In an age of digital transformation, web app security is a necessity for all businesses. As cyberattacks and data breaches escalate, securing web applications has now become a necessity. Web applications in 2025 are no longer merely a convenience to communicate with the user base but also a high-priority target for attackers wishing to breach weaknesses. Collaborating with a cybersecurity firm like Qualysec that offers Application Security Services and specializes in protection from the beginning is key to protecting sensitive information and keeping your applications steady.
This blog delves into the threats, high-quality practices, and progressive answers that guarantee the integrity and protection of your web packages.
The Increasing Importance Of Web App Security In 2025
Web applications form a critical component of most enterprises today, be it an e-commerce site, a financial services company, or a content delivery network. As the dependence on web applications increases, so do the dangers inherent in them. The nature of cybercrime has evolved to include more sophisticated threats, and the attack surface of web applications has increased with advances in APIs, microservices, and distributed systems.
The year is 2025, and data breaches keep piling up the bill, pressing big companies in a major way to lock their web apps adequately. Many organizations now use Application Security Services to proactively identify and fix vulnerabilities before attackers can exploit them. As per IBM’s 2024 Cost of a Data Breach Report, the cost of a facts breach now stands at $four.88 million, as compared to $4.35 million in 2023.
Additionally, Gartner’s API Security Report mentioned that API vulnerabilities had been chargeable for 33% of internet app breaches in 2024 and are in all likelihood to boom with the growing use of API-pushed architectures.
“Explore: Top Application Security Testing Services.
The Fundamentals of Web App Security
Web app security is the security practices and measures that protect web applications from cyber attacks. These range from valid user authentication and input validation to encryption and threat detection in real time. Here, we discuss the key pillars of protecting web apps.
Authentication And Authorization: Ensuring Secure Access
Authentication verifies the identity of a user, whereas authorization regulates what that user can do within the app. Poorly implemented authentication and authorization mechanisms are some of the most common web application vulnerabilities.
Google has been at the forefront of using multi-factor authentication (MFA) for its entire platform. After it introduced MFA on all of Gmail as well as other Google applications, the company saw a 99.9% reduction in successful phishing attacks. This demonstrates the importance of robust authentication to secure web applications against unauthorized access. John Wu, Cloudflare Head of Cybersecurity, observes: “Most breaches are caused by weak or compromised passwords. Using MFA, along with session management controls such as timeouts and IP whitelisting, significantly limits the attack surface.
Data Encryption: Securing Data In Transit And At Rest
Encryption offers a guarantee that exclusive statistics, be it even as traveling among the server and client or inside the database, remains personal and stable. In 2025, organizations must use encryption, especially in industries handling financial transactions, personal health data, or intellectual property.
In 2025, one of the leading e-trade websites experienced an extreme statistics breach due to unsecured session management. Hackers took advantage of sessions that had not been nicely expired, and as a result, they gained access to the bills of customers months after the initial consultation expired. The breach resulted in the business enterprise dropping tens of millions in penalties and a widespread quantity of consumer belief.
Session Management: Securing User Sessions
Web applications establish sessions whenever users engage with them, storing sensitive information like login credentials and user data. Session hijacking takes place when intruders hijack an existing session, usually by exploiting cookie management vulnerabilities.
The Consequences of Poor Session Management
In 2025, one of the leading e-commerce websites experienced a serious data breach because of unsecured session management. Hackers took advantage of sessions that were not properly expired, and as a result, they gained access to the accounts of customers months after the initial session expired. The breach resulted in the company losing millions in penalties and an enormous amount of consumer trust.
Session Management Best Practices:
- Use secure cookies (HTTPOnly and Secure flags).
- Implement session timeouts for inactive users.
- Regularly refresh and rotate session tokens.
Also, explore how web application penetration testing helps secure your apps.
API Security: Securing The Backbone Of Modern Web Apps
As web applications more and more depend on APIs to share information and functionality with other systems, API security has emerged as a central topic. Insecure APIs are a main attack vector for most cybercriminals.
In 2025, T-Mobile experienced a massive data breach when attackers used exposed API endpoints to access customers’ account information, including addresses and phone numbers. The breach involved more than 40 million users and further underscored the imperative of having strict API security protocols.
Expert Advice: David Kennedy, founder of TrustedSec and former Chief Security Officer at Diebold, suggests, “API security calls for end-to-end encryption, proper authentication tokens, and a zero-trust model. Security teams must perform regular audits to discover exposed or poorly secured APIs.
Learn more in our detailed guide to What is a Security Audit? Importance, Types, and Methodology.
Common Web App Vulnerabilities: 2025 Overview
These numbers indicate the increasing demand for solid security measures.
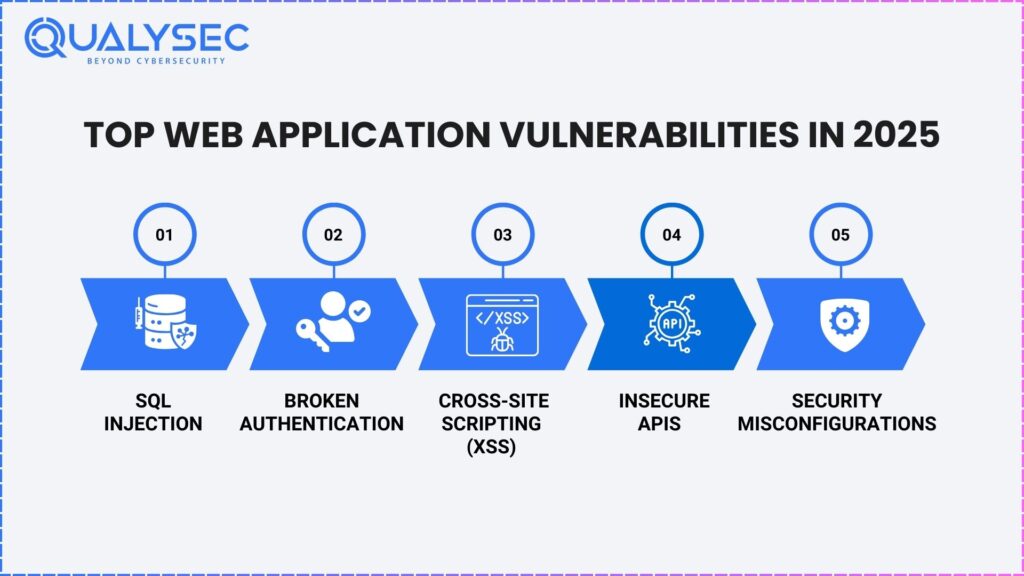
- With SQL Injection impacting 25% of internet applications, the attackers use poorly verified enter fields to control databases, leading to information breaches. Attackers exploit Cross-Site Scripting (XSS) in 18% of web applications to inject malicious scripts into web pages, compromising personal interactions.
- Broken authentication is a widespread chance in 27% of programs, wherein the attackers use susceptible login mechanisms. Lastly, researchers observed insecure APIs in 33% of apps, where improperly secured endpoints gave hackers unauthorized access to backend systems. To address these vulnerabilities, organizations must take proactive measures to secure web applications in 2025.
- Attack vectors in web app security can assume numerous forms, each of which presents serious threats to the integrity and functionality of applications. One of the most popular techniques is injecting malicious SQL code into web forms, which allows attackers to control databases and access sensitive data without authorization.
- Another popular technique is inserting malicious scripts into web pages, which can result in Cross-Site Scripting (XSS) attacks, permitting malicious code to be executed within users’ browsers. Insecure or poorly handled authentication tokens are also a significant threat, as they can be used to hijack user sessions and achieve unauthorized access.
Moreover, unprotected API endpoints are now favored by cybercriminals, as they offer direct access to backend systems and data in case of improper protection. Remediation of these vulnerabilities is necessary to ensure effective web app security.
You might like to read our recent guide on Application Security Audit.
Advanced Security Techniques For 2025
As cybersecurity attackers become smarter, so do their security practices need to get intelligent. Advanced techniques like AI-based threat detection, DevSecOps, and patch automation are fast becoming necessities for any web app security-conscious organization in 2025.
AI-Driven Threat Detection
Machine learning (ML) and synthetic intelligence (AI) are transforming cybersecurity. AI-powered tools are capable of perceiving anomalies in user conduct, site visitor drift, and alertness utilization, which assists in figuring out feasible threats before they turn out to be real attacks.
AI in Threat Detection at Darktrace, a cybersecurity organization that is predicated on AI, employs machine mastering algorithms to become aware of faint patterns in data site visitors. Darktrace’s AI structures have been capable of neutralizing some of the biggest cyber threats in 2024, defending agencies from billions of dollars in potential losses.
DevSecOps: Integrating Security In Development
The old segregation of improvement, operations, and protection is unexpectedly being made a relic of the past. DevSecOps carries security into each step of the improvement life cycle, from coding to deployment and past. Julia Hunter, DevSecOps Specialist at GitHub, states, “Security needs to be baked into improvement, no longer bolted on as an afterthought. DevSecOps permits us to automate safety scanning without making developers less efficient, however so that protection is in no way an afterthought.”
Supply Chain Security: Addressing Third-Party Risks
As companies increasingly depend on third-party libraries and components in their web applications, supply chain attacks have emerged as a significant issue. Malicious code can be injected into third-party software, which is then shared with all users of that software.
The SolarWinds attack of 2020 was one of the most debilitating supply chain attacks ever, yet its effects persist to this day. In 2025, companies are wiser regarding third-party software and perform stringent code audits, and keep an eye on vulnerabilities.
Supply Chain Security Best Practices:
- Implement SCA tools to monitor the usage of third-party libraries and determine vulnerabilities.
- Perform periodic audits of vendor code.
Qualysec’s Role in Application Security Services
At Qualysec, we know that web application security is no longer a matter of simply patching flaws; it’s about building a robust, future-proof security architecture that adapts to new threats. As a visionary cybersecurity firm, we know that the digital landscape today requires an end-to-end, adaptive security strategy that supports business objectives while safeguarding valuable assets through our Application Security Services.
Comprehensive, End-To-End Security Solutions
Qualysec’s web app security testing skills go far beyond ensuring applications are secured. From the outset of a project, our cybersecurity testing teams work together with clients to incorporate security-first concepts into the whole development process—a process called Secure Development Life Cycle (SDLC). This guarantees your web applications are constructed with strong security measures at their foundation instead of addressing security as an afterthought. These practices are a fundamental part of our Application Security Services offering.
Specialization Across Key Industries: Custom Solutions
Qualysec’s difference maker is that it can tailor security solutions to meet the unique requirements of industries with increased security demands, like healthcare, finance, and education. Every industry has its challenges—going from following healthcare regulations such as HIPAA to financial data integrity according to PCI-DSS standards—and our security specialists are skilled at developing solutions that address both business and regulatory requirements.
For instance, in healthcare, where patient confidentiality and data integrity are critical, we provide end-to-end encryption for all communication channels and guarantee that data-at-rest is completely secured. Our finance practice is highly geared towards multi-factor authentication (MFA) and fraud detection mechanisms, essential for sustaining the trust of financial customers and regulatory agencies as well.
DevSecOps Integration: Blending Development And Security
Security is not best the domain of cybersecurity groups—it is infused in every part of the DevOps pipeline at Qualysec through DevSecOps integration. By getting improvement, operations, and safety teams aligned, we automate security practices together with code scanning and vulnerability exams across all degrees of the development lifecycle. This gets rid of human mistakes and accelerates the delivery of stable, scalable net applications, allowing agencies to set up faster without compromising on security.
Compliance And Regulatory Alignment
Compliance is an essential part of web app security, particularly for sectors subject to strict regulation. At Qualysec, we remain at the forefront of regulatory updates across several sectors and make sure that our web app solutions comply with international and local security standards, including GDPR for data protection in the EU, HIPAA in healthcare, and ISO/IEC 27001 for information management security.
By integrating compliance checks into our security audit procedures, we assist companies in evading the financial and legal consequences of non-compliance. Our Application Security Services seamlessly integrate compliance with technical protection.
Proactive Threat Intelligence And Real-Time Monitoring
With increasingly advanced cyberattacks, the capacity to predict and react to threats in real time is essential. Qualysec’s security model extends beyond static defense and adopts proactive threat intelligence. Leveraging AI-driven anomaly detection and real-time monitoring systems, we offer an additional layer of security that assists in detecting and mitigating suspicious behavior before it becomes a breach.
We use automated tools to regularly scan for vulnerabilities, but our process also includes manual review by experienced cybersecurity teams familiar with the subtleties of certain attack vectors. This blended methodology ensures that no possible threat goes unnoticed and your web applications stay secure in an ever-changing threat environment.
Scalable, Future-Proof Security Strategies
In the fast-paced digital environment nowadays, safety has to be scalable so that you can adapt as your business enterprise expands and as technology continues to develop. Qualysec’s technique to net app protection is future-proof so that your app can preserve pace not just with present threats but also be resilient to emerging vulnerabilities. Our scalable answers are designed to let corporations grow their virtual footprint securely through cloud migration, API-first architectures, or microservices.
Our widespread revel in contemporary technologies along with blockchain, AI, and IoT security, permits us to foresee safety issues related to new tech trends. Being proactive on this approach manner that as your organization embraces new improvements, our security fashions adapt to prevent dangers from occurring.
Expert Security Consultation And Support
What differentiates Qualysec is not only the technology we deploy but the professional advice we offer. Our cybersecurity specialists work in close partnership with clients to learn about their individual risk profiles and security aspirations. We provide security consultancy services that permit corporations to study their existing protection measures, spot vulnerabilities, and expand robust plans that increase beyond compliance to supply final safety resilience.
Also, we offer non-stop assistance and renovation to make certain your safety infrastructure is often up to date to save you from new vulnerabilities and meet converting regulatory requirements. This allows you to awareness on increase and innovate your understanding your the net packages that are included via skilled experts.
See how we secure your business—explore our advanced penetration testing services!
Conclusion
Application Security Services are a vital part of current business operations. With net programs turning into greater state-of-the-art, they need to be secured with a multi-pronged method regarding authentication, encryption, input validation, and safety automation.
By staying up-to-date with emerging threats and participating with an application security service provider like Qualysec, organizations can shield their net packages from the evolving change of 2025.
Related Resources:



























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments