With more sophisticated cyber crimes than ever before, organizations have to become a truly proactive defensive platform for cybersecurity. Vulnerability Assessment and Penetration Testing (VAPT) is one of the most effective methods to secure one’s digital assets. So, this process identifies the loopholes in terms of security and gives us an insight into what to do about them to reduce the risks further. With cybercriminals constantly changing their strategy in attacks, the VAPT assessment implemented in business in 2025 helped businesses to be ahead of any potential threat. Today, Qualysec Technologies is going to explain what VAPT is, how it is important, what are methodologies, tools, and best practices, and how Qualysec Technologies can enhance the security of your organization.
What is a VAPT Assessment?
VAPT assessment is the name of the cybersecurity evaluation process for organizations to find and eliminate weaknesses related to security in their IT environment. Organizations need VAPT to improve their security posture, audit and comply with certain external requirements (ISO 27001, PCI DSS, GDPR), and mitigate any sensitive data compromise. Businesses across industries, including finance, healthcare, and e-commerce, use VAPT to protect themselves from financial loss and reputational damage caused by security breaches. It includes two key components.
- Vulnerability Assessment (VA): In this stage, there are scans of systems, networks, and applications using automated tools to identify any security flaws like outdated software, misconfiguration, and weak authentication methods. The idea is to find holes before an attacker can use them.
- Penetration Testing (PT): In this phase, the real-world cyber attacks are simulated against the systems that were detected through the vulnerabilities. These weaknesses are assessed as to the severity and recommendations for remediation are provided by penetration testers.
Importance of VAPT in 2025
With the progress of cyber threats, it comes to pass that an increased organization should embrace a proactive approach to security. Vulnerability Assessment and Penetration Testing (VAPT) helps in detecting security vulnerabilities before they become easy prey to these malicious actors. The reliance on digital systems and the growing importance of compliance have added importance to VAPT assessment, which gained its recognition in 2025.
Rising Cyber Threats
Cybercriminals are targeting businesses using advanced techniques such as AI-driven attacks, ransomware, phishing, and zero-day exploits. By 2025, organizations will face significantly more risks from:
- Cyberattacks Powered by AI – Hackers are using AI to enhance attackers’ efficiency and avoid being detected.
- Ransomware Evolution – Attackers are creating complex codes, locking users out of their data for ransomware that demands large sums for computers to be unlocked.
- IoT Security – More and more businesses are adopting the use of cloud computing and IoT devices and thus are creating gaps in their security.
- VAPT – These assessments are conducted to detect and eliminate existing vulnerabilities so that the organization is in a strong position regarding security.
Regulatory Compliance Requirements
Governments and industry regulators mandate VAPT for many sectors by enforcing strict cybersecurity laws. GDPR, PCI DSS, ISO 27001, HIPAA, and NIST are guidelines that businesses need to comply with. Otherwise, authorities will fine them and impose legal consequences. Failure to perform a VAPT assessment by 2025 can result to:
- Non-compliance penalties from regulatory bodies.
- Loss of business reputation due to data breaches.
- Legal liabilities in case of customer data exposure.
Businesses meet compliance requirements and maintain good trust with stakeholders through regular VAPT assessments.
Protection Against Financial Losses
A cyberattack can be so successful in wiping out valuable data, spending significant cash on rebuilding and legal fees, not to mention financial damage to online reputation. Security investments like VAPT become necessary because the global cost of cybercrime will be 10.5 trillion a year by the year 2025. VAPT benefits in the financial protection include:
- Timely Identifying Security Issues – Before they become prohibitively fraught to cure, VAPT prevents disruption of operations due to cyberattacks.
- Proactively Vulnerability Addressing – This helps reduce ‘incident response’ costs that involve reactive security measures.
Enhancing Customer Trust and Business Continuity
Consumers are more aware of the risk of cybersecurity today than they ever have been. Customer trust and brand reputation are affected due to data breaches. VAPT makes sure that businesses have a secure environment, which in turn gives customers confidence about their data privacy.
“Related content: Read our guide to the Difference between VA and PT“
The VAPT Process
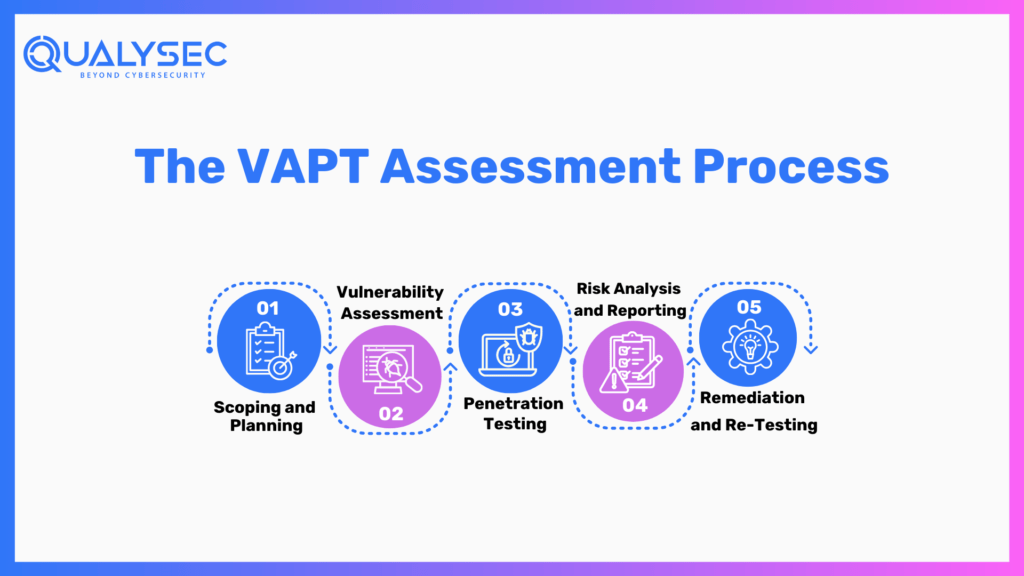
1. Scoping and Planning
Before conducting a VAPT assessment, you must define the scope and objectives of the test. This includes:
- Determine critical assets including applications, networks, databases, and cloud.
- Determining what kind of testing (black box, white box, or grey box) is needed.
- Setting up legal permissions and considerations of ethical and legal testing.
A well-defined scope prevents disruptions to business operations and focuses the assessment on high-risk areas.
2. Vulnerability Assessment
During this phase, you get to the security weaknesses of the system using automated tools as well as manual techniques. The key activities include:
- Tools – Nessus, Qualys, or OpenVAS in order, to find out misconfiguration, obsolete software, and ways of the weak authentication mechanism.
- Common Vulnerabilities Identification – Finding out for SQL injection, cross-site scripting (XSS), open access controls, etc.
- Vulnerability Categorization – Grouping of vulnerabilities as per their sensitivity (Critical, High, Medium, and Low).
Security gaps that need to be imposed before penetration testing are presented in the vulnerability assessment.
“Explore: Top Vulnerability Assessment Methodology“
3. Penetration Testing
This phase involves security professionals making real-world plays against discovered vulnerabilities to determine what they can do. The penetration testing process includes:
- Ethical hacking techniques used to breach security controls are known as initial exploitation.
- Try to gain a higher level inside the system.
- Navigating the network.
- Determining whether the data are sensitive, if it can be extracted, and assessing damage.
Active exploitation of vulnerabilities allows penetration testers to see critical insights into how attackers may invoke real-world attack scenarios.
“Explore: Top Penetration Testing Methodologies“
4. Risk Analysis and Reporting
When done with the VAPT assessment, the findings are elaborated into a complete report. The report typically includes:
- A summary of identified vulnerabilities and their risk levels.
- Technical details of exploited weaknesses.
- Steps to patch security gaps are recommended.
The security team and management need to take corrective actions toward their security posture by reviewing this report.
Latest Penetration Testing Report

5. Remediation and Re-Testing
Once vulnerabilities are found, the organization has to work on remediation, that is:
- Patching software and fixing misconfigurations.
- Strengthening security controls, as such, by the use of multi-factor authentication (MFA).
- Improving how security is defined and using the employee education that was left behind from the breach to prevent such from happening again in the future.
The re-test after follow-up is done to ensure that all the vulnerabilities are accounted for and the system is secure.
Key VAPT Methodologies
Black-Box Testing
Black box testing mimics an attack by an external hacker with no knowledge of the target system’s internal architecture, code, or credentials. Reconnaissance techniques, for example, are used by the tester the way a real-world attacker would deal with it – interacting with the system, gathering information, and exploiting potential weaknesses.
- Role – Evaluate an organization’s ability to protect External Security Defenses against unauthorized access.
- Pros – Gives realistic simulation of attack. Also, it identifies external vulnerabilities.
White-Box Testing
White box testing also known as transparent box or clear box testing gives the tester complete access to the internal structure, source code as well as system architecture. It can be used for thorough security analysis such as the checking of insecure coding practices, logic flaws, configurations, etc.
- Role – Very useful to measure security at the development stage to avoid vulnerabilities before deployment.
- Pros – Provides a thorough code security analysis.
Grey-Box Testing
The hybrid Grey Box approach includes software in which the tester has limited knowledge about credentials or limited access to documentation. This is a method of attack by the insider or hacker who has managed to breach part of the network.
- Role – Testing security posture with inside attackers or even attackers with some system access.
- Pros – Balances efficiency and realism, focuses on high-impact vulnerabilities.
Network Penetration Testing
It is a methodology that qualifies security weaknesses existing in the network infrastructure of an organization, which is composed of routers, firewalls, servers, and connected devices. The tester will test for misconfigurations, weak encryption, and open ports in an attempt to gain unauthorized access.
- Role – It protects the corporate network from external and internal cyber threats.
- Pros – Let you identify risks concerning network misconfiguration. Also, provides anonymity and security for the data transmitted through the network.
Web Application Penetration Testing
It is a method that checks web applications for vulnerabilities like SQL injection, XSS, and broken authentication mechanisms. Web-based flaws are systematically tested in automated tools and manual tools testing techniques.
- Role – It improves the security of online platforms that deal with user data.
- Pros – Uncovers critical application vulnerabilities.
API Security Testing
Data exchange between systems is a hundred times easier using APIs. API security testing is performed to ensure authentication mechanisms, rate limiting, and data validation are hard against unauthorized access and data breaches.
- Role – Protects the API endpoints from the man in the middle (MITA) and API injection attacks.
- Pros – It helps to prevent API-specific vulnerabilities from being exploited.
“Learn more about Advanced Penetration Testing Services!”
How Qualysec Technologies Can Help in VAPT Assessment
With cyber threats always changing, organizations simply cannot trust any company to do the job – it’s a requirement in our digital society to have a partner that you can trust. With Vulnerability Assessment and Penetration Testing (VAPT) services that remain at the top in the industry, Qualysec Technologies ensures that businesses stay resilient against cyberattacks.
Why Choose Qualysec for VAPT?
Comprehensive Security Audits
In the field of network and web security, Qualysec provides in-depth assessments of network, web applications, APIs, cloud, and IoT device-based assessments before vulnerabilities become threats.
Certified Security Experts
Our team consists of Certified Ethical Hackers (CEH), as well as OSCP-certified professionals and cybersecurity analysts who can perform similar to a real-world attack scenario and find security weaknesses within it.
AI-Driven Testing Approach
With higher accuracy of zero-day vulnerability, misconfiguration, etc, we leverage AI-based threat detection.
Detailed Reports with Actionable Insights
The risk ratings on comprehensive reports provide impact analysis, as well as step-by-step remediation guidance to businesses to fix vulnerabilities effectively.
Compliance Readiness
Qulysec will make sure that all organizations meet the requirements of ISO 27001, GDPR, PCI DSS, HIPAA, NIST, etc., and avoid non-compliance penalties.
Continuous Monitoring & Re-Testing
Cybersecurity is an ongoing process. Do regular re-testing and regular checks to continually monitor it so your security measures will stay effective.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
VAPT assessment has officially become a cybersecurity measure that organizations need to undertake to avoid the risks associated with security and protect digital assets in 2025. As cyber threats become more complex, these businesses have to adopt proactive security testing strategies. When you partner with Qualysec Technologies, you are sure to get the best of VAPT solutions in the industry that deprive your organization of being a victim of cyber adversaries. Don’t go for a cyber attack – invest in the VAPT now and protect your business from possible security breaches!































































































































































































































































































































































































































































































































0 Comments