Checking security with the pace of network improvement is known as continuous penetration testing. Continuous testing, in contrast to traditional Pentesting, tests the durability of the latest improvements immediately rather than waiting for a year or even a couple of months. When comparing pentesting vs continuous pentesting, the latter provides real-time insights, ensuring vulnerabilities are addressed proactively.
The reason were traditional pen testing is no longer effective? A comprehensive plan for continuous monitoring is crucial for sustainability in an environment in which ransomware-a-e-services and viruses that are versatile and AI-operated by cybercriminals are constantly growing.
Traditional Pentesting Vs. Continuous Pentesting
Traditional Pentesting
- It can plan the evaluation such as annual, bi-yearly or quarterly.
- It depends on a manual testing approach with some automation
- It consists of fixed rates per engagement.
- It emphasizes specific programs or technologies at a given moment in time.
- Static reports are supplied following the evaluation.
- Remediation gets postponed because of document processing time.
- Observance Suitable for submitting formal reports on compliance.
Continuous Pentesting
- The frequency of continuous testing with 24/7 analysis.
- Depends entirely on the automation tools and equipment.
- Follows a subscription-based approach with different levels.
- checks for risks throughout the whole IT architecture.
- Current information and interactive reports are offered.
- It aids in maintaining compliance throughout time.
“Explore our Complete Guide for Penetration Testing and Vulnerability Assessment“
Why Is Continuous Pentesting Required?
Fresh threats and attacks are occurring each day in today’s dangerous landscape. Companies may be vulnerable to assaults due to the extended intervals among standard tests. Persistent hacking has various benefits.
Preventive cybersecurity is achieved by identifying all flaws and implementing remedies immediately as they can be detected.
Following through with rules regulations, and legal requirements in areas like GDPR and HIPAA, many organisations cannot go weeks without checking their safety measures.
Enhancing the management of risks while maintaining current data about safety state allows businesses to control the risks associated with cybersecurity more effectively.
Affordable over a long time run, while traditional pen testing might seem to be less expensive in terms of upfront expenditure, the implications of an undiscovered intrusion may prove substantially more expensive than running the assessments regularly.
The Continuous Penetration Testing Technique
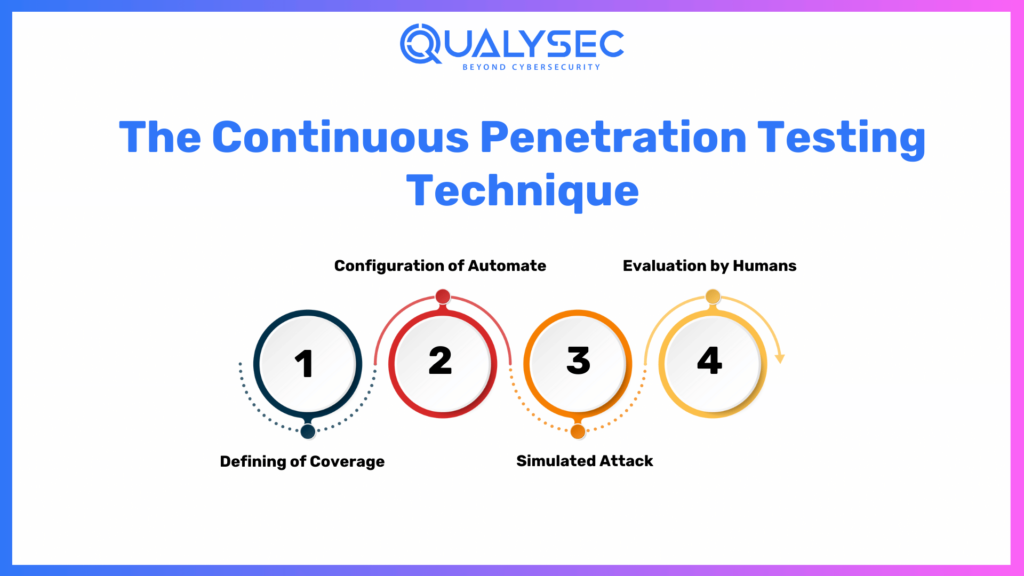
Continuous penetration testing covers the following crucial measures:
Defining of Coverage
Identify the parameters, supplies, and outcomes of the network or programs you plan to test. A web page, cellphone application, computer, system, Application Programming Interface or data are all included in this.
Configuration of Automate
To continually monitor the IT infrastructure for risks, machines are used. This includes channel functioning, connection detection, and the ability to identify code flaws.
Simulated Attack
SQL injection and cross-domain scripting including phishing attacks are a few of the attack models. It looks for vulnerabilities and assesses how your system responds to them.
Evaluation by Humans
Security professionals identify and verify weaknesses discovered through ongoing testing for safety, and they also suggest solutions to mitigate or eliminate them. In these situations, certain vulnerabilities may be more intricate and call for closer examination than the software program can provide.
“You might like to learn about Security Testing Services!“
Advantages of Continuous Pentesting
- Encourage self-belief to create fearlessly
- Use active security instead of defensive risk management
- Increase safety towards technical performance
Latest Penetration Testing Report

How Qualysec Can Help You To Achieve?
At Qualysec, we specialize in providing the best offerings, including continuous pen testing. Using advanced automated methods for periodic assessments to identify your networks’ vulnerabilities, our team of trained professional hackers ensures that you receive the greatest degree of safety defence.
Extensive Evaluation:
For this reason, we provide frequently planned penetration testing for systems, mobile apps, internet pages, and APIs.
Actual Time Notifications:
To enable your group to respond appropriately, we provide current-time notifications of hazards that have been discovered.
Skilled Evaluation:
The entire process monitoring is provided by software programs, which work in tandem with our team of cybersecurity specialists’ testing methods.
Customisable Options:
Regardless of the size of your company, our computerized penetration screening procedures are completely adaptable to meet your specific requirements.
Adding towards this, Qualysec allows can to unwind realizing that your computer networks are always fully safeguarded while you delegate the work of network management to us.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
To Sum Up
Penetration testing is frequently used by different groups as a crucial component of implementing effective safety protocols. It provides full defence from online attacks because of its continuous tracking, proactive detection, and ongoing safety improvement. Continuous penetration testing helps your company stay ahead of prospective hackers in the ever-changing threat landscape of nowadays.
Qualysec offers you the best services for penetration testing to safeguard your company from harmful threats, regardless of your decision to require aid in creating, modifying, or upgrading your penetration testing processes.






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments