Cloud computing has transformed businesses in terms of retrieving, storing, and managing data. Cloud security vulnerability is one of the major concerns in cloud computing as it describes the cloud environment’s weakness and is exploited by attackers. Businesses need to understand these vulnerabilities as they can damage a business’s data, apps and infrastructure. Qualysec Technologies is here to evaluate the cloud security vulnerabilities, the possible causes, different types of Cloud Security VAPT, and how businesses can be safe from them.
Understanding Cloud Security VAPT & Vulnerability
Cloud security vulnerability is the weakness in cloud environments that a hacker can exploit to intrude into his target’s cloud space, steal data, or adversely disrupt services. However, these vulnerabilities exist because of misconfiguration, weak access control, unpatched software, insecure API, or even insider threats. Risks common to this include data breaches, identity theft, denial-of-service attacks, and so on. Therefore, businesses need to protect data by enforcing strong Cloud Security VAPT and making it encrypted, monitoring security regularly and providing compliance with industry standards are the ways to mitigate these threats. Since the adoption of the cloud is growing, organizations need to be proactive in the area of strengthening the security posture for critical information while ensuring the continuity of doing business in the fast-moving cyber threat landscape.
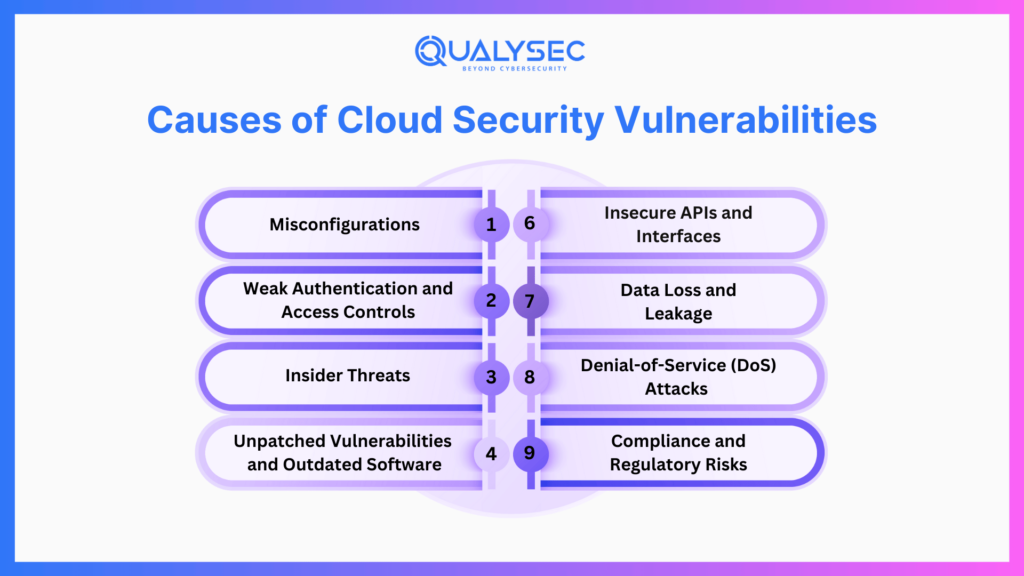
Causes of Cloud Security Vulnerabilities
The concept of cloud computing has come a long way, which means that it has made the implementation of business processes much easier. That is where this becomes interesting because as cloud adoption grows more, that also increases the security risks. There are many factors in Cloud Security VAPT such as misconfiguration and highly sophisticated cyber threats. To secure the cloud environments of an organisation, it is important to understand these causes.
Misconfigurations
Misconfiguration is one of the most common reasons for cloud security vulnerability. Cloud resources are left open to attacks as organizations set up their cloud resources poorly and fail to secure them. Some common misconfigurations include:
- Public cloud storage buckets (some examples include Amazon S3)
- Weak or default security settings
- Improper access control policies
- Unrestricted inbound/outbound traffic
Unauthorized access, the leaking of data, and even full system compromise can occur through misconfigurations.
Weak Authentication and Access Controls
This however is a big load in cloud environments where IAM is a much more important enforcing force. When the user is authenticating using weak methods, it turns out that unauthorized users can gain access to sensitive resources. Some major issues include:
In other words – using weak or reused passwords.
- Lack of Multi-Factor Authentication (MFA)
- Overprivileged user accounts
- Poor session management
However, cloud systems are subject to infiltration by cyber criminals without strong authentication and adequate access control policies.
Insider Threats
Some employees, contractors and third-party vendors can be a big security risk. The threats may be malicious (intentional insider threats) or negligence (unintentional insider threats). Common insider threats include:
- Unauthorized data access and sharing
- Misuse of credentials
- Accidental data deletion or leakage
- Poor handling of security configurations
To mitigate insider threats, organizations are required to implement strict access control measures and monitor the activity of the users.
“Check out our recent articles on Cloud Security Testing and Cloud Penetration testing to gain deeper insights into securing cloud environments.”
Unpatched Vulnerabilities and Outdated Software
Security patches and updates are being released by the cloud provider. But, to leave a vulnerability un-updated can be dangerous by exposing applications in the cloud, operating system and security software. For cybercriminals, it is often using known vulnerabilities of outdated software that:
- Will execute remote code on their cloud systems.
- Steal sensitive data
- Deploy ransomware attacks
- Patching and updating automatically are necessary for security.
Insecure APIs and Interfaces
Between cloud services and applications, there are Application Programming Interfaces (APIs) and management interfaces for communication. But insecure APIs can bring major security risks such as:
- Weak authentication mechanisms
- Unencrypted data transmission
- Exposure of sensitive API keys
- Excessive API permissions
These weaknesses can be exploited by attackers to unlawfully obtain access to other’s data, data manipulation, or attack cloud resources.
Data Loss and Leakage
Security of the data is an issue of significant importance in cloud computing. Data loss or leakage can be caused by any of the following depending on the situation.
- Accidental deletion of critical files
- Poor backup policies
- Lack of encryption in data storage and transmission
- Data exposure due to misconfigured permissions
To keep the data from being leaked or lost, encryption, backups regularly and rigorously enforced rules and policies on what people can and can’t do are also essential.
Denial-of-Service (DoS) Attacks
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks are the usual targets for Cloud environments. Cloud servers get overwhelmed with excessive amounts of traffic in these attacks and one of the results is:
- Service disruptions
- Performance degradation
- Increased operational costs
DDoS protection services are also offered by cloud providers, but organizations also need to implement rate limiting and traffic filtering to manage risks.
Compliance and Regulatory Risks
One of the security vulnerabilities for a company to have is failure to comply with industry regulations (i.e. GDPR, HIPAA, PCI DSS). Non-compliance issues include:
- Lack of proper data encryption
- Poor audit logging practices
- Failure to conduct security assessments
At the same time, all organizations are required to align their Cloud Security VAPT practices with the requirements of the regulations.
“Also explore: Top Cloud Computing Vulnerabilities & How to Address Them?“
- Combines manual & automated testing for accurate results
- Runs 200+ industry-standard test cases
- Zero false positives – all findings are manually verified
- CI/CD integration for smooth DevSecOps workflows
- Get a real-time dashboard to track and manage vulnerabilities
- Receive developer-friendly reports with clear remediation steps
- Share publicly verifiable pentest certificates
- Supports compliance with SOC2, ISO27001, PCI-DSS, HIPAA, and more
- Trusted by startups to enterprises in Fintech, SaaS, Healthcare, and beyond
Types of Cloud Security Vulnerabilities
Cloud security vulnerabilities are vulnerabilities in the cloud environments that can be exploited by cybercriminals to gain access to data, applications and the cloud infrastructure. These vulnerabilities come from misconfiguration lack of security controls, and the evolution of cyber threats. However, these are the major types of Cloud Security VAPT.
Data Security Vulnerabilities
Cloud computing is one of utmost concern in terms of data security. Breaches, loss and unauthorized access are the consequences when it comes to vulnerabilities in data security.
- Data Breaches – Unauthorized access to sensitive data due to weak security controls.
- Data Loss – Accidental deletion, ransomware attacks, or corruption of critical data.
- Insecure Data Transmission – No encryption of data being sent over the internet can be intercepted by hackers.
Mitigation:
- Encrypt your data in the rest and transit.
- Implement robust access control measures.
- Secure backup solutions will recover the data.
Identity and Access Management (IAM) Vulnerabilities
Identity and access management (IAM) errors in the cloud expose such environments to unauthorized access and privilege escalation attacks.
- Easily guessable passwords – Attackers get into cloud accounts by being able to easily guess passwords.
- Stolen credentials – Without MFA, attackers can exploit stolen credentials.
- Excessive Permissions – With such excessive permissions, if their credentials get compromised then users may pose a security risk.
Mitigation:
- All users should use strong passwords and require at least an MFA.
- Improve IT workloads by following the principle of least privilege (PoLP).
- Have users’ access permissions audited and updated regularly.
Infrastructure Vulnerabilities
Cloud infrastructure, Virtual Machines (VMs) containers, and storage services contain misconfigurations and security threats.
- Misconfiguration – Exposed storage buckets can also result in data leaks if they are misconfigured.
- VM – Attackers can exploit vulnerabilities present within virtualized environments too, known as Virtual Machine (VM) Exploits.
- Contingency Security Issues – Unsecured container leads to unauthentic access.
Mitigation:
- Use automated cloud security posture management (CSPM) tools.
- Updates include updating and applying security patches, etc.
- Network segmentation and firewalls should be implemented strongly.
“Related content: A Guide to Infrastructure Security in Cloud Computing“
API and Application Security Vulnerabilities
Cyber attacks target frequent cloud-based applications and APIs. It can also result in data exposure and service disruptions if weak security is present in the APIs.
- Poorly protected APIs – This allows attackers to govern any clouds.
- Code – These attacks are often vulnerable to SQL injection and cross-site scripting (XSS).
- Zero-Day Vulnerabilities – Newly discovered software flaws, the exploitation of which has simultaneously not been patched, are known as zero-day vulnerabilities.
Mitigation:
- Employ gateways using APIs and enforce a strong authentication.
- Perform regular in-depth Cloud Security VAPT and vulnerability tests.
- Keep software and applications updated.
Compliance and Legal Vulnerabilities
Not complying with regulatory requirements is liable to get you legally and historically fired.
- Non-Compliance with Regulations – Violating GDPR, HIPAA, or PCI DSS leads to fines and reputational damage.
- Inadequate Logging – This makes it hard to discover that your security has been breached.
- Security Gaps in Third-party Cloud Services – Organizations are facing the risks of third-party cloud services security gaps which can lead to breaches.
Mitigation:
- Bring the Cloud Security VAPT policies into sync with organizational, legal, and regulatory requirements.
- Regularly audit and compliance assessments.
- Monitor third-party vendors for security risks.
How Qualysec Technologies Can Help
Penetration testing, vulnerability checking and security consultancy services are some of the services Qualysec Technologies offers for businesses to detect, fix, and deal with security threats. They work with clientele in the financial, healthcare, e-commerce, technology, and cloud-based enterprises sectors offering them customized services.
Penetration Testing (VAPT)
Qualysec Technologies is one of VAPT‘s core offerings. The service identifies the security weaknesses in an organization’s IT infrastructure, network, and applications. Ethical hackers from Qualysec fake actual world cyberattacks to check on system weaknesses and give remedy approaches to enhance its safety.
Cloud Security Testing
The challenges of security increase to the extent enterprises migrate to the cloud. It provides organizations with the capability to discover misconfigurations in their AWS, Azure, And Google Cloud environment, weak authentication methods and API security flaws. They examine and validate their Cloud Security VAPT to the industry standards and best practices.
Web & Mobile Application Security Testing
Since the web and mobile applications are now cybercriminals’ targets, Qualysec offers a complete security test to reveal and fix the vulnerabilities of SQL injection, cross-site scripting (XSS), broken authentication, insecurity APIs, etc. Their main testing methodologies comply with OWASP standards, so the applications are as well protected as possible.
IoT and Embedded Security Testing
Today, hackers have new attack vectors due to the growing adoption of IoT devices. Qualysec assists businesses in securing their IoT ecosystem by discovering firmware weakness, weak encryption and insecure communication protocols to keep the devices resistant to cyber-attacks.
Compliance & Security Consulting
Qualysec Technologies helps organizations achieve compliance with ISO 27001, GDPR, HIPAA, PCI DSS, and SOC 2 regulations. They act as their customers’ security consultants with advice on risk management, security architecture, and incident response planning to help businesses stay in compliance and secure.
Latest Penetration Testing Report

Conclusion
Also, the Cloud Security VAPT poses a lot of risks to the company and it can be handled with a proactive security policy. Knowing these cloud security vulnerabilities and implementing sound security controls, an organization would be able to secure its cloud environment away from cyber attacks. It is necessary to have regular security assessments, strong access control, encryption and continuous monitoring for a secure cloud infrastructure. With cloud adoption an inevitability in the world, securing cloud assets should be of top priority to organizations of all sizes. Businesses can enjoy cloud computing’s benefits while limiting security issues and include the mass adoption of big data with cloud storage. Contact Qualysec Technologies to secure your cloud today!






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments