One of the most important challenges in information systems is security. The rising interconnectedness of computers via the internet, and the increasing extensibility of systems have made software security a more serious challenge than in the past.
Furthermore, it is a responsibility to appropriately safeguard a company’s information assets by using a comprehensive and organized approach to protect against the dangers that an organization may encounter. Security specialists have created numerous security assurance approaches such as penetration testing, in an attempt to address the security challenge and comply with mandatory security standards.
This article introduces penetration testing. It goes over the advantages, techniques, and methodology of penetration testing. We’ll also shed light on who needs pen tests, the tools and why should a business choose a service provider. Keep reading to know more.
What is Penetration Testing?
Penetration testing, often known as a security pen test, is a simulation of a cyberattack on a company’s infrastructure. Security professionals or ethical hackers are hired by organizations to execute an assault against their IT infrastructure in order to detect misconfigurations and existing vulnerabilities in online applications, networks, and on the user’s end.
It also seeks to assess the efficacy of an organization’s defensive mechanisms, security policies, regulatory compliance, and employee knowledge. A web application pen test, for example, seeks to uncover, test, and report on APIs, backend, and frontend vulnerabilities in order to fine-tune web application firewall (WAF) policies and correct found security flaws.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Why is Pen Testing Important?
Penetration testing aids in assessing an organization’s systems, applications, and networks’ security. It detects security flaws before thieves do. Penetration testers mimic assaults in order to uncover security flaws.
This approach assists an organization in identifying and correcting problems before a criminal may exploit them. Penetration testing services allow you to evaluate the efficacy of your system’s security safeguards. It also assists firms in designing more effective security procedures and security controls. Below are some of the reasons why businesses need to conduct penetration testing:
- It Assists with Regulatory Compliance
Certain security controls require data security rules such as the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR). Penetration testing can assist businesses in demonstrating compliance with these rules by confirming that their controls function as intended.
- It Saves from Monetary Loss
Due to notification expenses, remediation efforts, lower productivity, and lost income, organizations spend millions of dollars to recover from a security breach. According to the CSI research, recovery operations alone cost $167,713.00 per occurrence. Penetration testing can discover and fix issues before unethical hackers create a security breach, hence reducing financial damage caused by a security breach.
- It Saves the Brand Image
A single event involving compromised client data may be disastrous. Loss of consumer trust and corporate reputation might jeopardize the entire corporation. Penetration testing also raises awareness of the necessity of security at all levels of the company. Furthermore, this assists the firm in avoiding security issues that jeopardize its corporate image, jeopardize its reputation, and undermine consumer loyalty.
- It Secures Business Infrastructure
A secure infrastructure is critical for every firm. Penetration testing is one of the most prevalent methods for testing a security system. Penetration testing assists in identifying weak points in an application or network that is readily abused by a cyber-criminal.
Who Needs to Perform Penetration Testing?
Penetration testing is an important technique for firms in a variety of sectors that want to protect their digital assets and implement strong cybersecurity measures. It also helps businesses of all sizes, from tiny start-ups to huge organizations, find weaknesses in their systems and networks.
Furthermore, IT departments and security teams use penetration testing to replicate real-world cyber assaults. This allows them to evaluate the efficiency of existing security measures and incident response procedures.
Financial institutions, healthcare providers, e-commerce platforms, and government organizations, among others, need proactive security measures to protect sensitive data. Organizations may keep one step ahead of possible attacks, minimize risks, and improve their overall security posture by running penetration testing on a regular basis.
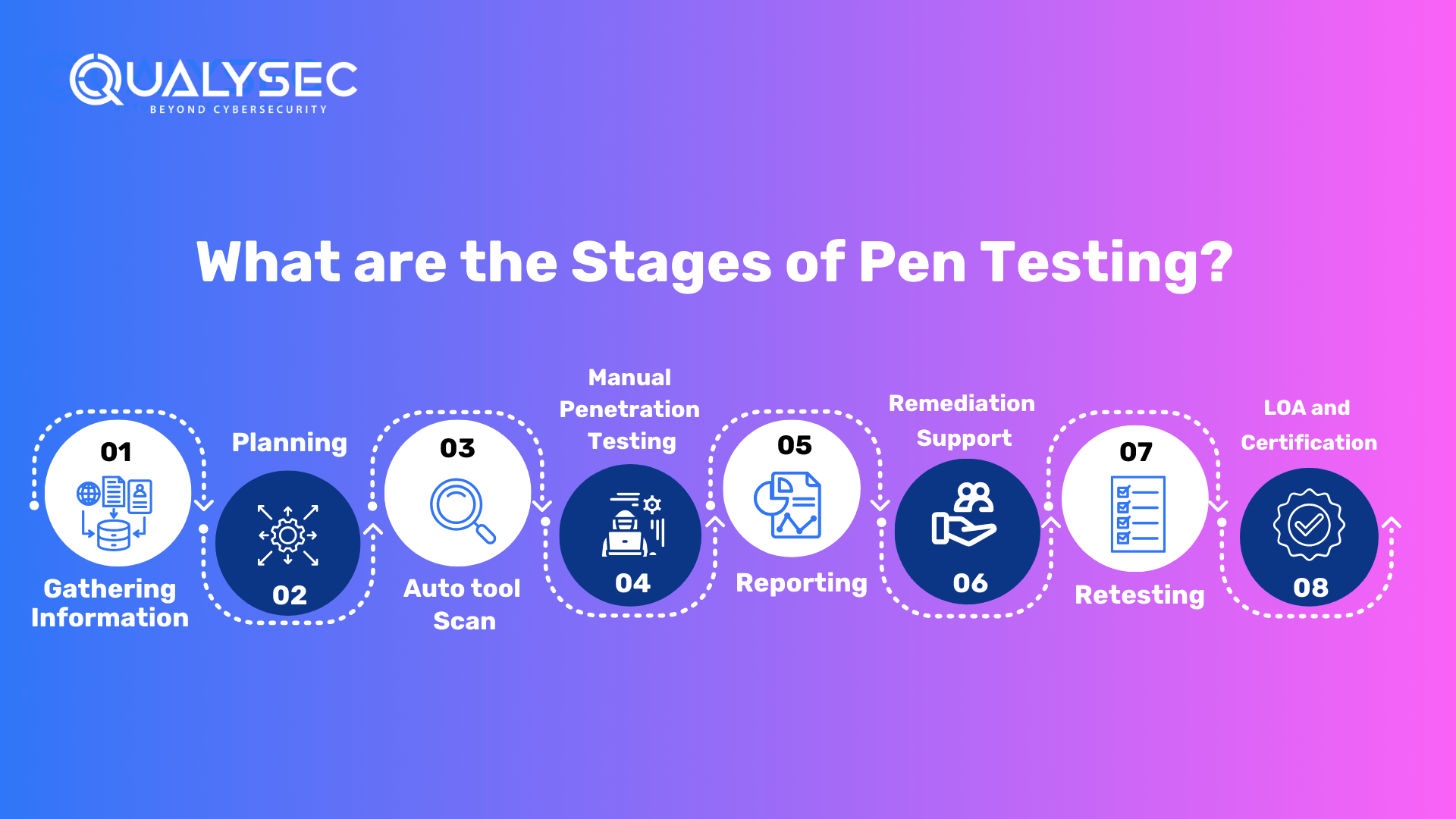
What are the Stages of Pen Testing?
Here is the step-by-step guide to the process of penetration testing containing all the phases of how the testing is done:
Gathering Information
The primary focus in penetration testing is on extensive information collection. This entails a two-pronged approach: exploiting accessible information from your end and employing multiple approaches and tools to gain technical and functional insights. The penetration testing company works with your team to obtain important application information. Furthermore, architecture schematics, network layouts, and any current security measures may be included. Understanding user roles, permissions, and data flows is essential for designing a successful testing approach.
Planning
The penetration testing service provider begins the penetration testing process by painstakingly establishing the objectives and goals. They probe deeply into the complexities of your application’s technology and functionality. Furthermore, this thorough examination enables the testers to modify the testing approach to address particular vulnerabilities and threats relevant to your environment.
A thorough penetration testing strategy is developed, describing the scope, methodology, and testing criteria. The firm will provide a high-level checklist to guide the testing process. This checklist serves as a thorough foundation, covering important topics such as authentication techniques, data processing, and input validation.
They gather and set up the necessary files and tools for testing. Configuring testing settings, verifying script availability, and developing any bespoke tools required for a smooth and successful evaluation are all part of this process.
Auto Tool Scan
Ding the penetration testing process, requires automate and invasive scans, especially in a staging environment. This scan entails using specialized pen testing tools to methodically look for vulnerabilities on the application’s surface level. By crawling through every request in the application, the automated tools simulate possible attackers, revealing potential flaws and security holes.
The pen testing firm proactively discovers and fixes surface-level vulnerabilities in the staging environment by performing this invasive scan, providing a preventative step against prospective attacks. This method not only ensures a thorough evaluation but also fast correction, strengthening the application’s security posture before the deployment in a production environment.
Manual Penetration Testing
The penetration testing company provides a full range of deep manual penetration testing services that precisely align with your individual needs and security standards. This is also a one-of-a-kind technique that enables a complete analysis of possible vulnerabilities across several domains, including:
- Network Penetrating Testing: Extensive network infrastructure examination to discover and eliminate vulnerabilities, assuring the resilience of your entire network security.
- API Penetration Testing: In-depth examination of API functionality, with a focus on possible flaws and security breaches, to strengthen the robustness of your application interfaces.
- Web Applications Penetration Testing: Systematic evaluation of online applications, probing for weaknesses in authentication, data management, and other crucial areas to improve the security posture of the application.
- Mobile Apps Penetration Testing: A specialized assessment of mobile apps that identifies and addresses vulnerabilities specific to mobile settings, assuring the safe launch of your mobile applications.
Reporting
The pen testing team methodically identifies and categorizes vulnerabilities uncovered throughout the assessment, ensuring that possible risks are well understood. In addition, a senior consultant does a high-level penetration test and goes over the complete report.
This assures the greatest quality in testing procedures as well as reporting accuracy. This extensive documentation is a helpful resource for understanding the application’s security situation.
Key Report Components:
- Vulnerability Name: Specifies each vulnerability, such as SQL Injection, providing a precise identification.
- Likelihood, Impact, Severity: Quantifies the potential risk by assessing the likelihood, impact, and severity of each vulnerability.
- Description: Offers an overview of the vulnerability, enhancing comprehension for stakeholders.
- Consequence: Describes how each vulnerability could impact the application, emphasizing the importance of mitigation.
- Instances (URL/Place): Pinpoints the location of vulnerabilities, facilitating targeted remediation efforts.
- Step to Reproduce and POC: Provides a step-by-step guide and a Proof of Concept (POC) to validate and reproduce each vulnerability.
- Remediation: Offers actionable recommendations to effectively eliminate detected breaches, promoting a secure environment.
- CWE No.: Assigns Common Weakness Enumeration identifiers for precise classification and reference.
- OWASP TOP 10 Rank: Indicates the vulnerability’s ranking in the OWASP TOP 10, highlighting its significance in the current threat landscape.
- SANS Top 25 Rank: Indicates the vulnerability’s ranking in the SANS Top 25, further contextualizing its importance.
- Reference: Provides additional resources and references for a deeper understanding of vulnerabilities and potential remediation processes.
This thorough reporting strategy guarantees that stakeholders acquire relevant insights into the application’s security state and receive actionable suggestions for a strong security posture.
Remediation Support
The penetration testing service provider provides service through consultation calls if the development team requires assistance in mitigating reported vulnerabilities. Furthermore, the penetration testers encourage direct interactions to assist the development team in efficiently understanding and addressing the security risks. This collaborative approach guarantees that the development team receives professional counsel, enabling a rapid resolution of vulnerabilities to improve the application’s overall security posture.
Retesting
Following the development team’s completion of vulnerability mitigation, a critical step of retesting occurs. Our staff conducts a comprehensive assessment to confirm the efficacy of the remedies performed. The final report is extensive, containing:
- History of Findings: This section provides a full record of vulnerabilities discovered in past assessments, providing a clear reference point for following the progress of security solutions.
- State Assessment: Clearly defines the state of each vulnerability, whether it is fixed, not addressed, or ruled out of scope, providing a comprehensive summary of the remediation outcomes.
- Proof and Screenshots: Adds physical proof and screenshots to the retest report, providing visual validation of the corrected vulnerabilities. This validates the procedure and assures a thorough and accurate assessment of the application’s security state following repair.
LOA and Certificate
The testing organization goes above and above by offering a Letter of Attestation, which is a critical document. Furthermore, this letter, bolstered by data from penetration testing and security assessments, fulfills several functions:
- Level of Security Confirmation: Use the letter to obtain physical certification of your organization’s security level, ensuring stakeholders of your security measures’ strength.
- Showing Stakeholders Security: Show clients and partners your dedication to security by using the letter as a visible witness to the thoroughness of your security processes.
- Fulfillment of Compliance: Address compliance needs quickly, as the Letter of Attestation is a helpful resource for satisfying regulatory criteria and establishing compliance with industry-specific security practices.
Furthermore, the testing organization will provide a Security Certificate, which will improve your capacity to express a safe environment, reinforce confidence, and satisfy the demands of many stakeholders in today’s evolving cybersecurity scene.
How Often Should You Pen Test?
A pen test isn’t a one-time event. Networks and computer systems are dynamic – they do not remain static for long. As time passes, new software is delivered and modifications are made, all of which must be tested or retested.
Businesses should conduct Penetration testing on a regular (at least once a year) basis to guarantee more consistent IT and network security management by disclosing newly found threats (0-days, 1-days) or growing vulnerabilities that malevolent hackers can exploit.
- In addition to the regular analysis and assessments need by rules such as GDPR, PCI-DSS tests should be performed anytime new network infrastructure or app deployment.
- Infrastructure or apps are upgraded or modified significantly.
- New office site updates.
- Installment of Patches for security.
End-user policies are altered. Don’t take Pen testing lightly; it has the ability to offer all businesses crucial security services. A pen test, on the other hand, is not one-size-fits-all. Understanding the company’s line of business is ultimately critical to successful security testing.
Difference Between Vulnerability Scans and Pen Tests
Vulnerability Scan:
The process of finding and analyzing vulnerabilities in your website, application, network, or devices is known as a vulnerability assessment or vulnerability scan. Furthermore, it accomplishes this with the assistance of an automated vulnerability scanner, which checks your systems for common vulnerabilities and exposures by referencing a vulnerability database.
Penetration Testing:
Penetration testing is the practice of simulating an attack on a system in order to identify and correct security flaws. It is often carried out by security specialists who use a variety of hacker-like approaches to locate ways into your system and study those ways to determine how much harm may be done through them.
Vulnerability Scan Vs Penetration Testing
Although the breadth of pen tests and vulnerability assessments appears to be comparable, there are some significant variances.
- In terms of Automation and Manual Testing
Vulnerability scanning is automated since it depends exclusively on security scanning technologies. The scan throws a broad net across the whole network.
In contrast, to uncover vulnerabilities, pen testing employs a combination of automated tools and human testing by expert penetration testers.
- In terms of Exploiting any Discovered Flaws
Vulnerability scanning seeks to identify flaws rather than attack them.
Pen testing exploits any vulnerabilities discovered in order to assess the security posture. Pen testing, which also depends on creative tactics and techniques to penetrate internal networks, may result in the discovery of a zero-day vulnerability.
- In terms of Preventive and Detective Controls
Vulnerability scanning is a detective control, which implies that detecting issues is the priority (and the aim).
In contrast, pen testing is a preventative control, which implies that the aim is to detect vulnerabilities and use the results to keep such vulnerabilities from being exploited.
- In terms of Required Financial Investment
Because vulnerability scanning often includes the use of tools, the cost is modest to moderate.
Pen testing is more expensive since firms typically hire an outside team to do the pen test and publish their findings.
What are the Types of Pen Testing?
Different companies have different infrastructure and assets. In addition to that, every business has its requirement for pen testing. Here are some common types that a penetration testing service provider helps businesses with:
- Web Application: Web application pen testing aids in identifying real-world assaults that may be successful in gaining access to these systems. It identifies weaknesses. Web application pen testing detects application flaws or weak infrastructure channels before an attacker does. It aids in the verification of security policies.
- Mobile Application: Mobile application penetration testing is the act of testing mobile apps to discover and uncover gaps or vulnerabilities before they are exploited for malicious gain, in order to assess the degree of the threat posed by them to the application. This can be done manually or automatically.
- Cloud: Cloud penetration testing is intended to examine a cloud system’s strengths and vulnerabilities in order to enhance its overall security posture. Cloud penetration testing aids in the identification of risks, weaknesses, and gaps. The consequences of vulnerable vulnerabilities. Determine how to make use of any access gained through exploitation.
- Network: Network penetration testing employs a variety of hacking techniques to uncover security flaws in your networks. These tests employ genuine methods and tactics that a hacker may use to get access to the system, providing crucial information regarding network security.
What are the Methods or Approaches of Pen Testing?
There are three approaches to performing penetration testing, namely, Black; White, and Gray box testing. Below, we’ve described them all:
- Black-box testing is done without the tester knowing anything about the program being evaluated. This is referred to as “zero-knowledge testing” at times. In addition, the major goal of this test is to allow the tester to act like a real attacker by investigating potential applications for publicly available and discoverable information.
- White-box testing is the polar opposite of black-box testing in that the tester has complete information about the software. Source code, documentation, and diagrams are examples of knowledge. Because of its openness, this technique enables significantly faster testing than black-box testing, and with the additional knowledge gathered, a tester may design far more comprehensive and detailed test cases.
- Gray-box testing encompasses any testing that falls between the two previously described types: some information is supplied to the tester (typically merely credentials), and other information is supposed to be uncovered. This sort of testing represents an intriguing balance in terms of the number of test cases, cost, speed, and breadth of testing. The most popular type of testing in the security business is gray-box testing.
How Does Pen Testing Help with Compliance?
Cybersecurity teams must often ensure that they are in compliance with requirements such as:
- HIPAA
- PCI DSS
- GDPR
- ISO 27001
Pen testing may reveal how an attacker could obtain access to sensitive data by attacking an organization’s infrastructure. As attack techniques develop, frequently required testing ensures that businesses keep one step ahead by detecting and correcting security flaws before they are exploited. Furthermore, for auditors, these tests can confirm that other needed security measures are in place and functioning effectively.
What are the Tools for Pen Testing?
Security testing in current, large-scale IT settings requires the use of pentesting tools. Furthermore, they facilitate asset detection in complex, hybrid contexts and can assist testers in evaluating systems against security benchmarks and compliance standards. Here are some of the major tools, pen testers use to identify vulnerabilities:
1. Netsparker
Everything from cross-site scripting to SQL injection may be detected by the program. This tool may be used by developers on websites, web services, and web apps. Furthermore, Netsparker automatically exploits weak points in a read-only manner. Evidence of exploitation is created. The consequences of vulnerability are immediately seen.
Advantages:
- Scan 1000+ web apps in less than a day!
- Add more team members to facilitate cooperation and quick sharing of findings.
- Automatic scanning guarantees that just a minimal amount of setup is required.
- Look for SQL and XSS vulnerabilities in web applications that can be exploited.
- Reports on regulatory compliance and legal web applications.
- The use of proof-based scanning technology ensures reliable detection.
2. Burp Suite
The free version includes all of the tools required for scanning operations. Furthermore, this program is great for testing web-based apps. There are tools available for mapping the tack surface and analyzing requests between a browser and destination servers. Web Penetration Testing on the Java platform is utilized by the framework and is an industry-standard tool used by the majority of information security experts.
Benefits:
- Capable of crawling web-based apps automatically.
- Windows, OS X, Linux, and Windows are all supported.
3. SQLMap
SQLMap is a database SQL injection takeover tool. MySQL, SQLite, Sybase, DB2, Access, MSSQL, and PostgreSQL are among the database systems supported. SQLMap is a free and open-source tool for attacking database servers and SQL injection vulnerabilities.
Benefits:
- Vulnerabilities are detected and mapped.
- Supports all injection methods: Union, Time, Stack, Error, and Boolean.
- Runs applications via the command line and is available for Linux, Mac OS, and Windows computers.
4. Metasploit
Metasploit assists professional teams in verifying and managing security assessments, raising awareness, and arming and empowering defenders to remain ahead of the game. In addition, this open-source program will allow a network administrator to break in and detect serious flaws.
Benefits:
- The GUI clickable interface and command line make it simple to use.
- Manual brute-forcing, payloads designed to escape leading solutions, spear phishing, and awareness, and an app for testing OWASP vulnerabilities, are all available.
- Test data for approximately 1,500 exploits is collected.
- Can investigate previous vulnerabilities in your infrastructure.
Why Should Businesses Choose a Penetration Testing Service Provider?
Exploitable vulnerabilities should be detected by organizations before attackers may discover and exploit them. During a cyber event, a business must not only fix the exploited vulnerability, but also identify modifications made by the attacker, rollback them, find the damage caused, and control the problem.
One thing to know before employing a pen testing business is that it hires “ethical hackers,” also known as “white-hat hackers,” who are designated team members. They infiltrate a service after taking substantial measures to uncover weaknesses and determine where the organization or system needs to enhance for more security.
While it is well known that it is an important step in securing one’s systems, selecting the appropriate firm may be a critical aspect in receiving the finest service for you. QualySec is a highly recognized penetration testing company, that takes pride in its deep penetration testing and reporting.
The services include:
- Web App Pen Testing
- Mobile App Pen Testing
- API Penetration Testing
- Network Penetration Testing
- Cloud Penetration Testing
- IoT Device Pen Testing
The penetration testing performed by our expert penetration testers will be for the whole application as well as its underlying infrastructure, including all network devices, management systems, and other components. Our thorough examination assists you in identifying security flaws so you can address them before a hacker can.
One of our primary assets is deep penetration testing skills, in which our specialists conduct extensive and sophisticated examinations to uncover weaknesses in a company’s digital infrastructure. Furthermore, these tests go beyond surface-level scans, digging deep into the system for flaws.
Important Characteristics:
- Over 3,000 tests are used to find and eliminate all forms of vulnerabilities.
- Capable of identifying business logic flaws and security holes.
- Manual pen testing ensures that there are no false positives.
- SOC2, HIPAA, ISO27001, and other applicable standards compliance scans.
- Security professionals are available for on-demand remedial support.
Furthermore, our unwavering dedication to accuracy distinguishes us with an astounding zero-false positive report record. After rigorous testing, we give clients a thorough and informative report, accurately finding flaws and potential exploits.
We go above and beyond by partnering with developers to help them through the bug-fixing process, ensuring that reported vulnerabilities are resolved as soon as possible. Businesses obtain a security certificate at project completion as a final stamp of security, establishing trust in our cybersecurity procedures and boosting their defenses against prospective threats.
Latest Penetration Testing Report

Conclusion
This article provided a thorough description of what Pen Testing is, its many types, phases, and methods, as well as the cyber security penetration testing methodologies involved. Finally, this is how hackers would execute the assault, and the defensive side will strive to safeguard the businesses and prepare before hackers by running pen tests and exploiting them wherever feasible to determine the damage.
Get professional help and deep penetration testing with QualySec Technologies today! Fill the form to take step forward to securing your company and assets.
FAQ
Q. What is the basic principle of penetration testing?
Penetration testing examines your current cybersecurity procedure in order to identify holes that attackers may exploit. Pen tests provide insight into how attackers may attempt to infiltrate your networks, allowing you to plug vulnerabilities and stay one step ahead.
Q. Who performs penetration testing?
Pen testing is often carried out by testers referred to as ethical hackers. These ethical hackers are IT professionals who employ hacking techniques to assist businesses in identifying potential entry points into their infrastructure.
Q. What is the importance of penetration?
Penetration testing aids in assessing an organization’s systems, applications, and networks’ security. It is used to detect security flaws before thieves do. Penetration testers mimic assaults in order to uncover security flaws.
Q. What is the ultimate objective of a penetration test?
A penetration test’s primary goal is to detect security flaws in a network, system, or piece of software. Once that establishes, the vulnerabilities may be eliminate or minimize before hostile parties find and exploit them.
Q. What are the 5 stages of penetration testing?
The stages of penetration testing include gathering information, planning, scanning and penetration testing, reporting, and remediation and retesting. These are the major steps of penetration testing.
Q. What are the different types of penetration testing?
The types of penetration testing include network penetration testing, web application pen testing, mobile app pen testing, cloud app penetration testing, IoT device pen testing, API penetration testing, and many more. This depends on which digital platform or technology a business uses and needs it secure from cybersecurity.
Q. Which company provides the best penetration testing in India?
Among the list of thousands, QualySec Technologies, TCS, Wipro, and IBM are the top-ranking companies for providing top-notch penetration testing services.




























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments