Cybersecurity risk assessment helps businesses avoid costly security incidents and compliance issues. It is a systematic process that identifies vulnerabilities in an IT environment, checks the likelihood of them happening, and determines their potential impact. Risk assessments also recommend measures to enhance the organization’s security posture and mitigate the risk of breaches.
According to Forbes, 2023 saw a significant increase in cyberattacks, with more than 343 million victims. Since the nature of cyber threats evolves regularly, they have become more sophisticated and frequent. In fact, according to sources, there is a cybercrime every 37 seconds on average.
This blog aims to help organizations of all levels by educating them about cybersecurity risk assessments. We will discuss the steps involved in the process and the tools and techniques used by cybersecurity experts to comprehensively analyze the IT infrastructure.
What is Cybersecurity Risk Assessment?
A cybersecurity risk assessment is a process of checking the current security measures of an organization and whether they are strong enough to resist a cyberattack. The main purpose of a cybersecurity risk assessment is to uncover security flaws in IT systems and make suggestions for their improvement.
Almost every organization uses the Internet and has some form of IT infrastructure, which means they all are vulnerable to cyberattacks. To know what type of security risk an organization can face, they conduct a cybersecurity risk assessment. By mitigating the risks involved, organizations can prevent costly breaches, comply with industry standards, and build trust with customers and stakeholders.
There are various cyber security assessment frameworks available internationally, but they all share the same goal. For example, The National Institute of Standards and Technology (NIST) Cybersecurity Framework and ISO 27001 are the two most popular frameworks that outline what needs to be done to have robust cybersecurity.
Benefits of Conducting a Cybersecurity Risk Assessment
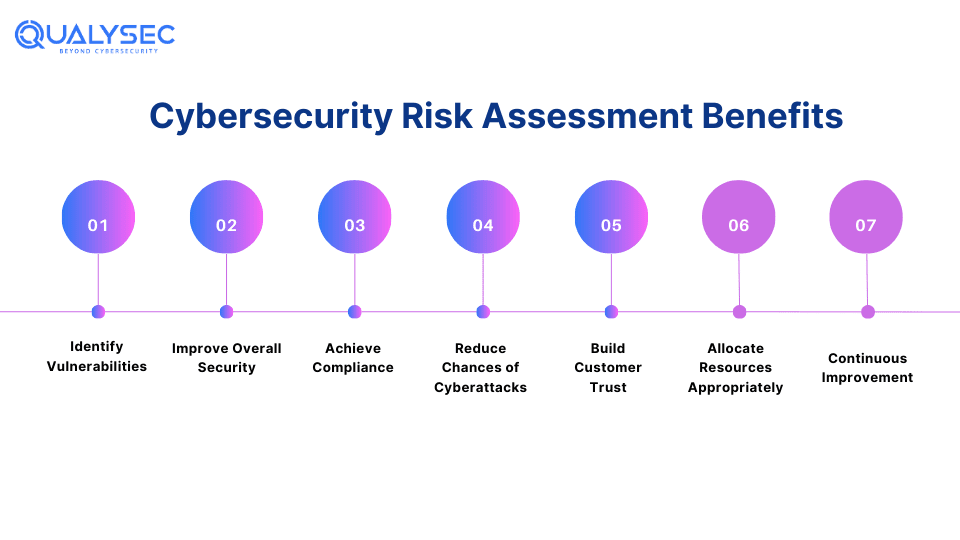
A cybersecurity risk assessment helps an organization improve its cybersecurity program by identifying and fixing security vulnerabilities. It has a wide range of benefits, such as:
1. Identify Vulnerabilities
A risk assessment helps you uncover potential security weaknesses in your applications and networks, such as outdated software, weak passwords, and configuration issues. By identifying these vulnerabilities early, you can mitigate them before they are exploited by attackers.
2. Improve Overall Security
By understanding your security gaps in detail, you can implement the necessary measures to protect sensitive data and IT infrastructure. This might include enhancing your firewall settings, enforcing stronger access controls, and implementing multi-factor authentication (MFA).
3. Achieve Compliance
Many industries have strict regulations and standards for data protection. By conducting a cybersecurity risk assessment, you can ensure your organization meets these legal requirements and avoid fines and penalties. Popular compliance standards include ISO 27001, SOC 2, HIPAA, GDPR, etc. It also increases your organization’s credibility.
4. Reduce Chances of Cyberattacks
By detecting and mitigating security risks, you can minimize the chances of data breaches and cyberattacks. Additionally, this will protect your organization from financial losses, bad reputation, customer loss, and business disruptions.
5. Build Customer Trust
By conducting a vulnerability assessment in cyber security, you can show that you take data protection and asset protection seriously. As a result, it will build trust among your customers and stakeholders, knowing that their data is safe with you. This will even attract more customers and give you a competitive advantage.
6. Allocate Resources Appropriately
A comprehensive risk assessment will let you know the most critical vulnerabilities and threats to your organization. As a result, you can make informed decisions in allocating your cybersecurity budget and manpower to the right place.
7. Continuous Improvement
Cyber threats are always evolving, with attackers trying new ways to penetrate your systems. Cybersecurity is not a one-time thing, it’s an ongoing process. Regular information security risk assessment help you adapt to changes in your IT environment and continuously improve your security posture.
What are the Steps Involved in a Cybersecurity Risk Assessment?
The first thing you need to do is choose the right cybersecurity risk assessment company. the right company will follow all the industry-approved standards and methodologies for a thorough risk assessment.
There are several steps involved in a cyber threat assessment, such as:
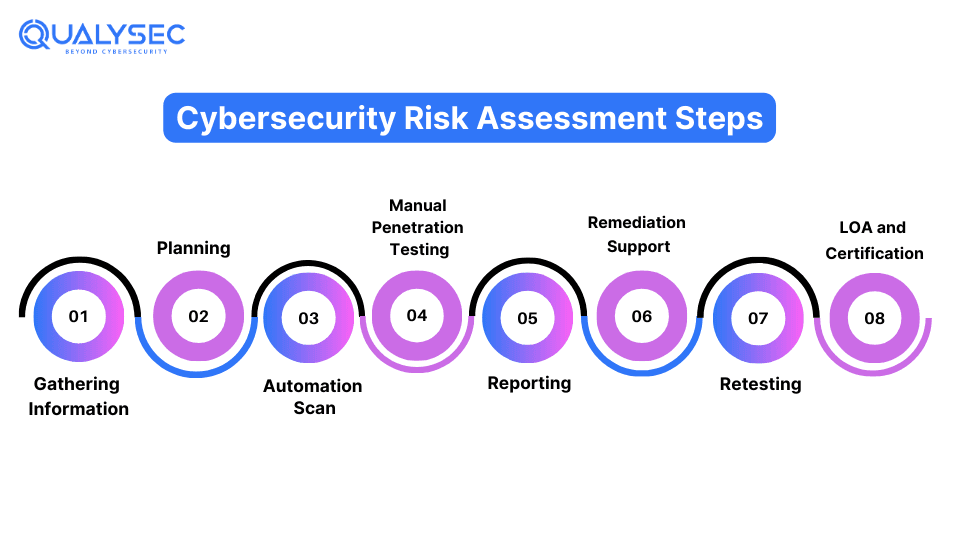
- Define Scope: The first of a security risk assessment is to determine which areas or digital assets you should test that are critical to your business. This may include applications, external networks, cloud, etc.
- Information Gathering: Then the assessment team will gather as much information as possible about the applications that are to be tested. This will help them tap into a variety of methodologies.
- Automated Scanning: The assessment may involve scanning the application for common vulnerabilities using automated tools. This is a quick process to detect known vulnerabilities.
- Manual Penetration Testing: Then they will conduct penetration tests on the target environment to identify complex vulnerabilities and verify those found from the automated tools.
- Reporting: The testing team will document the results of the tests and share them with your development team for remediation. This may include the total vulnerabilities identified, their impact, and suggested fixes.
- Remediation: The development team will use the report to implement necessary security controls. If they need it, the testing team will help them locate the vulnerabilities and fix them.
- Retesting: The testing team will retest the given environment to determine vulnerabilities that were fixed and those that were not fixed.
- Letter of Attestation: This is the final document of risk assessment. It includes the summary of the assessment, and the total vulnerabilities identified and mitigated. This document will help you with various business and compliance needs.
Ever seen a cybersecurity risk assessment report? If not, then download one by clicking the link below!
Latest Penetration Testing Report

Tools and Techniques for Cybersecurity Risk Assessment
A cybersecurity risk assessment is basically testing your IT environment for vulnerabilities, measuring existing security risks, and their real-world impact, and suggesting remediation measures. Several tools and technologies can help accomplish this. However, the most used ones are:
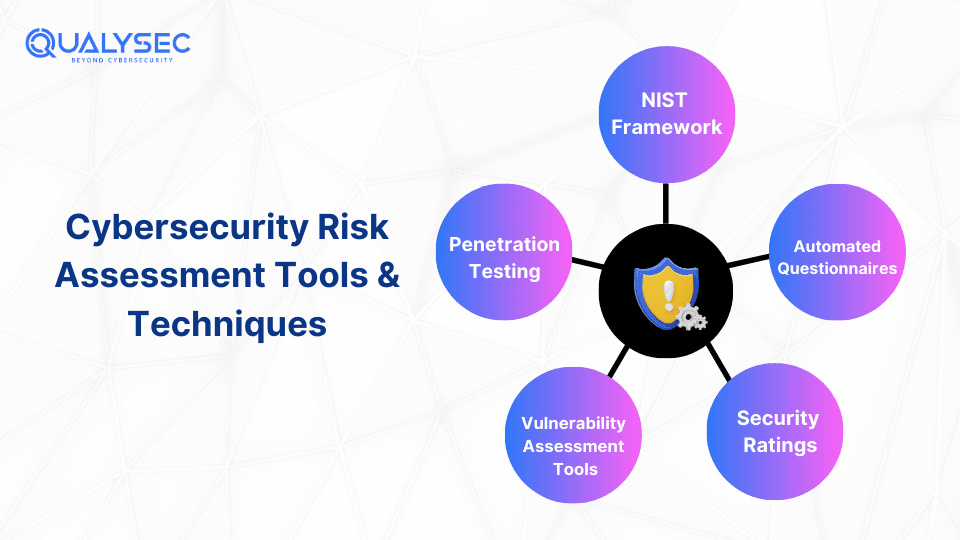
1. NIST Framework
The National Institute of Standards and Technology (NIST) framework provides a set of guidelines for organizations to manage and reduce cybersecurity risks in a better way. By creating a common language for managing cyber risks, the NIST framework provides comprehensive management strategies that are understood by all departments.
The NIST framework is divided into 5 functions, each related to a specific area of risk assessment and management in cyber security:
- Identify
- Protect
- Detect
- Respond
- Recover
2. Automated Questionnaires
Questionnaires are used to evaluate third-party security risks. Since creating and sending questionnaires takes a lot of time and resources, using an automated platform is the best way to validate the responses. It helps you create vendor-specific questionnaires that can be sent at scale and tracked.
3. Security Ratings
These provide a data-driven and objective view of a company’s cybersecurity posture. While initially security ratings were used to assess third-party risk, many organizations now have adopted them to monitor their internal security measures. They also provide valuable insights into various security aspects, such as security testing, attack surface management, and threat identification.
4. Vulnerability Assessment Tools
These tools follow a definitive script and help in identifying common vulnerabilities within your IT infrastructure. By using the report generated from vulnerability assessment tools, organizations can better understand each security risk, helping them establish a robust security posture. Popular vulnerability scanners include Nessus, OpenVAS, Intruder, Netsparker, etc.
5. Penetration Testing
Penetration tests involve simulating real-world attacks on a given IT environment to detect vulnerabilities. It also evaluates the asset’s current security status and helps the organization comply with regulatory standards like PCI DSS, SOC 2, ISO 27001, HIPAA, etc. It is an offensive strategy where the testers act like hackers who expose real security risks and offer remediation measures. There are various types of penetration tests you can choose from, such as:
- Web app penetration testing
- Mobile app penetration testing
- Network penetration testing
- API penetration testing
- Cloud penetration testing
Want to conduct a penetration test? Tap the link button below and talk to our expert cybersecurity consultant right now! We have completed over 450 assessments for over 110 clients, and we can do it for you effectively. Don’t wait, call now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Challenges in Information Security Risk Assessment
There are several misconceptions about cybersecurity risk assessments. For example, many think a security audit is the same as risk management or that it is required only for compliance. However, this is not the case and there are various challenges that cyber security assessment providers face, such as:
- Identifying all Assets: It can be difficult to know which digital asset to evaluate for security risks, for example, applications, networks, data, etc.
- Evolving Threats: Cyber threats are always evolving, making it a huge challenge to keep up with the latest vulnerabilities. What is secure today might be insecure tomorrow.
- Complex IT Systems: Modern IT environments are often complex and usually interconnected. This makes it hard to assess all potential vulnerabilities and their real-world impact.
- Lack of Resources: Conducting a comprehensive cybersecurity risk assessment requires time, expertise, and finance. Certain organizations may not be willing to or just lack the budget to complete the assessments.
- Handling Sensitive Data: During a risk assessment, it can be risky to handle huge amounts of sensitive information. It can be challenging to maintain the security and confidentiality of each data.
- Compliance Issues: Different industries and regions have different compliance standards. Keeping up with all the requirements can be tough, especially if they need a different approach.
- Prioritizing Risks: Once you have identified the risks, it can be challenging to decide which ones to address first. Organizations should allocate their resources as per the severity of the risks.
Conclusion
A cybersecurity risk assessment is an ongoing process, so organizations need to allocate the appropriate amount of time and resources to take full advantage. You should not conduct a risk assessment only on a fixed date but also when you face a cyberattack or if your IT infrastructure has undergone a huge change.
The first time can be challenging but once your initial vulnerabilities are fixed, a risk assessment will then provide a template for future assessments. To get the best out of it, it is important to hire a good cybersecurity risk assessment provider who will be with you till the end.
FAQs
Q: What is the main goal of a cybersecurity risk assessment?
A: The main goal of a cyber security assessment is to check whether the organization has appropriate security measures to prevent cyberattacks and meet compliance.
Q: How often should a cybersecurity risk assessment be conducted?
A: Ideally, a risk assessment in cyber security should be conducted once a year. However, one should also conduct during the event of a cyberattack or if there have been significant changes in the IT infrastructure.
Q: How to measure cyber security risk?
A: A cybersecurity risk is measured by its severity and its real-world impact if exploited. At a high level, it can be calculated like: Cybersecurity Risk = Severity X Impact.
Q: How do you prioritize risks identified in a cyber security assessment?
A: An identified risk is prioritized based on the likelihood of its exploitation (more likely = critical risk) and its real-world impact. Sometimes the NIST framework is also used to prioritize cybersecurity risks.
Q: What are the key differences between qualitative and quantitative risk assessments?
A: key differences between qualitative and quantitative risk assessments include:
- Quantitative assessments use numerical data while qualitative assessments use words and detailed descriptions.
- Quantitative assessments are objective while qualitative assessments are subjective
































































































































































































































































































































































































































































































































0 Comments