As the threat landscape continues, protecting payment card information should be a priority for any organization. The Payment Card Industry Data Security Standard (PCI DSS) outlines the best practices for protecting cardholder data and provides practical solutions to mitigate risks of data breaches. Therefore, complying with PCI DSS Compliance is a means to increase an organization’s protection against cyber threats and can also be a tool to gain clients’ trust and continued patronage.
Hence, the blog briefly overviews PCI DSS compliance, explains its necessity, outlines its requirements, and details its implementations.
What is PCI DSS?
Payment Card Industry Data Security Standard (PCI DSS) is a recognized policy and regulation for the security of credit, debit, and cash card-based transactions to minimize the misuse of cardholders’ identities. Furthermore, PCI DSS has been developed to assist organizations that process payment card data to avoid cyber incidences with sensitive information.
In addition, it is important to note that PCI DSS is not a law or a legal regulation requirement. However, it is frequently included in contracts that businesses that process and store credit, debit, and other payment card transactions agree to. Any organization legally bound by contract to operate their business must adhere to the compliance laws stipulated by the PCI DSS standards to create the necessary security for the clients.
PCI DSS was created in 2004 by five major credit card companies: VISA, MasterCard, Discover, JCB, and American Express. Additionally, its standards were established by the Payment Card Industry Security Standards Council (PCI SSC).
What is PCI DSS compliance?
PCI DSS compliance refers to ensuring that an organization implements the specifications given by the PCI DSS for the protection of cardholder data and a secure payment process. Any organization dealing with credit card data must ensure proper control mechanisms and procedures are in place to meet the standards.
The concept of PCI DSS compliance, therefore, requires constant testing of the organization’s security measures, protection management of the vulnerabilities, and adoption of better measures. Hence, consequences of non-compliance include legal penalties, legal liabilities, and harm to an organization’s reputation.
What are the PCI DSS Requirements?
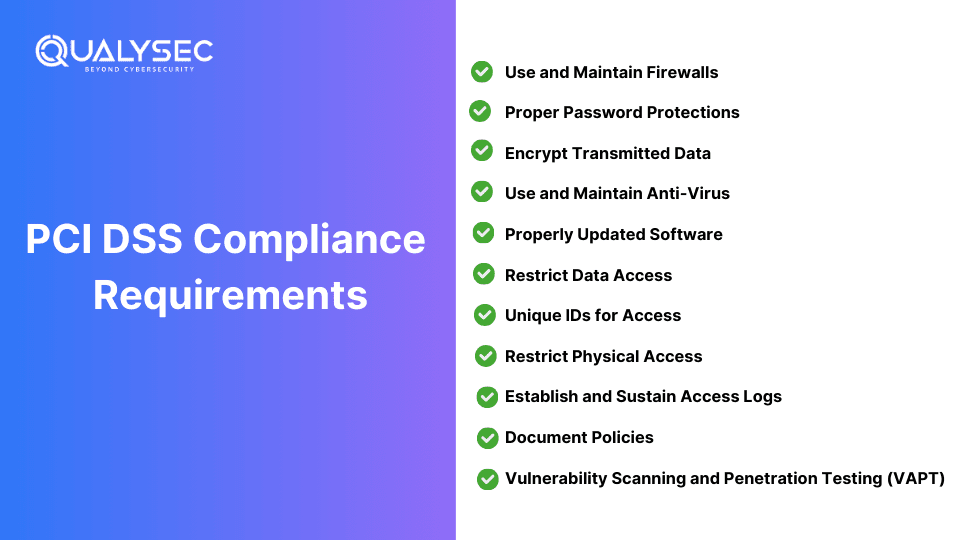
1. Use and Maintain Firewalls
Firewalls mainly prevent foreign or unknown entities from gaining access to private data. This prevention system acts as the initial barrier against hackers. Hence, firewalls are among the top PCI DSS requirements because they help minimize unauthorized access.
2. Proper Password Protections
Third-party products such as routers, modems, point of sale (POS) secure systems, etc., use generic passwords and security that can be easily found online. Measures of compliance in this area include a list of all devices and software that need a strong password.
3. Encrypt Transmitted Data
Cardholder information is transmitted through numerous regular channels (payment processors, home office, local stores, etc.). Such data must be encrypted each time it is transmitted to those known destinations. Additionally, never send account numbers to unknown locations.
4. Use and Maintain Anti-Virus
Anti-virus software should be used alongside the compliance steps for the payment card industry data security standard (PCI DSS). However, anti-virus is mandatory for all devices that process or store PAN information. This software should be periodically patched and updated. The POS provider should also incorporate anti-virus measures where it cannot be installed directly.
5. Properly Updated Software
Firewalls and anti-virus software will need upgrades many times. It is also beneficial to upgrade every application in a company. Updates of most software products contain additional layers of security, including patches that fix newfound exploits, for instance.
