Information security audit services are a comprehensive analysis of a business’s IT infrastructure to check if they are following the best security practices. These audits help in finding security issues and ensure compliance with regulatory requirements. Organizations should perform IT security audits at least once a year to stay ahead of evolving cyber threats.
According to a survey, only 52% of companies globally conduct security audits, while 19% of companies don’t conduct them at all. This is a primary reason why 2,200 cyberattacks are occurring every day since the pandemic.
We have created this blog to help businesses and individuals protect their valuable digital assets and sensitive data. This blog explains why information security audits are important, describes the steps involved, and highlights the tools and techniques used.
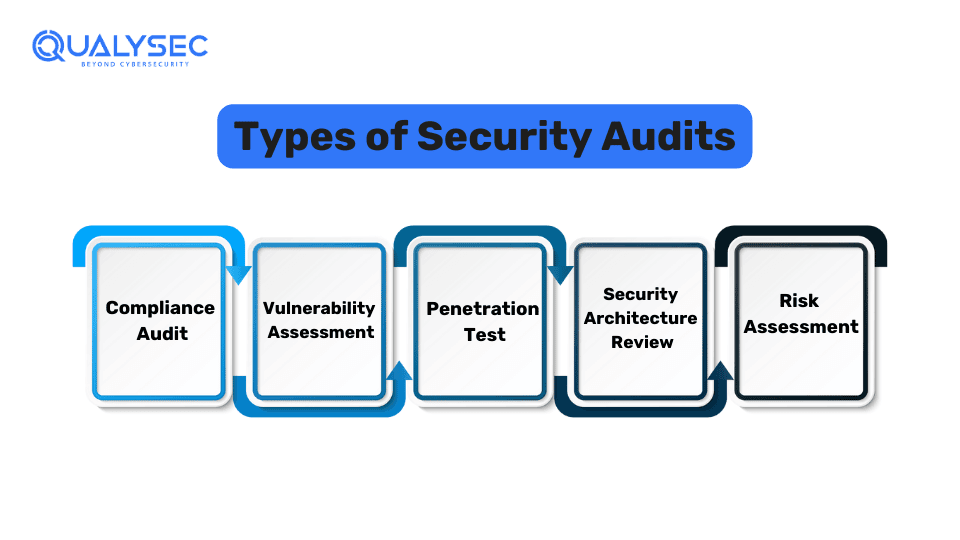
How Many Types of Security Audits Are There?
There are generally 5 types of security audits that an organization can choose to conduct.
1. Compliance Audit
A compliance audit involves evaluating an organization’s security policies to determine if they are following the established laws and industry standards. Many industries and regions have specific compliance laws such as HIPAA, ISO 27001, SOC 2, PCI DSS, etc. Organizations functioning under these laws need to comply with these standards or face legal problems.
In a compliance audit, the auditor may review documentation, internal controls, financial records, risk management policies, and several others to check if they are up to date. Being compliant with these regulations improves the image of the company and builds customer trust.
2. Vulnerability Assessment
A vulnerability assessment is the process of evaluating an organization’s IT systems to identify weaknesses that attackers could exploit. During this assessment, the auditor will use automated tools to scan the organization’s networks and applications for known vulnerabilities. Additionally, will recommend remediation steps to address the identified issues.
3. Penetration Test
A penetration test involves simulating real attacks on the organization’s IT infrastructure to check if it can be breached by cybercriminals. In a penetration test, the auditor will attempt to gain unauthorized access to the organization’s application, networks, and other systems and exploit common vulnerabilities.
4. Security Architecture Review
In a security architecture review, the auditor examines all areas of an organization’s IT infrastructure including its operating systems, network design, applications, database, and more. The goal is to find any security issues that could be used by malicious actors for unauthorized access. Additionally, information security audit services are essential in this process.
5. Risk Assessment
A risk assessment identifies potential security risks in an organization’s IT environment and assesses their impact on business operations. The auditor will analyze the security policies of staff, technology components, data flows, etc. to identify any potential risk that could affect the business.
What are the Key Components of Information Security?
Popularly known as the CI Triad, there are 3 main components of information security: confidentiality, integrity, and availability. Each element of the information security program must be designed to implement one of multiple of these principles. Information technology security audit ensures these principles are followed.
- Confidentiality: Confidentiality security measures are designed to prevent the unauthorized display of information. It ensures that only authorized users are allowed to access sensitive information. This means only those individuals who own it or need the information to perform organizational functions are given access.
- Integrity: Data integrity includes protecting the information from unauthorized changes, such as addition, deletion, or alteration. This ensures that the information is accurate and is not modified incorrectly, be it accidentally or maliciously.
- Availability: Availability refers to the system’s ability to ensure software resources and information are fully available when a user needs it. Additionally, availability measures guard the information against downtime, disruptions, and denial-of-service (DoS) attacks.
What are the Steps in a Security Audit?
Information security audit services generally involve eight steps, which are:
- Information Gathering: Gather necessary information about the IT systems (applications, networks, etc.) and policies that need to be audited.
- Define Scope: Outline the expectations from the audit and the tools and techniques to be used in the process.
- Vulnerability Assessment: Use automated vulnerability scanners to detect known vulnerabilities in the target system.
- Penetration Testing: Manually test and exploit all common vulnerabilities for a deeper analysis. This helps uncover complex vulnerabilities and also those missed by the scanners.
- Reporting: Document all the findings of the audit in a report, including the vulnerabilities found, their impact if they are exploited, and necessary remediation recommendations.
- Remediation: The development team uses this report and the recommendations in it to fix the vulnerabilities. If needed the audit team will help them locate the vulnerabilities.
- Retesting: The audit team will retest the IT system to confirm there are no remaining vulnerabilities. A final report is created that summarizes the entire process.
- LoA/Security Certificate: Finally, the audit team will provide a letter of attestation (LoA) that is proof of the successful conduct of the security audit. This can be used for compliance needs and stakeholders’ trust.
Ever seen a real IT security audit report? Click on the link below and download one right now!
Latest Penetration Testing Report

What are the Benefits of an IT Security Audit?
There are quite a lot of benefits that one can get from performing information security audit services, such as:
- Identify Vulnerabilities: An IT security audit helps in detecting the security vulnerabilities present in digital systems. As a result, organizations can enhance their security by fixing these vulnerabilities promptly.
- Protect Sensitive Data: By fixing the security issues, organizations can protect user data and intellectual property from unauthorized access and data breaches.
- Comply with Regulations: As mentioned earlier in this blog, organizations need to comply with respective industry regulations, or else face legal penalties and fines. An information technology security audit helps in achieving this.
- Improve Security Awareness: Knowingly or unknowingly, many malicious acts are done by insider threats (employees). A security audit will help the company know what security process they need to follow.
- Enhance Incident Response: Security audits help create a better response plan in the event of a security incident. They can detect gaps in current incident response plans and ensure backups are up to date.
- Build Stakeholders’/Customers’ Trust: By conducting a security audit, you can demonstrate your commitment to business and data security. As a result, it dwells well on stakeholders and customers.
- Allocate Budget Efficiently: A security audit helps organizations to get insights on what needs to be fixed and what doesn’t. This allows organizations to invest in security efficiently.
Want to conduct an IT security audit? Qualysec Technologies offers comprehensive security audits and penetration testing services at reasonable prices. Click on the link below and talk to our security expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Common Challenges Faced During an Information Security Audit?
Technology is always evolving and along with it, several challenges also emerge while auditing any digital system. Information security auditor plays a important role in addressing these challenges. Here are a few challenges that come with information security audit services:
- Complex IT Systems: With each passing year, the applications and IT devices become more technically complex. As a result, it becomes challenging for an auditor to understand each aspect completely.
- Evolving Threats: Similarly, cyber threats are constantly evolving and getting more sophisticated. Auditors need to be up to date with each vulnerability that could harm the IT infrastructure.
- Compliance Factors: Security audits are more complicated if the organization needs to meet industry standards like HIPAA, GDPR, ISO 27001, etc. Compliance audits can also be costly for organizations, especially if they operate in various jurisdictions.
- Limitation of Resources: Information technology security audits require a good amount of time and resources. However, organizations often struggle to allocate the necessities that are required for a comprehensive audit.
Tools and Techniques Used in Information Security Audits
Looking at so many benefits and features of information security audit services there are some effective IT audit tools and techniques used, such as:
Information Security Audit Tools
- Vulnerability Scanners: These are automated vulnerability scanning tools that scan systems, applications, and networks for security weaknesses like outdated software, open ports, or misconfigurations. For example, Nessus, Burp Suite, Nikto, etc.
- Compliance Checker: These tools ensure that the systems and policies comply with industry regulations and standards like ISO 27001, HIPAA, etc. For example, Axe, Accessibility Viewer, etc.
- Log Analysis Tools: These tools review logs from servers, network devices, and applications to detect unusual activities. For example, Graylog, Splunk, LogsHero Ltd., etc.
- Data Encryption Tools: These verify whether sensitive data is properly encrypted or not (both in transit and at rest). For example, VeraCrypt, AxCrypt, DiskCryptor, etc.
- Network Monitoring Tools: These tools continuously monitor network traffic to detect and respond to suspicious activities in real time. For example, Datadog, Paessler PRTG, OpManager, etc.
- Access Control Tools: These check who has access to various data and systems and assess that only authorized people can access sensitive data. For example, CyberArk, Okta, SailPoint, etc.
Information Security Audit Techniques
- Penetration Testing: Pen-testers or ethical hackers simulate real-world attacks to find security vulnerabilities in systems, applications, and networks.
- Log Analysis: The auditor reviews systems and network logs to detect and investigate suspicious activities.
- Access Control Review: Checking and verifying permissions to sensitive data and ensuring only authorized individuals have access to them.
- Configuration Review: Ensuring all systems and source code are configured as per industry best practices and standards.
- Risk Assessment: Identifying and evaluating potential security risks so that the organization can address the most critical risks first.
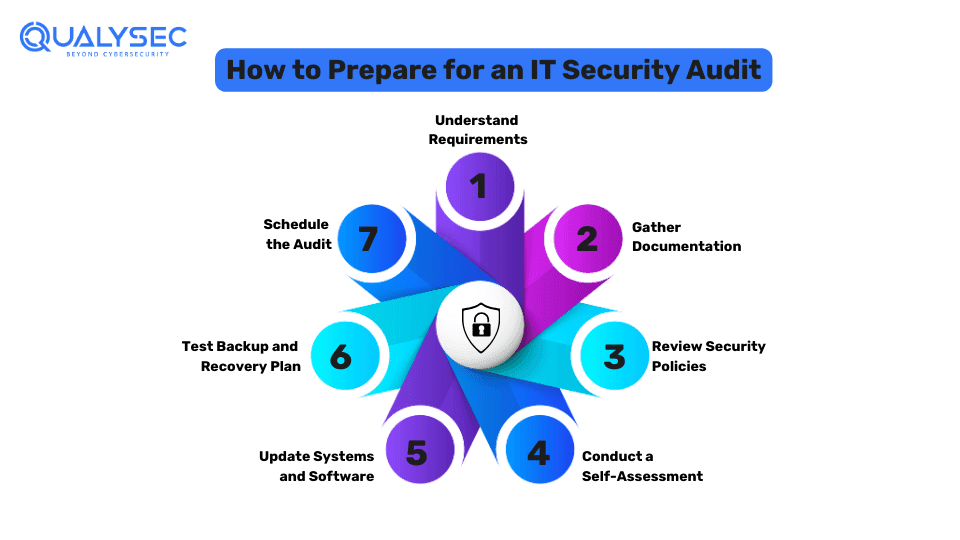
What are the Steps to Prepare for an Information Security Audit?
There are several key steps involved to ensure that the organization is ready to conduct a comprehensive IT security audit including the Information Security Audit Process, such as:
- Understand Requirements: Know what regulations, standards, and security policies you need to comply with for the audit.
- Gather Documentation: Collect all relevant documents for the audit, such as security policies, procedures, and previous audit reports.
- Review Security Policies: Ensure your security policies are up to date and align with respective compliance requirements.
- Conduct a Self-Assessment: Perform an internal review (if possible) to identify and fix security issues before the actual audit.
- Update Systems and Software: Ensure all systems and software are updated with the latest security patches.
- Test Backup and Recovery Plan: Ensure all your plans for data backup and recovery are functional and effective.
- Schedule the Audit: Coordinate with the auditor or audit company to schedule the audit and ensure all resources and documents are available during that period.
Conclusion
Audits are a separate concept from other security practices like tests and assessments. Information security audit services are a way to ensure that an organization is adhering to all the set security standards and policies effectively.
Information security audit services help in identifying and fixing security issues, ensure compliance, and build customers’ trust in the brand. While organizations can conduct some auditing internally, it is best to do it with a third-party IT security audit provider.
FAQs
Q: What is the Difference Between an Internal and External Audit?
A: An internal audit is conducted by the organization’s internal team to evaluate and improve internal security practices and security policies. However, an external audit is conducted by a third-party audit provider who assesses the organization’s security measures and compliance standards.
Q: How Often Should an Organization Conduct Information Security Audits?
A: Organizations should conduct an information security audit at least 1 – 2 times a year. This is because cyber threats are always evolving, and security measures need to be up to date.
Q: What is the cost of an IT security audit?
A: While different auditors charge different fees, the average cost of an IT security audit ranges from USD 1,000 to USD 5,000. Additionally, it depends on several other factors, such as the complexity of the systems, the number of systems to be audited, the type of audit, expertise of the auditor.
Q: How Can Businesses Ensure Continuous Compliance?
A: Businesses can ensure continuous compliance by performing regular information security audits. Additionally, they can revisit the security policies regularly and ensure all their systems are up to date.






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments