A vulnerability assessment finds, classifies, and prioritizes vulnerabilities in a computer system’s network infrastructure and applications. It means an organization’s weakness to be attacked by cyber threats and risks. Conducting a vulnerability assessment utilizes automated testing tools like network security scanners with results in the vulnerability assessment report.
Organizations under constant cyber attacks can highly benefit from a regular vulnerability assessment. Threat actors continuously seek vulnerabilities to exploit applications, systems, and even the whole network. There are newly discovered vulnerabilities in software and hardware components that exist in the market today, and the same goes for new components introduced by organizations.
This is part of an extensive series of guides about hacking.
What is Vulnerability Assessment?
Thus, vulnerability assessment entails a systematic review of weaknesses in the security of computer systems and networks. It also checks for these vulnerabilities in the system and gives them severity levels when remediation or mitigation is needed.
Specific examples of threats against which a vulnerability assessment can serve are:
- SQL injection, XSS, and other code injection attacks.
- Faulty authentication mechanisms lead to privilege escalation.
- Insecure defaults – the software ships with insecure settings, such as a guessable admin password.
Understanding Vulnerability Assessment
A structured process to find and evaluate possible security vulnerabilities concerning an organization’s IT environment is referred to as a ‘’Vulnerability assessment‘. Such procedures entail identifying hardware, software, networks, and personnel practices that may reveal the particular vulnerabilities criminals may exploit. The idea is, in the long term, to increase the level of resilience against incidents like data breaches, downtime, or other different types of incidents.
Usually, that consists of five stages:
- Planning: Formulating the scope and the focus of the assessment.
- Discovery: Scanning the IT environment to expose vulnerabilities.
- Analysis: Assessing the potential effect and priority of vulnerabilities discovered.
- Reporting: Documenting information about those findings and giving recommendations for their mitigation.
- Remediation: Fixing the vulnerabilities found through the application of patches, updates, or other security remedies.
“Also Explore: What is VAPT Testing?
Types of Vulnerability Assessment
There are several types of vulnerability assessments. These include:
- Host assessment – The assessment of critical servers, which may be vulnerable to attacks if not adequately tested or not generated from a tested machine image.
- Network and wireless evaluation – Examining policies and practices to restrict unauthorized access into private or public networks and other network-accessible resources.
- Database review – Examination of databases or large data systems for vulnerabilities and misconfigurations or identifying rogue databases or an insecure dev/test environment. The process also classifies the sensitive data across the organization’s infrastructure.
- Application scans – The identification of security vulnerabilities in web applications and their source code by automated scans either on the front end or through the static/dynamic analysis of source code.
Vulnerability Assessment Scanning Process
The security scanning process consists of four steps: testing, analysis, assessment, and remediation.
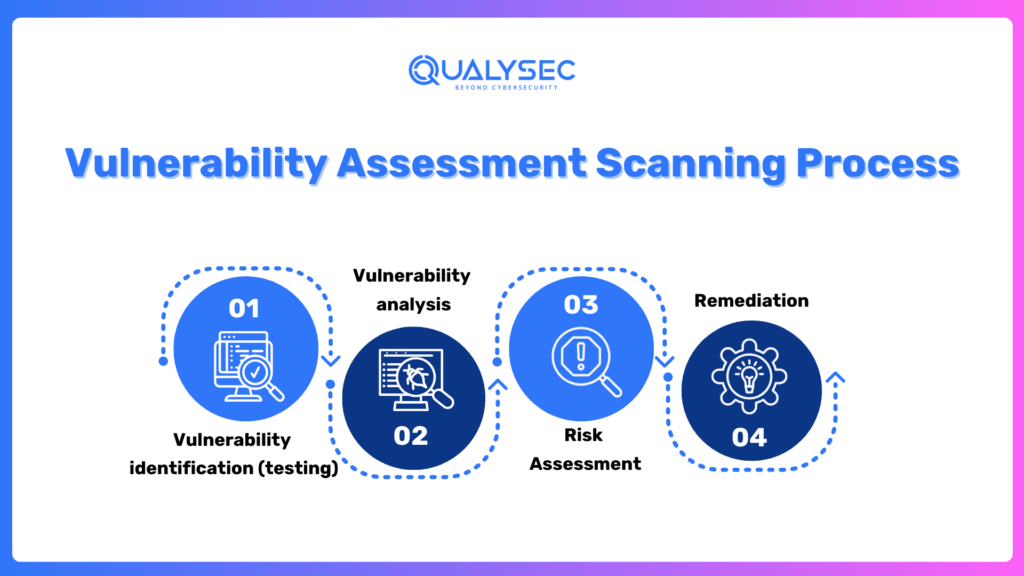
1. Vulnerability identification (testing)
The aim of this step is to prepare a detailed list of vulnerabilities in an application. Security analysts check the security health of applications, servers or other systems by scanning them with automated tools, or testing and evaluating them manually. Analysts also rely on vulnerability databases, vendor vulnerability announcements, asset management systems, and threat intelligence feeds to identify security weaknesses.
2. Vulnerability analysis
It’s supposed to identify where the vulnerabilities arise, how they are derived, and therefore their root causes.
This implies identifying the system component responsible for that particular vulnerability. This includes what caused the weakness in the system: its root cause. For instance, the reason a certain software library is exposed might be the use of an outdated version of an open-source library. Remediation becomes straightforward—one has to update the library to a newer version.
3. Risk Assessment
The outcome of this step is the ranking of vulnerabilities. In this step, security analysts attach a rank or severity score to each vulnerability depending on such considerations as:
- What systems are vulnerable?
- What information is exposed?
- What business operations are vulnerable?
- Easiness to attack or exploit.
- The severity of an attack.
- Potential damage resulting from a vulnerability.
4. Remediation
The goal of this stage is the closing of security gaps. It’s usually a collaborative effort by security personnel, and development and operations teams, who decide on the best course of remediation or mitigation for each vulnerability.
Some specific remediation steps may include:
- Implementation of new security procedures, measures, or tools.
- Operational or configuration updates.
- Development and implementation of a vulnerability patch.
- Vulnerability assessment cannot be a one-off activity. To be effective, organizations must operationalize this process and repeat it at regular intervals. It is also critical to foster cooperation between security, operation, and development teams – a process known as DevSecOps.
“You might like to explore: Vulnerability Assessment Report: A Complete Guide
Latest Penetration Testing Report

Vulnerability Assessment Tools
Vulnerability assessment tools are there to automatically scan for new and existing threats that could target your application. Types of tools include:
- Web application scanners that test for and simulate known attack patterns.
- Protocol scanners that search for vulnerable protocols, ports, and network services.
- Network scanners help visualize networks and discover warning signals like stray IP addresses, spoofed packets, and suspicious packet generation from a single IP address.
It is a best practice to schedule regular automated scans of all critical IT systems. The results of such scans must feed into the organization’s ongoing vulnerability assessment process.
Vulnerability assessment and WAF
Qualysec’s web application firewall helps protect against application vulnerabilities in several ways:
- It acts as a gateway for all incoming traffic and can proactively filter out malicious visitors and requests, such as SQL injections and XSS attacks. This eliminates the risk of data exposure to malicious actors.
- It can accomplish virtual patching — the auto-applying of a patch for a newly found vulnerability at the network edge, providing developers and IT teams the chance to safely roll out a new patch of the application without fear.
- Our WAF provides a view of security events. Attack Analytics helps contextualize attacks and exposes overarching threats, like showing thousands of seemingly unrelated attacks as part of one big attack campaign.
- Our WAF integrates with all leading SIEM platforms to give you a clear view of the threats you are facing and help you prepare for new attacks.
Common Challenges in Vulnerability Assessment
Here are some of the common challenges in vulnerability assessment:
- Resource Constraints: Small and medium-sized businesses often lack the resources to conduct thorough assessments.
- False Positives: Automated tools may generate false positives, requiring additional analysis to determine actual risks.
- Complex IT Environments: Modern IT infrastructures are complex and constantly evolving, making comprehensive assessments challenging.
- Human Error: Misconfigurations or oversights during the assessment process can lead to missed vulnerabilities.
- Evolving Threat Landscape: New vulnerabilities are discovered daily, requiring businesses to stay updated and proactive.
“Related Read: What Is Vulnerability Scanning?
Best Practices for Successful Vulnerability Assessments
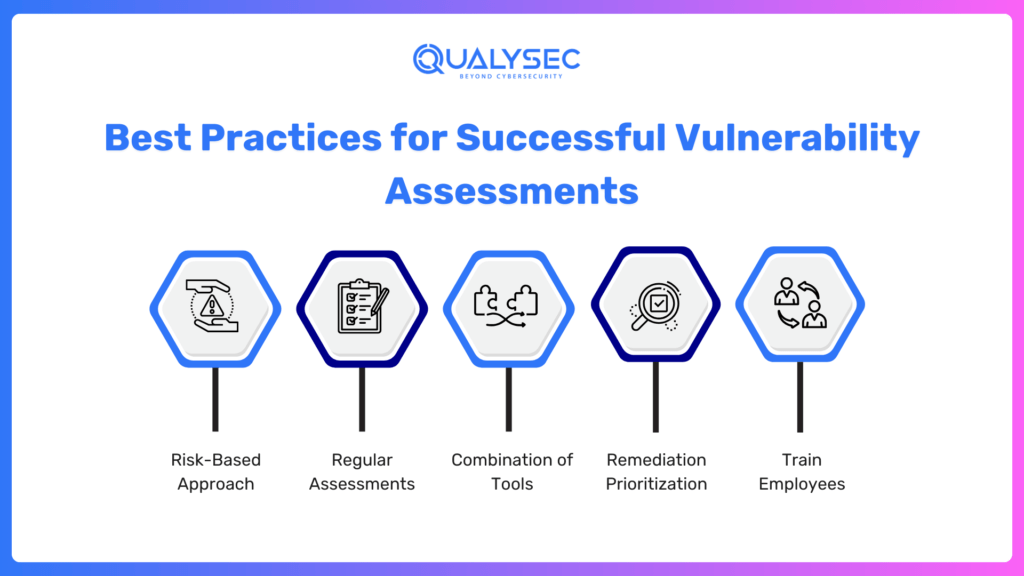
- Risk-Based Approach: Focus on the two or three most damaging vulnerabilities that would hurt your business the most.
- Regular Assessments: You should schedule regular assessments to remain abreast of the fast-changing threats.
- Combination of Tools: It has combined both tools to make sure it covers all areas.
- Key Stakeholders: Get security, IT, and business people involved in the process to get on the same page.
- Remediation Prioritization: We should first focus on the remediation of critical vulnerabilities that can mitigate immediate risks.
- Train Employees: Educate employees to know their contribution to maintaining Cyber Security.
Why Vulnerability Assessment Is Essential for Any Business in 2025?
Let us understand why vulnerability assessment is essential for any business in 2025:
1. Rise in Cyber Threats
Cyberattacks are on the rise, be it ransomware or zero-day exploits, the threat landscape in 2025 calls for a solid defense mechanism. A vulnerability assessment clearly explains what vulnerabilities are available, and which businesses can use to correct things before the attacker hits them.
2. Compliance with Regulatory Standards
Governments and industry associations are enforcing stronger regulations to protect sensitive data. Non-compliance will attract severe fines and damage the reputation. Vulnerability assessment helps businesses to comply with standards such as GDPR, CCPA, ISO 27001, and PCI DSS by filling gaps in the security measures.
3. Protection of Customer Trust
Customer trust and, subsequently, brand reputation can be eroded through a single data breach. The business will assure its customers that their data is safe and secure by addressing vulnerabilities proactively.
4. Cost-Effective Risk Management
It is more expensive to recover from the damage resulting from a cyberattack than it is to make preventive investments. Vulnerability assessments are cost-effective ways to reduce risk and avoid financial losses that may result from breaches.
5. Protecting Intellectual Property
For most organizations, intellectual property is their most valuable asset. Vulnerability assessments help protect proprietary data, trade secrets, and other sensitive information from falling into the wrong hands.
6. Facilitating Business Continuity
Cyberattacks can disrupt operations, leading to downtime and revenue loss. Identifying and mitigating vulnerabilities ensures that critical systems remain operational and minimizes disruptions.
How Qualysec Pentest helps you with Vulnerability Assessment

Qualysec is widely famous for detecting vulnerabilities and risks. They have many services available to people such as the VAPT (Vulnerability Assessment and Penetration Testing), where they find vulnerabilities before hackers.
Although Qualysec’s main office is in India, they are known as one of the best cybersecurity companies in the world, since they have a thorough understanding of the subject and are very successful in it. Experts at Qualysec can detect weak points that cyber attackers may exploit. By finding vulnerabilities, Qualysec comes up with a mitigation strategy in collaboration with the company. This enables the company’s security to become better. They provide various other services which are:
- Web Application Penetration Testing
- Mobile App Penetration Testing
- Cloud Penetration Testing
- APIs Penetration Testing
- IoT Penetration Testing
- Blockchain Penetration Testing
At Qualysec, a team of cybersecurity experts, tackle and investigate security attacks that give the upper hand against their clients in security solutions. They provide VAPT Services through the latest procedures and approaches.
Qualysec implements industry standards and provides step-by-step results so that clients can easily understand and fix problems. Qualysec’s solution is perfectly meant for organizations with strict industry regulations or clients who need to evidence their commitment to privacy and security to vendors and other relevant parties. Through continuous testing, businesses can reveal those weaknesses right away and fix them before hackers exploit them.
Qualysec offers top-of-the-line vulnerability assessment and penetration testing for web applications, mobile apps, cloud, IoT devices, etc. along with source code review and Vulnerability Assessment. Contact Us Now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
In this article, we described the fundamentals of vulnerability assessment, covered the main tools that can be used to discover vulnerabilities, along with community scanning, host scanning, and application scanning, and presented a 5-step process for handling vulnerability assessments to your organization:
- Initial preparation – defining the scope and goals of vulnerability testing.
- Vulnerability testing: running automated tests to identify vulnerabilities in systems included in the scope.
- Prioritize vulnerabilities – identify which vulnerabilities are important and require attention and their possible business impact.
- Create a vulnerability evaluation record – broaden a plan outlining the medium and high precedence vulnerabilities diagnosed and endorsed remediations.
- Continuous vulnerability assessment – scanning for vulnerabilities on a non-stop basis to see if preceding vulnerabilities have been remediated and find out new ones.
Follow Qualysec on Facebook, Twitter, and LinkedIn for more relevant and interesting cyber security updates.
FAQs
1. What is vulnerability assessment?
Vulnerability assessment is the process of systematic identification and analysis of such security weaknesses in an organization’s IT infrastructure.
2. When should vulnerability assessment be conducted?
Such assessments should be performed on a quarterly basis, or following the implementation of major changes in the IT environment.
3. What common tools for vulnerability assessments are used?
The popular tools in Nessus, Qualys, OpenVAS, and Rapid7 Nexpose.
4. What is the difference between penetration testing and vulnerability assessment?
The vulnerability assessment only identifies the vulnerability, and penetration testing gives vulnerability as well as exploits of the vulnerability and its impact.
5. Are vulnerability assessments useful to small businesses?
Vulnerability assessments certainly aid small businesses in adhering to compliance requirements, protecting the business’s information, and ensuring a costly breach is prevented.
6. Is vulnerability assessment a one-time process?
No, it is an ongoing process whereby one should perform it regularly to address new threats and vulnerabilities.
































































































































































































































































































































































































































































































































0 Comments