Software as a Service (SaaS) applications have become essential for many companies, providing unequaled convenience and flexibility. This, however, comes with the significant task of assuring that the apps are secure. The SaaS application security is paramount when protecting sensitive data, maintaining user trust, and preventing cyber threats.
In this blog, we will dive into the complexities of SaaS application security by explaining its importance, key points, challenges, and best practices and providing a practical checklist of actions to strengthen your SaaS applications.
What is SaaS Application Security?
SaaS (Software as a Service) application security deals with the set of actions and protocols applied to secure SaaS applications presented over the internet. It includes strategies such as data encryption, authentication methods, access controls, and regular security audits. Software as a service (SaaS) providers prioritize the security of customer data and comply with relevant industry standards such as GDPR and HIPAA.
Additionally, they use advanced cybersecurity techniques to prevent risks like data breaches, unauthorized access, and service interruption. Real-time monitoring, updates, and client involvement should be part of the SaaS environment framework that secures the provider’s and the user’s interest in the dynamic, interconnected digital environment.
Importance of SaaS Application Security
SaaS application security is not just a necessity but a crucial aspect that ensures the safety of confidential information, the privacy of users, and the integrity of organizations. By implementing strong security measures, SaaS applications can avoid unauthorized access, data breaches, and cyber-attacks, fostering trust among users and clients.
However, the potential risks of not prioritizing SaaS application security are significant. They include the loss of sensitive data, damage to the company’s reputation, and legal and financial repercussions. Secure SaaS applications comply with industry regulations, eliminating these potential risks. Moreover, a robust security framework demonstrates a dedication towards the safety of customers, helping to retain existing ones and acquire new ones.
By proactively harnessing encryption, authentication protocols, and frequent updates, SaaS applications can become cyber-proof against emerging vulnerabilities. Therefore, considering SaaS application security protects the business and its reputation in the digitally connected world.
SaaS Application Security – Key Principles
Securing a Software as a Service (SaaS) application is a core task to ensure data safety, users’ trust, and regulation compliance. Here are some fundamental principles for SaaS application security:
1. Data Encryption:
Implement robust encryption algorithms for data both at rest and in transit. Thus, the possibility of the data being compromised through unauthorized access may not happen as it will remain inaccessible and unreadable.
2. Identity and Access Management (IAM):
Implement strong IAM policies to authenticate the users and control their access levels in the application. Therefore, this can be accomplished by implementing multi-factor authentication, role-based access controls, and periodic access reviews.
3. Regular Security Audits and Testing:
Implement periodic security audits and penetration testing to discover the app’s weaknesses and vulnerabilities. Routine testing reveals developing threats and provides room for bettering the security protocols.
4. Compliance and Regulatory Adherence:
Make sure the app adheres to applicable industry standards and regulations like GDPR, ISO 27001, or PCI DSS based on the kind of application it handles and the data it processes. Furthermore, compliance increases trust among customers and prevents them from having legal implications.
SaaS Application Security Challenges and Risks
Here are some common challenges and risks associated with SaaS application security:
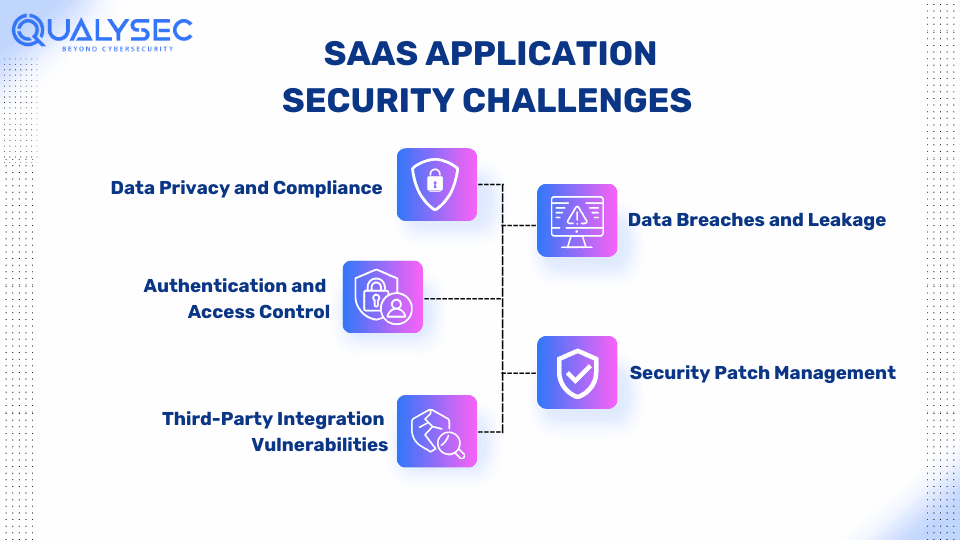
1. Data Privacy and Compliance:
Many SaaS applications involving sensitive data become cyberattack targets, often leading to data breaches. Complying with the regulations, including GDPR, ISO 27001, and SOC 2 is essential. It not only implies heavy penalties but also affects users’ trust.
2. Authentication and Access Control:
Lack of solid authentication can result in unauthorized access to confidential data. This is done through multi-factor authentication (MFA) and role-based access controls, which help avert the risks.
3. Third-Party Integration Vulnerabilities:
SaaS apps usually integrate several third-party service providers to enhance their functionality. However, third-party integrations may uncover software vulnerabilities if inadequate scrutiny is conducted. The regular security auditing of third-party services is vital for detecting and eliminating potential threats.
4. Data Breaches and Leakage:
The breach of SAAS applications can expose sensitive data, causing reputational damage and financial losses. Ensuring data encryption both in transit and at rest and designing a solid DLP framework is crucial for minimizing this risk.
5. Security Patch Management:
SaaS applications require secure environments that are constantly updated to address security flaws and loopholes. Not following security patches promptly renders systems prone to exploitation. A robust patch management process guarantees the timely distribution of patches, helping to avoid security issues through their timely resolution.
Contact the specialists of Qualysec and schedule a call today. We will assist you in identifying and addressing any weaknesses in your business’s infrastructure.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Best Practices to Strengthen SaaS Application Security
To improve the security of SaaS applications, consider the following best practices:
| Best Practices | Descriptions |
| Secure Software Development Lifecycle (SDLC) | Incorporate security into every stage of software development, including the design, development, deployment, and maintenance phases. Including security measures in the initial stage could help identify weak points and direct their resolution before they become problems. |
| Continuous Monitoring | Establish continuous monitoring tools to detect any suspicious activities or irregularities immediately. A proper plan should be created to adequately handle security incidents and limit their effects on the application and its users. |
| Vendor and Third-Party Risk Management | Evaluate the security profile of the third-party companies and providers upon whom your SaaS application relies. Ensure they follow best practices and standards for safety to prevent risks that may occur in connection with the services or products they offer. |
| Secure Configuration Management | Develop a secure configuration for each component or dependency of SaaS applications, like servers, databases, and third-party libraries. Often, check and update the configurations to let go of any security problems that appear because of modification in an environment or application requirements. |
SaaS Application Security Checklist
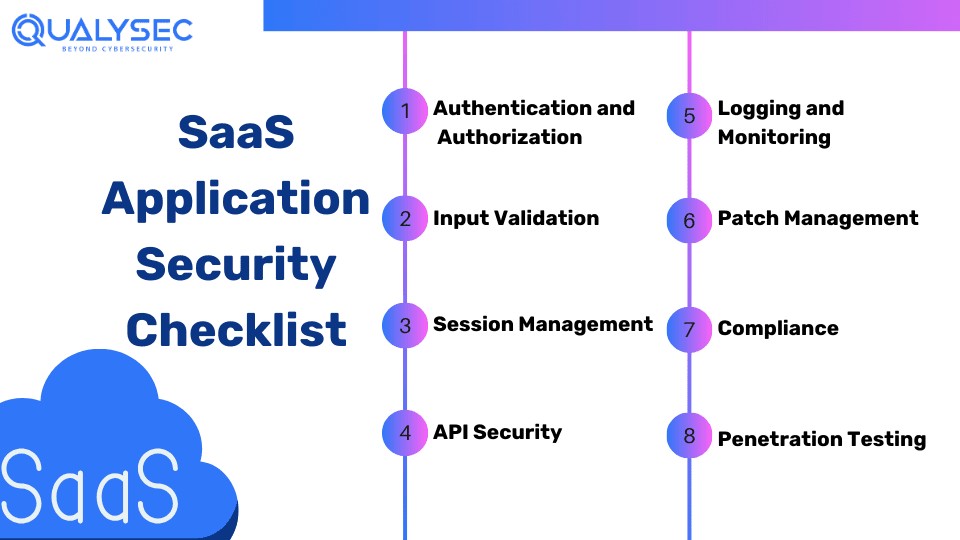
1. Authentication and Authorization:
Develop a robust authentication method with multi-factor authentication (MFA) and role-based access controls (RBAC) to prevent unauthorized access to sensitive data and services. This reduces the chance of information leakage and system vulnerability.
2. Input Validation:
Carry out validation and sanitizing of all user input to stop injection attacks like SQL injection and cross-site scripting (XSS), thus hardening the application against input manipulation through malicious attacks meant for data breaches or system compromise.
3. Session Management:
Incorporate the use of secure session handling mechanisms such as generating unique session identifiers, enforcing session timeouts, and encrypting session data to avoid session hijacking attempts and ensure the confidentiality and integrity of user sessions·
4. API Security:
Provide secure API authentication mechanisms like OAuth 2.0. Use the OAuth 2.0 and OpenID Connect authorization, thus enforcing appropriate authorization controls and deploying encryption for data in transit to safeguard APIs against unauthorized access and data leakage.
5. Logging and Monitoring:
Implement a comprehensive security logging policy to record all events of security interest and use real-time monitoring tools to enable quick detection and response to threats. This ensures optimal threat visibility and timely analysis.
6. Patch Management:
Regularly update and patch components, libraries, and frameworks to remove known security exploitation mechanisms, minimizing the risk of malicious actor exploitation and ensuring the integrity and security of application ecosystems.
7. Compliance:
Comply with regulatory requirements and industry standards like GDPR, ISO 27001, and PCI DSS. Use appropriate controls and procedures to safeguard sensitive information and adhere to the law and regulations.
8. Penetration Testing:
Regular penetration tests and security assessments can identify weaknesses and vulnerabilities in the infrastructure, code base, and configuration to increase resilience and reduce the likelihood of compromising the application.
Conclusion
Making SaaS apps secure against security threats needs a proactive and multilevel approach that utilizes technical controls, employee awareness, and vendor management. Organizations can adhere to fundamental principles, best practices, and checklists described in this guide to improve the information security posture of their SaaS applications and thwart the risks effectively.
In a continuously changing threat space, we cannot ignore SaaS application security, where we must protect sensitive data, maintain compliance with our regulations, and also preserve the trust of our customers and stakeholders.
FAQs
Q. What is the SaaS security?
A. SaaS security includes protecting cloud-based software applications and data from cyber threats using encryption, access control, threat detection, and compliance management to assure data integrity, confidentiality, and availability in a multi-tenant environment.
Q. How to protect SaaS applications?
A. To protect SaaS applications, employ strong user authentication, data encryption, and regular security upgrades. Watch for suspicious activity, conduct penetration testing, enforce access rules, and follow industry standards and regulations.
Q. Who is responsible for security in SaaS?
A. Security is a shared duty between the SaaS provider and the customer. While the supplier secures the infrastructure, the customer is responsible for protecting their data and user access within the application. Additionally, you can hire third-party security firms like Qualysec that offer SaaS security testing.





















































































































































































































































































































































0 Comments