Network VAPT is a security evaluation process where experts test user networks to find vulnerabilities that attackers can exploit. The main goal of network VAPT (vulnerability assessment and penetration testing) is to find security flaws in networks, systems, hosts, and network devices that hackers can use for unauthorized access and data breaches.
As per research by GlobeNewswire, cybercrime costs will reach $10.5 trillion annually by 2025. Around 43% of these cyberattacks happen on the organization’s network. With roughly 2,200 attacks every day, it is inevitable to secure the main component of the IT infrastructure – the network.
Therefore, in this blog, we are going to discuss how network VAPT is the best solution to prevent attacks on the network and its components. Additionally, we will offer tips to help you choose the best network VAPT provider.
What is Network VAPT?
Network VAPT is conducted to identify exploitable vulnerabilities in networks and systems to help reduce or mitigate security risks. Network components like firewalls and access points are thoroughly tested to reduce the potential attack surface and prevent unauthorized access.
Once the base layer of the network is protected and proper security measures are implemented, the risk of the top layers is also automatically reduced. Since every digital asset (applications and APIs) is connected to the network, a breach in its infrastructure can make everything vulnerable.
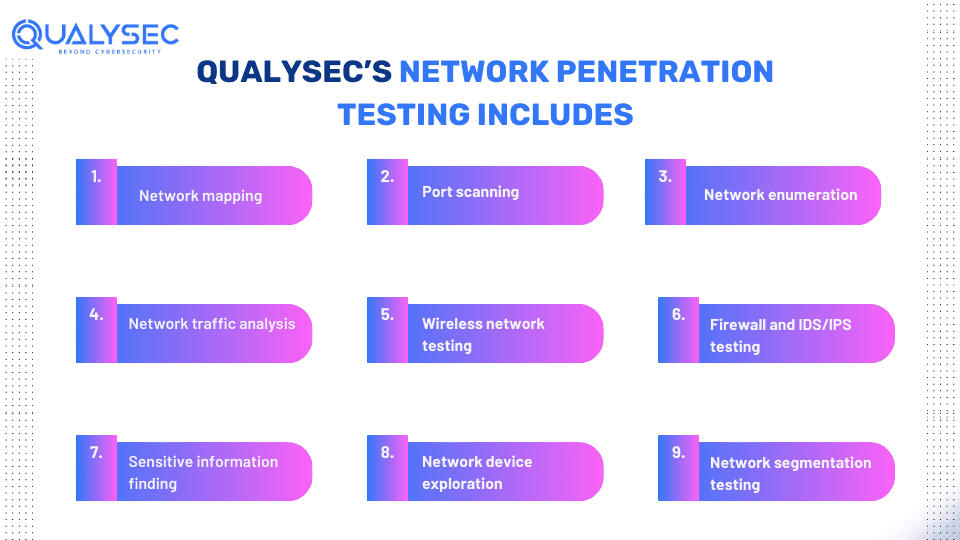
Network penetration testing involves using specialized tools and techniques to discover security vulnerabilities in the network that can lead to cyberattacks. After identifying all vulnerabilities, the testing team then recommends possible solutions. As a result, organizations can quickly address them and secure their network perimeter.
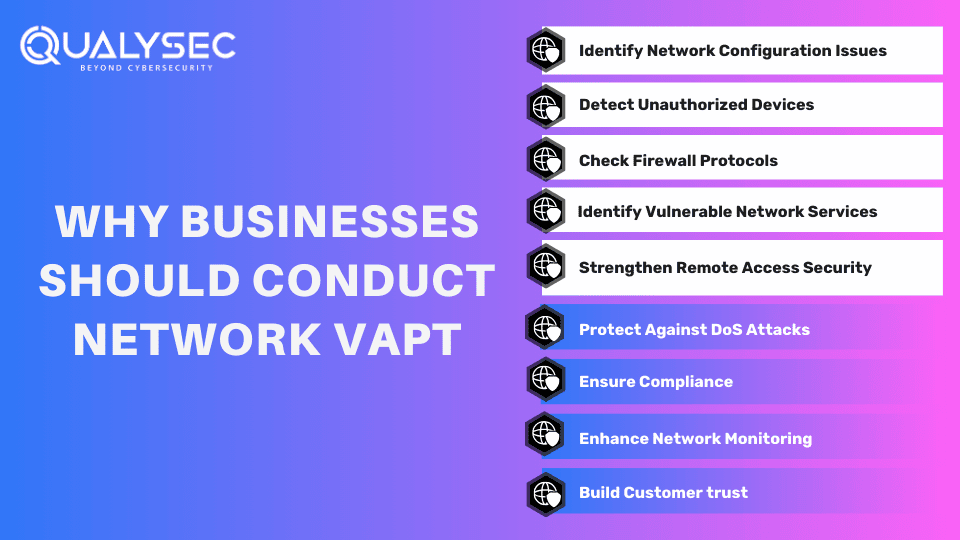
Benefits of Network VAPT in Cyber Security
VAPT Network provides enough details on security issues for developers or security officers to address them before they cause big problems. However, this is not the only benefit. Here are a few reasons why VAPT in cyber security is important for businesses:
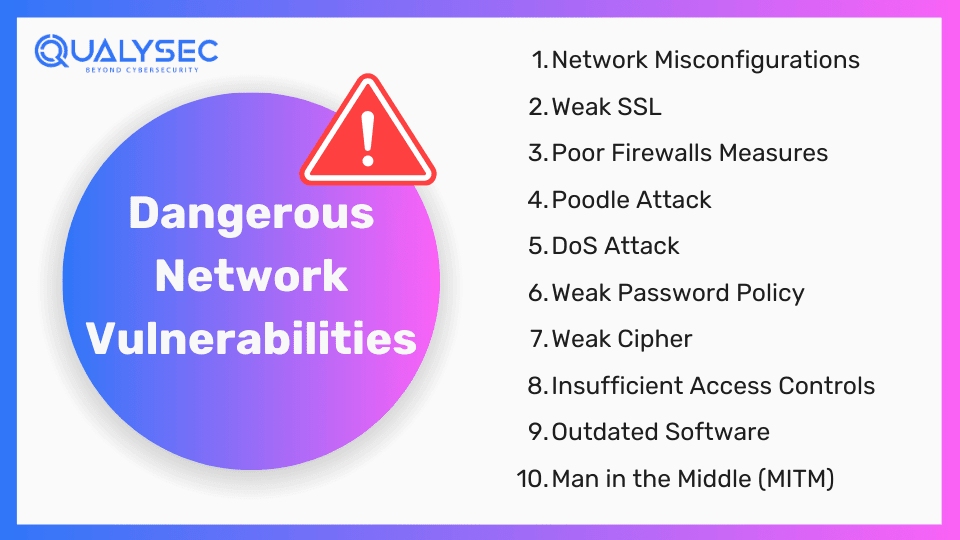
1. Identify Network Configuration Issues
By conducting network VAPT, you can detect misconfigurations in the network architecture that could be exploited by attackers. For example, incorrect firewall measures might allow unauthorized access, or sometimes default network settings might leave it open for attacks. VAPT in networking helps identify such issues and helps strengthen the overall network security posture.
2. Detect Unauthorized Devices
VAPT scans the entire network and identifies any unauthorized devices connected. This prevents malicious devices from accessing sensitive data. For example, attackers might connect an unauthorized device to the network port, which will give them access to the internal systems.
3. Check Firewall Protocols
The job of a firewall is to block unauthorized access and allow legitimate traffic. Network VAPT tests the firewall’s configuration and optimizes its performance and security. VAPT includes simulating various attacks on the firewall to check if it can block them.
4. Identify Vulnerable Network Services
VAPT pinpoints vulnerable services running on network devices. As a result, it helps organizations to update or disable these services to enhance network security. This is because an outdated version of a network service might have known vulnerabilities that attackers can take advantage of.
5. Strengthen Remote Access Security
With the rise of remote working conditions after the pandemic, it is more essential now to test network security. VAPT also tests the security of VPNs and other remote access solutions to secure remote access. It identifies weaknesses in VPN configurations or outdated encryption protocols to ensure remote connections cannot be easily intercepted by attackers.
6. Protection Against DoS Attacks
A Denial of Service (DoS) attack is when the attacker disrupts the business by flooding the network of an organization with traffic. Network VAPT in cyber security helps identify those vulnerabilities that could be exploited for DoS attacks. These vulnerabilities may include inadequate bandwidth or unoptimized network configurations.
7. Ensure Compliance
Many industries make it mandatory for organizations to test the security of the networks that store sensitive user data, such as PCI DSS, HIPAA, ISO 27001, etc. Non-compliance with these rules would result in fines and legal problems. Network VAPT helps companies comply with these regulations by thoroughly testing the network and its components.
8. Enhance Network Monitoring
The VAPT report can be used to improve network monitoring and logging. Better monitoring helps in detecting and responding to security incidents early. By identifying gaps in the current monitoring measures, VAPT recommends implementing more comprehensive monitoring solutions. As a result, this ensures any unusual or suspicious activities are effectively detected and addressed.
9. Build Customer trust
A secure network builds trust among the users/customers. When the users feel confident that their data is safe, it enhances their loyalty. VAPT finds those security flaws that may lead to data breaches. By showing the world you prioritize customer data safety, you are not only securing your business but attracting more customers.
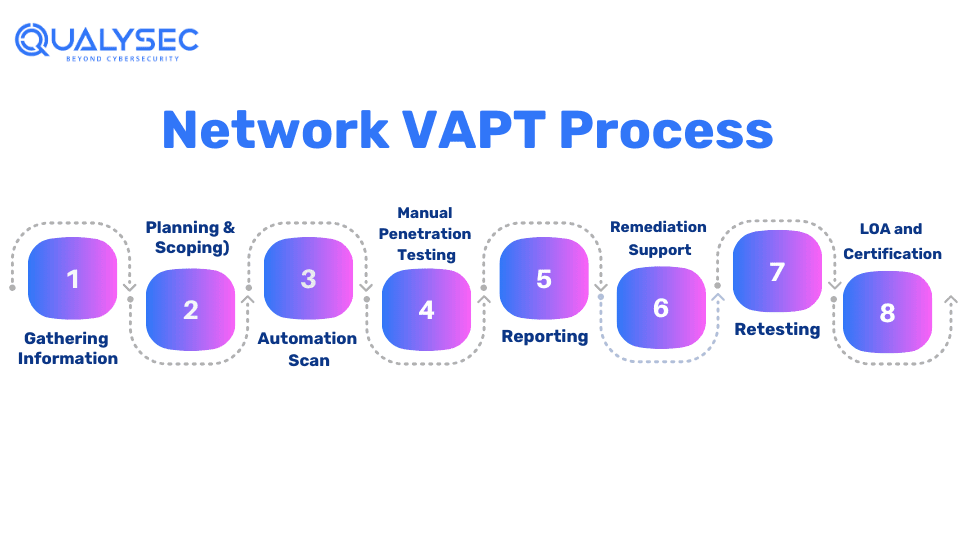
What are the Steps Involved in VAPT Network
VAPT mostly has 3 phases – pre-assessment, assessment, and post-assessment. Here is the brief network VAPT process:
1. Information Gathering
The 1st step involves the testing team collecting relevant information about the target systems, such as domain names, network architecture, IP addresses, and technologies in use. This information helps them understand the potential attack surface and entry points.
2. Planning/Scoping
The next step involves defining the goals and identifying the scope of the test. Here the testing team outlines which tools and techniques will be used and which vulnerabilities they are going to target. This gives a brief idea to the client of what to expect from the test.
3. Automated Vulnerability Scanning
This step includes using automated tools to scan and analyze the target network and systems for known vulnerabilities that attackers could exploit. For example, weak configurations, outdated software, and other common vulnerabilities.
4. Manual Penetration Testing
In the 4th step, expert pen testers or “ethical hackers” perform manual penetration testing. They use manual techniques to detect vulnerabilities missed by the tools and exploit the found vulnerabilities. The goal is to simulate real cyberattacks to understand the resilience of existing security measures and the potential impact of successful exploits.
5. Reporting
After the test is completed, a detailed report is created and shared with the development team that provides a comprehensive overview of the test. It includes the vulnerabilities identified, the potential impact they have, and recommended remediation measures. Additionally, the report includes the technical findings, risk ratings, and actionable solutions to enhance the security posture.
6. Remediation
The development team uses the recommended solutions to fix the vulnerabilities in their network security. if the client needs it, the team usually helps locate the vulnerabilities they found over consultation calls. Both the testing and development teams collaborate to make the network secure.
7. Retesting
After all the necessary fixes and patches are done, the testing team retests the system to check if everything is well and good. Additionally, retesting also ensures there are no vulnerabilities left that could grant unauthorized access to attackers. Then a final report is generated, which contains the entire summary of the VAPT process.
8. LoA/Security Certificate
At last, the testing team provides the client with a letter of attestation (LoA) that is proof that the organization has successfully conducted VAPT for their network systems. This security certificate is then shared with the stakeholders to gain their trust. It is also used to comply with the mandatory industry regulations.
Ever wished to see a real VAPT report? Click the link below and download a network VAPT report that belongs to one of our existing clients (the identity remains hidden for security purposes).
Latest Penetration Testing Report

How to Choose the Best Network Security Testing Company
Different organizations have different network architecture and have different security needs. Despite this, one can still choose the right network security testing company by following these tips:
- Experience and Expertise: Look for a testing company with a proven track record in network VAPT. Check the types of networks they have tested and overall experience in the industry.
- Certifications and Credentials: Check whether the testers have necessary certifications like CISSP, CEH, and OSCP. These certifications indicate they are trained with the necessary skills and adhere to industry standards.
- Detailed Reporting: A good network security testing company should provide detailed reports that outline identified vulnerabilities, their impact level, and remediation recommendations. Clear and actionable reports help the development team take the necessary measures to strengthen network security.
- Client Reviews and References: Check the company’s client reviews and ask them for references. Testimonials and feedback can also give you insights into the company’s working methods and professionalism.
- A Hybrid Testing Method: Make sure the company follows a hybrid testing method that includes using both automated vulnerability scanning tools and manual penetration testing. A combination of both offers a comprehensive security evaluation.
- Retesting Options: Ensure the company retests the network systems after remediation. Retesting confirms whether all the necessary fixes are implemented or not. Continuous support after assessment is also an additional positive factor.
Want to secure your networks from cyber threats? Do VAPT with Qualysec and protect your network components from hackers. We follow a process-based pentesting methodology that allows us to check the target system in-depth. Till now we have completed over 450 assessments for over 100 clients. Talk with our cybersecurity expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Everything that is in the digital space is connected to a network. If the network gets hacked, everything else is also compromised. With network VAPT, organizations can check the strength of their current security measures and also detect security flaws that can become possible entry points for attackers. Regular vulnerability assessment and penetration testing (VAPT) services can help organizations stay miles ahead of hackers and emerging cyber threats.
FAQs
Q: What is a vulnerability scan on a network?
A: A vulnerability scan on a network involves using automated tools to scan the network and its components for known vulnerabilities like misconfigurations and improper firewall measures.
Q: What is a vulnerability in networking?
A: A vulnerability in networking is a weakness or flaw in the software or organizational process. When compromised by a threat or exploited by a hacker, it can lead to a security breach.
Q: What is network security testing?
A: Network security testing is a cybersecurity exercise that helps organizations detect vulnerabilities present in their network infrastructure. Vulnerability scanning and penetration testing are a major part of security testing.
Q: What is a network security assessment?
A: A network security assessment is a form of audit, designed to find vulnerabilities that attackers can exploit. Additionally, these vulnerabilities can expose sensitive information and disrupt business operations.






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments