Businesses are facing greater cyber dangers than ever before in today’s digital economy. With data breaches and cyber-attacks becoming more widespread, businesses of all sizes must take precautions to safeguard their assets and reputations.
Investing in VAPT services is one of the most effective and finest methods to do this. Furthermore, it is a complete cybersecurity methodology that involves vulnerability evaluation and penetration testing.
Today’s article will discuss the significance of VAPT for organizations and how it may assist in securing your web and mobile applications. So, let’s get started.
Understanding Vulnerability Assessment
Vulnerability assessment is an approach to finding security flaws and possible threats in online and mobile apps. It entails examining code, settings, and infrastructure for vulnerabilities like SQL injection, cross-site scripting, and misconfigurations that hostile actors might exploit. Additionally, the scope includes a thorough examination, which includes source code inspection, network scanning, and application testing.
Importance:
Vulnerability analysis is critical for improving application security. It assists enterprises in proactively identifying and correcting vulnerabilities before hackers may exploit them. This proactive strategy decreases the chance of data breaches, financial losses, and reputational harm to a business. Regular evaluations also help to ensure compliance with industry norms and standards, resulting in a more secure digital environment.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
The Role of Penetration Testing
Penetration testing on mobile application and web application, often known as ethical hacking, is the methodical process of identifying security flaws in an organization’s computer systems, networks, and applications. Its goal is to uncover vulnerabilities that criminal hackers may exploit, therefore assisting enterprises in strengthening their cybersecurity defenses.
Importance:
- Penetration testing evaluates an organization’s security posture, finding weaknesses that might lead to data leaks and cyberattacks.
- Penetration testing reduces the risk of data loss and financial harm by proactively finding and correcting vulnerabilities.
- To achieve compliance with security requirements, many businesses and laws need frequent penetration testing.
- Building confidence with consumers and stakeholders requires demonstrating a commitment to security through penetration testing.
- Routine testing fosters a culture of security improvement and awareness
Benefits of VAPT for Web and Mobile Apps
VAPT is beneficial in many ways when done right with the help of a professional cybersecurity company or pen tester. Take a look at the top advantages of performing VAPT for mobile and web applications:
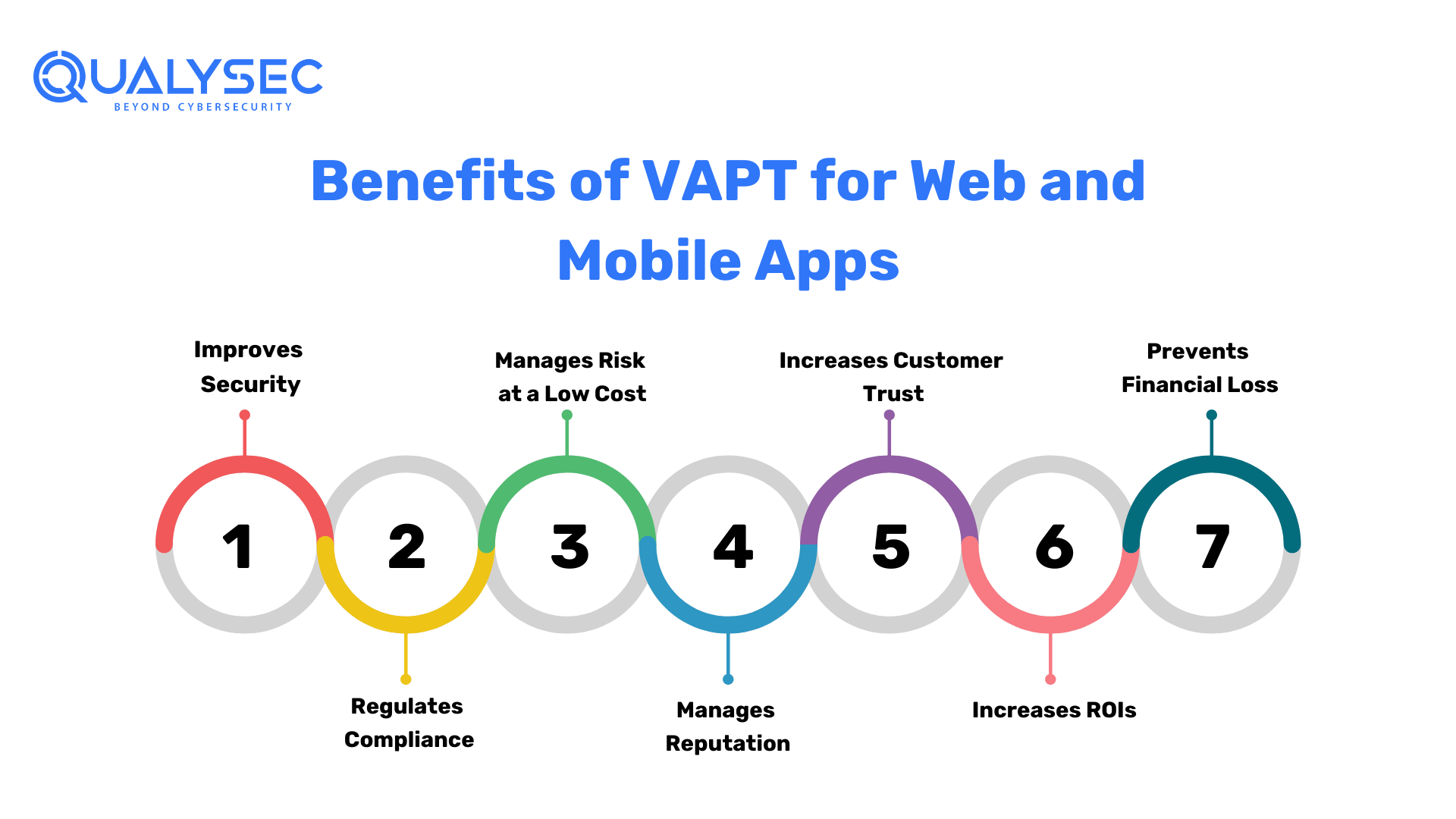
- Improves Security
Vulnerability Assessment and Penetration Testing on web application and mobile application (VAPT) improves the security of online and mobile apps dramatically. VAPT helps avoid prospective assaults and data breaches by finding and fixing vulnerabilities such as weak authentication, unpatched software, or insecure setups. It is a preventative security mechanism that strengthens the app’s defenses against developing threats.
- Regulates Compliance
VAPT is essential for assuring compliance with data protection rules and industry standards. Many regulations, such as GDPR and HIPAA, require enterprises to keep customer data secure and private. VAPT assists businesses in meeting these compliance obligations by discovering and correcting security problems that might result in legal ramifications.
- Manages Risk at a Low Cost
VAPT provides a low-cost solution to risk management. Organizations may limit possible risks before they escalate into costly security breaches by detecting vulnerabilities early in the development process. VAPT is a reasonable investment since the cost of prevention is considerably cheaper than the cost of recovery following a breach.
- Manages Reputation
A security breach may destroy a company’s reputation, resulting in customer turnover and unfavorable press. Customers’ confidence and loyalty typically erode in organizations that suffer data breaches. Proactive methods, such as rigorous web application security testing, are required to discover and eliminate vulnerabilities before they are exploited by bad actors.
- Increases Customer Trust
Prioritizing web application security testing is an effective strategy to establish and maintain client confidence. 80% of customers are more willing to buy from firms that they believe would secure their data. Additionally, addressing security flaws proactively displays a commitment to protecting consumer information and generating trust, loyalty, and a favorable brand impression.
- Increases ROIs
With the use of timely vulnerability assessments, an organization may prioritize which vulnerabilities to target first depending on the damage they might do to a system. Making a major investment in high-quality equipment and qualified staff today may greatly boost an organization’s long-term advantages. This may also assist a company in gaining new clients and consumers.
- Prevents Financial Loss
Preventing security breaches in advance can save firms from major financial damages. Organizational cybercrime expenditures climbed to an average of $17.4 million in 2023, including spending for cleanup, legal proceedings, reputational harm, and prospective litigation. Furthermore, organizations can decrease their exposure to financial risks and potential cybercrime-related charges by investing in comprehensive web application security testing.
VAPT Process for Web and Mobile Applications
Here is the step-by-step guide to the process of VAPT testing containing all the phases of how the testing is done:
-
Pre-Assessment
During the pre-assessment phase, the testing team sets the scope and goals of the test. They work with the app’s owner or developer to comprehend the app’s goals, functionalities, and potential hazards. This stage involves planning and logistics, such as defining the testing environment, setting rules of engagement, and obtaining the necessary approvals and credentials to carry out the test.
-
Information Gathering
The testing business recommends starting the testing procedure in a simple way. Begin by utilizing the provided link to submit an inquiry, which will connect you with skilled cybersecurity experts.
They will guide you through the process of filling out a pre-assessment questionnaire, which will include both technical and non-technical aspects of your intended mobile application. Testers organize a virtual presentation meeting to discuss the evaluation strategy, tools, timeline, and anticipated costs.
They then scheduled the signing of a nondisclosure agreement (NDA) and service agreement to ensure stringent data privacy. After gathering the relevant information, penetration testing will commence to ensure the security of your mobile app.
-
Penetration Testing
During the penetration testing process, the testing team actively looks to exploit vulnerabilities and security issues in the mobile app. This phase consists of a series of simulated attacks and defect detection examinations. Testers can score the authentication methods, data storage, data transit, session management, and connectivity with external services of the application or infrastructure. Furthermore, a tester’s typical penetration testing approaches include source code analysis, dynamic analysis, reverse engineering, manual testing, and automated testing.
Want to read more about Penetration Testing? Click here!
-
Analysis
The severity of each discovery is evaluated independently, and those with higher ratings have a bigger technical and commercial impact with fewer dependencies.
Likelihood Determination: The evaluation team assigns a probability of exploitation to each vulnerability based on the following criteria:
- The motivation and capability of the potential threat source
- The characteristics of the vulnerability
- The presence and efficacy of countermeasures
- If you need physical access to a device and/or a jailbreak.
Impact Analysis: The web and mobile application security assessment team investigates and evaluates the impact of the exploit on the organization and its customers in terms of confidentiality, integrity, and availability for each vulnerability that might be exploited efficiently.
Severity Determination: The severity ratings are given by the pen testing business based on internal expertise as well as commonly used rating methods such as the Open Web Application Security Project (OWASP) and the Common Vulnerability Scoring System (CVSS). Each discovery’s severity is determined independently of the severity of other discoveries. Higher-severity vulnerabilities have a greater technical and business impact and are less dependent on other issues.
-
Reporting
Only if the results of the security tester are adequately documented will they be relevant to the client. A good report should contain, but it doesn’t limit to, the following details:
- A succinct explanation
- A description of the scope and context (for example, targeted systems).
- Techniques made use of information sources (provided by the customer or discovered during the pentest).
- Results that have been prioritized (for example, vulnerabilities organized using the DREAD category)
- Comprehensive fix advice for each fault
Click here to get a free report sample and learn more about it!
-
Remediation
The last stage involves dealing with the discovered flaws and vulnerabilities. The mobile app developer or owner follows the recommendations in the report and works on remedial methods to improve the app’s security. This stage may also entail retesting to check that the detected weaknesses found at the time of web and mobile app vulnerability assessment have been addressed and the app has become more secure. The goal is to reduce the app’s vulnerability to security threats while still preserving user data.
-
Consulting & Support
The testing team conducts consultation calls on a regular basis to guarantee that discovered vulnerabilities are effectively fixed. The security professionals evaluate the results and give advice on how to address and fix the concerns during this session. This hands-on assistance is critical for your development team to apply the essential changes as soon as feasible.
-
Certification
To confirm the security measures implemented, penetration testing businesses issue a letter of attestation as well as a security certificate. These papers attest to the fact that your application has been extensively tested and that all necessary security measures have been implemented.
Choosing the Right VAPT Service Provider
The most important aspects to consider when choosing a VAPT service provider are qualifications, experience, and cost. Let us go over them one by one:
-
Experience
When selecting a pen testing company, consider the level of experience. The more VAPT testing a company conducts, the better it grows at detecting a wide range of security problems. Because not every testing company is familiar with every technology, you may need to be adaptable as well. Instead of looking for a company with considerable experience, look for someone who knows how to do VAPT testing on the technology that your organization utilizes.
-
Certification
This is the most crucial factor for firms to consider when hiring pen testers since it demonstrates that the service provider is trustworthy. You should be certain that the tester is accredited by a respected organization. Furthermore, you should conduct thorough research on the company because CREST provides both corporate-level and individual credentials. Inquire about the tester who will be working on the job to ensure they have the necessary credentials and expertise.
-
Price
Businesses frequently inquire about the cost of VAPT testing services. Unfortunately, estimating the cost of pen testing is problematic since it is dependent on the size and complexity of a company’s IT infrastructure. As a result, the majority of VAPT-testing firms charge on a sliding scale. Choose a service provider that charges a reasonable fee for its services. However, keep in mind that qualifications and experience come first.
-
Procedures for Extensive Testing
Examine whether the service supplier uses extensive testing methodologies. A trustworthy service will conduct a thorough evaluation that involves both automatic and manual testing procedures. They should be able to mimic real-world assaults and be knowledgeable about the most recent vulnerabilities and attack routes.
-
Compliance
It is critical to choose a VAPT testing business that adheres to industry norms and regulations. The business should be knowledgeable with compliance standards such as GDPR, HIPAA, PCI DSS, and other comparable frameworks, depending on your sector. This assures that the VAPT testing technique meets legal and regulatory requirements, decreasing legal and financial risks.
-
Service and Support
Take a look at the testing company’s offerings. Consider their proficiency in a variety of testing approaches for your web application and mobile app testing needs. In addition, evaluate their availability and response to providing support both throughout and after the testing procedure. A dependable and responsive staff can help you resolve vulnerabilities quickly and guide you through the remedy process.
-
Reports
The precision with which penetration testing results are obtained is critical in determining your organization’s security posture. Look for a company that provides a detailed and easy-to-understand daily report on transparency. These reports should include information regarding vulnerabilities detected, their severity, and repair recommendations. Clear and actionable reports help your firm successfully resolve security issues, thus enhancing your overall cybersecurity posture. You can obtain security certificates as proof that the software is safe.
Why Choose QualySec for VAPT?
Look no further than QualySec Technologies for safeguarding digital assets and ensuring the greatest degree of security for your firm. QualySec is proud to be the leading VAPT Testing services provider for good reason. Among our services are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI ML Pen testing
The highly experienced and trained cybersecurity professionals at QualySec are dedicated to strengthening your defenses. We give comprehensive reports that not only detect vulnerabilities but also make actionable suggestions to improve your security.
Our competent support is always ready to assist you in resolving security issues and giving ongoing assistance. The commitment of QualySec to seamless collaboration with your development teams guarantees that issues are resolved quickly.
We employ cutting-edge tools and methodologies to pinpoint vulnerabilities while avoiding false positives. QualySec goes above and above by providing a Letter of Attestation, which certifies your security level, displays your commitment to strong cybersecurity, and satisfies regulatory obligations.
At QualySec Technologies, we prioritize your peace of mind, and our track record as the best VAPT company speaks volumes about our commitment to your digital security. For solid security, go with QualySec.
Latest Penetration Testing Report

Conclusion
Technology contributes to the improvement of company processes and goals by fostering a more efficient and productive work environment. However, technology may also impede an organization’s ability to achieve its objectives.
If you don’t control important business systems and applications, it can harm the organization’s infrastructure. VAPT promotes a healthy ecosystem by finding and correcting vulnerabilities that might cause significant harm, resulting in legal, financial, and reputational ramifications for your business operations.
This post has demonstrated the value VAPT offers to a business by setting out its top benefits. Furthermore, you may now simply discuss and justify to stakeholders and project teams why this area of security is critical to achieving common objectives.
Reach us to get a professional roadmap of VAPT to safeguard any digital asset of your company infrastructure and save your business from weaknesses and losses. We hope we have shed light on the requirements you searched about VAPT.
FAQs
What are the benefits of web application security assessment?
Web application security testing assists in identifying and mitigating vulnerabilities, hence protecting against cyber-attacks. It improves overall system integrity, safeguards sensitive data, and builds user trust by providing strong protection against prospective threats.
What is web application vulnerability assessment?
Web application vulnerability assessment entails scanning and analyzing web applications in order to find and resolve security flaws. It seeks to identify potential entry points for cyber threats such as SQL injection, cross-site scripting, and other vulnerabilities in order to improve overall application security.
What is the role of vulnerability assessment in cybersecurity?
Vulnerability assessment is critical in cybersecurity because it proactively identifies and addresses gaps in systems and applications. It assists enterprises in fortifying their defense systems, reducing the danger of exploitation, and maintaining a robust cybersecurity posture.
What is needed for vulnerability assessment?
A vulnerability assessment requires specialized scanning equipment, competent staff to evaluate data, and a thorough understanding of the target system. For efficient vulnerability assessment in cybersecurity, regular updates, communication among security teams, and adherence to best practices are required.























































































































































































































































































































































0 Comments