A penetration test (also known as a pentest or ethical hacking) is a controlled cyber assault carried out by an ethical hacker. The objective is to identify security flaws that a criminal hacker may use for malicious purposes. Penetration testing for small businesses can help them view their systems and applications like an attacker would, detecting weaknesses and how they are exploited.
Penetration testers employ the same techniques as criminal hackers, mimicking their methodology as precisely as possible. Following the test, the ethical hacker prepares a report advising the organization on enhancing its defenses and preventing assaults.
In this blog, you’ll learn why, how, and when to conduct penetration testing for start-ups. We have discussed everything you need to know in this detailed guide. Without any further ado, dive in.
How can a Startup Embrace Cybersecurity into its Culture?
Embracing cybersecurity within a startup culture entails creating a proactive and security-conscious mentality at all levels of the firm. First, leaders should prioritize cybersecurity by committing money for training, tools, and expertise. Educating all staff about cybersecurity dangers and recommended practices through frequent training sessions and awareness campaigns is critical.
Encouraging an accountability culture in which everyone takes responsibility for protecting sensitive information and reporting potential risks is critical. Implementing strong security measures, such as multi-factor authentication and encryption, should be included in the company’s procedures and workflows from the beginning.
Including cybersecurity in the business plan helps create a security-first mindset that evolves with the startup.
Finally, creating an atmosphere in which open communication about security issues is encouraged aids in quickly addressing and mitigating potential cyber risks. By incorporating cybersecurity into its culture, a firm may effectively safeguard its assets, reputation, and consumer confidence.
The Importance of Penetration Testing for Small Businesses
Penetration testing for start-ups is necessary. New vulnerabilities are constantly being identified; if your organization does not identify them quickly, a cybercriminal will.
Did you know that in 2022, cyber security experts found over 25,000 CVEs? It was the greatest number ever recorded, demonstrating how increasingly difficult it is for organizations to fix software issues.
You will be able to find and resolve vulnerabilities more quickly if you test your systems and network on a frequent basis. A penetration test for start-ups is advised at any level of development, including establishment, validation, and expansion. Some of the primary benefits of doing cybersecurity assessments on a regular basis are as follows:
1. Regulatory compliance
Many companies operate in industries governed by legal and regulatory requirements. Obtaining SOC 2 compliance, particularly in recent years, has been a major driver of pentesting procurement. Penetration testing helps to assure compliance with these standards by demonstrating a commitment to security best practices while avoiding potential penalties and legal difficulties.
2. Customer trust and loyalty
According to 2022 research, 57% of startups are asked by prospective clients to demonstrate their security procedures. Lack of suitable certification, security audits, or at least a recent full report following a penetration testing assessment can stymie a company’s growth, particularly in its early stages.
3. Vendor/third-party requirements
Startups frequently perform penetration testing, not only because partners may want a report, but also to build confidence in vendor and third-party connections. Startups demonstrate their commitment to data security by thoroughly testing their systems and enhancing their credibility with larger organizations with stringent security standards.
If you want to check how a pentest report can help your business gain client trust, download our sample report.
Latest Penetration Testing Report

4. Protection from data breaches
Startups may drastically minimize their risk of data breaches by detecting and correcting vulnerabilities early on. This is critical for securing sensitive information, including customer data, intellectual property, financial records, and the startup’s assets and reputation. Protecting sensitive data is crucial since startups commonly manage intellectual property and sensitive consumer data.
5. Increased security posture and resilience
Regular penetration testing helps businesses create a strong security posture by regularly detecting and resolving vulnerabilities. This continual procedure improves security and increases the startup’s resilience to intrusions.
6. Competitive edge
In competitive marketplaces, startups demonstrating a strong commitment to cybersecurity through penetration testing may acquire a competitive edge. This is especially true as customers become more concerned about cybersecurity compliance.
How Does Penetration Testing Work?
An expert penetration tester can simulate criminal practices while causing little damage. The penetration tester generates a report that describes any vulnerabilities discovered (and, if feasible, exhibits proof of concept) and provides advice on how to mitigate them. The penetration testing consists of phases that test the assets from head to toe.
The picture below demonstrates the steps involved and how they impact the whole test.
1. Information Gathering
Data collection is intended to improve knowledge of the organizational infrastructure’s user roles, permissions, and data flows. The testing company undertakes reconnaissance, which entails acquiring information about the target applications, network architecture, and possible entry points.
2. Scoping
This entails establishing testing objectives and targets, identifying technological difficulties, and building a comprehensive strategy. Furthermore, the activities include:
-
- Defining the scope of the penetration test.
-
- Identifying specific goals.
-
- Assessing the potential impact on the firm.
-
- Evaluating technical issues.
-
- Developing an overall testing strategy.
3. Auto Tool Scan
An automatic and invasive scan is necessary for testing, particularly in a staging environment. Specialized VAPT tools conduct a thorough search for vulnerabilities on the application’s surface. This invasive scan mimics a potential attacker, detecting surface-level vulnerabilities in the staging environment and allowing for rapid modifications before deployment in production.
4. Penetration Testing
Penetration testing aims to discover holes in programs, particularly in authentication and data management. Active testing entails mimicking real-world assaults to identify system weaknesses. This comprises using flaws in the program, network, or other components to evaluate security measures.
5. Reporting
During this stage, the testing organization offers detailed documentation to consumers and developers about discovered vulnerabilities, categorizing them based on high-level testing. It also provides a thorough report explaining the found vulnerabilities, their severity, and the possible impact on the company. The corrective recommendations are organized according to danger.
6. Remediation Assistance
Here, the testing provider assists development teams in duplicating and limiting vulnerabilities while assuring effective resolution. Activities include consultation calls with development teams to assist them in implementing appropriate security measures. They also help to reproduce discovered vulnerabilities in controlled conditions and work on effective mitigation techniques.
7. Retesting
This phase evaluates the effectiveness of vulnerability mitigation after development. Follow-up tests should be undertaken to ensure that the identified vulnerabilities have been addressed effectively and that the implemented solutions adequately reduce the risks. This rating indicates that your organization’s security posture has improved.
8. LoA and Security Certificate
The testing company provides a Letter of Attestation and a Security Certificate to assure security, compliance, stakeholder and customer confidence. Furthermore, giving a Letter of Attestation verifies the completion of penetration testing, including the scope and methodology employed. It demonstrates compliance with security standards and legislation, increasing customer trust in the organization’s security initiatives.
What Kind of Pentest is Best for a Small Business?
It depends on your aim and objectives. If your company relies on a web application, gray box testing is the most effective way to uncover flaws and prevent risks. Web programs rely heavily on their architecture; design choices and component interactions can significantly impede this.
Black box testing is used when you wish to recreate an external assault as nearly as possible. Vulnerabilities are uncovered while the penetration tester navigates your systems, naturally constructing an attack route. If your company is deeply concerned about external attacks on its infrastructure, black box testing is for you.
Suppose you are concerned about a malicious insider or want to learn about the widest range of vulnerabilities. In that case, you will need a thorough grasp of your application and network design, corporate culture, and access tools. White box testing is the best way to reduce internal risks and better understand your entire security posture.
Finally, a small organization may find PTaaS (penetration testing as a service) to be a cost-effective solution, providing access to deep penetration testing more frequently.
Are you willing to take the next step toward safeguarding your business and digital assets? Connect to the leading offensive security testing company that provides deep pentesting as a service.
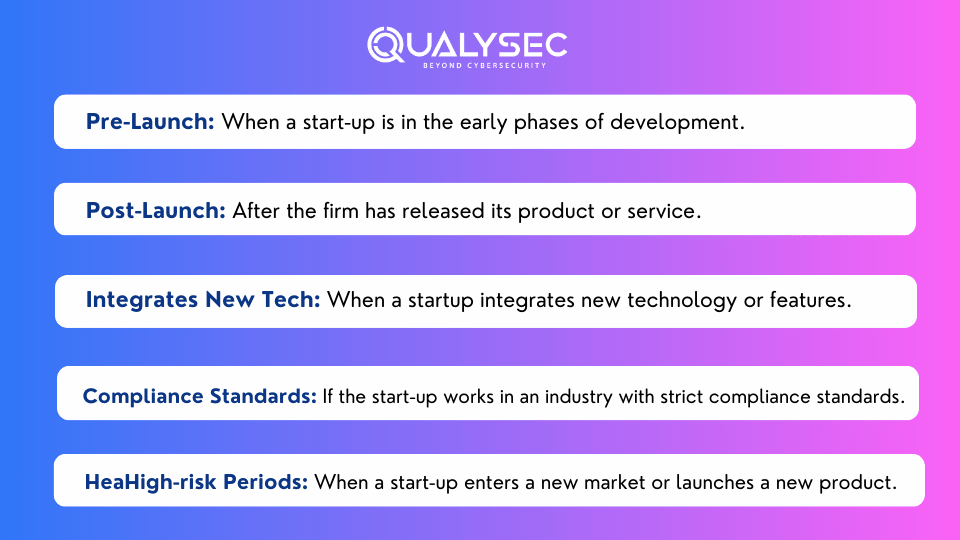
When Should a Small Business Get Penetration Testing Done?
The timeline of penetration testing for start-ups or small businesses varies depending on criteria such as the type of the firm, the sector it works in, and its overall risk profile. However, here are some broad suggestions for different stages of start-up:
Continuous Testing
While the various steps stated above emphasize essential areas, it is critical to regard pentesting as a continuous activity. Regular testing, preferably incorporated into the development lifecycle, contributes to a proactive and resilient security posture.
Challenges Small Businesses Face with Penetration Testing
As startups face budgetary limits, limited in-house IT experience, and a complex web of various technologies, implementing adequate security measures becomes a difficult balancing act.
1. Budget Constraints
Small organizations frequently encounter budget constraints when allocating funding for penetration testing. Limited financial resources might make it difficult to invest in comprehensive security audits.
2. Employee Issues
Consider this: a tiny firm with a few employees wearing numerous hats. Add a dearth of specialized IT and security staff to the mix. It’s like juggling a dozen chores with insufficient hands, making it difficult to monitor and address security problems straight on.
3. Integration Issues
Integrating penetration testing into established company procedures might be difficult. Small firms may struggle to smoothly integrate testing into their development lifecycle or continuous operations, resulting in possible security weaknesses.
4. Priority of Security
Balancing day-to-day operational demands with long-term security concerns can be challenging for small firms. Some may favor immediate commercial goals over security precautions, underestimating the long-term consequences of a security breach.
How Can Small Businesses Find the Correct Pentest Vendor?
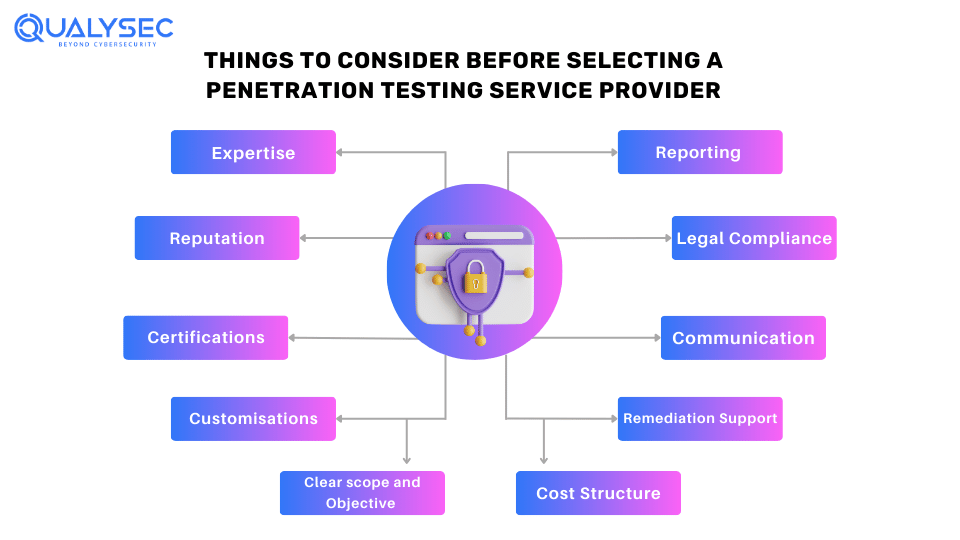
There are several reasons to perform a pentest, such as improving security defenses, lowering risk levels, or satisfying tight compliance requirements. But how can you pick the proper penetration testing company? What should you consider before hiring an external provider? Here’s a checklist to help you find the finest penetration testing company for your small business or startup:
Expertise: Make sure the service provider has experience testing specified technologies crucial to your business.
Reputation: Study the providers’ reputation by seeking testimonials, case studies, and customer references.
Certifications: Check if the testing team has the necessary certificates, such as CEH.
Customization: Search for a service provider who can customize testing processes to meet your specific goals and issues.
Clear Scope and Objectives: Outline your scope and objective of the pentest to make sure they align with your company goals.
Reporting: Ask for sample reports to verify they are comprehensive, developer-friendly, and provide actionable suggestions.
Compliance: Ensure the service provider supports ethical standards and follows the rules.
Communication: Assess the vendor’s communication and response to ensure a smooth testing process.
Remediation Support: Inquire about post-testing support, such as remediation and fixing detected vulnerabilities.
Cost Structure: Understand the provider’s penetration testing cost and confirm it is consistent with your budget limits.
How Can Qualysec Help You with Penetration Testing?
Qualysec Technologies is one of the Leading Offensive Security Testing Companies that prevails in providing penetration testing for small businesses. At Qualysec, we provide a process-based penetration testing approach.
We combine automated tools to scan the surface-level vulnerabilities of an app and deep manual testing that goes beyond the surface level to find issues that a tool may miss. We offer a clean and comprehensive pentest report that lists the issues and helps your developer team mitigate the vulnerabilities with actionable references.
Add Image- Why is Qualysec a Top Provider of Penetration Testing for Small Businesses?
We also ease the remediation part with consultation calls with your development team to help them fix issues in case any queries crop up. We ensure that your company not only meets but surpasses industry requirements by conducting penetration tests, safeguarding your digital assets, and strengthening consumer trust.
With a track record of securing 350 assets from across 18+ countries, we have not received a single record of a data breach from our client. Working with companies from Fortune 500 to startups, we have prevailed in cybersecurity since our establishment.
Connect with seasoned professionals for penetration testing for start-ups and gain access to robust cybersecurity strategies. Contact Qualysec Today!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
The digital sphere is riddled with dangers. However, it is also full of opportunity. Small enterprises must strike a balance between taking advantage of internet possibilities and protecting themselves against risks.
As the worrisome number indicates, no firm is too small to attack. As a result, preemptive procedures such as penetration testing are not just suggested but necessary. Investing in rigorous penetration testing for small businesses ensures their long-term viability, reputation, and future success.
FAQs
What is the cost of penetration testing for small businesses?
The cost of penetration testing for small businesses varies with different factors such as aim and objective, application type, timeline, expertise, etc.
What type of small business benefits most from penetration testing?
Companies that handle sensitive data, or those who rely on applications, or are subject to compliance requirements, those need penetration testing.
How many times should a start-up conduct penetration testing?
It is recommended to conduct penetration testing once a year, but it is also advised to do it when there is an update in technology and features.
Why is penetration testing essential?
Penetration testing offers a detailed insight on exploitable security threats. This helps in identifying vulnerabilities that can harm any business’s digital asset and reputation.






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments