Application security audit help businesses discover vulnerabilities in their web and mobile applications that need fixing. Applications are the most used digital items for any IT industry. Since it is directly connected with the users, they are the main target of attackers. Hackers are trying new ways to breach applications every day, which is why businesses should prioritize cybersecurity.
The frequency and cost of security incidents are increasing, with roughly 2,200 daily attacks. Additionally, IBM reports that the average price of a data breach is $4.45 million. You don’t want something like this happening to you right?
So, to help businesses and individuals that handle digital applications, we bring you this blog. Here you will know the importance of application security audit, what it is exactly, and how it can save you from security risks.
What is an Application Security Audit?
For app developers, an application security audit is the best way to ensure that the app is secure and has all the necessary security measures. Additionally, it helps the companies check whether their app’s defenses are strong enough to prevent unauthorized access and cyberattacks. Third-party companies perform security audits using various automated tools and manual techniques.
The main goal of an application security audit is to detect vulnerabilities in the app that hackers could exploit for breaching. For example, the process checks whether the app has proper encryption measures, authentication & authorization, network security, API security, etc.
Security auditors review the application’s code and configurations to determine whether the app is performing as it should. After testing the application, they provide a report to the developers. This report contains the vulnerabilities they found and how to fix them. In addition, an app security audit also helps companies achieve the necessary industry compliance requirements.
Importance of Application Security Assessment or Audit
The goal of application security audit services is to provide clear and actionable reports that the developers can use to create secure apps. While some companies think it is a costly and time-consuming job, the trust is, that investing a small amount in security audit or application security assessment can help you a lot in the long run. Just ask those companies that handle huge amounts of sensitive data or face continuous cyberattacks.
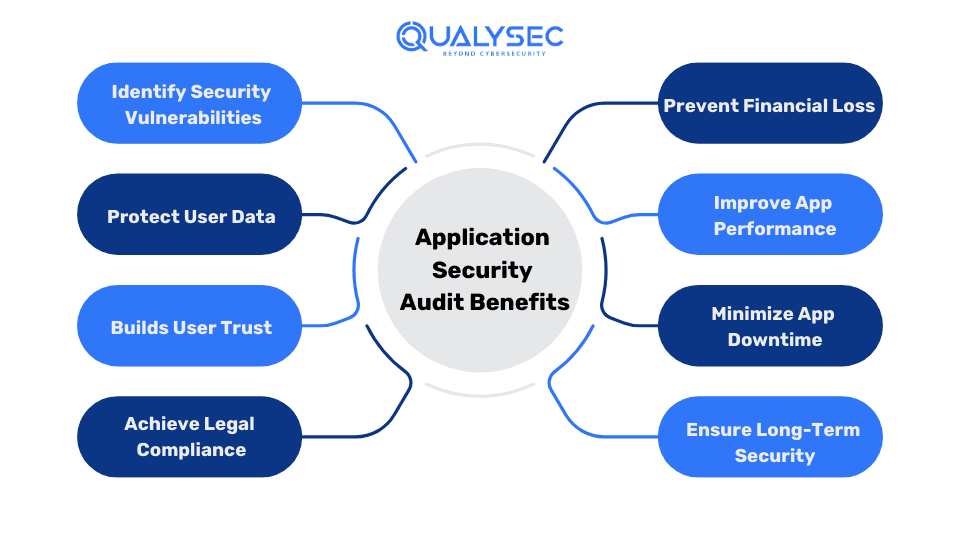
Let’s discuss some of the major benefits of application security audits:
1. Identify Security Vulnerabilities
Application security audits include security testing that helps detect vulnerabilities present in the app. Hackers are always looking for these vulnerabilities so that they can breach the defense and do malicious acts. Additionally, by adding security audits in the development cycle, developers can create secure apps before it reaches the users.
2. Protect User Data
Both web and mobile applications tend to store and manage sensitive user data, such as personal and financial details. Attackers are mostly likely to breach the app to steal this data and use it or their gain/ regular security audits help find and fix vulnerabilities that hackers could use for data breaches.
3. Builds User Trust
By preventing data breaches, you can gain the trust of your users. When they know that your application is regularly audited for security and undergoes application penetration testing, they will feel more confident in using it and may recommend it to their friends. Building user trust and loyalty is the only way to get long-term success.
4. Achieve Legal Compliance
Certain industries and regions have strict data protection laws that applications must adhere to. Not complying with these laws can lead to legal penalties, fines, and reputation loss. Security audits ensure all the application security compliance requirements are met with ease.
5. Prevent Financial Loss
Some applications, like e-commerce, handle financial transactions. Attackers may use techniques like payment gateway manipulation, OTP bypass, or coupon manipulation to steal your sales. Security audits uncover the weaknesses that may lead to such attacks.
6. Improve App Performance
Some attacks like the denial-of-services (Dos) flood the application with a huge amount of traffic and slow it down. By identifying and addressing these issues, security audits make the app smoother, faster, and more reliable user experience.
7. Minimize App Downtime
Attacks like DoS attacks, man-in-the-middle (MitM) attacks, SQL injection, and server-side request forgery (SSRF) attacks can disrupt app operations and cause downtime. As a result, you may lose loyal users and face financial loss with loss of sales. Security audits help find the vulnerabilities that cause these attacks.
8. Ensure Long-Term Security
Ongoing security audits maintain the long-term security of the application. By regularly auditing the app, you can stay one step ahead of the evolving threat landscape. Additionally, you can prevent vulnerabilities from the integrated APIs and third-party libraries.
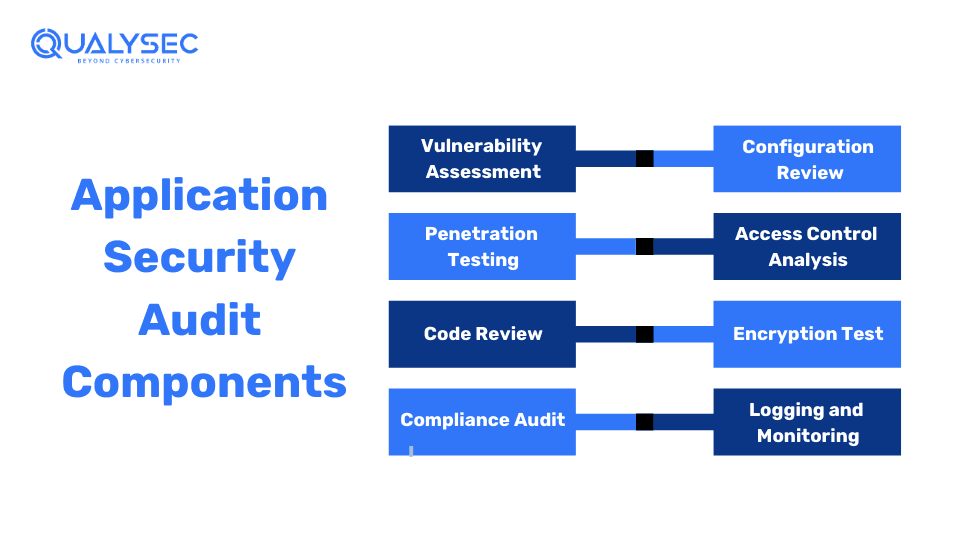
Key Components of Application Security Audits
Security auditors can perform a variety of audits that companies can choose. However, if the client chooses a comprehensive application security audit, then it must know what are the components involved.
1. Vulnerability Assessment
This process mostly uses automated vulnerability scanners like Nessus and MobSF to identify potential weaknesses in the application (both web and mobile). By discovering vulnerabilities, developers can prioritize which issues to fix first (starting from critical). It significantly reduces the risk of exploitation by cybercriminals.
2. Penetration Testing
Penetration testing is when cybersecurity professionals (also called “ethical hackers” simulate real-world cyberattacks to detect weak points. By mimicking real attackers, this security test helps developers understand how vulnerabilities could be exploited to carry out malicious acts. This process helps the developers address security issues proactively.
3. Code Review
This involves a thorough examination of the application’s source code to identify security flaws. This is done to ensure that the code follows all the security best practices and is free from vulnerabilities. Regular code reviews enhance the security of the application and protect it from potential attacks.
4. Compliance Audit
The application is checked against relevant legal and regulatory standards to ensure compliance. Certain data protection laws like PCI DSS, ISO 27001, and HIPAA make it mandatory for the app to have proper security measures. Not following it might result in legal problems and fines. Compliance audit ensures that these requirements are effectively met.
5. Configuration Review
This includes reviewing the application’s configuration settings to identify and rectify misconfigurations that may lead to a security risk. To maintain and secure and stable environment, proper configuration is essential. Additionally, it prevents unauthorized access and ensures that the application operates smoothly without any disruptions. Application security risk management plays an important role in this process by continually assessing and addressing potential security threats.
6. Access Control Analysis
This analysis checks how user permissions and designated roles are managed within the application. Applications that have proper access controls are better at preventing unauthorized access to sensitive data and resources. It ensures that only trusted individuals and those with proper job roles can have access.
7. Encryption Test
Data encryption is one of the most fundamental security measures to protect sensitive data. Only those with a decryption key are allowed to view this data. Hence, this security test ensures that proper encryption measures are in place to protect confidential user information and intellectual property.
8. Logging and Monitoring
This evaluates the logging and monitoring systems and ensures that all security events are accurately tracked and analyzed. Effective logging and monitoring are essential to detect and respond to potential security incidents promptly. As a result, this enhances the application’s security and enables quick action to address security threats and protect against future attacks.
