potential impact, and recommendations for remediation.
Benefits of DAST Tools
Using DAST tools offers several benefits in security, such as:
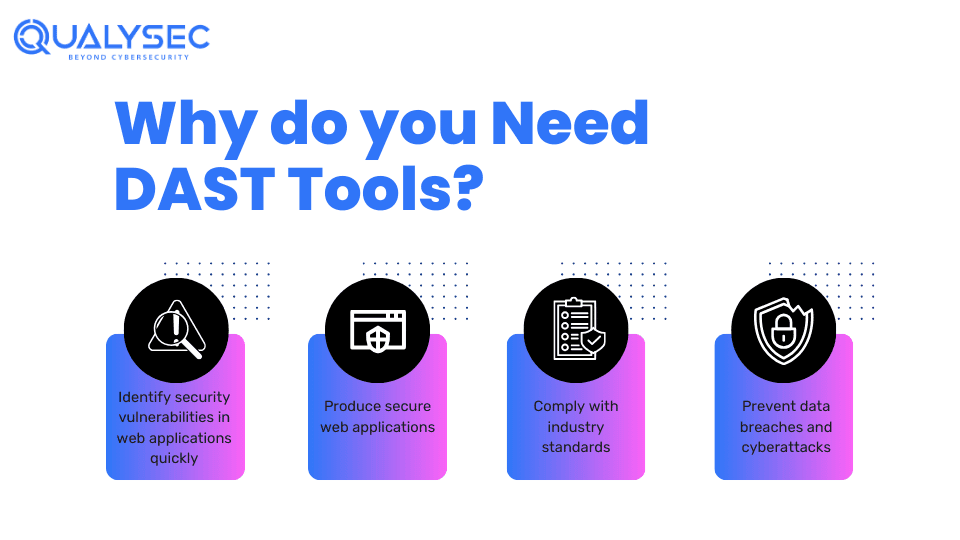
1. Identify Vulnerabilities
DAST tools can identify security vulnerabilities in web applications that attacks can exploit. The tools generate a report that includes the description of vulnerabilities discovered. As a result, it helps developers and security teams take necessary steps to fix those vulnerabilities and produce secure applications.
2. Real World Testing
DAST tools test the application in its operational or running state. Hence, it allows organizations to find security flaws that might not be discovered by other security testing, such as Static application security testing (SAST) or source code review.
3. Quick Testing
Unlike manual testing, DAST tools are automated. This means they can quickly scan applications to find vulnerabilities. As a result, it allows developers to prioritize remediation efforts based on the severity of the risks.
4. Comprehensive Testing
In DAST, the tools can test the entire application, including the user interface, back-end components, and web services. This provides a more comprehensive evaluation of the application’s security posture.
5. Language Agnostic
DAST is the only method in security testing that is not programming-language specific. It doesn’t look at your source code, assembly code, or byte code, instead, it checks the application’s inputs and outputs.
6. Cost-Effective
Using DAST tools is a cost-effective way to test the security of a web application. It doesn’t require access to the source code or specialized ethical hackers to test the application.
7. Compliance
DAST can help achieve compliance with industry standards like PCI DSS, ISO 2700, GDPR, HIPAA, etc. These regulations mandate security testing for applications that store user data. Using DAST tools can help with this criteria.
Top 10 DAST Tools for Businesses
Now that we have explored the importance of DAST tools, it’s time to look at some of the best popular tools in the market. In the security world, choosing the right tool is crucial for getting the desired results. Here are 10 of the best DAST tools that businesses can use:

1. Burp Suite
Burp Suite is a popular DAST tool used to test web applications. It offers features like automated scanning, manual testing, and advanced debugging tools to identify vulnerabilities such as SQL injection and cross-site scripting (XSS). It includes components like Spider for crawling, Scanner for vulnerability detection, and Intruder for customized attacks.
2. Netsparker
Netsparker is an automated web application vulnerability scanner that identifies common web vulnerabilities. It is known for its convenient use and accuracy. It uses a unique proof-based scanning technology that verifies identified vulnerabilities, which reduces false positives. Additionally, it integrates with various CI/CD pipelines for continuous security testing throughout the SDLC.
3. OWASP ZAP
OWASP ZAP (Zed Attack Proxy) is an open-source DAST tool that provides automated scanning and manual testing capabilities. It includes features like an automated scanner, passive scanner, and various components for manual testing such as spider, intercepting proxy, and fuzzer. It is suitable for both beginners and experts.
