Did you know in 2022, the overall cost of cyberattacks reached $6 trillion? Cyberattacks have become increasingly common in recent years. In response to the increase in assaults and the sophistication of malware and hacking tactics, organizations have turned to the application VAPT to uncover and manage security problems.
In this blog, you’ll get a grasp on VAPT testing on mobile apps, APIs, and AWS platforms. Furthermore, we’ve also talked about how this testing approach is carried on, how can you overcome the challenges, and the major benefits you will get from the VAPT penetration test.
How Can a Cyber-Attack Affect Your Company?
Cyber-attacks are a serious problem for all businesses and organizations, not just those who have been hacked. Furthermore, cyber-attacks can result in identity theft, money theft, or a loss of user confidence. However, data is the asset to which any organization is most vulnerable to risk.
Organizations must ensure to protect and secure their data and applications. Application VAPT play a role in giving some kind of protection against data theft. VAPT is one of the finest ways to ensure the protection of your application and data against potential assaults by malicious hackers. Furthermore, VAPT is a technique for discovering known security weaknesses in a system or network. Let’s learn more about its type.
Demystifying Application VAPT: The Essence in Cybersecurity
Vulnerability Assessment and Penetration Testing is a type of security testing that looks for holes in an application, network, endpoint, or cloud. Vulnerability Assessment and Penetration Testing have significant advantages, and they are frequently used in tandem to produce a full study.
- Vulnerability Assessment
There are some distinctions between Vulnerability Assessment (VA) and Penetration Testing (PT), both of which are methodologies for finding weaknesses in systems, networks, or online applications. First, a Vulnerability Assessment (VA) investigates, identifies, and reports known vulnerabilities. It creates a report outlining the vulnerability’s classification and priority.
- Penetration Testing
On the other hand, a Penetration Test (PT) attempts to exploit vulnerabilities to determine the level of entry. It evaluates the level of defense. Approaching the VA is like approaching a door, analyzing it, and considering its possible weaknesses. Furthermore, the VA is often an automation process, whereas the PT is typically a manual process.
The Goal of VAPT
Because hackers’ tools, techniques, and procedures for infiltrating networks are always evolving, it is necessary to conduct regular assessments of the organization’s cyber security. VAPT contributes to your organization’s security by providing insight into security problems as well as guidance on how to fix them. Furthermore, VAPT is becoming increasingly important for enterprises trying to comply with standards such as the GDPR, ISO 27001, and PCI DSS.
Are you a business searching for security solutions like VAPT for applications? You are in the right place. Schedule a FREE call with our expert security consultants and learn why and how you can perform application VAPT.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Navigating the Mobile Frontier: The Use of Mobile App VAPT
The smartphone itself is subject to several types of cyberattacks. Each application loaded on the smartphone, whether Android or iOS, exposes the organization’s data to known and unknown vulnerabilities.
Mobile application VAPT comprises extensive security testing of the app’s functionality as well as exposing the app’s underlying codes and design to determine whether or not suitable security measures are in place. In addition, it also plays a crucial function in identifying vulnerabilities in downloading programs that may have possible hazards and faults that make data susceptible. Here are some of the benefits of testing mobile applications:
- VAPT protects the security of mobile apps by finding and correcting vulnerabilities that attackers might exploit.
- It helps to preserve sensitive user information by avoiding unwanted access or data breaches.
- By demonstrating a commitment to app security, regular VAPT instills trust in users and stakeholders.
Read more: Deep Dive into Mobile App Pentesting
Decoding the World of API: The Fundamentals of API VAPT
When a company utilizes an API, it exposes itself to cyber assaults since most APIs are insecure and readily exploited. A successful assault might result in data theft or even total system or network damage. As a result, companies must test their APIs regularly to ensure that they are not subject to attacks that might result in data loss and other issues. Here are some benefits of API VAPT:
- Protects against injection attacks (for example, SQL injection, DDoS), which might jeopardize API integrity and result in unauthorized access or data leaks.
- Allows enterprises to make educated decisions and prioritize repair activities by providing insights into potential security concerns related to APIs.
- Ensures that APIs are dependable and secure, preventing interruptions that might damage company operations and user experience.
Read more: API Penetration Testing: A Comprehensive Guide
Fortifying the Cloud Environment: The Approach of AWS VAPT
Amazon Web Services (AWS) is the world’s most popular cloud computing platform. It offers elastic computing services, cloud storage, databases, and a variety of data analytics and artificial intelligence applications, as well as deployment and automation services.
Companies should examine compliance duties, the dangers of cyber-attacks against cloud resources or sensitive data housed on the cloud, and how to manage them before switching to AWS. Furthermore, penetration testing is a very efficient method of finding security flaws in a cloud system. A penetration tester can identify key security flaws in an AWS implementation and make proactive suggestions to address them. Here’s why you should perform VAPT on AWS:
- VAPT testing identifies vulnerabilities that are used in Distributed Denial of Service (DDoS) attacks, ensuring that AWS infrastructure can withstand such attacks.
- Ensures strong IAM regulations and procedures, preventing illegal users or entities from getting excessive AWS rights.
- VAPT for AWS covers assessing the security of serverless functions, API Gateway setups, and other serverless components because AWS enables serverless computing.
Read more: Cloud Penetration Testing: A Complete Guide
Strengthening the Base: The Benefits of Performing Application VAPT?
Businesses are leveraging the potential of apps to expand their reach and streamline operations, thanks to the fast evolution of web services. However, the ever-increasing threat of cyber-attacks poses a serious risk to enterprises’ online infrastructure. Furthermore, conducting Vulnerability Assessment and Penetration Testing (VAPT) is critical for protecting your online applications and effectively countering these attacks. Here’s how:
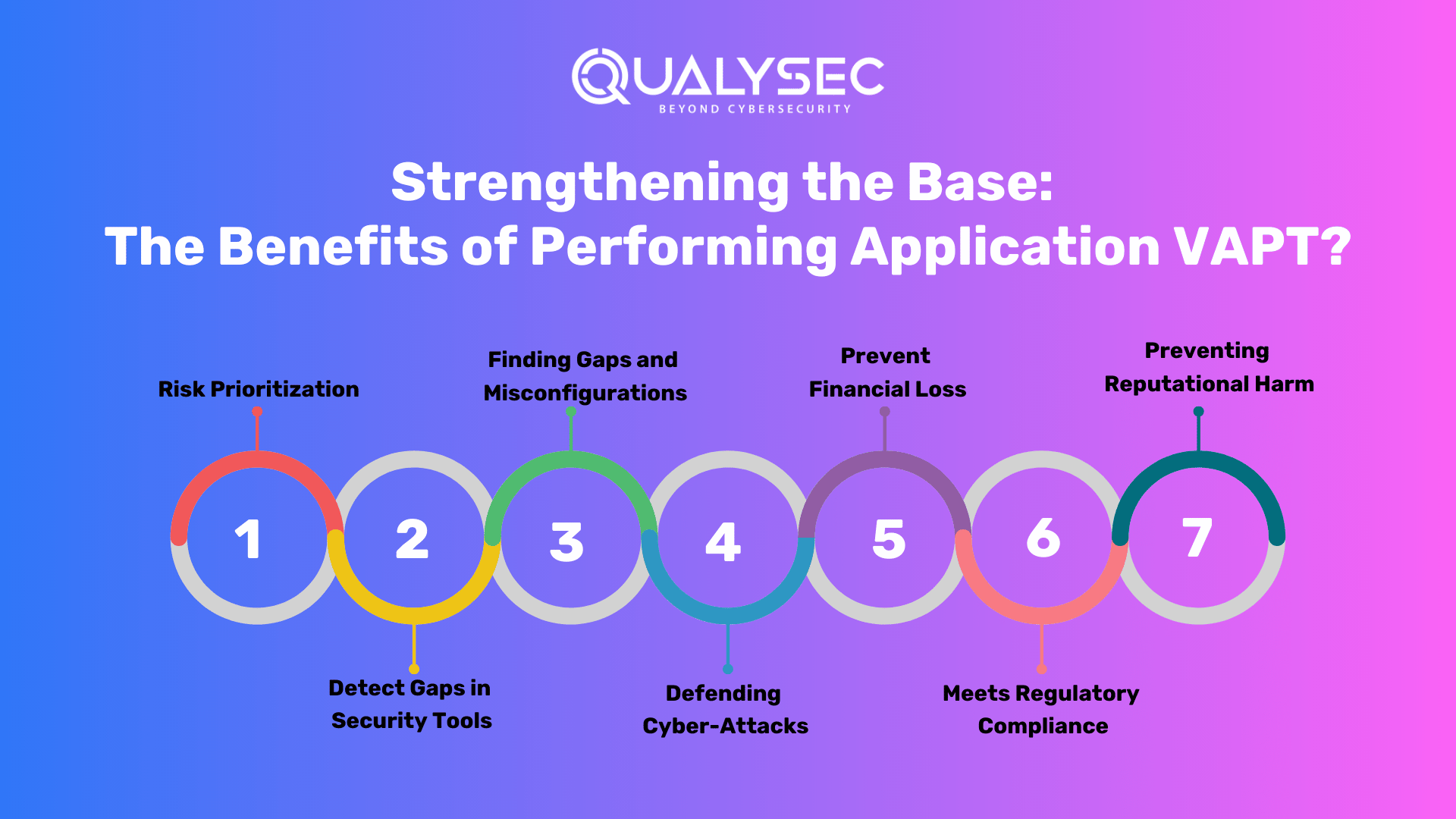
1. Risk Prioritization
Vulnerabilities are often discovered and collected, but risk prioritization is not performed. Furthermore, with so many security dangers to deal with these days, IT decision-makers must figure out how to rank them in order of importance. We observe several businesses that spend a lot of time on minor problem-solving and try to delay or neglect to repair the most serious ones if they are not in priority.
2. Detect Gaps in Security Tools
This may seem like an odd explanation, but if you do a pentest using various tools for the same app, you are more likely to obtain inconsistent findings, sometimes contradicting each other. So, if you know your app’s security posture, you can and should use it to compare tools. Furthermore, Manual penetration testing is the first step, then the comparison of tools to see which are capable of capturing the same set of data.
3. Finding Gaps and Misconfigurations
Because they are human errors, web apps, mobile apps, and IT networks are prone to human flaws, which a hacker exploits or takes advantage of. Furthermore, the majority of hacking efforts or flaws that have recently been identified as bugs are the result of poor coding techniques rather than vulnerabilities that have emerged from these platforms. VAPT security testing helps in mitigating these vulnerabilities.
4. Defending Cyber-Attacks
Secure coding, vulnerability assessments, and penetration testing are examples of robust app security techniques that fix weaknesses and protect against data breaches and hacker attempts. Furthermore, secure code, input validation, and access restrictions, for example, reduce the danger of different threats such as injection assaults, cross-site scripting, and authentication bypasses.
5. Prevent Financial Loss
A data breach may cause considerable financial harm to a company in a variety of ways. If hackers get your personal information, they may demand payment in the form of ransomware. As a result, the firm will incur financial as well as credibility and reputational damages. Furthermore, VAPT examines all security weaknesses to guarantee that it is secure from both internal and external attacks.
6. Meets Regulatory Compliance
The IT industry highly regulates, with strict compliance standards such as HIPAA, FDA, and GDPR. Vulnerability assessments and penetration testing assist organizations in meeting regulatory requirements and avoiding costly penalties. Furthermore, frequent inspections guarantee that sensitive information stays private and follows data protection requirements.
7. Preventing Reputational Harm
Businesses are extremely concerned about reputational harm. With VAPT, data breaches and cyberattacks may be averted, which can result in negative headlines and destroy a company’s brand. Furthermore, businesses may protect their brand name and maintain customer confidence by securing their IT infrastructure.
Also Read: VAPT’s Impact on Reducing Cybersecurity Vulnerabilities
The Techniques: The Methodologies of Application VAPT
In the software testing process, three types of testing are used: white box, black box, and gray box testing. All three techniques look at the testing process from a different angle and cannot be employed independently.
White Box Testing
The primary goal of White Box testing is to validate the code and internal structure of the product being tested. Furthermore, a tester is inspecting the input-output processes here, with a strong emphasis on the product’s inner workings. White Box testing is also known as Open, Glass, Transparent, Clear Box, and Code-based testing.
Black Box Testing
Behavioral testing, or Black Box testing, is a process of VAPT penetration test in which the tester is unaware of the platform. The quality assurance specialist is unaware of the product’s interior layout, application, and design. Furthermore, these tests are typically functional, and websites are examined with a browser, some data is entered, and the results are evaluated.
Gray Box Testing
Gray Box testing combines elements of both White Box and Black Box testing. Furthermore, using this strategy, the tester hopes to identify all potential code and functionality flaws. At this point, a professional can test the end-to-end functions.
The Workflow of VAPT Security Testing: A Detailed Guide
Testers perform VAPT testing which includes particular steps in it. Here is the step-by-step guide to the process:
Gathering Information
The fundamental goal of VAPT is to collect as much information as possible. This includes a two-pronged approach: utilizing readily available information from your end, and numerous tools to get technical and functional insights. Furthermore, the VAPT business collaborates with your team to gather critical application information.
Planning
The penetration testing process is initiated by the VAPT service provider by defining the objectives and goals. Furthermore, they delve extensively into the technical and functional complexity of your application. This comprehensive investigation allows the testers to alter the testing strategy to address specific vulnerabilities and threats specific to your environment.
A comprehensive penetration testing plan is created, outlining the scope, methodology, and testing criteria. Furthermore, they acquire and prepare the essential files and testing instruments. This procedure includes configuring testing settings, checking script availability, and designing any unique tools needed for a smooth and effective review.
Auto Tool Scan
During the application VAPT process, especially in a staging environment, an automated and intrusive scan is necessary. This scan comprises utilizing specific VAPT tools to seek vulnerabilities on the application’s surface level carefully. Furthermore, the automated tools mimic prospective attackers by crawling through every request in the application, uncovering potential weaknesses and security gaps.
By running this intrusive scan, the testers proactively find and patch surface-level vulnerabilities in the staging environment, acting as a preventative measure against potential assaults. Furthermore, this strategy provides not only a thorough review but also quick rectification, boosting the application’s security posture before it is deployed in a production environment.
Manual Penetration Testing
The provider offers a comprehensive selection of deep manual penetration testing services that are tailored to specific requirements and standards. This one-of-a-kind method allows for a thorough examination of potential vulnerabilities across several domains. Furthermore, this VAPT test conducts a systematic assessment of online applications, looking for vulnerabilities in authentication, data management, and other crucial areas to improve the security posture of the application.
Reporting
The testing team systematically identifies and categorizes vulnerabilities discovered throughout the evaluation, ensuring that potential risks are recognized. Furthermore, a senior consultant also does a high-level penetration test and reviews the entire report.
VAPT security testing ensures the highest level of quality in testing methods as well as the accuracy of reporting. Furthermore, this thorough documentation is a valuable resource for understanding the security state of the application.
Components of the Report:
- Vulnerability Name: Provides a clear identification for each vulnerability, such as SQL Injection.
- Likelihood, Impact, and Severity: Assesses the likelihood, impact, and severity of each vulnerability to quantify the possible risk.
- Description: Provides a summary of the vulnerability, allowing stakeholders to understand it better.
- Consequence: Explains how each vulnerability may affect the application and emphasizes the significance of mitigation.
- Instances (URL/Place): Identifies the location of vulnerabilities, allowing for more targeted repair efforts.
- Proof of Concept (POC): Provides a step-by-step tutorial and a Proof of Concept (POC) for validating and reproducing each vulnerability.
- Remediation: Provides concrete solutions for eliminating discovered breaches and fostering a secure workplace.
- CWE No.: Assigns IDs for Common Weakness Enumeration for exact classification and referencing.
- OWASP TOP 10 Rank: Indicates the vulnerability’s position in the OWASP TOP 10, emphasizing its importance in today’s threat landscape.
- SANS Top 25 Rank: Indicates the vulnerability’s position in the SANS Top 25, which helps to contextualize its significance.
- References: Additional materials and references are provided for a better knowledge of vulnerabilities and relevant remedial techniques.
This comprehensive reporting method ensures that you and the developers receive relevant insights into the application’s security condition as well as practical recommendations for a solid security posture. Comprehensive reporting method is important for companies which hire offshore mobile app developers and need to be on the same page with remote teams.
Doesn’t it feel difficult to read all this and get a grasp of what the pentest report looks like? Here’s the solution: Download a Sample Report!
Latest Penetration Testing Report

Remediation Support
If the development team requires support in reproducing or reducing reported vulnerabilities, the provider delivers a critical service through consultation calls. Furthermore, testers discover issues that promote direct engagement to aid the development team in effectively analyzing and addressing security threats. In addition, this collaborative approach ensures that the development team receives advice, allowing for the seamless and speedy resolution of vulnerabilities.
Retesting
Following the completion of vulnerability mitigation by the development team, a vital stage of retesting happens. Furthermore, to check the efficacy of the treatments administered, our staff undertakes a detailed examination. The final report is lengthy and includes:
- History of Findings: This section has a complete record of vulnerabilities uncovered in previous assessments, making it easy to track the progress of security solutions.
- Condition of Assessment: Specifies the condition of each vulnerability, whether it is corrected, ignored, or declared out of scope, and provides a detailed overview of the remediation outcomes.
- Screenshots for Proof: Physical evidence and images are added to the retest report, visually validating the fixed vulnerabilities. Furthermore, this verifies the method and ensures a full and accurate assessment of the application’s security condition when the procedure is completed.
LOA and Certificate
The testing company goes above by providing a Letter of Attestation, which is an important document in VAPT security testing. Furthermore, this letter, which is supported by evidence from penetration testing and security assessments, has numerous purposes:
- Confirmation of Security Level: Use the letter to acquire physical confirmation of your organization’s security level, assuring stakeholders of the robustness of your security procedures.
- Stakeholder Security: Use the letter as a tangible testimony to the depth of your security practices to demonstrate to clients and partners your commitment to security.
- Compliance Satisfaction: The Letter of Attestation is a valuable resource for meeting regulatory requirements and proving compliance with industry-specific security procedures.
Furthermore, the testing company will provide a Security Certificate. This will enhance your ability to represent a secure environment, reinforce confidence, and meet the expectations of various stakeholders in today’s dynamic cybersecurity landscape.
The Hurdles: The Challenges and Solutions in the VAPT Penetration Test
Here are the challenges faced during web app VAPT testing and how to solve them:
1. Constraints on Resources
- Challenge: Organizations may be unable to invest effectively in VAPT tools, competent staff, and rigorous testing due to limited budgets and resources.
- Implication: Inadequate resources can lead to insufficient or infrequent VAPT, leaving potential risks untreated.
- Solution: Recognize VAPT as a critical component of cybersecurity, assign dedicated funding, and investigate cost-effective alternatives to overcome resource constraints.
2. Modern IT Environment Complexity
- Challenge: The growth of varied IT environments, such as cloud services, mobile apps, and complicated APIs, complicates VAPT.
- Implication: Traditional VAPT techniques may struggle to cover the whole attack surface, resulting in security protection blind spots.
- Solution: Take a comprehensive strategy that takes into consideration the complexities of current IT environments. Invest in technologies and skills that are focused on safeguarding a variety of digital settings.
3. Adapting VAPT to Evolving Threats
- Challenge: The cybersecurity landscape is continually changing, with new threats and attack vectors appearing regularly.
- Implication: Outdated and static VAPT approaches may fail to handle fresh dangers, leaving firms susceptible to the most recent cyber-attacks.
- Solution: To remain ahead of changing risks, implement continual VAPT processes. Update testing methodology and tools regularly to integrate the most recent attack strategies. Encourage a proactive approach to threat intelligence, to ensure that VAPT initiatives are influenced by current cybersecurity trends.
Choosing the Pros: The Best Web App VAPT Testing Company
QualySec Technologies emerges as a beacon of excellence in the domain of reinforcing digital landscapes, effortlessly combining innovation, reliability, and efficiency while persistently supporting the security of cloud services. We are known for our revolutionary process-based VAPT penetration test and provide tailored security solutions that meet the highest industry requirements.
Furthermore, we ensure your apps are fortified against changing threats by employing a Hybrid security testing approach (combination of automation and manual pentest) and leveraging the capability of a professional team steeped in testing experience. Our pentesting services utilize both in-house and commercial tools such as Burp Suite and Netsparker.
We are steadfast partners for organizations seeking complete security solutions, navigating the maze of regulatory compliance requirements such as GDPR, SOC2, ISO 27001, and HIPAA. Furthermore, our commitment is centered on enabling developers.
Our comprehensive and developer-friendly pentesting report serves as a road map for addressing vulnerabilities. Furthermore, we provide you with the knowledge you need to improve the security posture of your application, from pinpointing the vulnerability’s position to providing step-by-step fixes.
QualySec proudly maintains a faultless zero-data-breach record, having safeguarded over 250 apps and expanding our knowledge to 20+ countries via a worldwide network of 100+ partners. Increase your digital security with unrivaled knowledge – contact QualySec today for a more secure future for your application and organization.
Conclusion
Vulnerabilities Assessment and Penetration Testing (VAPT) arises as a vital precaution in the ever-expanding digital ecosystem, where technology is both the driving force and the principal risk. The application VAPT becomes increasingly evident as businesses negotiate the intricacies of modern IT ecosystems – a proactive, comprehensive, and adaptable approach to security is not only advantageous; it is required.
VAPT stands as a robust shield, ready to uncover and eliminate vulnerabilities that might otherwise be exploited by hostile actors, from the intricate domain of mobile applications to the vast horizons of cloud services and APIs. Finally, as technology progresses, so do the capabilities of people attempting to exploit its flaws.
The VAPT imperative is a proactive position against the unknown difficulties of the future, not just a reaction to existing concerns. Organizations that embrace and prioritize VAPT are not just protecting their digital domain; they are also setting the groundwork for a secure and resilient future in the face of an ever-changing cyber scenario.
Frequently Asked Questions
Is VAPT mandatory for iso 27001?
While ISO 27001 does not specifically require VAPT, it is regarded as a best practice within the standard. VAPT assists companies in proactively identifying and addressing vulnerabilities before bad actors may exploit them.
How frequently is vulnerability scanning done?
Organizations should scan their internal and external systems at least periodically, according to industry standards. Assessments should ideally be performed once a year.
How does VAPT defend against data breaches?
VAPT scans the whole application as well as its underlying infrastructure, which includes all network devices, applications, and other components. It’s a thorough examination that assists you in identifying security flaws so you can address them before a hacker can.
What are the risks of not performing vulnerability scans?
Critical vulnerabilities must be regularly detected, prioritized, and remediated to lower your risk and prevent a data breach. Without frequent vulnerability scanning, your chances of being exploited and compromised skyrocket.
How are vulnerabilities patched?
Scanners and endpoint agents are two of the most frequent methods. Scans give an awareness of known abnormalities or vulnerabilities that may signal the presence of a malware assault or harmful event. Advice from your hardware and software vendors, as well as third-party best practice groups.
What is the role of VAPT in cyber security?
VAPT is an acronym that stands for Vulnerability Assessment and Penetration Testing. This technique assists businesses in identifying and correcting security flaws before attackers may exploit them. VAPT also assists firms in meeting regulatory compliance obligations and safeguarding their brands.


















































































































































































































































































































































0 Comments