Today’s technical world is more vulnerable to a variety of cyberattacks. To detect and reduce risks, including system, network, and application breaches, vulnerability testing has become a vulnerable procedure. To preserve cybersecurity, let’s examine the tools, techniques, and best practices provided by vulnerability testing providers.
Vulnerability Testing: What Is It?
Vulnerability testing is the process of determining and addressing security flaws in a computer system, network, or software application. To find potential vulnerabilities, such as code problems, configuration issues, or out-of-date software components, it entails methodically scanning, probing, and analyzing systems and applications. Vulnerability testing in cyber security seeks to find security flaws that hackers could use to gain unauthorized access. Furthermore, the test offers practical advice for resolving the vulnerabilities discovered.
The primary objective of vulnerability testing is to identify and fix these security flaws before attackers can take advantage of them, hence enhancing the system’s overall security and resilience. Cybersecurity vulnerability assessment‘s main aim is to find security flaws such as incorrect setups, inadequate access controls, unsafe network protocols, a lack of authorization and authentication, or known flaws in software components.
The procedure looks for possible weaknesses in the target environment by using a variety of tools and methods. Code reviews, automated scanning tools, and manual penetration testing are a few examples of this.
Vulnerability Testing: Why Is It Important?
Testing for vulnerabilities is crucial for several reasons:
A thorough comprehension of the assault surface: Organizations can gain a deeper understanding of their systems, networks, and applications through vulnerability tests. This all-encompassing perspective aids in locating possible entry points and weak places that an attacker could take advantage of.
Recognizing and responding to changing threats: Due to the frequent emergence of new attack channels and vulnerabilities, cyber dangers are always changing and evolving. Organizations may stay informed about the most recent security dangers and take preventative action against them by using vulnerability testing.
lowering the number of attack points: Organizations can lessen the number of possible attack channels that hackers have access to by detecting and fixing vulnerabilities. This helps protect important systems and data and lowers the chance of a successful cyberattack.
Improved security protocols: Vulnerability testing yields useful data that may be applied to enhance security protocols. This could entail changing policies and procedures, putting in place new security oversight, or training staff members on security standards.
Constant enhancement: Through the constant practice of vulnerability testing, companies can keep an eye out for emerging vulnerabilities in their systems and applications. Organizations may make the required modifications and enhancements thanks to this iterative process, which guarantees that their security posture will continue to be robust as time passes.
Controlling risks: Vulnerability testing aids organizations in better understanding and controlling their security threats. Organizations can make well-informed decisions regarding resource allocation and risk mitigation by assessing vulnerabilities and ranking them according to their potential impact.
“Read our article on Vulnerability Assessment And Penetration Testing
Vulnerability Testing Methods:
Vulnerability testing methods can be widely classified according to the approach used to find vulnerabilities. The following is an outline of network, distributed, active, and passive testing:
1. Testing in Active Mode:
To find potential security flaws, testers use the active testing technique, which involves direct interaction with the target system, network, or application. In order to find vulnerabilities, generally involves delivering inputs, demands, or frames to the target and examining the results.
Although it might be intrusive and result in disruptions or performance problems in the target system, active testing is typically more successful than passive testing at identifying vulnerabilities. Active testing examples include:
- Port scanning to find services and open ports on a network.
- Sending apps unexpected or distorted inputs to find input validation and error handling flaws is known as fuzz testing.
2. Testing in Passive Mode:
A non-intrusive vulnerability testing method called “passive testing” entails watching and examining the target system, network, or application without making direct contact with it. To find potential vulnerabilities, passive testing focuses on obtaining data about the target, such as network traffic, configuration settings, or application behavior.
Compared to active testing, this approach may be less successful in identifying vulnerabilities but is less likely to result in interruptions or performance problems. Passive testing examples include:
- Tracking data to find trends or irregularities that might point to security flaws.
- Conduct installation evaluations to check security settings and identify any misconfigurations.
3. Testing the Network:
To find security flaws in network infrastructure, such as devices, protocols, and configurations, network testing is a vulnerability testing technique. Finding weaknesses that might permit illegal access, eavesdropping, or Denial of Service (DoS) assaults on the network is its goal.
To thoroughly assess the network’s security posture, network testing usually combines active and passive testing methodologies. Network testing examples include:
- Checking network devices for open ports and services.
- Checking for security vulnerabilities in network setups and standards.
4. Testing in Distributed Places:
Using several testing tools or systems, frequently spread over various locations, to scan and examine the target system, network, or application for vulnerabilities is known as distributed testing.
This method can assist in offering a more thorough understanding of the target’s security posture by assisting in the identification of vulnerabilities that would only be apparent from particular angles or in particular situations. Additionally, by distributing the burden of vulnerability testing, distributed testing can lessen the impact on the target system and improve testing efficiency.
Here are some instances of distributed testing:
- Searching for possible security holes in a web application using several vulnerability scanners from various locations.
- Organizing a group of testers in multiple locations to carry out simultaneous network vulnerability testing.
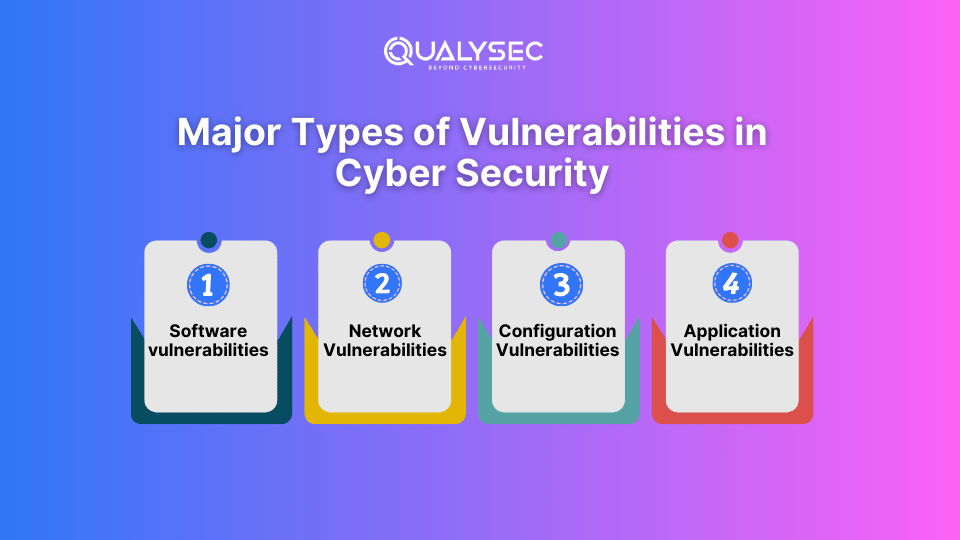
The Four Major Types of Vulnerabilities in Cyber Security
To defend against assaults on apps and data, we must be aware of the many forms of vulnerability tests in cyber security. Frequent vulnerability testing can help avoid these problems and safeguard the company’s digital property.
- Software vulnerabilities: Refer to defects or weaknesses in software systems that attackers can exploit. These could be defects, erroneous code, or out-of-date software that hasn’t been fixed.
- Network vulnerabilities: older protocols, unprotected wireless connections, and unsafe network setups are examples of infrastructure flaws in a network. These flaws can be used by attackers to steal data or initiate DNS assaults.
- Configuration Vulnerabilities: These happen when systems are not set up correctly, increasing the likelihood of an attack. Weak permissions, default settings, and superfluous services are examples of common configuration problems. These flaws could be used by attackers to obtain illegal access or command.
- Application Vulnerabilities: These are potentially exploitable weaknesses in software programs, including web and mobile ones. Numerous application vulnerabilities exist, including buffer overflows, SQL injection, and cross-site scripting (XSS).
Vulnerability Testing Tools: What Are They?
Software programs or services called vulnerability testing tools are made to assist businesses in locating and evaluating security flaws in their networks, apps, or systems. By automating the vulnerability testing process, these solutions improve its accuracy, consistency, and efficiency.
Vulnerability testing tools come in several varieties, such as:
- Network vulnerability scanners: These programs check networks for configuration errors, open ports, and other security flaws.
- Web Application Vulnerability Scanners: These scanners identify vulnerabilities in web applications, including SQL injection, cross-site scripting (XSS), and compromised authentication.
- Static Application Security Testing (SAST) Tools: Designed to analyze source or compiled code to detect security flaws without executing the program.
- Dynamic Application Security Testing (DAST) Tools: Designed to communicate with running apps to find security flaws while they’re running.
- Fuzz testing tools: Create and deliver programs with unexpected or distorted inputs to find input validation and error handling flaws.
- Tools for configuration management and compliance: These evaluate system and application configurations about recognized security best practices or compliance guidelines, such as PCI DSS or CIS benchmarks.
- Cloud security and unit tools: These tools concentrate on finding flaws and incorrect setups in containerized apps and cloud-based settings.
To get a thorough evaluation of their security posture, organizations frequently combine various vulnerability testing techniques. To guarantee that these tools can accurately identify and assess the most recent security threats and vulnerabilities, it is crucial to keep them updated.
How Does Vulnerability Testing Work?
Using automated scanning techniques to identify security flaws in digital assets like apps, networks, cloud, APIs, etc. is known as vulnerability testing in cybersecurity.
After completing a complete analysis of the target system, the automated program provides a comprehensive report. This covers the vulnerabilities identified as well as practical suggestions for resolving and lessening these risks.
Numerous databases containing information on known vulnerabilities (such as misconfigurations and information leaks) are available for these technologies. They can therefore successfully identify possible weaknesses in all areas of the system architecture, including information, network connectivity, apps, and storage.
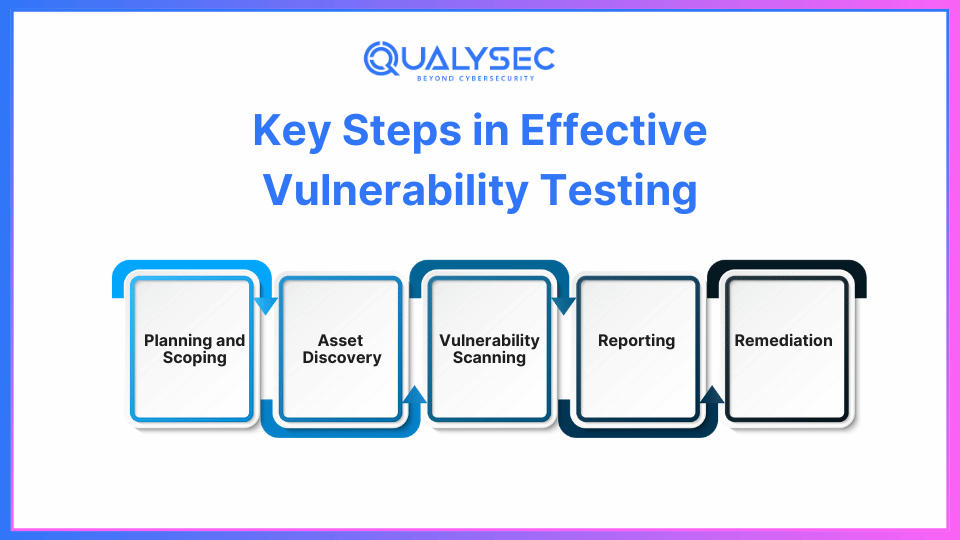
The Vulnerability Testing Procedure
- Planning and Scoping: Clearly defining the test’s objectives is the first stage in vulnerability testing. This covers the test’s goals, which include finding vulnerabilities, determining the degree of risk, and improving security in general.
- Asset Discovery: Selecting which networks or apps to test is the task at hand. Since many firms do not have visibility into their digital assets, this is simpler said than done. Fortunately, automated scanning simplifies this asset-finding process.
- Vulnerability Scanning: To find security flaws in the target environment, automated scanners or programs are utilized. Although automated methods are efficient and fast, they may overlook many vulnerabilities, necessitating manual penetration testing.
- Reporting: Following scanning, the tools produce a report with information on every vulnerability discovered. The tools classify the vulnerabilities using a severity-based ranking methodology, assisting developers in addressing the most serious issues first.
- Treatment: The vulnerability testing result is used by developers to learn about all of the system’s security flaws. After that, they begin the patching or repair process, working their way down from the essential ones. Developers can construct applications that are safe with the aid of routine testing.
Latest Penetration Testing Report

12 Vulnerability Testing Best Practices
Achieving successful outcomes and enhancing an organization’s overall security posture requires adhering to best practices in vulnerability testing. The following are important best practices to think about:
1. Develop a Clear Strategy and Scope:
Specify the systems, apps, and network segments that will be tested and the extent of the vulnerability testing. Develop a thoroughly defined strategy that details the methods, tools, and testing procedures to be employed.
2. Perform Regular Vulnerability Assessments:
Since new threats and vulnerabilities are always emerging, schedule vulnerability assessment and testing testing often. Frequent evaluations will help keep your company abreast of the most recent configuration modifications and security updates.
3. Combine Tools and Techniques:
To obtain a thorough assessment, combine automatic vulnerability scanners with traditional testing methods like penetration testing. While automatic tools can swiftly find known vulnerabilities, manual methods could help find more complicated problems that automated scanners could have overlooked.
4. Prioritize Vulnerabilities:
Assess and rank vulnerabilities according to their seriousness, possible consequences, and ease of exploitation. Prioritize fixing high-priority vulnerabilities to reduce the likelihood of an attack.
5. Implement Effective Patch Management:
To mitigate vulnerabilities found, implement a strong patch management procedure that guarantees prompt application of security fixes and updates. This procedure ought to involve keeping an eye out for fresh patches, evaluating their compatibility, and distributing them around the company.
6. Remediation and Validation:
Address vulnerabilities that have been found and confirm that the remedies have been successful in resolving the problems. Retesting apps or systems may be necessary to make sure that no new vulnerabilities have been created.
7. Foster Cross-Department Collaboration:
To guarantee efficient coordination, communication, and corrective efforts, promote cooperation between IT, security, and other pertinent departments.
8. Employee Training and Awareness:
Increase staff members’ understanding of security issues by implementing frequent training and education initiatives. This lessens the possibility that human error may result in security events and fosters a security-conscious culture within the company.
9. Monitor and Adapt:
Keep an eye on the threat environment at all times, and modify your vulnerability assessment procedures as necessary. Keep up with the latest security testing best practices, new vulnerabilities, and emerging threats.
10. Document and Review:
Keep thorough records of all vulnerability assessment procedures, findings, and corrective actions. Review and update these documents frequently to make sure they continue to be applicable and useful in meeting the security requirements of the company.
11. Assess Third-Party Software and Application:
Testing for security flaws in third-party programs and applications is one of the best practices for software security testing. This implies that before being incorporated into the system, any external code or libraries that your application uses should undergo extensive testing.
It’s critical to make sure that any potential weaknesses are found and fixed as soon as possible to prevent problems later.
12. Implement Proper Session Management:
Using appropriate session management is one of the procedures for software security testing. This entails ensuring that user sessions are appropriately logged and maintained during the application’s use. To prevent bad actors from compromising any authentication credentials, it is also necessary to make sure that they have been secured and maintained securely.
How to Select the Best Vulnerability Testing Company?
Selecting the appropriate vulnerability testing company is therefore essential because legal compliances such as GDPR, PCI DSS, HIPAA, and ISO 27001 require security testing for applications that handle user data. The following are some things to think about:
- Seek out businesses with a track record of success and a specific understanding of vulnerability testing.
- A wide range of vulnerability assessment services, including network, application, and mobile security, should be provided.
- Accreditations and Guidelines: Check to see if they adhere to industry standards and possess the necessary certifications, such as CREST, OSCP, etc.
- Customer Ratings and Reviews: Look for gratifying comments and case studies from prior customers.
- Assess the quality and range of tools used to test vulnerabilities.
- Make sure they can modify their testing methodology to meet your unique requirements and setting.
- Finding thorough studies with specific suggestions for addressing risks is important.
- Evaluate communication and support during testing.
- Examine pricing models to make sure you are getting a decent deal on the services being provided.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
An essential component of locating and addressing security flaws in networks, apps, and other digital systems is vulnerability testing. Regular vulnerability testing has become increasingly crucial for enterprises as the threat landscape changes constantly due to complex attack techniques and cutting-edge tools.
When choosing a vulnerability testing firm, be careful to look at its wide range of services, reviews, and tools. When selecting a security testing firm, bear in mind that a thorough security analysis can be obtained by combining vulnerability scans with manual penetration testing.
FAQs
Who does vulnerability assessments?
A vulnerability test can be carried out by anyone who understands how to use automated vulnerability scanners. To perform a thorough analysis or manual penetration testing, however, one needs the appropriate qualifications. These people are also known as ethical hackers or pen testers.
What is the tool used for vulnerability testing?
A vulnerability test can be conducted using a variety of tools, including Burp Suite, Nessus, OWASP ZAP, MobSF, and Nmap.
What do you mean by cybersecurity vulnerability?
A vulnerability in cybersecurity is a defect or weakness in a system, network, or application that a hacker could use to gain unauthorized access or compromise data. Numerous things, such as defects, incorrect configurations, out-of-date systems, inadequate security measures, weak passwords, etc., might cause these vulnerabilities.



























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments