Do you remember when you had the last cybersecurity audit? If you have a business online, you will require cybersecurity audits to improve your defenses against cyber threats. Cybersecurity auditors help businesses identify security vulnerabilities, ensure compliance, and help prevent data breaches.
According to Forbes, the frequency of data breaches increased by 72% between 2021 and 2023, resulting in more than 343 million victims. Additionally, another survey shows that the average cost of cybercrimes in 2022 was $8.4 trillion and is expected to hit more than $23 trillion in 2027. This is all the more reason to invest in proper cybersecurity audit consulting services.
In this blog, we are going to explore the ins and outs of cybersecurity audit, why it is important for businesses, and what are its best practices. If you are a business owner or an IT professional, here you will know the importance of security audits in this interconnected digital world.
What is a Cybersecurity Audit?
A cybersecurity audit involves a comprehensive review and analysis of your digital assets and IT environment. It helps organizations detect vulnerabilities and threats, displaying weak spots and high-security risks. A security audit in cyber security aims to find security flaws through which unauthorized access and data breaches could occur.
The auditors use various technologies and methodologies to evaluate how well an organization’s networks, applications, devices, and data are protected against various security risks and threats. These audits can be performed by the internal security team, but it is better and recommended that a third-party firm perform them.
Why Cybersecurity Audit is Important to a Business?
Auditing in cyber security includes an in-depth analysis of the organization’s current IT environment. The audit offers a detailed report that highlights security weaknesses and solutions to fix them.
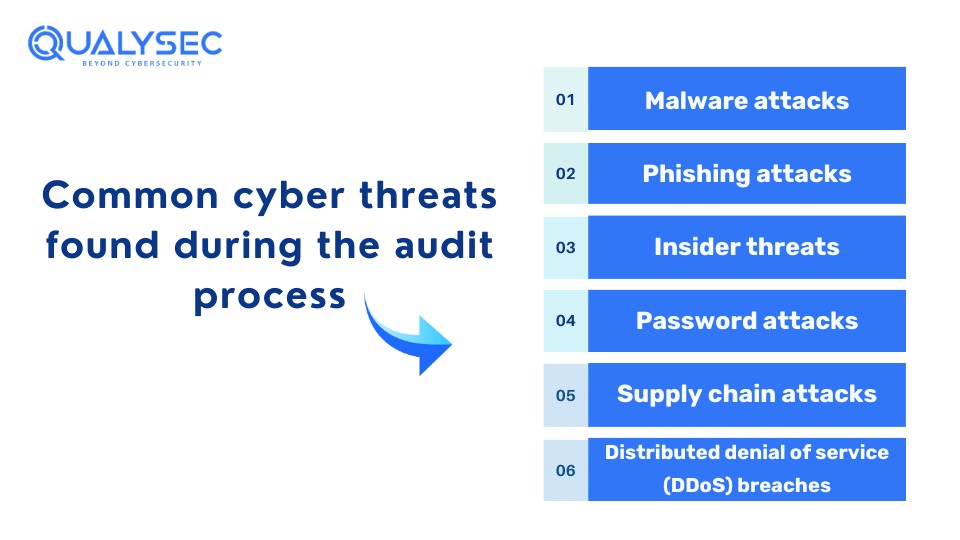
Benefits of Conducting Cybersecurity Audits
Cybersecurity audits help businesses enhance their overall security posture, along with meeting compliance standards set by respective industries.
-
Identifying Vulnerabilities in the IT Environment
By various techniques, cybersecurity auditors find vulnerabilities present in the organization’s IT infrastructure, network, and security measures. These vulnerabilities can become potential entry points for cyberattacks, which can now be addressed by organizations.
-
Enhanced Security
By finding and fixing vulnerabilities present in the IT environment, organizations can implement effective measures to enhance their overall security posture. This may include updating security protocols, implementing authentication mechanisms, and including encryption techniques to secure sensitive data. A cyber security audit and compliance process ensures that these measures are in place, helping organizations meet regulatory requirements and protect against potential threats.
-
Regulatory Compliance
Compliance with industry laws and regulations such as PCI DSS, GDPR, HIPAA, SOC 2, etc. is crucial and mandatory for organizations. A cybersecurity audit helps organizations meet necessary compliance requirements and avoid the risk of legal penalties and reputation damage.
-
Risk Management
By conducting regular security audits, organizations can stay updated with the evolving cyber threat landscape. They can make informed decisions with their risk mitigation strategies and allocate their resources accordingly.
Increase Confidence Among Stakeholders and Clients
With regular security audits in cyber security, organizations can maintain trust and confidence in stakeholders, as well as clients, partners, and investors. Regular audits show that you prioritize the security of their data and interests. Furthermore, it will show that it is safe to do business with your organization.
Has it been a long time since you have performed a security audit for your business? Don’t worry, contact us, and get immediate cybersecurity audit services!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
How cyber security risks are managed in an Organisation?
It is not enough only to have security measures in place, consistent security auditing is also important. When was the last time you updated your security plans? Is your organization complying with necessary industry regulations? Are all your digital products and networks free from vulnerabilities? If you are unsure about all of these, then it is time for you to perform a cybersecurity audit.
Top indicators that you need better security measures:
- Outdated Technology: If you have older technologies like old software or outdated policies and services, it can leave you vulnerable to evolving cyber threats.
- Thinking that your Business is “Too small” for Cybersecurity Audit: If you believe that only big companies require cybersecurity audits, then think again. Most companies, regardless of size, are prone to cyberattacks and data breaches. Whether you are a startup or a Fortune 500 company, regular cybersecurity audits can benefit all.
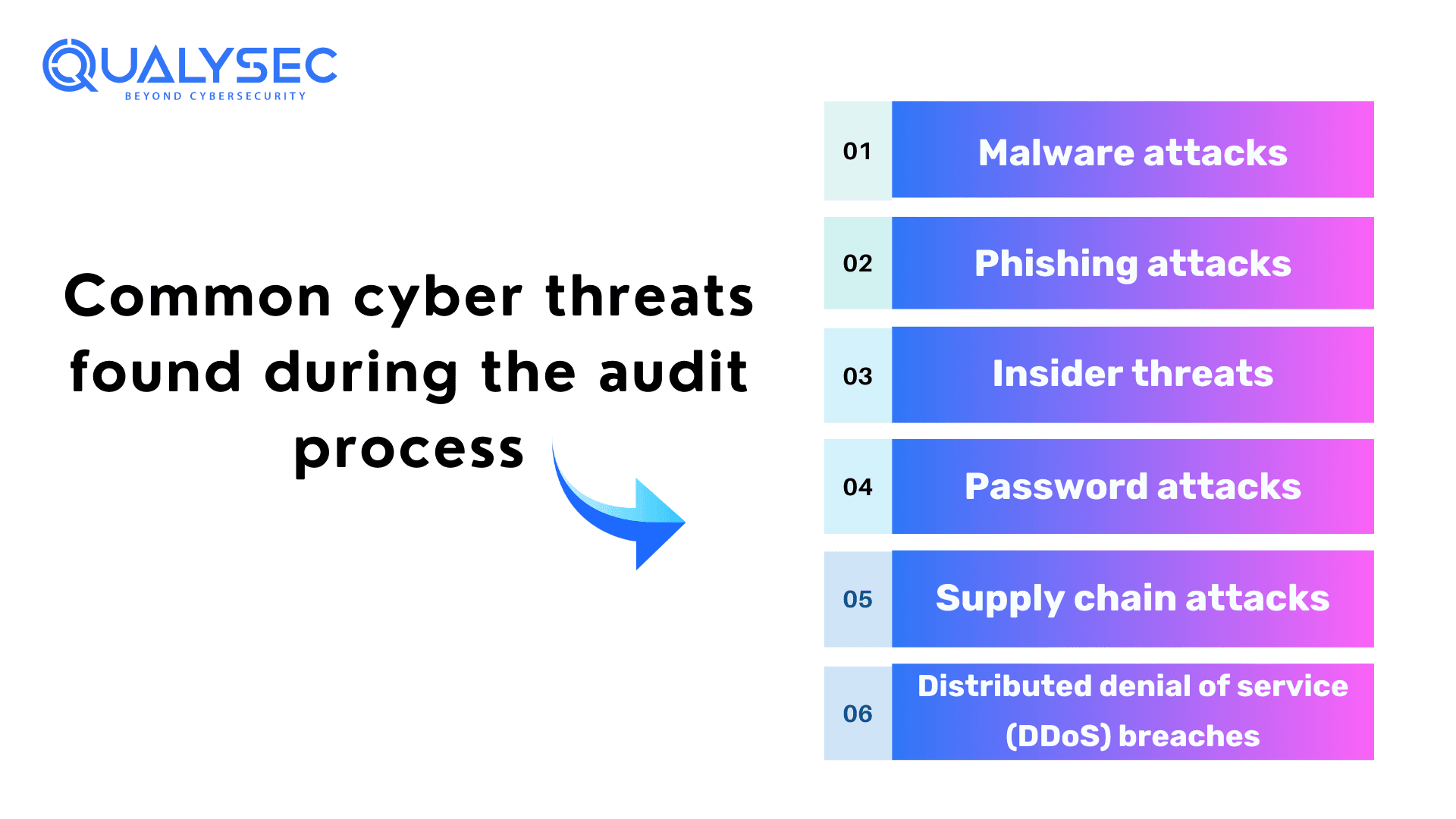
Scope of Cybersecurity Audits – What Does it Cover?
Cybersecurity audits provide a comprehensive analysis of the organization’s security posture. Their main goal is to identify vulnerabilities, risks, and threats that may lead to cyberattacks. To keep your data and business safe, it is important to understand what a cybersecurity audit covers.
 Data Security
Data Security
It involves a complete review of network access control, encryption use, and data protection at rest, along with how safe your data is during transmission.
Operational Security
This includes a complete look at all the security policies, procedures, processes, and controls in your data loss prevention strategy.
Network Security
In this review, the auditors review all network controls and security protocols. In fact, they will let you know if your security measures are working efficiently or not. Additionally, this reviews anti-virus configurations, security monitoring capabilities, etc.
System Security
It covers hardening processes patching processes, role-based access, privileged account management, etc.
Physical Security
In this security audit, auditors review the state of all physical devices that are used to access your network. This covers disk encryption, biometric data, role-based access controls, multi-factor authentication, etc.
External Vs Internal Security Audits
Cybersecurity audits can be conducted by either internal security teams or external cybersecurity firms. Both audits offer distinct advantages and serve different purposes.
External cybersecurity audits are performed by professionals from specialized cybersecurity audit companies. They have in-depth knowledge of security protocols and use advanced tools and techniques to conduct a comprehensive audit.
On the other hand, internal cybersecurity audits are conducted by the organization’s in-house security team. They can be performed more frequently and have the advantage of having direct access to the organization’s internal structure.
| External Cybersecurity Audit | Internal Cybersecurity Audit |
| Done by an external or third-party penetration testing provider. | Done by the organization’s in-house security team. |
| It is a cost-effective approach. | It is usually expensive, as the organization has to maintain an in-house team. |
| They review the effectiveness of your current security measures and how much damage a hacker can do. | Since the in-house security team has all the access to the internal structure, they fail to mimic real hackers, who don’t have full access. |
| It can’t be conducted frequently, as it is outsourced. | Since it is conducted by the in-house team, it can be conducted more frequently. |
| It is necessary to meet necessary regulatory compliances. | Internal security audits are not enough to meet regulatory compliances. |
How Often Should You Conduct a Cybersecurity Audit?
The frequency of conducting a cybersecurity audit relies on multiple factors such as the size of the organization, nature of the business, level of security risks, and required industry regulations. Generally, it is suggested to perform cybersecurity audits regularly to strengthen the security of your business.
Here are a few instances when you should conduct a cybersecurity audit:
- Annual Audits: It is recommended to perform cybersecurity audits at least once a year to assess the overall security posture. In addition to that, annual audits also allow you to stay updated with evolving cyber threats.
- Significant Change: If your organization went for a significant change in terms of network, application, or any other digital product, it could attract new threats. In such cases, you should perform security audits to safeguard your business.
- Regulatory Requirements: Certain industries make it mandatory to perform regular security audits to ensure data protection such as PCI DSS, SOC 2, HIPAA, GDPR, etc.
Best Practices to Perform Cybersecurity Audits
To conduct a comprehensive and effective cybersecurity audit, you need to follow the best practices. Here are some recommended steps that will help:
Establish Clear Objectives
Define specific objectives and goals of the audit. For example, evaluating network security controls, the effectiveness of access management processes, identifying potential vulnerabilities, etc.
Review Compliance Standards
Different industries have different sets of security regulations. Make sure your auditor knows the proper industry standard they need to comply with.
Vulnerability Assessment and Penetration Testing (VAPT)
Vulnerability assessment and penetration testing (VAPT) is a process in which cybersecurity professionals use automated tools and manual testing techniques to find vulnerabilities. They will provide a detailed report of the found vulnerabilities and steps to fix them.
Wondering what a VAPT report looks like? Click below and download one!
Latest Penetration Testing Report

Top 10 Cybersecurity Audit Tools
There are several security tools available for various tasks. However, here is a list of the top 10 cybersecurity audit tools that are most effective:
-
- Nessus
- Nmap
- Wireshark
- Metasploit
- Burp Suite
- Kali Linux
- Software Testing
- OpenVAS
- SQLMap
- Aircrack-ng
Conclusion
As a business owner, you must understand the risks and threats associated with businesses operating online. Your applications and network are not safe from hackers and cyberattacks. With the increasing cases of data breaches, it is necessary to perform regular cybersecurity audits. Additionally, it helps improve the overall security posture and comply with required industry standards.
A proper cybersecurity audit focuses on data security and highlights the weaknesses in your network and IT infrastructure. By identifying vulnerabilities before hackers, organizations stay protected from evolving cyber threats. Therefore, investing in regular cybersecurity audit consulting services not only enhances the security of your business but also maintains your reputation among clients and stakeholders.
FAQs
Q: What are the types of audits in cybersecurity?
A: Some common types of audits in cyber security include:
-
- Penetration testing
- Vulnerability assessment
- Risk assessment
- Compliance audit
Q: What is audit methodology in cybersecurity?
A: The audit methodology in cybersecurity involves a comprehensive analysis of the entire IT infrastructure. The methods help identify vulnerabilities through which cyberattacks can occur. In addition, it also helps meet required industry standards.
Q: What is the main purpose of a security audit?
A: The main goal of a security audit is to protect sensitive data, identify security flaws, create new security measures, and track the effectiveness of security protocols.
Q: Who can do a cyber security audit?
A: Though an in-house security team can perform security audits, it is recommended to perform cybersecurity audits through a specialized third-party firm. This is because a third-party firm can provide better, accurate results and the reports are more authentic.






 Data Security
Data Security

















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)





























































































































































































































































































































































































































































































0 Comments