The impending threat of cyberattacks has never been more prominent in an era driven by digital reliance. This blog seeks to untangle the convoluted web of cybersecurity by diving into the practical benefits of Web Vulnerability Assessment and Penetration Testing services, eventually advocating for proactive security measures that go beyond the conventional.
In essence, cybersecurity is a proactive strategy for identifying and mitigating possible risks. Vulnerability Assessment provides the framework for identifying system flaws, but Penetration Testing goes a step further by simulating real-world cyberattacks. Businesses may enhance their defenses against an ever-changing digital threat landscape by thoroughly grasping these fundamentals. Let’s dive into the blog.
Decoding Web VAPT: A Definitive Overview
Web Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security testing method for identifying and mitigating potential vulnerabilities and flaws in web applications, websites, and online systems. It entails a comprehensive analysis of the application’s security posture to identify and address any vulnerabilities before they may be exploited by bad actors.
Differences Between Vulnerability Assessment and Penetration Testing
Vulnerability Assessment (VA): This step entails a thorough examination of the web application’s code, configuration, and infrastructure to discover any security flaws. VA is similar to a thorough scan that seeks to generate a list of probable flaws. It frequently involves automated tools, although it may also entail hand examination.
Penetration Testing (PT): Unlike vulnerability assessment, penetration testing actively exploits reported vulnerabilities to determine their real-world effect and possible hazards. This simulates a bad hacker’s approach, assisting companies in understanding the actual dangers they face.
Related: Read more about Penetration Testing
The Approaches of Web VAPT:
Black Box Testing: It focuses on the behavior of the program on the outside, at the interface level, and hence does not require knowledge of its internal workings. This implies that testers will not be dealing with any code, algorithms, or other technical aspects. They approach the program only from the user’s standpoint, with little regard for what’s going on behind the surface. It’s like viewing software, with only the inputs and outputs running through it.
White Box Testing: While black box testing provides testers with a high-level overview of a software system, it provides no insight into its core code structure. This is where white box testing comes into play. This method allows testers to peer inside the white box and examine every component of the software system, from its code and architecture to its interconnections. This enables testers to have a full understanding of how the program performs its duties.
Gray Box Testing: Gray box testing is an excellent combination of black box and white box testing. It enables testers to approach a software product from the perspective of a user while still gaining access to its internal code. As a result, with this sort of testing, testers must have some grasp of the system’s core mechanics, although not as much as with white box testing. Furthermore, they test end-to-end features and user scenarios.
Navigating the Online Space: The Significance of Online VAPT Testing
If you own a business, you understand how important your reputation and assets are. That is why it is critical to take the required precautions to safeguard them from potential cyber security risks such as phishing, ransomware, and other serious cyber assaults. This is where the web app VAPT may help. Here are 5 reasons why businesses should conduct VAPT tests:
1. Meeting Compliance Requirements
Several industries have unique compliance standards that must be met to secure sensitive data. Healthcare organizations, for example, must follow HIPAA regulations, whereas banking institutions must follow PCI DSS guidelines. Pen testing may help businesses ensure that they are meeting regulatory guidelines and appropriately securing their data.
2. Identifying Vulnerabilities
One of the main reasons for doing a pen test is to find vulnerabilities in a company’s systems and networks. These might include software flaws, incorrectly configured systems, or other vulnerabilities that attackers could exploit. It is critical to identify vulnerabilities before they are exploited to keep an organization’s data and systems safe.
3. Identifying Insider Threats
Pen testing can also be used to identify insider threats. These hazards are posed by employees or contractors who have access to sensitive data and systems. By conducting a pen test, organizations may identify possible vulnerabilities that could be exploited by insiders and act to mitigate these risks.
4. Protecting Critical Business Assets
One of the primary reasons businesses want VAPT is to safeguard critical assets. By conducting frequent VAPT audits, businesses may identify security faults and vulnerabilities that could jeopardize their assets, such as intellectual property, financial data, and customer data.
5. Protection Against Cyber Threats
Businesses are often concerned about cyber dangers, and VAPT may help to provide safety. VAPT audits can assist in identifying vulnerabilities that hackers may use to gain unauthorized access to critical corporate data. Furthermore, businesses can drastically minimize their exposure to attacks by correcting these weaknesses.
Online VAPT Test: A Shield for Your Digital Fortress
As technology evolves, so do cyber enemies’ strategies. Modern cyber-attacks are sophisticated, focused, and possibly destructive, and are no longer limited to basement hackers. The necessity for a proactive cybersecurity approach is clearer than ever, with ransomware attacks holding organizations hostage and stealthy data breaches.
VAPT is on the front lines, reacting to the changing threat landscape and keeping your company one step ahead of possible attackers. The cat-and-mouse game between cybersecurity measures and cyber-attacks continues to escalate in this era of digital growth.
Cyber attackers are not just skilled at exploiting technological flaws, but they are also becoming increasingly competent at influencing human aspects through social engineering. The presence of nation-state actors and organized cybercrime syndicates in the environment has increased the importance of effective cybersecurity measures.
VAPT serves not only as a defense against known threats but also as a strategic compass, assisting firms in anticipating and fortifying themselves against the unexpected and ever-changing tactics of cyber attackers. It is not only about defense; it is also about remaining adaptable and proactive in the face of an ever-changing digital frontier.
Read More: VAPT and Its Impact in Reducing Vulnerabilities
Web Application VAPT: Ensuring Robust Cyber Defenses
Web apps are essential components of company operations in the digital age, acting as portals to vital data and services. However, because of their extensive use, they are attractive targets for cyber assaults. Web Application Vulnerability Assessment and Penetration Testing (Web App VAPT) is a specific technique designed to strengthen these critical components of a company’s online presence. Here are some of the common vulnerabilities that web app VAPT cures:
Attack Vectors:
- Web applications are vulnerable to a broad range of attack vectors, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and others.
- Web VAPT entails thorough testing to discover and mitigate vulnerabilities across these many attack surfaces.
Client-Side and Server-Side Vulnerabilities:
- Testing must cover both client-side and server-side vulnerabilities, including user inputs, data processing, and server settings.
- Web App VAPT enables a comprehensive approach to security testing by reviewing the complete application stack.
Session Management & Authentication:
- Evaluating the efficiency of session management and authentication techniques is critical in preventing unwanted access and identity-related issues.
- These components are examined by Web VAPT to guarantee safe user interactions and access controls.
API Security:
- Because APIs (Application Programming Interfaces) are increasingly used in current online applications, online App VAPT incorporates API security evaluations to avoid unwanted access and data disclosure.
- It is critical for overall web application security to ensure the secure integration of APIs.
Bolstering Security with Web Application VAPT: The Steps Involved
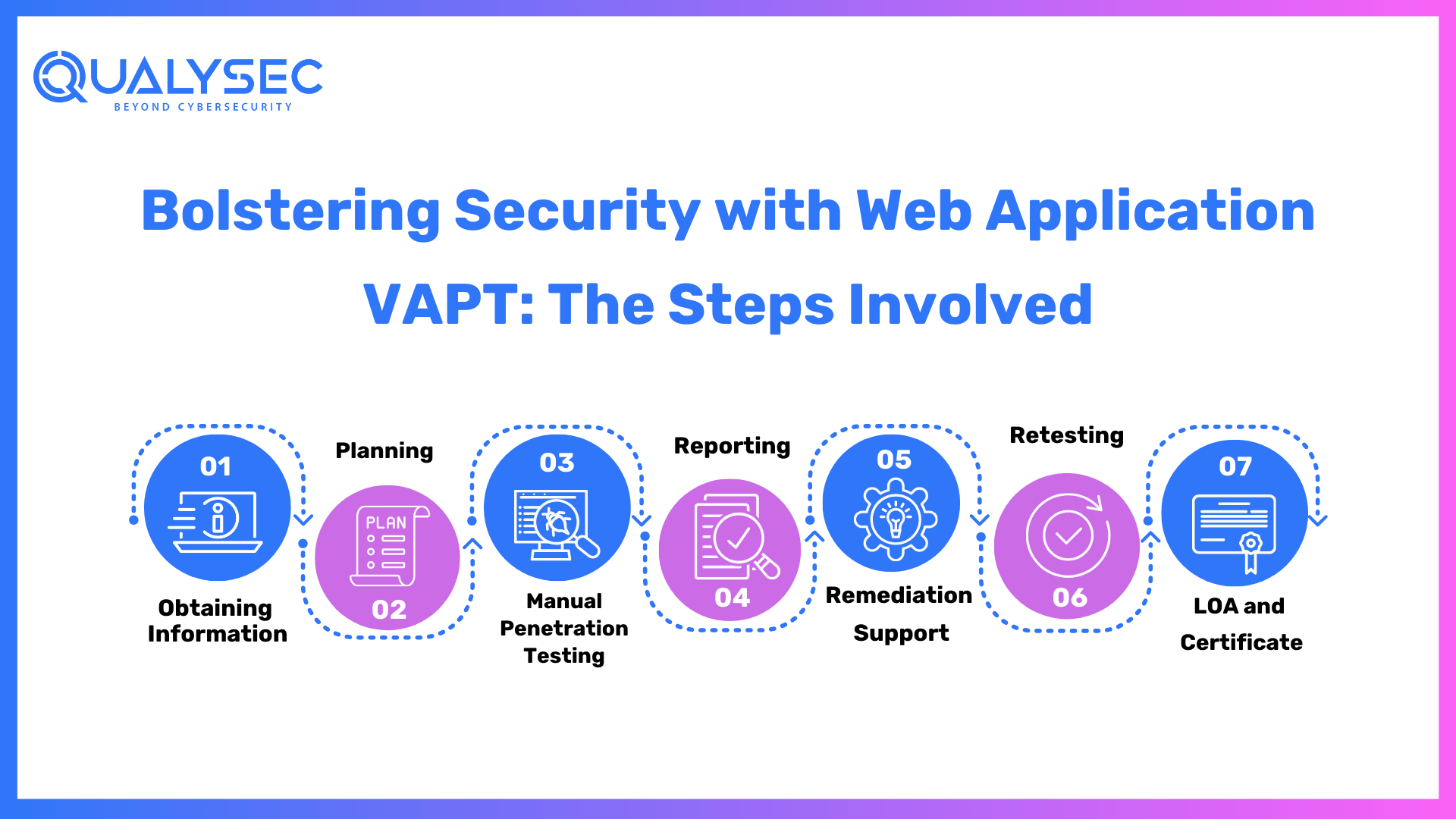
Penetration testing businesses are frequently used by organizations to evaluate their infrastructure for vulnerabilities. These service providers have a defined procedure for doing penetration testing on the specified application or network. Here’s a rundown of the entire procedure:
1. Obtaining Information:
The first step in penetration testing is to collect as much data as possible. This entails a two-pronged approach: using easily accessible information from your end, as well as leveraging a variety of methods and tools to obtain technical and functional insights. Understanding user roles, permissions, and data flows is essential for developing a successful testing approach.
2. Planning
The penetration testing company starts by carefully establishing the objectives and goals. They probe deeply into the application’s technical and functional complexity. Furthermore, this thorough research enables testers to modify their testing method to target certain vulnerabilities and threats in the application.
A thorough penetration testing strategy is developed, describing the scope, methodology, and testing criteria. Furthermore, the business provides a high-level checklist to help guide the testing process. They gather and prepare the necessary files and testing equipment. To guarantee a smooth and effective assessment, this process comprises creating testing parameters and validating script availability.
3. Manual Penetration Testing
We offer a comprehensive selection of deep manual penetration testing services that are tailored to your specific requirements and security standards. Furthermore, this one-of-a-kind method allows for a thorough examination of potential vulnerabilities in web applications. This online VAPT test performs a systematic review of online applications, probing for flaws in authentication, data management, and other critical areas to enhance the application’s security posture.
4. Reporting
The testing team detects and categorizes vulnerabilities found throughout the examination, ensuring that possible hazards are identified. A senior consultant conducts a high-level penetration test and thoroughly evaluates the result.
This assures the greatest degree of quality in testing methodologies as well as reporting accuracy. This detailed documentation is a helpful resource for understanding the application’s security condition.
This thorough reporting mechanism guarantees that clients and developers obtain relevant insights into the application’s security status as well as practical advice for maintaining a strong security posture.
Want to see how a detailed report can ensure the security of your application? Download a copy of our sample report here!
Latest Penetration Testing Report

5. Remediation Support
If the development team requires assistance in replicating or mitigating identified vulnerabilities, the service provider provides a vital service via consultation calls. Furthermore, penetration testers with an in-depth understanding of the detected vulnerabilities encourage direct participation to assist the development team in efficiently assessing and responding to security concerns. This collaborative approach guarantees that the development team receives competent guidance, enabling the smooth and rapid resolution of vulnerabilities to improve the application’s overall security posture.
6. Retesting
Following the development team’s completion of vulnerability mitigation, a critical stage of retesting occurs. Our staff conducts a thorough assessment to ensure that the therapies are effective. The final report is long and covers the following sections:
- History of Discoveries
- State of Assessment
- Screenshots
7. LOA and Certificate
The testing business goes beyond by giving a vital document called a Letter of Attestation. Furthermore, this letter backs up findings from penetration testing and security assessments and serves several functions:
- Confirmation of Security Level
- Providing Stakeholders with Security
- Compliance Completion
In addition, the testing organization will give you a Security Certificate, which will improve your capacity to represent a safe environment, boost confidence, and satisfy the demands of many stakeholders in today’s evolving cybersecurity scene.
Did You Know?
You can also make QualySec’s Pentest Certificate publicly verifiable, allowing your clients and partners to validate it. It aids in the establishment of openness and trust for your company.
Want to hire a web VAPT testing company, but don’t know how to? Click here to learn about it.
Unveiling the Essence: Desktop Application VAPT
Desktop Application Vulnerability Assessment and Penetration Testing (Desktop App VAPT) is a sophisticated cybersecurity methodology that focuses on discovering and addressing vulnerabilities in desktop software applications. These apps, as opposed to web applications, which are accessed through browsers, are installed and operate directly on users’ PCs. Desktop App VAPT is critical for guaranteeing the security of these locally executed programs and preventing malicious actors from exploiting them.
Beyond the Web: Desktop Application VAPT Unveiled
Web and Desktop seem very similar. But, there are some differences beyond their similarities. Here are some of the differences and similarities between web and desktop app VAPT:
Differences:
- Access Points: Web apps are accessed via browsers, frequently over the internet, whereas desktop programs operate locally on a user’s PC.
- Attack Surface: Web applications contain a variety of attack surfaces, such as input fields and server interfaces, whereas desktop apps may have vulnerabilities linked to local data storage, API usage, and software interactions.
- Deployment: Web applications are installed on servers with centralized updates, but desktop apps may require manual upgrades on each user’s PC.
Similarities:
- Code Vulnerabilities: Injection attacks, unsecured data storage, and poor input validation are all examples of typical code vulnerabilities that may affect both web and desktop programs.
- Authentication and Authorization: To provide safe access controls, similar authentication and authorization concepts apply to both types of applications.
- Data Protection: Both types of applications require sophisticated data protection mechanisms to ensure the confidentiality and integrity of sensitive data.
Related: Read more about the Difference between Security testing and Penetration testing
Mastering the Web: The Role of Web App VAPT
Security flaws in any online application may reveal a wealth of sensitive information. Thus, data safety and security of crucial and sensitive company data are critical. The VAPT test aids in the analysis of risks and the assessment of possible damage. VAPT assists in analyzing the present security of the web application by relentlessly testing the program’s defenses and determining where they may potentially fail.
Furthermore, it is a process of continual development in which organizations may analyze and strengthen security to decrease possible dangers. Code Vulnerability is an important tool for detecting cyber threats and ensuring that the code is threat-free is critical. The following are the primary actions carried out:
- Code Vulnerability Analysis
- VAPT & Vulnerability Compliance Audit
Conclusion: Elevating Security with Web App VAPT
VAPT is an essential component of a company’s cybersecurity strategy. It aids in the detection and remediation of vulnerabilities before they can be exploited, offering useful insights to improve security defenses. Organizations may reduce possible risks, secure sensitive data, and maintain a strong security posture in the face of ever-changing cyber threats by undertaking frequent VAPT evaluations.
In this digital age, when information security is critical, web application testing has become a key method for strengthening defenses and encouraging user attention. It is about safeguarding the confidence and trust of everyone who comes into contact with them, not merely shutting up shipments.
QualySec plays a critical role in enhancing online application security. We conduct web VAPT on applications and desktops to uncover and resolve any vulnerabilities, drawing on considerable VAPT experience.
In addition, we provide specific security solutions via process-based penetration testing. A one-of-a-kind process that employs a Hybrid testing strategy and a professional team with extensive testing expertise to ensure that the app meets the industry’s highest standards.
In addition, our pentesting services include a full range of automated vulnerability scanning and manual testing using in-house and commercial tools like Burp Suite and Metasploit. We actively assist firms in successfully negotiating difficult regulatory compliance settings such as GDPR, SOC2, ISO 27001, and HIPAA.
We assist developers in resolving vulnerabilities by delivering comprehensive and developer-friendly pentesting findings. Furthermore, this report includes all of the insights, beginning with the location of the discovered vulnerabilities and ending with a reference on how to resolve them, i.e., you get a detailed step-by-step report on how to resolve a vulnerability.
Frequently Asked Questions
What is the difference between Vulnerability Assessment and Penetration Testing?
A vulnerability scan is a high-level automated test that detects and reports possible vulnerabilities. Furthermore, a penetration test is a hands-on inspection conducted by a real person to find and exploit holes in your system.
Why is VAPT essential for my organization’s cybersecurity strategy?
VAPT web application assists in identifying vulnerabilities that might be exploited to obtain unauthorized access to Systems, hence strengthening the overall security. To begin the road of VAPT implementation, enterprises should work with cybersecurity firms that specialize in this area.
How often should a company conduct VAPT on its web applications?
As a general guideline, you should do vulnerability testing on your network and apps at least twice a year. This will enhance the security of your digital assets and overall IT infrastructure.
Can VAPT be performed in-house, or is it better to hire external experts?
Relying entirely on an in-house security staff to handle network and digital asset protection is insufficient. To detect internal and external threats, organizations must engage external teams that use a combination of automated and manual testing methodologies. Furthermore, external pentesters’ final report assists firms in correcting faults and improving their overall security posture.
What types of vulnerabilities does VAPT typically uncover?
Network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities are the four major categories of vulnerabilities in information security. VAPT testing helps uncover all these vulnerabilities.

















































































































































































































































































































































0 Comments