Want to conduct an application security audit for your web or mobile app? Contact our cybersecurity experts and secure your app from evolving threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
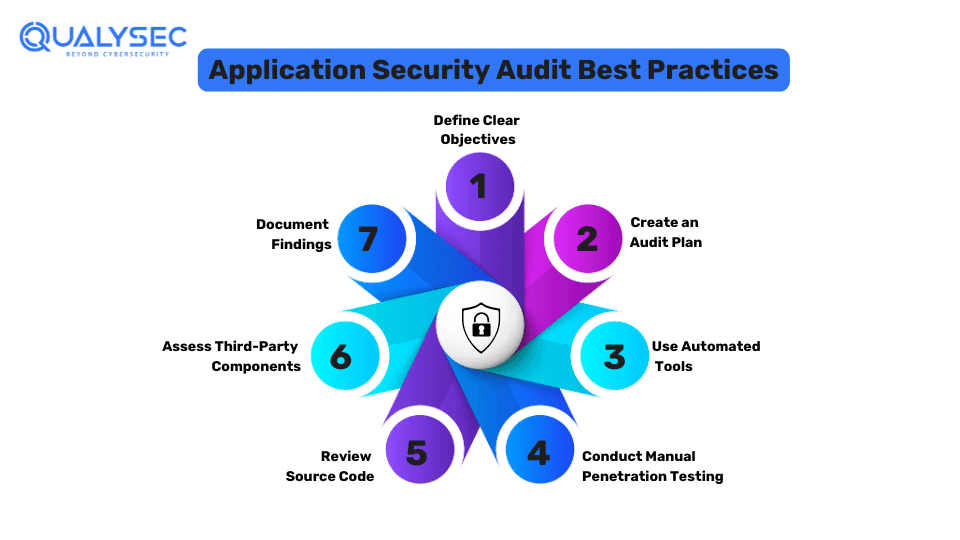
Best Practices For Conducting Application Security Audit
A comprehensive app security audit helps keep data and resources safe from hackers. The process involves thoroughly evaluating the application to identify security and address vulnerabilities. Here is the list of application security audit best practices:
1. Define Clear Objectives
Set specific goals for the security audit, such as identifying vulnerabilities, achieving compliance, or enhancing security measures. Clear objectives guide the audit process and ensure all the critical aspects are thoroughly examined and necessary fixes are implemented.
2. Create an Audit Plan
Develop a detailed plan that outlines the scope, timeline, and methodology of the audit. In addition, a strategic plan helps ensure the comprehensive evaluation of the application’s security. It helps cover all critical areas and identify potential vulnerabilities.
3. Use Automated Tools
Use automated scanning tools to scan the application for known vulnerabilities. These tools can quickly find security issues like SQL injection, outdated software, hardcoded passwords, and misconfigurations. It then provides the auditor with a broad overview of the application’s security posture and highlights areas that need improvement.
4. Conduct Manual Penetration Testing
Automated scanning is quick and effective, but it might miss many other critical vulnerabilities. This is where manual testing comes in. In this process, pen testers try to find and exploit the vulnerabilities to check the strength of the current security measures. Therefore. this is a critical step as it mimics how a real attacker would try to breach the application.
5. Review Source Code
Perform an in-depth review of the application’s source code to identify security flaws. Code reviews ensure that the application follows security best practices and is free from vulnerabilities. As a result, regular reviews enhance the app’s code quality and security.
6. Assess Third-Party Components
This includes evaluating the security of third-party libraries and APIs used in the application. Additionally, ensure all these components are up-to-date and free from vulnerabilities. Since hackers can also penetrate through these components, it is essential to maintain their security as well.
7. Document Findings
Record all the found vulnerabilities in a detailed report. Documentation helps the developers know what security vulnerabilities are in the app and how to fix them. It also helps track the remediation efforts and provides a clear reference for future audits.
Want to see a real application security testing report? Click the link below and check how the vulnerabilities are recorded, and remediation steps are recommended!
Latest Penetration Testing Report

Conclusion
Application security is a bigger deal than most people realize. Hence, it is essential to understand how application security audits work. You can make your application and the data stored in it more secure by finding and addressing security vulnerabilities. Each vulnerability makes it easy for a hacker to breach your application and access sensitive data.
As a business, you should perform security audits regularly. Check for vulnerabilities and ensure you comply with all the necessary industry standards. Remember, investing a small amount in prevention is better than spending millions in recovery.
FAQs
Q: What is application security in cyber security?
A: Application security in cybersecurity refers to the practices that secure the code and data of applications from security threats. For example, security audits, vulnerability assessments, and penetration testing.
Q: What is a security audit in cybersecurity?
A: A security audit is an independent review of the IT system that helps in identifying vulnerabilities that could lead to cyberattacks. Additionally, it helps companies comply with necessary industry regulations.
Q: How many types of cybersecurity audits are there?
A: There are two main types of cybersecurity audits: internal and external. Internal audits are conducted by the employees of the organization, while an independent third-party audit firm conducts external audits.
Q: How to prepare for a cybersecurity audit?
A: To prepare for a cybersecurity audit, you must:
- Define the scope
- Conduct vulnerability assessment and penetration testing
- Implement necessary security measures
- Gather evidence to achieve compliance






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments