White box penetration testing is a testing method to test the security of your applications, network, and other digital infrastructure. Penetration testing is a security testing method that simulates real-world cyberattacks to find vulnerabilities present in the tested environment. White box testing is one of the three types of penetration testing that organizations can choose from.
In this blog, we will discuss white box penetration testing in detail, what are its techniques, and why businesses need it.
What is White Box Penetration Testing
White box penetration testing, also called clear box or transparent box testing, involves giving penetration testers maximum information about the tested environment. It grants them full access to the target, including source code, credentials, access to documentation, and multiple accounts with varying access levels.
A white box penetration test is often used to check a system’s essential parts, especially by companies that develop their software products or use multiple applications. It is a method to check a system’s defenses and see if it can handle different types of cyberattacks.
This specific approach helps detect vulnerabilities in the logic flow of an application, which sometimes automated tools miss.
Why do Businesses Need White Box Penetration Testing?
Successful white box penetration testing helps businesses avoid mistakes that can leave their organization vulnerable to hackers or cyber attackers. Businesses can identify security flaws in their web products and quickly fix them to avoid unauthorized access or data breaches. Penetration testing, in general, is very much essential to create strong security for a business and also to comply with certain mandatory industry standards.
Benefits of White Box Penetration Testing
Here are some crucial advantages of conducting white box penetration testing:
Comprehensive analysis
White box pentesting offers a comprehensive analysis of both internal and external vulnerabilities. In fact, it also analyzes the tested environment from the internal point of view that is usually not available to attackers.
Early Vulnerability Detection
White box pentesting can be integrated into the initial development stages before the software has a user interface, and even before it is available to users. As a result, it detects vulnerabilities at a very early stage.
Wide Coverage
White box penetration testing can detect vulnerabilities in areas that are not accessible with black box testing. For example, the app’s source code, design, and business logic.
Precise Vulnerability Identification
Since pen testers have a detailed knowledge of the system’s internal workings, they can accurately locate specific vulnerabilities. In addition to that, they can also exactly locate potential security gaps and flaws in the code’s logic.
Time-Saving
Especially when compared to black box testing, and even with grey box testing, white box penetration testing is by far the quickest security testing method. This is because the testers are already given all the required information and access to the tested environment.
Do you have an online business that needs security testing? Or do you need to comply with your industry standards? Whatever the reason, Qualysec Technologies can offer you the best penetration testing services to fulfill your needs. Contact now!
Disadvantages of White Box Penetration Testing
Despite having multiple advantages, white box penetration testing has certain drawbacks.
Requires High Programming Knowledge
White box penetration testing involves internal penetration testing. However, to carry out this method, testers need to know critical programming tasks such as port scanning, SQL injections, and executing common attacks. As a result of this, testers will have a better understanding of the access points through which breaches could occur.
Limited Vulnerability Detection
White box pentesting is conducted with complete knowledge of the tested environment, which doesn’t accurately mimic real-world cyberattacks, as hackers have limited to no knowledge of the system. As a result, testers might miss many of the critical vulnerabilities.
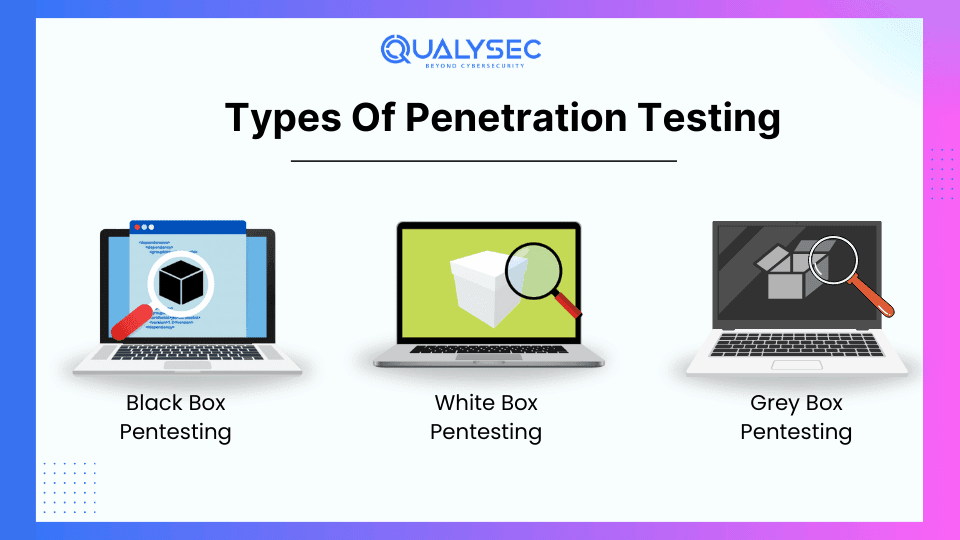
Black Box, Grey Box, and White Box Penetration Testing Differences
Penetration testing is a practice of testing web applications, mobile applications, networks, cloud, APIs, and other digital environments to find vulnerabilities that an attacker could exploit. There are three types of penetration testing: black box, white box, and grey box. The main difference between these types is the level of information provided by the organization to the tester about the tested environment.
All three types of penetration testing use both manual and automated techniques to identify vulnerabilities and security flaws. Let’s dive deep into each type and discover what sets them apart.
Black Box Vs White Box Vs Grey Box Penetration Testing
| Black Box Pentesting | White Box Pentesting | Grey Box Pentesting |
| Knowledge of the internal working structure is not required. Only GUI (Graphical User Interface) is required | Knowledge of the internal working structure (coding structure) is required. | Partial knowledge of the internal working structure (code) is required. |
| Includes trial techniques and error guessing method as no information on internal coding is present. | Includes verifying the system boundaries and data domains inherent in the software as maximum knowledge of internal coding is present. | If internal coding knowledge is present with the tester, it involves validating data domains and internal system boundaries of the software. |
| No programming knowledge is required. | High programming knowledge is required. | Limited programming knowledge is required. |
| Difficult to detect hidden errors as internal working information is absent. | Easy to discover hidden errors as all the information is present. | Difficult to discover hidden errors but might be found in user-level testing. |
| Not considered for algorithm testing. | Suitable and recommended for algorithm testing | Not considered for algorithm testing. |
| The tester, developer, and end-user can be part of this testing. | Only the tester and developer can be a part of this testing. | The tester, developer, and end-user can all be part of this testing. |
| Least time-consuming security testing method. | Most time-consuming security testing method. | Less time-consuming than white box penetration testing. |
| Resilience and security against viral attacks are covered. | Resilience and security against viral attacks are not covered. | Resilience and security against viral attacks are covered. |
White Box Penetration Testing Techniques
In software security testing, the white box technique involves reviewing the source code (the internal structure of the software) to find weaknesses that could expose the software or application to cyber threats. The three main types of white box penetration testing techniques are:
Path Coverage
The white box pentesting technique examines all possible execution paths within the software or application. Each path represents a set of instructions that are followed during execution. Path coverage ensures that every possible path is tested for vulnerabilities at least once, making it particularly effective for sweaters with complex structures.
Statement Coverage
Statement coverage focuses on checking each functionality at least once. A statement refers to a specific function or set of actions that the application performs based on its programming language. An executable statement is when the statement is combined and transformed into an object code, which will execute the action it was designed for. As a result, it helps to identify unused or missing statements, as well as any leftover dead code.
Branch Coverage
A branch represents a different execution path that the ode can take after processing decision statements, like “if” statements. The branch coverage method in white box penetration testing ensures testing of all possible branch codes. This technique evaluates whether tests exercise all branches in the codebase and ensure that no branch leads to any unusual behavior in the application. It maps the code into branches of conditional logic and verifies that unit tests cover all branches, ensuring that every line of code executes at least once.
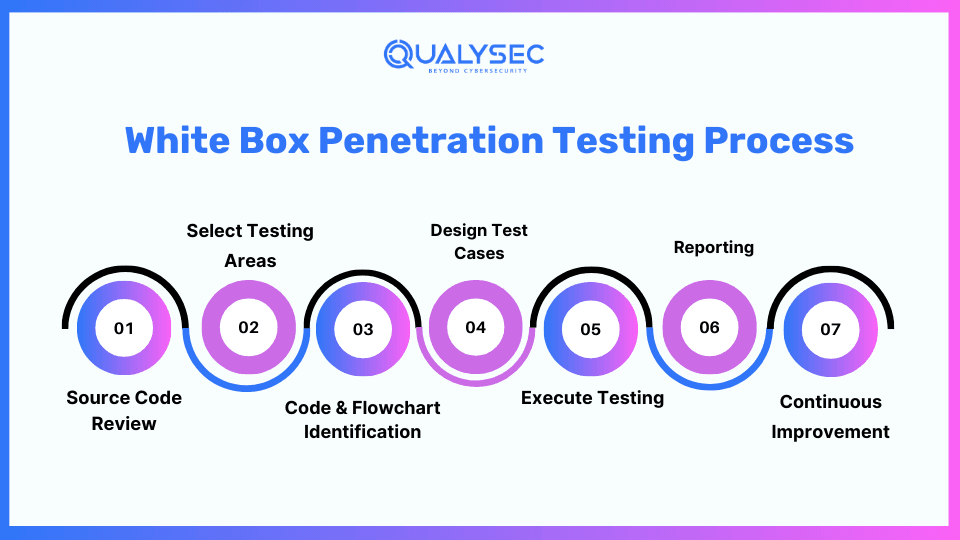
White Box Penetration Testing Process
Source Code Review
- Understand the software’s internal structure and functionality by thoroughly reviewing its source code.
- Design test cases based on this understanding to identify security weaknesses effectively.
Select Testing Areas
- Determine specific areas for testing after understanding the software’s structure and functionality.
- Focus on smaller areas systematically for comprehensive coverage, rather than attempting to cover larger areas which may be impractical.
Code & Flowchart Identification
- Map code execution visually through flowcharts to organize and analyze the system’s functionalities.
- Identify potential code segments, create flowcharts, and trace outputs to understand system behavior and potential vulnerabilities.
Design Test Cases
- White box penetration testing involves creating detailed scenarios for each identified code segment and system functionality.
- Each test case outlines potential security flaws, weak points, and specific testing procedures.
- Include boundary testing and attack simulations to systematically evaluate security and record outcomes.
Execute Testing
- Implement testing plans rigorously, performing through processes to examine all identified systems thoroughly.
- Conduct comprehensive testing, document findings, validate vulnerabilities, and refine procedures for robust security.
Reporting
- Compile a detailed report listing identified vulnerabilities, their impact, and mitigation recommendations.
- Prioritize vulnerabilities based on their severity to guide mitigation efforts effectively.
Continuous Improvement
- Maintain a robust security posture through ongoing monitoring, regular assessments, and improvements in policies and practices.
Want to see what an actual white box penetration testing report looks like? Click below to check one!
Common White Box Penetration Testing Tools
While there are multiple tools to automate certain tasks of white box penetration testing and carry out various processes, here are some common and effective ones:
- Burp Suite
- Nmap
- Metasploit
- MobSF
- PyTest
- Postman
- Pacu
- firm walker
- Nessus
- OpenVAS
- SQLmap
- ZAP
Conclusion
White box penetration testing is a great method to check for vulnerabilities in a software or application during the development stage. It employs the same techniques as black box penetration testing but this time, the testers have all the knowledge of the internal coding structure. It helps businesses by preventing mistakes that could potentially expose your company to cyber threats.
White box pentesting offers a comprehensive analysis, detects vulnerabilities early, and identifies security gaps precisely in any digital environment. However, due to certain drawbacks, it may not detect all the vulnerabilities that could lead to real-world cyberattacks. Despite this, white box penetration testing remains an essential testing method to ensure the tight security of digital assets.
FAQs
Q: What is the main objective of a white box penetration test?
A: White box penetration testing aims to identify vulnerabilities in a software or application that could lead to potential cyber threats. Along with that, this security testing method is also particularly effective in examining the quality of the code.
Q: What is white box vs black box pentesting?
A: In the white box pentesting, the testers have all the information regarding the tested product, including the internal coding structure. While, in black box pretesting, the testers have absolutely no knowledge about the tested environment. Grey box pentesting however, is carried out with testers having limited knowledge about the tested environment.
Q: Who performs white box testing?
A: Usually, testers and developers perform white box penetration testing.
Q: Is white box penetration testing better?
A: There are a few benefits of white box penetration testing over the other two types of testing. White box testing is better to discover hidden errors in code as all the information is available. It is also suitable for algorithm testing.




























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments