With growing digitalization, you are responsible for safeguarding all of your important information. Your cybersecurity must be frequently and systematically assessed. Find out how important network security testing is to protecting your company.
Network security testing is a procedure that identifies security vulnerabilities and flaws in a network. It can encompass several network devices and applications, as well as direct communication with customers, other organizations, and government agencies. Frequent network security testing uncovers vulnerabilities and enables owners to take preventative and remedial action to improve cybersecurity.
Network security protects a large, interconnected technological network from cyberattacks. All businesses, no matter how big or little, depend on strong networks to send, receive, or retain private data. However, there is now more concern regarding data integrity and confidentiality due to the rise of increasingly sophisticated cyberattacks. Network security testing has become essential due to growing concerns about online threats.
Importance of Network Security Testing
Security testing guarantees that the system is safe from malware, attackers, and other online threats. The system examines all security-related requirements to attain this level of protection. Network security testing ensures there are no security vulnerabilities in the database, computer, system, or application.
It is important to remember that security testing is a crucial component of software testing. Numerous security flaws in applications can lead to a complete loss of data, income, reputation, and clients. The primary goal of security testers is to identify program threats by monitoring different attack strategies. To counter any danger and prevent damaging exploits by cybercriminals, it is crucial to comprehend the fundamentals of security testing, various tools, and methodologies, as well as when and how to employ them in various cases.
Read the related blog on Network Penetration Testing
Impacts of Security Breaches
security breaches can result in lost business and damage the company’s credibility. Database corruption and destruction can result from breaches. Regulatory and compliance implications can originate from data breaches. Security breaches can also have a big effect on people, leading to identity theft and privacy loss in certain situations.
Different Types of Network Security Testing
Vulnerability assessment and penetration testing are the two primary methods for verifying network security. These two methods complement each other.
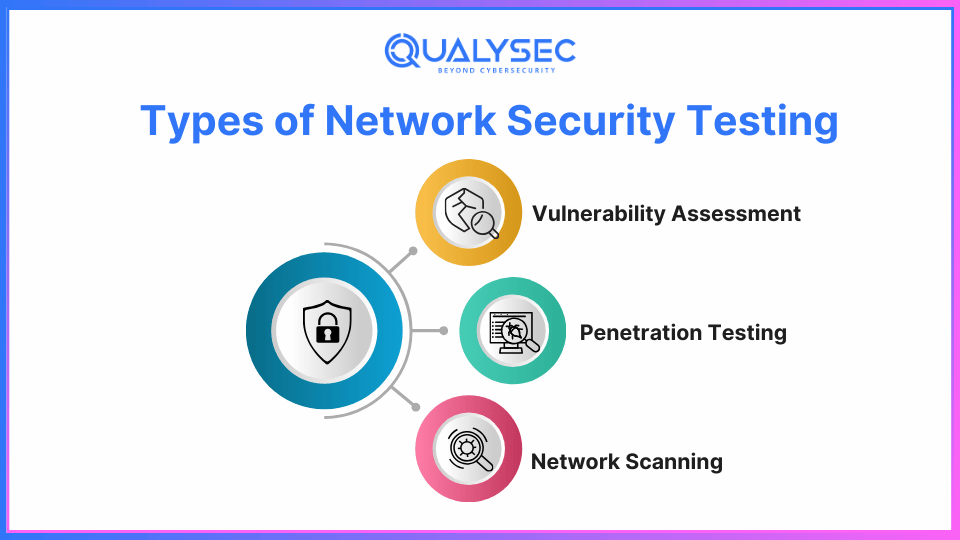
1. Vulnerability Assessment:
A vulnerability assessment involves a set of security tests on your business. They examine the security of your network from every perspective. Often performed by automated technologies that generate a report highlighting potential weak points in your network. This type of scan finds important issues and suggests ways to secure the network. It enables you to have a positive view of the organization’s network, which can assist you in properly focusing the efforts of your staff.
2. Penetration Testing:
Penetration testing is a thorough way to audit a network, going beyond a simple vulnerability check to take a closer look at a system’s security. It uses advanced tools and automated techniques to spot potential threats.
Penetration testing and vulnerability assessments work together to keep networks secure and manage risks. Often referred to as Vulnerability Assessment and Penetration Testing (VAPT), this process helps find any weak points or risks in a network. It’s a must for businesses that can’t afford to put their network or digital assets at risk. Companies with experience in penetration testing and cybersecurity do VAPT testing to help protect these critical resources.
3. Network scanning and mapping:
These are crucial techniques for network security since they assist in locating and fixing network vulnerabilities.
- Network mapping: facilitates comprehension of the actual physical links among networked devices. It may be used to locate active systems, which is crucial for network security and keeping track of assets. Network maps can be made automatically with software or by hand.
- Network Scanning: Identifies the hosts currently present on a network, as well as their IP addresses. Additionally, it can be used to find vulnerable ports that hackers might exploit to enter the network.
Download a copy of our network pen testing sample report right here for free !
Latest Penetration Testing Report

Key Techniques in Network Security Testing
The word “network security” encompasses a wide range of techniques and approaches. We’ll go over a few of such strategies in brief.
1. Testing for White Box Security:
The term “white box” describes a security testing technique where the testers are familiar with the system’s operation. In order to determine whether the code execution complies with the planned design, they look at controller flow, the movement of data, code application, and error resolution.
2. Testing for Black Box Security:
Black box testing is a type of testing where the testers are not aware of confidential network information. This testing procedure represents an actual attack. Black box testing is useful for investigating deployment problems and server setup errors.
3. Testing for Grey Box Security:
The White Box and Black Box techniques for network security testing are combined in the Grey Box method. The testers use restricted data, including login passwords, during this process. Knowing how much access a privileged person has and how much harm a hacker with similar privileges can do is made easier with the help of these tests.
Our experts at Qualysec have helped secure fintech, SaaS, and enterprise systems across 25+ countries. Manual + Automated Pentesting. No false positives. Actionable reports.

Manual Testing vs. Automated Tools
The most important difference between automation and manual testing is who runs the test case. Manual testing is carried out by a human tester. It is done by the tool in automation testing.
1. What is meant by manual testing?
The process of manual testing involves quality assurance analysts carrying out tests independently and one at a time. Finding defects and feature problems prior to a software application becoming live is the goal of manual testing.
When testing a software program by hand, the tester verifies its essential characteristics. Without the use of specialist automation tools, analysts carry out test cases and create brief problem reports.
2. Automation testing: What is it?
Automated testing is a procedure where testers use scripts and tools to automate testing. Testers can increase test coverage and run more test cases with the use of automated testing. Testing by hand takes longer than testing by automation. Testing that is automated is more effective.
Different Network Security Devices
Here is a quick overview of a few network security devices:
- Firewalls: Within a network, a firewall is the safety buffer that regulates what interactions are permitted.
- Virtual private networks: The purpose of VPN gateways is to establish a safe connection to distant systems.
- Antivirus: It is employed to detect, track, and remove many types of malware.
- Filtering URLs: By preventing access to harmful websites, URL filtering will protect end users.
- The IDS system: The admin team is kept more vigilant by the intrusion detection system, which keeps an eye out for harmful attempts.
Some Popular Network Security Testing Tools in 2025
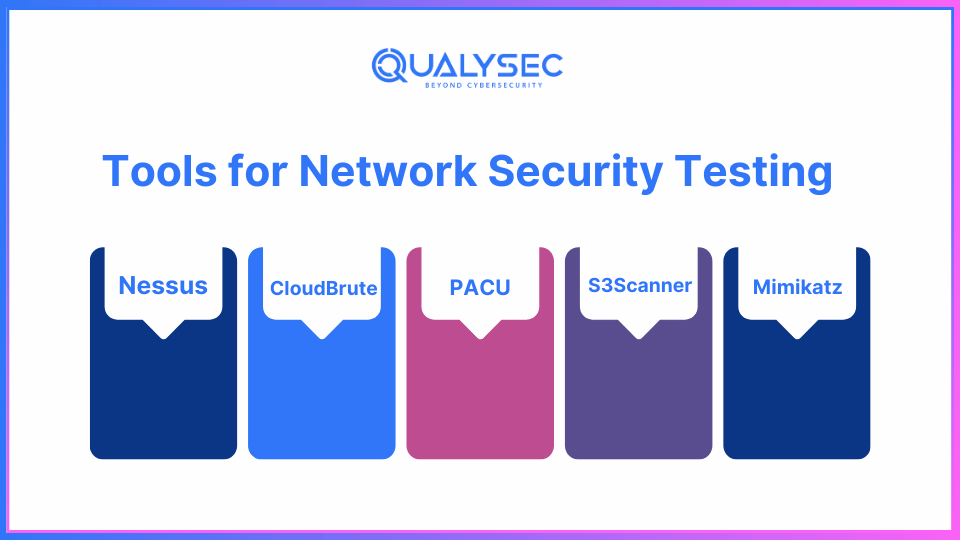
Here is a list of some popular tools.
1. Nessus:
Nessus professional is a network security software that detects and manages vulnerabilities in software applications, IT devices, and operating systems.
Users can create their own security plug-ins, access a range of security plug-ins, and scan networks and individual PCs.
Characteristics
- It generates an outline for users and allows variation of reports by hosts or vulnerabilities.
- Notifies the recipient via email of the scan’s findings
- It assists in fulfilling corporate, governmental, and regulatory obligations.
- It protects your company from cybersecurity risks by scanning cloud apps.
2. CloudBrute
CloudBrute is an open-source tool for discovering the customer’s AWS S3 buckets. The tool is widely used due of its relative speed and is modular and adaptable. The tool’s features include:
- Cloud detection (Source Code with IPINFO API)
- Black-box, unauthenticated testing
- Cross-platform compatibility
- Randomization via User-Agent
- Randomization by Proxy
3. PACU
Pacu is a complete AWS security-testing toolkit made for offensive security professionals, and it is named after a particular kind of piranha found in the Amazon. Although a number of AWS security scanners are now the cloud’s “Nessus,” Pacu is intended to be the Metasploit of security scanners. With its modular architecture and Python 3 code, Pacu includes tools for each stage of the pentesting process, encompassing the entire cyber death chain.
Pacu is the culmination of our innumerable previous AWS red team engagements’ research and exploitation expertise. In addition to increasing productivity, automating assessment components enables our assessment team to be far more thorough in huge situations. It now just takes minutes to manually enumerate what used to take days.
4. S3Scanner
An automated cyber security program called S3Scanner is used to search and extract data from the target domain’s open buckets. The program is accessible on the GitHub site and was created using the Python programming language.
5. Mimikatz
Mimikatz is an open-source application that lets you examine and save authentication credentials like Kerberos tickets. The toolbox offers a variety of network attacks to assist evaluate vulnerabilities and is compatible with the most recent version of Windows.
Since antivirus and endpoint security products typically fail to identify or remove attacks, attackers frequently employ Mimikatz to escalate access and steal credentials. Pen testers, on the other hand, employ Mimikatz to find and take advantage of security holes in your networks so that you can address
The Network Security Testing Process
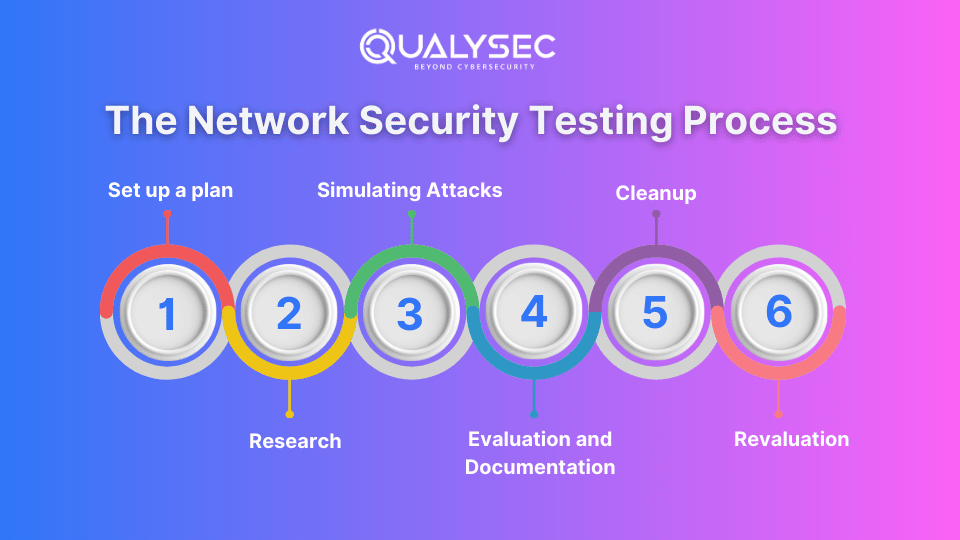
- Set up a plan:
It is necessary to define the objectives, goals, and breadth of security tests.
Selecting particular networks, systems, and applications that require testing - Research:
gathering data in order to identify any potential weaknesses. Listing resources and services with both automatic and traditional approaches - Simulating Attacks:
Use penetration testing methods to take advantage of weaknesses.
It mimics the actions of a malevolent actor in order to assess how well security protections are working. - Evaluation and Documentation:
These results will be divided into three groups: vulnerabilities that have been found, successful exploits, and remedial suggestions. Therefore, such vulnerabilities must to be prioritized according to their seriousness and possible consequences. - Cleanup:
Fixing and enhancing any vulnerabilities found in collaboration with stakeholders - Revaluation:
completing follow-up evaluations to make sure corrective actions are effective.
Make sure that no weakness was overlooked.
Challenges in Network Security Testing
- Invalid Negative and Positive Results:
These problems can make it difficult for us to distinguish genuine undiscovered vulnerabilities from fake ones. It is important to avoid mistaking real threats for random events. - Limitations of Scope:
A precise determination of the scope for testing
Verifying that every system and component is a part of the evaluation process is crucial. - Intensivity of Resources:
Enough time and resources ought to be made available for comprehensive testing.
This contrasts with a comprehensive examination that solely considers corporate operations. - The Human Factor:
recognizing that automated techniques are limited in their ability to identify vulnerabilities related to human behaviors, activities, and decisions. addressing the dangers of social engineering techniques and the possibility of insider danger in a company. - Integration with Lifecycles of Development:
seamlessly incorporating security testing into the software development lifecycle (SDLC) at each level. Making certain that security considerations are carefully incorporated from the very beginning of the design process to the actions that follow execution.
Putting Network Security Testing into Practice
- Tools for Automated Scanning:
What: Quickly scan your network for known vulnerabilities using programs like OpenVAS, or Nessus.
How: To identify weaknesses and maintain control, do routine scans. - Frameworks for Penetration Testing
What: For comprehensive and structured testing, use frameworks like OWASP Zap or Metasploit.
How: To determine how well your security measures are working and where they need to be improved, simulate real-world attacks. - Information and Event Management for Security (SIEM)
What: Use SIEM solutions to improve the intelligence of your security.
How: Gather and examine security logs continuously to identify possible dangers and enable prompt action in the event of an issue. - Tools for Wireless Protection
What: Use programs like Wireshark or Aircrack to safeguard your wireless networks.
How: By identifying any Wi-Fi security vulnerabilities that require quick action, these tools assist in evaluating the general security of wireless networks. - Evaluations of Social Engineering
What: Evaluate how resilient your team is to phishing and other social engineering assaults.
How: Run mock campaigns to test people’s ability to identify and respond to social engineering techniques. Utilize the findings to customize training initiatives that raise staff members’ knowledge of security measures best practices.
How Qualysec Benefits in Network Security Testing
Qualysec has an excellent track record for being adept at identifying security risks and issues. They are therefore the top provider of network security evaluation. They can offer you a variety of services, including VAPT, by offering security advice and helping you in the event of a security problem.
With its main office located in India, Qualysec is a globally recognized leader in the cybersecurity sector. In this position, they have a wealth of information and expertise. When the Qualysec team finds a problem, they create a solution to address it, increasing the security of the business.
Any cybersecurity event that poses a danger can be tracked and neutralized by Qualysec’s pen tester team. This makes it possible for them to offer the greatest security solutions. They provide these services by utilizing modern technology like:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- Blockchain Pentesting
Qualysec has the resources, complies with industry regulations, and provides clear instructions so that customers may use the solutions to resolve their issues. They also accomplish this by creating a solid plan that is founded on the information acquired and the outcomes.
Businesses that must adhere to stringent standards or clients who wish to demonstrate their commitment to privacy and security to clients or suppliers would find Qualysec’s solution to be an ideal option. Frequent security testing helps businesses find those flaws quickly and fix them before hackers take advantage of them.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Last but not least, maintaining network security is crucial since cybercriminals continuously come up with novel ways to attack. Regular network security testing and security audits are essential, as they ensure a secure network. By using these techniques, companies can identify and address system vulnerabilities that hackers might use against them. Additionally, a report with the assessment results and recommendations for securing their networks at the lowest possible level must be sent to the businesses.
Qualysec has a solid track record of assisting customers and providing cybersecurity services across a variety of sectors, including IT. Through their expertise, clients have been able to identify and address vulnerabilities, prevent data breaches, and improve their overall security.
FAQ
Q. What is testing network security?
Finding possible security vulnerabilities in a network is known as testing network security. These may include configuration mistakes, insecure protocols, software flaws, and other mistakes that expose the company to misuse.
Q. How to check network security?
The process of employing computerized scanners to check networks, servers, and apps for security flaws and vulnerabilities is known as vulnerability scanning. These computer applications, known as detectors, compile an inventory of every piece of technology that is part of a network and identify their operational characteristics as well as any weaknesses that may exist.
Q. How to do security testing manually?
Start by going over the application’s features, gadgets, and structure in detail. Determine which departments deal with private data or essential features. Make a thorough exam strategy based on your comprehension of the application.


















































































































































































































































































































































0 Comments