As wireless, internet, and network-connected features become more integrated, along with portable media like USBs or CDs and the frequent technological transfer of health data related to medical devices, strong cybersecurity measures have become increasingly necessary to ensure the safety and efficacy of medical devices. The FDA Cybersecurity Guidelines highlight the need to protect medical devices from vulnerabilities to keep patients safe and devices functional. Additionally, due to the increased frequency and intensity of cybersecurity assaults directed at the healthcare industry, there is a higher chance of clinical repercussions.
The provision of patient care at healthcare institutions across the United States and the world has been hampered by cybersecurity breaches that have led to the failure of hospital networks and medical devices. As a result of these cyberattacks and vulnerabilities, clinical hazards, like delays in diagnosis and/or treatment, could harm patients.
Due to growing interconnection, specific devices are now functioning as separate components of bigger healthcare systems. These systems may consist of application update machines, other devices, connections of medical centers, and other interconnected components. A breach of FDA cybersecurity can therefore jeopardize a device’s safety and efficacy by impairing the operation of any system component if proper cybersecurity considerations are not given to all facets of these systems. Therefore, proper device cybersecurity and system-wide security are essential to guarantee device efficacy and safety.
What is the FDA (Food and Drug Administration)?
The Food and Drug Administration (FDA) is a federal agency of the United States Department of Health and Human Services that is responsible for safeguarding the general public by guaranteeing the security, reliability, and efficacy of both human and veterinary pharmaceuticals, biological compounds, and surgical instruments. It also regulates the country’s diet, beauty products, and radiation-emitting goods.
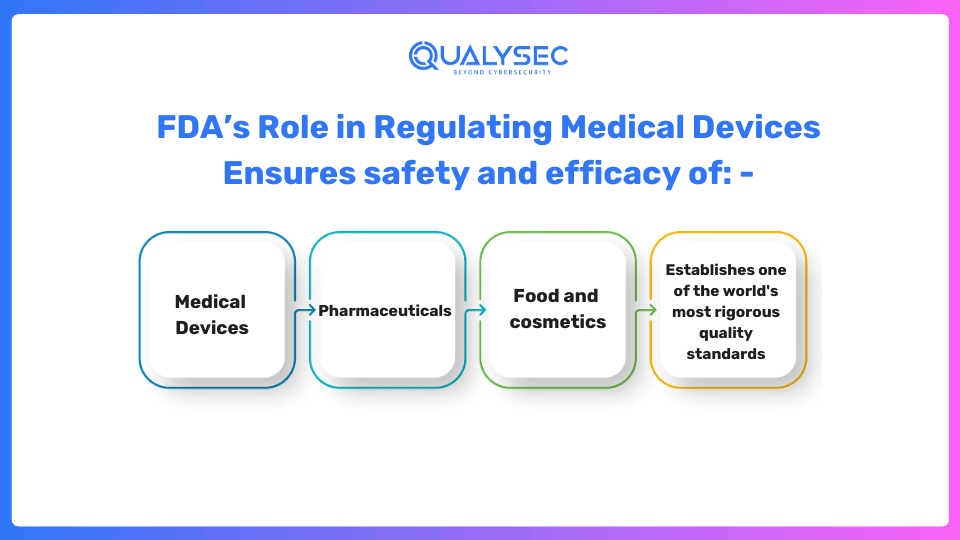
How Does the FDA Regulate Medical Devices?
The FDA is responsible for monitoring the development, production, marketing, and subsequent monitoring of healthcare products, ensuring that they meet rigorous security and efficacy standards, including FDA Cybersecurity Guidelines. As the oldest consumer protection organization in the United States, the FDA sets some of the most stringent quality requirements globally.
The FDA utilizes an administrative structure to classify healthcare products according to the danger they pose to the user or patient. The least amount of regulation is applied to the first-class devices, which are thought to present the least amount of danger. Due to their increased risk, second-generation devices need more scrutiny from regulators to give a fair guarantee of their efficacy and safety. FDA medical device cybersecurity that fall under Class III are thought to be the most dangerous and typically need preliminary market authorization (PMA), which is an academic assessment that guarantees the device’s effectiveness and security.
“Also Read – FDA Guidance for Medical Device Security Testing
FDA Guidelines for Securing Medical Network Devices
Key Updates in the Guidelines:
Although the layout and product of the updated FDA cybersecurity guidelines for medical devices are identical to those of the prior version, the security risk control part now includes two more significant sections:
- The exact data components that are required to be included in premarket entries will also be included in a separate annex for IDE filings.
- There are several cybersecurity word definitions.
Secure Product Development Framework (SPDF):
The FDA endorses the creation and application of a “Secure Product Development Framework,” or “SPDF,”. This is defined as a set of actions that reduce the quantity and seriousness of manufacturing flaws throughout its duration.
Three key components are the emphasis of the SPDF, which is intended to be the fundamental framework for managing cyberspace threats and they are Security Risk Management, Security Architecture, and Cybersecurity Testing.
The health software reference standard IEC 81001-5-1 is also mentioned in the manual as an excellent structure to look into while creating the SPDF.
Premarket Submissions and Cybersecurity Risk Reports:
According to the FDA Cybersecurity Guide the year 2023, a security risk report by management should be included in a submission for premarket approval to help demonstrate the efficacy and safety of the product.
Cybersecurity Risk Assessments:
The initial of the two new parts on “Cybersecurity Risk Assessments” is part of the updated cybersecurity risk management section of the instructions. The recommendation recognizes that risks related to cybersecurity are hard to predict and that the likelihood of a breach happening may not be estimated or quantified using past information or simulation.
By defining the content required for premarket paperwork, these guidelines make sure that companies provide sufficient evidence of their cybersecurity risk management plans. This includes a cybercrime risk management strategy for the gadget as well as documentation of medical device cybersecurity risk assessments, security controls, and outcomes of testing.
An SBOM (Software Bill of Materials), that contains an in-depth list of all software components used in a device for healthcare, which includes those created by the manufacturer and those created by other companies, is what the FDA cybersecurity compliance is requesting. An SBOM facilitates risk management procedures by assisting users and device manufacturers in promptly identifying possible safety risks.
The FDA’s Cybersecurity Requirements for Medical Devices
Unlike various facets of the manufacturing process, assessment is used to demonstrate the effectiveness of control mechanisms. Cybersecurity regulations require a test that goes beyond typical software validation and verification tasks, notwithstanding the intimate relationship between the creation of software and cybercrime. This is necessary to illustrate the measures’ efficacy inside an appropriate safety framework. This proves that the product’s efficiency and security are reasonably guaranteed.
It is necessary for an organization to establish and uphold procedures for verifying its device layout. This check must guarantee that the design result meets the design input’s requirements. To certify the design of a device, its maker must set up and uphold procedures. Validation of software and risk assessments must be included in the validation of designs in which applicable.
The FDA suggests that sufficient examination of the maker’s inputs and findings, if any, and additionally, the cybersecurity requirements for medical devices should be part of the verification and endorsement process. The premarket filing should contain security testing paperwork along with any related conclusions or assessments.
Several types of tests are recommended to be included in the surrender, among other things, by the FDA cybersecurity guidance for the year 2023:
- Security Conditions
- Reduction of threats
- Testing for Vulnerabilities
- Testing for Penetration
The FDA recommends evaluating the SPDF for cybersecurity. In addition to preventing the requirement to completely remake or revamp the device, early testing for security ensures that safety flaws are fixed before impacting the date of release. After release, continuous cybersecurity analysis is conducted following the danger to make sure that flaws may be identified and fixed before they are exploited.
Cybersecurity Majors to Be Enrolled in Medical Supplies
To help cybersecurity experts manage healthcare device safety, the FDA developed cybersecurity guidelines for connected medical equipment. When handling medical equipment, important security requirements are satisfied, including:
- Incorporate safety in the gadget.
- Make safety unique to all of them.
- Firmware security
- Device-stored secure data
- Secure connection between devices
Medical device intrusions can take many different forms, ranging from attacks using ransomware where attackers pretend to have compromised IoMT devices and want payment to restore availability, to theft of information operations that are intended to go undetected. It is essential to continuously monitor for various cybersecurity attacks to identify vulnerabilities before hackers cause significant damage.
There isn’t any simple method for securing each medical instrument against every type of attack because there are so many variables that affect IoMT safety. Making sure you know which medical equipment is on your computer system and what kinds of attacks could damage them is an essential starting point, though.
Benefits of Manufacturers Following FDA Standards
The recommendations cover the main responsibilities of manufacturers of medical devices that employ open-source software. The FDA’s Safety Management rule explains these obligations. The FDA has previously notified companies of their responsibilities.
The purpose of this data is to help manufacturers fully comprehend their cybersecurity responsibilities under the FDA for devices for medical use. If companies decide to use OTS programs, they must take action to maintain the security and functionality of their connected equipment. In addition, the security and functionality of their gadgets are compromised by flaws in OTS technology.
Medical device manufacturers are required by the FDA’s Quality Framework rule to look into reliable sources of data and address or prevent quality problems. Software patches are typically not subject to FDA review before being installed by a device manufacturer.
The majority of improvements to the software are regarded by the FDA as design changes that companies are free to implement with no prior FDA approval. In the past, the FDA has advised manufacturers on when to seek advice from the FDA.
Suppliers are required to verify their software versions under the Quality System rule. This means they have to look at what the change achieves and show that the updated application meets user needs and functions as intended regularly.
However, it is rarely necessary for manufacturers to request FDA approval for their implants. However, they must create and carry out a strategy for these changes as part of quality control. To safeguard the gadgets and adhere to FDA cybersecurity guidelines for medical devices, companies could request expert assistance from penetration test firms.
How can Healthcare Device Makers Improve their Security?
Manufacturers of medical devices can improve their cybersecurity by implementing these strategies:
- Secure Communications: When it involves transmitting information between and within the device, the manufacturer should consider how the gadget might function with different networks and devices, communicate with equipment that provide less secure communication, and guard from unauthorized access or alteration.
- Data Protection: The manufacturer should determine whether some level of cryptography is necessary for data that is stored or transferred on the device. This also covers if privacy risk control techniques are necessary for the device.
- Device integrity: The manufacturer should assess threats to the device’s integrity, examine the at system level framework for mandatory characteristics, as well as anti-malware measures.
- User Authentication: The creator should consider identification of users, which determines who may use the gadget or grant access to user rolls.
- Software Maintenance: The maker ought to take the method of communication into account. This covers the control and updating of the software. Additionally, the connections that are required to perform updates, the method of updating the device to protect it from other weaknesses, and the usage of code signatures to verify the legitimacy of the link.
- Access Controls: To avoid unauthorized access to the gadget, the maker ought to think about implementing limitations.
- Durability and Reliability: The manufacturer should consider creating features that enable the gadget to recognize, thwart, react to, and recover from cyberattacks.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
With more and more companies depending on smart devices or the World Wide Web of Medical Equipment, the healthcare industry is changing. IoMT offers innovative ways to modernize medical practices and enhance patient treatment, but it isn’t risk-free. These gadgets are vulnerable to potential cyberattacks since they don’t have sufficient safety features in place. To address this, aligning with FDA Cybersecurity Guidelines can help identify possible security dangers and vulnerabilities to ensure comprehensive protection. Once we are aware of our difficulties, we can implement efficient safeguards.
The system at hand may function more securely if the threat surface—the sum of all possible security issues—is managed. In addition, as technology develops, protecting patient information and electronic medical records becomes increasingly important.
Regarding medical device safety, we must speak with an expert. QualySec Technologies, a reputable business, offers healthcare vulnerability and penetration testing services. At QualySec Technologies, we understand how important it is to protect client data and healthcare systems. Our specialized healthcare penetration testing services aim to identify potential weaknesses in your healthcare devices, software, and networks beforehand.
Do not wait for a security compromise to jeopardize patients’ health and confidence. Contact QualySec Technologies right now to arrange a comprehensive healthcare security assessment tailored to your company’s unique needs. Let’s work together to bolster our protections and give everyone access to a safe and effective medical ecosystem.
FAQ:
What is medical device cyber security?
The practices and tools HDOs employ to protect their Internet of Medical Things (IoMT) are referred to as medical device security measures. Additionally, it protects medical software and devices from unauthorized access, theft of information, threats to patient safety, and/or disruptions of essential services.
What is a medical device that is networked?
Medical devices with networks include heart rate monitors, pumps for infusion, and imaging diagnostic equipment. These devices may be utilized to track patients, transfer patient data, and/or offer treatment.
Why is cybersecurity crucial for medical machinery?
Medical gear is protected by cybersecurity against malevolent thieves who could gain access to the device and alter data. In addition, this may result in financial damage, breach of confidentiality, or interruptions in care.
Ensure your healthcare solution is globally compliant.
Qualysec helps you meet HIPAA, FDA, ISO, and more. Contact us today!
























































































































































































































































































































































0 Comments