4. W3af
Web Application Attack and Audit Framework (w3af) is an open-source tool that helps identify and exploit web application vulnerabilities. It offers a comprehensive security assessment by combining automated scanning with manual testing features. W3af has over 150 plugins for vulnerability detection and exploitation. Its modular architecture allows testers to customize its functionality for unique testing needs.
5. Nikto
Nikto is a web server scanner that identifies security issues and misconfigurations. It can scan over 6,700 potentially dangerous files and programs, check over 1,250 servers for outdated versions, and identify version-specific issues. It has a straightforward command line interface that is accessible by both new and experienced users.
6. Metasploit
Metasploit is a powerful penetration testing framework that helps security professionals test and exploit vulnerabilities in web applications. It includes a huge library of exploits and auxiliary modules. Thus making it a versatile tool for performing comprehensive security testing. It can be integrated with other tools and its extensive documentation makes it a favorite for security experts.
7. Acunetix
Acunetix is an automated web vulnerability scanner that detects security issues like SQL injection and XSS. It supports both black and grey box testing, can be integrated with development and issue-tracking tools, and has a comprehensive vulnerability management system to remediate vulnerabilities effectively.
8. Checkmarx
Checkmarx is a DAST platform that scans web applications and provides actionable insights to fix security issues in the SDLC. Its versatile nature allows for a holistic approach to web application security. it can be seamlessly integrated into the development process, which ensures the web application is built with proper security from the ground up.
9. Veracode
Veracode scans web applications for security vulnerabilities with its cloud-based DAST solution. It particularly provides SaaS application testing that integrates application analysis into the development pipelines. It also provides detailed DAST reports and remediation guidance that helps organizations improve their security posture.
10. Detectify
Detectify is an effective DAST tool that uses crowd-sourced security research to detect emerging threats and provides insights for remediation. Being an external attack surface scanning and management tool, Detectify is entirely automated and uses the knowledge of ethical hackers to update its scanning abilities continuously. It gets easily integrated into the development workflow, helping developers quickly find and address web app security issues.
How to Choose The Best DAST Tool?
While the basic function of DAST tools remains the same – finding security vulnerabilities in web applications – their interface and components differ. Here are a few criteria that will help you choose the DAST tool you need.
Core Functionality
- Identifying Web App Vulnerabilities: The DAST tool should uncover security vulnerabilities within the web application.
- Remediation Recommendations: Along with identifying vulnerabilities, the tools should provide recommendations for remediation.
- Compliance Report: The DAST tool should generate compliance reports for organizations that need to meet certain regulatory standards.
Key Features
- Real-Time Monitoring: The tool should continuously monitor applications to detect threats as soon as they arise.
- Integration Capabilities: It should have the ability to integrate with existing tools and frameworks for a streamlined workflow.
- Advanced Threat Intelligence: The tool should use up-to-date information to predict and secure against new and emerging threats.
- Automated Vulnerability Scanning: Regular and automated vulnerability scanning of web apps to ensure nothing slips through the cracks.
Usability
- User-Friendly Interface: The DAST tool you choose should have a straightforward dashboard that shows clear insights into the application’s security.
- Seamless Onboarding Process: It should be easy for the security team to use the tool, with minimal training.
- Responsive Customer Support: If any issues or queries arise related to the tool, they should be resolved with accessible and effective customer support.
- Customizable Alerts: The DAST tool should allow users to set and receive alerts as per their specific needs and preferences.
How to Implement DAST Tools in Your Business
To effectively implement DAST tools in your business, it’s important to follow a few best practices, such as:
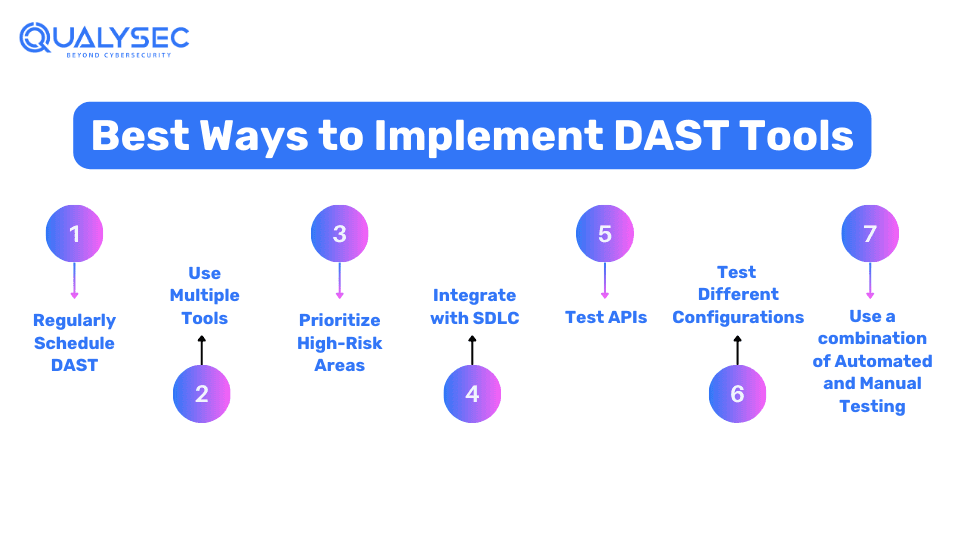
- Regularly Schedule DAST: Regular security testing is important because new vulnerabilities can emerge anytime, either through updates or changes in code.
- Use Multiple Tools: Different DAST tools have different capabilities for identifying vulnerabilities. Using multiple tools increases the chance of finding a variety of security weaknesses.
- Prioritize High-Risk Areas: Some vulnerabilities, such as authentication and encryption errors, are considered higher risk than others. DAST should ensure such vulnerabilities are identified and addressed first.
- Integrate with SDLC: DAST tools should be integrated into the development pipeline so that vulnerabilities can be addressed as early as possible.
- Test APIs: Make sure to test APIs as they can have vulnerabilities too that can be exploited by attackers, such as misconfigurations and validation issues.
- Test Different Configurations: Test the application under various configurations such as different browsers, devices, and web servers. This is because some vulnerabilities may be specific to certain configurations and might be missed if not tested across other configurations.
- Use a combination of Automated and Manual Testing: Automated DAST tool testing can identify a large number of vulnerabilities quickly. However, they may miss certain types of vulnerabilities for which manual testing is required.
Want to perform a combination of automated and manual testing on your application? Talk to our expert and secure your application from new security threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
With attacks on web applications on the rise, it is best to use DAST tools to test and identify vulnerabilities that can damage the application as well as your business. Some companies use DAST tools for DevSecOps like Acunetix for broad functionalities and seamless integration. Whereas others favor tools like OWASP ZAP that prioritize specific capabilities, in-depth analysis, and ease of use.
Nevertheless, combining DAST tool scanning with manual penetration testing is the best way to secure your web applications. The tool will identify surface-level vulnerabilities quickly, while dast penetration testing will identify the hidden vulnerabilities missed by the tool.
FAQs
Q: What is the best DAST tool?
A: While there are several DAST tools, here are a few popular ones:
- Acunetix: Best for automated vulnerability scanning
- Detectify: Best for information on crowd-sourced vulnerabilities
- Metasploit: Best for penetration testing and vulnerability exploitation
- Burp Suite: Best for web application security testing and analysis
- Netsparker: Best for accurate and automated web application vulnerability detection
Q: What is the DAST method?
A: Overview. Dynamic Application Security Testing (DAST) is the process of testing web applications for security vulnerabilities by simulating attacks. As a result, it helps developers to find and fix the errors in the application.
Q: What is the difference between SAST and DAST?
A: DAST analyses the web application in its runtime and doesn’t require source code access for scanning. In contrast, SAST tests the source code of the application when it is in the development phase.
Top Company Choose Qualysec for their Pentesting need
























































































































































































































































































































































0 Comments