6. Restrict Data Access
The cardholder data has to be kept confidential, and there is a need-to-know basis only, which means that any employee from the company and any third party who is not authorized does not need to access this data. The roles requiring sensitive data should be clearly defined and updated periodically, if necessary — as per the PCI DSS guidelines.
7. Unique IDs for Access
Persons who must access card data should have their unique identification to access the data. For example, there should not be a single access to the encrypted data with several people aware of the account details. Unique IDs reduce vulnerability and provide a faster response in the event of a data breach.
8. Restrict Physical Access
Any cardholder data must be stored in a physically secure environment. Any written or typed data, as well as the data stored on a hard drive, should be stored in a locked room, a drawer, or a cabinet. Documented every instance of accessing time-sensitive data to meet the PCI DSS compliance requirements.
9. Establish and Sustain Access Logs
Any action that involves cardholder data and primary account numbers (PAN) must be recorded in a log. To meet compliance standards, it is necessary to describe the procedure through which data enters the organization and the frequency of requiring access.
10. Document Policies
A list of equipment, software, and any human resources that have access will be required to be prepared for attestation of compliance. Documentation will also be necessary for the logs of accessing cardholder data. Describe how your company manages information as it enters, how it is processed, and how you use the information after the point of sale.
11. Vulnerability Scanning and Penetration Testing (VAPT)
Applications, networks, the cloud, APIs, etc. are always vulnerable to cyberattacks. If one of these is hacked, they could also steal the payment card information. By conducting vulnerability scanning and penetration testing (VAPT), you can identify and fix security weaknesses that could lead to data breaches.
Speak with our experts for VAPT services and PCI DSS compliance requirements. To make a call, click on the box below!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
What are the Steps to Achieve PCI DSS Compliance?
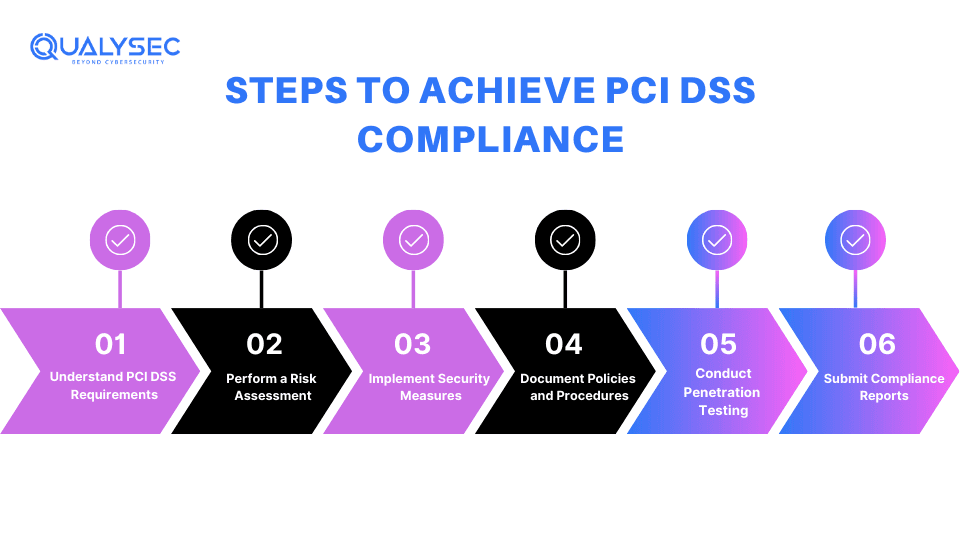
There are several important steps to PCI DSS compliance· Here’s a streamlined approach:
1. Understand PCI DSS Requirements
Familiarize yourself with the PCI DSS standards and requirements relevant to your company’s activities. This includes reading through the PCI DSS document and identifying how every requirement applies within the organization.
2. Perform a Risk Assessment
Start with a comprehensive security audit to recognize all the possible risks and weaknesses of the existing security framework. It aids in determining which sectors need enhancement to conform to the compliance specifications.
3. Implement Security Measures
Apply security measures to protect cardholder data. This involves securing data and the network through encryption and configuring the network settings and access.
4. Document Policies and Procedures
It is essential to create and update records of your security policies, procedures, and controls. This documentation should present information about your organization’s compliance with the PCI DSS requirements.
5. Conduct Penetration Testing
Conduct penetration testing and vulnerability scans to check the efficiency of your security measures. PCI DSS compliance requires conducting security testing on the systems to detect and fix vulnerabilities and penetration testing is the best way to do this.
6. Submit Compliance Reports
After completing the testing and remediating, prepare the compliance reports on the necessary payment card networks. Some of these are the Self-Assessment Questionnaire (SAQ) or the Report on Compliance (ROC), depending on the degree of compliance of your business.
Best Practices for PCI DSS Compliance
1. Strong Password Policies
Promote strong password practices that include using hard passwords and the need to change them frequently.
2. Encryption and Masking
To secure cardholder information, encrypt the data when transferring and storing. Implement data masking to reduce disclosure of sensitive information to authorized users only.
3. Access Controls
Control cardholder data access so that only the workers who need this data to perform their jobs can access it. Use the combination of unique identifiers and give user access based on defined client roles to keep data secure.
4. Regular Security Testing
Continuously perform vulnerability assessment, penetration testing, and security auditing to expose any security risks and ensure thorough security testing.
Tools and Resources for PCI DSS Compliance
Several tools and resources can help organizations achieve and maintain PCI DSS compliance:
- Qualified Security Assessors (QSAs): Always engage certified QSAs who will conduct structured PCI DSS evaluations and offer profound advice.
- Self-Assessment Questionnaires (SAQs): Companies with less complex structures can assess compliance using SAQs.
- PCI DSS Documentation Templates: Create security policies, procedures, and compliance documents using templates.
- Security Information and Event Management (SIEM) Solutions: Update and integrate SIEM tools to address security incidents, such as tracking, logging, and analysis.
- Vulnerability Scanning Tools: Nessus, Qualys, and OpenVAS are common vulnerability scanners for regular scans of networks and systems.
PCI DSS compliance checklist
1. Secure Network Configuration
Confirm that a firewall and network segmentation shield all systems that process payment card information to separate the cardholder data from other networks. Update firewall rules and configurations occasionally to meet current requirements.
2. Encryption and Protection of Cardholder Data
Employ proper encryption algorithms such as advanced encryption standard 256 (AES-256) in handling cardholder data, whether stored or in Transmission. Therefore, to ensure sure security of sensitive information such as the PAN (Primary Account Number) it should be masked.
3. Regular Security Testing and Vulnerability Scanning
Continuous scanning for vulnerabilities and penetration tests to determine and remediate risks. Make sure that a third-party PCI compliance company does the testing and that they follow the current PCI DSS guidelines.
4. Access Controls and Authentication
Restrict access to cardholder data by enforcing the following access controls at the network and system level. Implement multi-factor authentication (MFA) when dealing with systems that process, store, or transmit payment card data and provide detailed records of the users’ activity.
Conclusion
Maintaining PCI DSS compliance is important for companies that process credit cards to avoid penalties and legal repercussions. Compliance with the PCI DSS regulation, adoption of recommended measures, and use of proper tools make it possible to protect cardholder information, minimize the threat of breaches, and maintain customer confidence.
Moreover, compliance is not a one-time approach but a continuous process that requires effort and commitment. Therefore, this strong approach to compliance with PCI DSS will help organizations achieve payment security and contribute to a safer payment environment.
FAQs
1. Is PCI compliance legally required?
A. PCI compliance is compulsory for any company that accepts, stores or transmits credit card information as per the major credit card companies, including Visa and MasterCard.
2. Who needs to comply with the PCI DSS?
A. PCI DSS applies in every organization that detects, processes, stores, or transmits credit card details irrespective of the size or the volume of transactions.
3. How do you maintain PCI DSS compliance?
A. Ensure adherence to PCI DSS by conducting security assessments, having strict access control procedures, constantly monitoring the network, performing vulnerability scans, meeting the PCI DSS requirements, and conducting annual self-assessments or third-party assessments.
4. Who provides PCI DSS certification?
A. Qualified Security Assessors (QSAs) and Approved Scanning Vendors (ASVs) accredited by the Payment Card Industry Security Standards Council (PCI SSC) offer PCI DSS certificates by conducting the assessments.
5. What companies offer PCI compliance?
A. Some of the companies that offer PCI compliance are:
- Qualysec Technologies
- Rapid7
- Coalfire















































































































































































































































































































































0 Comments