Cloud security network is a set of technologies, practices, and protocols that protect cloud networks from breaches and cyberattacks. Organizations that use cloud services, both private and public, should implement necessary security measures to secure data and applications hosted in them.
With 45% of total breaches being cloud-based, it’s high time businesses start considering the need for cloud security. Practices like security audits and cloud penetration testing can help identify vulnerabilities in the cloud environment and strengthen its overall security posture.
In this blog, we are going to extensively learn about cloud security networks, their importance, and best practices. If you are a cloud service user or provider, stay until the end.
What is a Cloud Security Network?
Cloud security network solely focuses on protecting cloud networks from unauthorized access, misuse, modification, and exposure. It is one of the fundamental layers of cloud security that monitors, prevents, and manages risks in the network perimeter.
Keeping the data safe when it is stored and managed in the cloud is what cloud network security is all about. It includes components like firewalls, encryption, and access control mechanisms to ensure that only authorized people can access the data.
Additionally, it constantly monitors any suspicious activities and fixes vulnerabilities before an attacker exploits them. So, whether you are using cloud computing for work or personal use, a cloud security network ensures your information stays secure, giving you peace of mind.
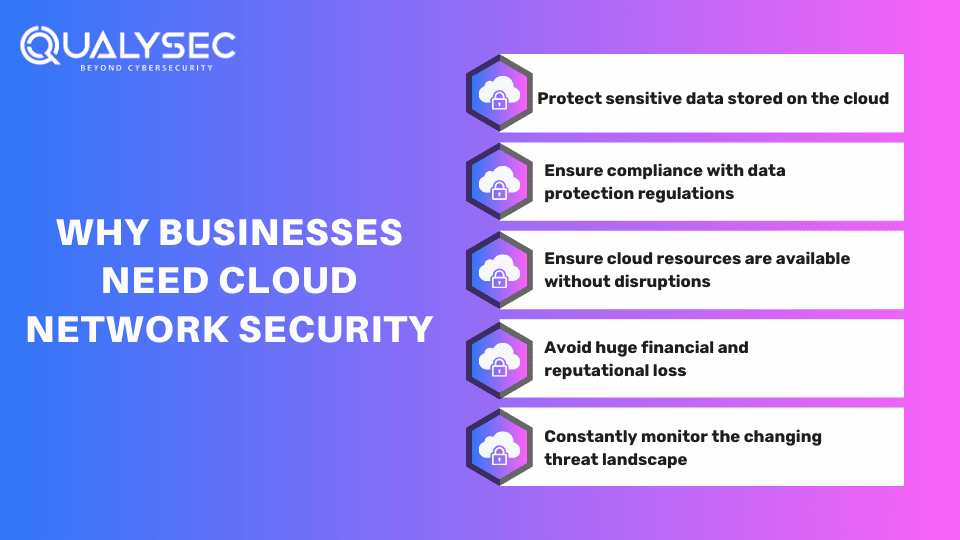
The Importance of Cloud Security Networks
Whether you have moved completely to a private cloud or are using a hybrid cloud model, its security is a no-brainer. You need to understand that when you move to the cloud from your traditional on-premises perimeter, there are additional security risks attached to it.
The usual multi-layered network security components like firewalls and encryption are a must but as workload and users increase, it becomes harder to detect and respond to security threats promptly. To keep up with modern IT requirements, organizations need an easier way to manage and scale network security that directly integrates with the cloud.
Cloud security network practices like penetration testing are the best way in modern cybersecurity that help you minimize risk, comply with industry standards, and ensure safe business operations.
Benefits of Cloud Security Network
- Detect Vulnerabilities: With measures like vulnerability assessment and penetration testing (VAPT), you can detect vulnerabilities that could lead to possible attacks. These measures use automated and manual techniques to identify and report security weaknesses.
- Data Protection: It keeps data stored and managed in the cloud safe from hackers and threats with security protocols like encryption. This means sensitive data like personal and business details are protected from breaches.
- Access Control: Cloud network security ensures that only the right people can access cloud data and resources, keeping unauthorized visitors out. Features like role-based access and multi-factor authentication (MFA) grant access to only authorized users, preventing breaches and misuse.
- Peace of Mind: Knowing that your cloud data and applications are secure means less stress about breaches. With strong security protocols in place, you can focus on other important things like innovation and achieving business goals, without constantly worrying about cyberattacks.
- Cost-Effective: Effective cybersecurity measures save millions of dollars every year. A single attack can help you lose significant revenue, loss of sales, and downtime. As prevention is more cost-effective than cure, investing in cloud security saves more costs than dealing with an attack.
- Compliance Needs: Cloud security measures like penetration testing help you meet industry standards for data protection, such as GDPR, HIPAA, ISO 27001, etc. Non-compliance can lead to legal problems, fines, and reputation damage.
- Scalability: Whether you’re a startup or a growing business, most cloud security protocols can easily adjust to your security needs. They can scale up or down based on your requirements, while certain practices like penetration testing, allow pay-as-you-use, without compromising on security.
- 24/7 Monitoring: Network security monitoring (NSM) always keeps an eye on threats and fixes security issues before they become big problems. Additionally, measures like firewalls and access controls offer round-the-clock surveillance.
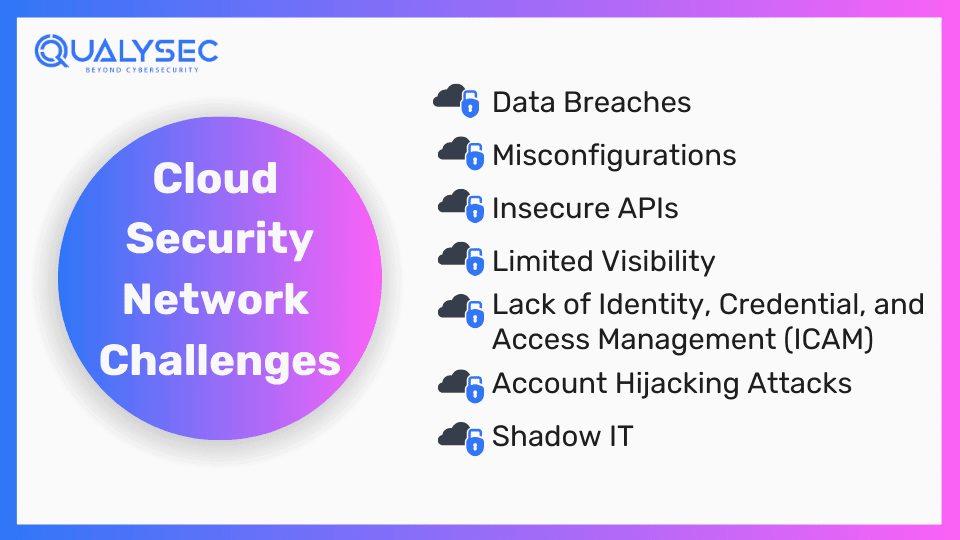
What are the Challenges to Cloud Security Networks?
Cloud computing is so powerful in accelerating business operations, that it comes with a wide range of challenges. One of the main reasons these challenges arise is due to organizations failing to understand network security in cloud computing, specifically where the obligations of the cloud service provider (CSP) end and where they begin in the shared responsibility model.
Cloud Network Security Challenges
- Data Breaches: Data breaches are the top concern in cloud security – and for good reason. Many data breaches have been recorded in the past that have led to the loss of billions of dollars, brand image, and market value.
- Misconfigurations: Take the example of Cpital One’s cloud misconfigurations in 2019 that exposed account details of 100 million customers. Cloud misconfigurations are the errors, gaps, or glitches that pose risks to cloud data and applications.
- Insecure APIs: If the APIs integrated within the cloud do not have proper authentication and authorization mechanisms, they can be easily exploited by attackers. Poorly configured APIs can expose sensitive data and allow unauthorized access.
- Limited Visibility: With new applications and huge amounts of data, it can be difficult to see what’s going on. Limited visibility of cloud networks can lead to misconfigurations and improper security coverage, resulting in data breaches and cyberattacks.
- Lack of Identity, Credential, and Access Management (ICAM): ICAM is a framework of technologies and policies that manage who can access the cloud data and resources. Lack of ICAM measures can lead to unauthorized access and data breaches.
- Account Hijacking Attacks: This occurs when the attacker takes over a user’s cloud account to gain authorized access to sensitive data. Account hijacking can happen due to a lot of reasons, such as weak passwords, improper coding, stolen credentials, cloud misconfigurations, etc.
- Shadow IT: Shadow IT is the hardware, software, or other systems and devices used by cloud users that aren’t allowed by the IT team. As a result, it can cause network bandwidth issues, compliance risks, and data breaches.
Cloud Security Network Best Practices
Now that we have understood what the common cloud security network risks are, it’s time to check out measures that can prevent these unfortunate events.
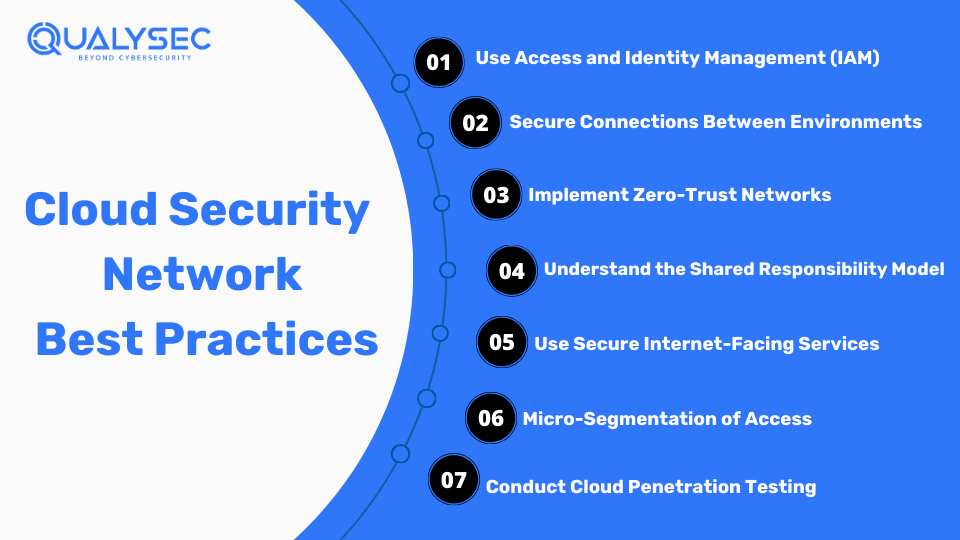
1. Use Access and Identity Management (IAM)
Managing who is allowed to access the cloud data and resources is critical in preventing unauthorized access. You need IAM services to implement role-based access controls or least privilege measures. Cloud platforms also offer tools that can be integrated with on-premises solutions, such as the Active Directory. This mechanism provides a single sign-on (SSO) for cloud-hosted job roles.
2. Secure Connections Between Environments
Your work may be conducted on-premises, in the cloud, or across multiple cloud models. This is why it is essential to secure connections between these environments to keep your operations as private as possible. As a result, it reduces exposure to threats. Additionally, you can avoid disruptions of your workflow by using private access options. These options allow cloud users and on-premises users to communicate with APIs and services without an external IP address.
3. Implement Zero-Trust Networks
It doesn’t matter whether you are outside or inside your network, the zero-trust security model ensures nothing, and no one is trusted by default. It allows cloud users to change access controls from the network perimeter to individual users and devices.
4. Understand the Shared Responsibility Model
Every cloud service provider (CSP), be it AWS, Google Cloud, or Azure, follows a shared responsibility model when it comes to cloud security. This model defines the different areas of security in the cloud, some of which are managed by the CSP while others are managed by the user. For example, the hardware security of the cloud is managed by the CSP while cloud infrastructure and application layers are managed by the user.
5. Use Secure Internet-Facing Services
It’s always best to restrict access to your cloud resources from the internet unless it is necessary. However, if you can’t seem to avoid it, you can still limit access to the network in the cloud. This includes security measures for DDoS attacks, identity-aware access control, web application firewall (WAF), and threat detection with real-time monitoring, logging, and alerting.
6. Micro-Segmentation of Access
Even within your cloud network, it’s important to regulate and manage communication between different applications and services. Micro-segmenting prevents lateral movement in detailed security policies to control traffic, especially if an attacker infiltrates the network.
7. Conduct Cloud Penetration Testing
If you want to know what your security flaws are and how you can strengthen them, perform cloud penetration testing. It is the process where pen testers or ethical hackers use simulated attacks on the target environment to detect security vulnerabilities. Along with that, their reports include remediation strategies for the found vulnerabilities. So, if you want to secure your cloud network, perform penetration testing at least once a year.
Qualysec Technologies has been securing cloud applications and networks for a while now. We are proud to say that we haven’t had a single data breach from the applications we have secured. Talk to our cybersecurity expert if you want to secure your cloud environment.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Cloud security networks are constantly advancing, with AI and machine learning capabilities being added to every possible technology. It’s just a matter of time before everything gets automated, even cyberattacks. Businesses must take cloud network security seriously and implement the security measures mentioned above to protect data and applications hosted by the cloud.
Therefore, it is important to partner with a reliable penetration testing company like Qualysec. We can test your cloud environment and report to you the security weaknesses and their mitigation strategies quickly.
Want to see how a cloud penetration testing report can help you enhance your security? Download a real sample cloud pen test report below!
Latest Penetration Testing Report

FAQs
Q: How to secure cloud networks?
A: There are various ways to secure cloud networks, such as:
- Conduct Cloud Penetration Testing
- Secure Connections Between Environments
- Implement Zero-Trust Networks
- Use Secure Internet-Facing Services
Q: What is cloud security control?
A: Cloud security control is a set of measures, tools, and policies that protect cloud environments from vulnerabilities and minimize the risks of cyberattacks. There are various cloud security controls, such as Single Sign-On (SSO), multi-factor authentication, and access control.
Q: What are the types of cloud security?
A: There are different types of cloud security, such as:
- Network security
- Data security
- Endpoint security
- Application security
- Compliance requirements






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments