What is a Penetration Testing report?
A penetration testing report is a detailed review of the security risks in a computer system, network, cloud service, website, or mobile app, that could allow someone to break in. The report covers weaknesses that were found. It covers how serious these threats are, what parts of the system they affect, steps to recreate the issue, and ways to fix the problems. Hence, it lets you know where your security gaps are and how to fix them. This blog aims to provide a comprehensive guide about what penetration testing report is.
Different types of Penetration Testing report
When you hire someone to test your computer systems and networks for security weaknesses, they’ll provide you with a detailed report of their findings. Depending on what you ask them to look for, these penetration testing reports can vary. Internal penetration testing reports check for insider risks (like human errors) and external penetration testing reports look for vulnerabilities that outside hackers could exploit.
1. Internal Pen Test Report
This type of testing looks at the risks an organization faces from the inside. The tester acts like an employee or contractor with some level of access provided by the firm. They try to see what data or systems a notorious employee could compromise. This helps the pentester to identify weaknesses in access controls, policies, and internal security practices.
2. External Pen Test Report:
External pen testing evaluates the threats from outside such as attackers and hackers on the internet. The tester has no prior access and tries to break in from the outside, just like a real cybercriminal. This exposes vulnerabilities in systems, websites, firewalls, and other perimeter defenses.
Both internal and external tests are important for getting a full picture of your security posture against insider threats and outside attacks. The reports outline the gaps that were found and give recommendations for fixing them.
Why Penetration Testing is Important for Small Business
Penetration testing is important for small businesses for various reasons. Small businesses are prone to cyber-attacks as their security system is weak or not secure enough as compared to big firms. A data breach can affect the entire operation of small businesses. They can have an effect on their data causing a critical loss and financial loss for the businesses. It also causes major reputational damage that smaller firms can’t recover from easily.
Hiring ethical hackers to purposely try and breach the company’s systems is a smart move. They find the vulnerabilities and security gaps and then provide recommendations to fix them properly. It’s a legal way to expose weaknesses before criminals can exploit them for malicious purposes.
For small businesses without massive security budgets, pen testing is an affordable way to get an expert security assessment. It lets them strengthen their systems against skilled hackers actively searching for soft targets to attack. Hence, identifying and fixing risks gives small companies a fighting chance to protect their business from cyber threats.
What is the Purpose of the Penetration Testing Report?
A Penetration testing report provides you with all the essential findings and the vulnerabilities that are discovered. So these reports provide an advantage when it comes to strengthening the security system. The main reasons these reports are so valuable are:
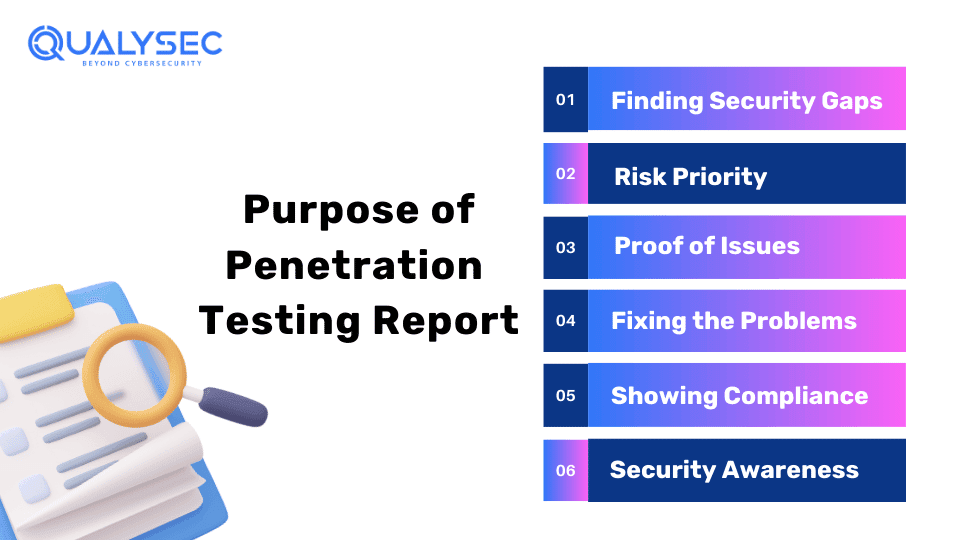
- Finding Security Gaps – The report identifies the areas where your security controls have potential openings that could be bypassed or breached. This identification allows you to focus your efforts on sealing the biggest security gaps first.
- Risk Priority – The report assesses the likelihood of each vulnerability being exploited and the potential damage it could cause, and prioritizes the risks that require urgent attention over others.
- Proof of Issues – The ethical hackers attach screenshots, data logs, and step-by-step examples to demonstrate how they exposed each security weakness.
- Fixing the Problems – The reports list the vulnerabilities discovered, and they provide detailed, practical guidance on how to remediate those security risks and gaps.
- Showing Compliance – For certain regulated industries, pen testing shows auditors and authorities that cybersecurity best practices are properly implemented.
- Security Awareness – Seeing the clever hacker tactics used provides an eye-opening education on real-world threats and the consequences of data breaches.
The biggest advantage is having an outside party of trusted “white hat” hackers take their best shot at breaching your systems, transparently documenting the findings. This ethical hacking gives you an unbiased assessment of your true cybersecurity vulnerabilities before actual criminals discover them.
Download Sample Pentest Report:
Do you also want to generate a penetration testing report? Qualysec Technologies provides latest sample Pentest report that will keep your organization secure from evolving cyber threats download now and get amazing offers!
Latest Penetration Testing Report

5 Key Components of a Penetration Report
Here is a complete overview of the key components of the penetration testing report:
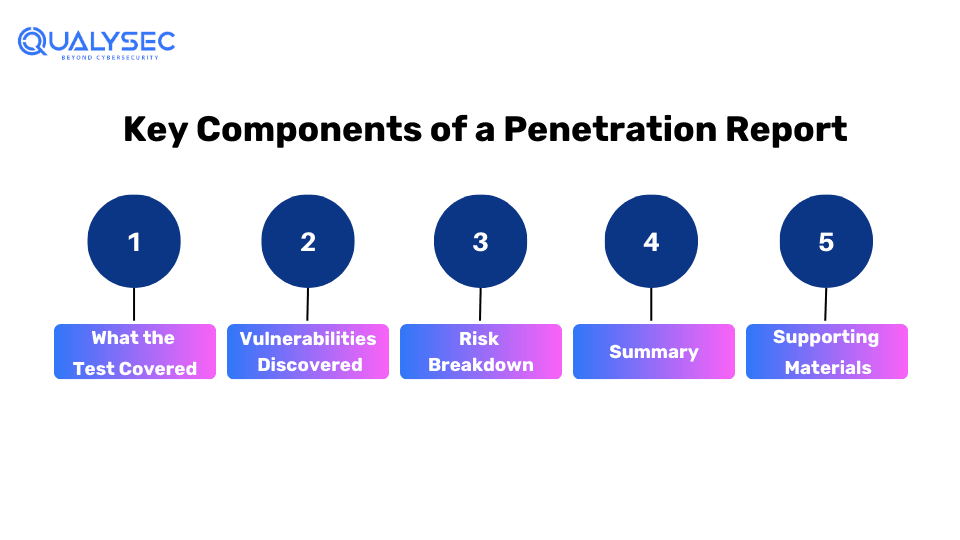
1. What the Test Covered
The first part lays out exactly what systems, networks, websites, etc. were tested and what the main goals were. It specifies if it was an internal test (acting like an employee) or an external (like an outside hacker). This also covers the testing methods used and how long they lasted. It sets the expectations for what got evaluated.
2. Vulnerabilities Discovered
This section goes over all the vulnerabilities and security weaknesses the testers managed to find and exploit. It explains what the potential impact is if these gaps are breached by attackers. Screenshots and evidence are documented for each issue. Most importantly, it provides clear remediation steps for fixing or minimizing the risks of each vulnerability.
3. Risk Breakdown
The report determines the severity and likelihood of potential exploitation of the network or system. It defines and breaks down each security issue. It assigns risk scores based on standard guidelines to assess the threat level posed by every vulnerability discovered during testing. This prioritizes which weaknesses need to be addressed most urgently.
4. Summary
This recap highlights the biggest takeaways and overall risk exposure based on all the findings. It sums up the main areas that need improvement and any positives noted during the test. There are suggestions for any additional testing that may be warranted too.
5. Supporting Materials
Any supplementary data from the test is included here as appendices. Things like testing logs, tools used, code samples, and reference guidelines are attached. Hence, this section is termed as supporting materials or Documentation.
Protect your digital Asset today! Schedule a consultation with our Cybersecurity Expert and safeguard your data against online threats.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Various Compliance Standards for Pen Tests & VAPT Report
When it comes to penetration testing reports, you might think they’re all pretty much the same. But it’s far from the truth. Different cybersecurity standards and guidelines have their specific requirements that need to be included, and we must follow these standards.
PCI-DSS
-
- Deep analysis of any vulnerabilities found
- Evidence showing how the testing was done
- Suggestions for fixing or reducing risks
- Any violations of PCI rules linked to each vulnerability
ISO/IEC 27001
A widely-used international standard that provides a framework for establishing, implementing, maintaining, and continually improving an information security management system.
SOC 2 Type I & Type II
Reports that assess whether a service organization’s controls related to security, availability, processing integrity, confidentiality, and privacy are suitably designed (Type I) and operating effectively (Type II). Often required for cloud service providers.
HIPAA
The Health Insurance Portability and Accountability Act sets standards for protecting sensitive patient health information for organizations associated with the healthcare industry.
GDPR
The General Data Protection Regulation is a legal framework that sets guidelines for collecting and processing personal information of individuals within the European Union. It also addresses data export, data breach notifications, and data subjects’ rights.
Best Practice Tips for Effective Pen Testing Report
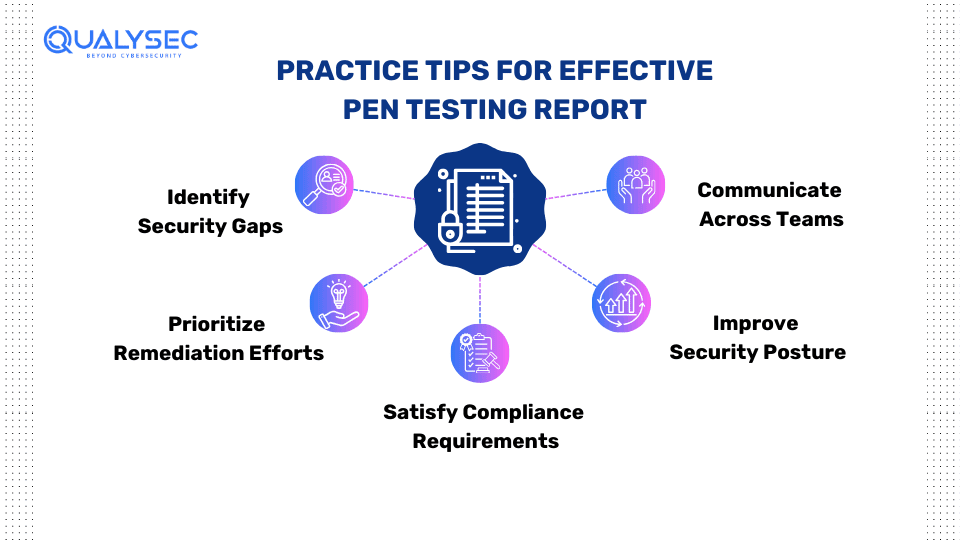
Identify Security Gaps
-
- A quality pen test report clearly lays out any vulnerabilities or weaknesses discovered during testing
- This allows the organization to understand their current risk exposure and areas needing improvement
Prioritize Remediation Efforts
-
- Better reports will prioritize and rank the findings based on risk severity
- This helps InfoSec teams quickly tackle the highest-impact issues first
Satisfy Compliance Requirements
-
- Many industry regulations and standards mandate periodic pen testing like GDPR, ISO 27001, HIPAA, etc.
- Comprehensive reports demonstrate due diligence and provide documentation for audits
Improve Security Posture
-
- In-depth reports provide specific remediation recommendations
- Following the report’s advice allows organizations to properly address and mitigate risks
Communicate Across Teams
-
- Well-written reports bridge the gap between technical and non-technical stakeholders
- Executive summaries convey risk impacts in easy-to-understand business terms
The key is creating pentest sample reports that are clear, actionable, and tailored appropriately for the intended audience. This ensures the findings don’t just get documented, but actively drive meaningful security improvements.
Conclusion
Therefore, summarizing using the right approach to reporting is important in keeping you on course with the objective of safeguarding the security situation. The adoption of the widely accepted formats (structuring the report clearly, highlighting the key issues, having the diagrams and evidence, and putting the premises and actions forward) will provide the foundation for a powerful and persuasive report.
A good Penetration Testing Report lets you find weak spots, manage risks properly, and improve your overall security score. A top-notch pentest report lets you take real actions against potential attackers and hackers before they can attack. That’s why working with cybersecurity experts like Qualysec is so valuable. They have the special tools and skills to deeply check all your systems. Their pentest can reveal holes you missed, and their reports tell you exactly how to fix issues before hackers exploit them.
If you need an expert pentest report for your company, contact Qualysec today. Their services give you the insights to strengthen your defenses and stay ahead of cyber threats. Contact them now to level up your security.
“Explore our recent post on How Much Does Penetration Testing Cost!”
FAQs
Q. What is a pentest report?
A pentest or penetration testing report gives you the full scoop on what happened after cyber experts tried to hack into your systems and networks. Hence, it lists out any weak spots they were able to break into and tells you exactly how to fix those security gaps.
Q: What is the methodology of the penetration report?
A: Penetration testing report methodology:
-
- Scope of the test
- Vulnerabilities detected
- Impact level of the vulnerabilities
- Remediation steps
- Summary of the test
- Additional materials
Q: Why is penetration testing Important?
A: Getting regular pen tests done is important for a few key reasons. It uncovers security risks before cyber threats interrupt the functioning of the firm. It validates whether your current security measures are working as intended. Many cybersecurity rules and standards require periodic penetration testing.
Q: How to make a penetration testing Report?
A: To make a quality pentest report, start with an executive summary of the highest risks. Use visual diagrams and screenshots as evidence. Focus on providing clear remediation advice. Be mindful of the audience’s technical knowledge level when giving details. Review thoroughly before delivery.






























































































































































































































































































































































































































































































































0 Comments