Mobile Application Penetration Testing: Ensuring Mobile App Security
Mobile Application Penetration Testing is a critical process in the realm of mobile application security. It involves a comprehensive evaluation of a mobile application’s security posture by simulating attacks that mimic the actions of malicious actors. The overarching goal of this testing is to systematically identify vulnerabilities and weaknesses in the security controls of the mobile app, ultimately providing insights and recommendations for remediation.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Why is Mobile Application Penetration Testing Necessary?
Mobile applications have witnessed explosive growth in recent years and have become an integral part of our daily lives. However, this ubiquity has also made them a prime target for cybercriminals seeking to exploit weaknesses in their security. This is why Mobile Application Penetration Testing holds such significance.
Securing Sensitive User Data
One of the primary drivers behind the need for robust security measures in mobile apps is the sensitive user data they often handle. Personal information, financial data, login credentials, and more are routinely entrusted to these applications. Consequently, a security breach within a mobile app can have devastating consequences, ranging from financial losses and reputational damage to legal liabilities.
Uncovering Vulnerabilities
During the Mobile Application Penetration Testing process, a team of skilled ethical hackers, often referred to as “white-hat” hackers, endeavors to replicate the tactics employed by cybercriminals. They systematically probe the mobile app for vulnerabilities that could potentially be exploited. These vulnerabilities may include weak authentication mechanisms, data storage flaws, and improper handling of user inputs.
Evaluating Security Controls
The evaluation goes beyond a surface-level analysis. It delves deep into the security controls that are in place to protect the application and its data. This includes scrutinizing encryption methods, access controls, and network communication protocols to ensure that they are robust and capable of withstanding sophisticated attacks.
Recommendations for Remediation
Once vulnerabilities are identified and analyzed, the Mobile Application Penetration Testing team generates a comprehensive report that outlines their findings. This report serves as a roadmap for developers and stakeholders to prioritize and address the identified security issues. Remediation actions may involve code fixes, configuration changes, or even a redesign of certain security features.
Staying Ahead of Evolving Threats
In the constantly evolving landscape of cybersecurity, mobile apps must adapt to new threats and attack vectors. Regular Mobile Application Penetration Testing helps organizations stay ahead of these threats by proactively identifying and mitigating vulnerabilities before they can be exploited.
Mobile Application Penetration Testing plays a pivotal role in securing the digital ecosystem by fortifying mobile apps against potential threats. As mobile technology continues to advance, and with it, the sophistication of cyberattacks, this practice remains indispensable in safeguarding sensitive user data and ensuring the overall trustworthiness of mobile applications.
Diverse Approaches to Mobile Application Penetration Testing
Mobile Application Penetration Testing encompasses a range of approaches, each tailored to specific testing requirements. These methodologies provide distinct insights into an app’s security posture and vulnerabilities. The three primary types of Mobile Application Penetration Testing are:
1. Black Box Testing
Exploring the Application from an External Perspective
Black Box Testing is a penetration testing method where the tester operates with no prior knowledge of the mobile application’s internal workings. This approach simulates how a potential attacker, devoid of any insider information, would interact with the application. Testers navigate the app as an end-user would, scrutinizing its functionalities, inputs, and outputs.
The primary objective of Black Box Testing is to identify vulnerabilities and weaknesses in the application’s security controls from an external standpoint. Testers often focus on common attack vectors, such as injection attacks, authentication bypass, and data leakage. This methodology provides a valuable perspective on how the app may be vulnerable to attacks initiated by malicious external actors.
2. White Box Testing
A Deep Dive into the Application’s Inner Workings
In White Box Testing, testers possess comprehensive knowledge of the mobile application’s internal architecture, source code, and underlying technologies. Armed with this insider perspective, testers scrutinize the application’s security controls, code quality, and implementation details.
White Box Testing aims to uncover vulnerabilities by conducting an in-depth analysis of the application’s codebase. Testers assess the adherence to secure coding practices, review the effectiveness of security mechanisms, and identify potential flaws in the implementation. This approach provides a holistic understanding of the app’s security posture from the inside out, allowing for precise identification of vulnerabilities that may not be apparent through external testing alone.
3. Gray Box Testing
Combining Insights from Both Worlds
Gray Box Testing strikes a balance between the external focus of Black Box Testing and the internal scrutiny of White Box Testing. Testers possess partial knowledge of the application’s inner workings, which may include limited access to the source code or architectural details.
By leveraging their partial insider knowledge, Gray Box Testers employ a hybrid approach to identify vulnerabilities. They interact with the mobile app from an end-user perspective, akin to Black Box Testing, while also conducting targeted internal assessments, reminiscent of White Box Testing. This dual approach can offer a nuanced view of security weaknesses, especially when some level of internal understanding is necessary to uncover certain vulnerabilities.
Tailoring the Approach to Specific Needs
Selecting the most appropriate type of Mobile Application Penetration Testing depends on the objectives, constraints, and context of the testing process. Organizations often choose one or a combination of these methodologies to gain a comprehensive understanding of their mobile app’s security posture and effectively mitigate potential risks. Whether it’s a Black Box, White Box, or Gray Box approach, the overarching goal remains consistent: to identify vulnerabilities, strengthen security, and safeguard sensitive user data in an increasingly interconnected and mobile-dependent world.
A Comparison
Certainly, here’s a table comparing the three types of Mobile Application Penetration Testing: Black Box Testing, White Box Testing, and Gray Box Testing, along with some additional information.
| Penetration Testing Type | Knowledge of Internal Workings | Testing Approach | Advantages | Disadvantages |
|---|---|---|---|---|
| Black Box Testing | No prior knowledge | External perspective | – Simulates real-world attacks. – Identifies external vulnerabilities. – Assesses user experience. – Suitable for black-hat perspective. |
– Limited insight into internal issues. – May not identify all vulnerabilities. – Less precise results. |
| White Box Testing | Full knowledge | Internal analysis | – In-depth examination of code. – Identifies coding flaws and architecture issues. – Precise vulnerability detection. – Comprehensive coverage. |
– Requires access to source code. – May not replicate real-world attack scenarios. – Time-consuming and resource-intensive. |
| Gray Box Testing | Partial knowledge | Hybrid approach | – Combines external and internal perspectives. – Balances real-world simulation with deep analysis. – Provides nuanced insights. – Flexible and adaptable. |
– Requires some level of internal knowledge. – May not provide the depth of analysis of White Box Testing. – Complexity in balancing approaches. |
Qualysec: The Best Service Provider
Qualysec is a cybersecurity company founded in 2020 that has quickly become one of the most trusted names in the industry in Los Angeles. The company provides services such as VAPT, security consulting, and incident response.
Although Qualysec’s Oppressional office is not situated in Los Angeles, Qualysec’s extensive knowledge and expertise in cybersecurity testing services have earned a reputation among the best Mobile Application Penetration Testing Service Provider.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The Qualysec team is made up of seasoned offensive specialists and security researchers who collaborate to give their clients access to the most recent security procedures and approaches. They provide VAPT services using both human and automated equipment.
In-house tools, adherence to industry standards, clear and simple findings with reproduction and mitigation procedures, and post-assessment consulting are all features of Qualysec’s offerings.
The solution offered by Qualysec is particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by doing routine penetration testing, businesses may see weaknesses and fix them before thieves attack them.
As a result, Qualysec is rated as the best of the best Mobile Application Penetration Testing Service Providers.
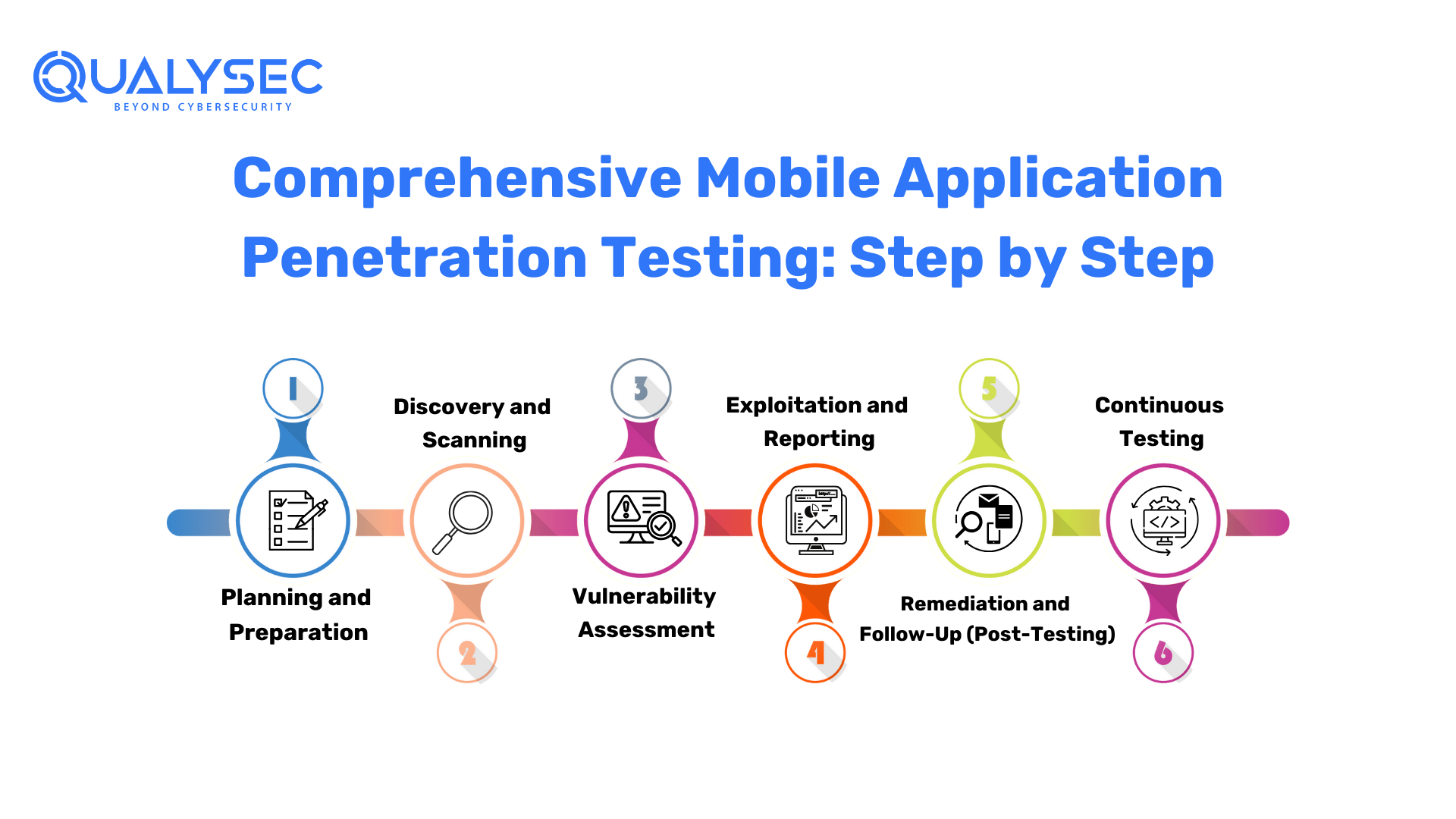
Comprehensive Mobile Application Penetration Testing: Step by Step
Mobile Application Penetration Testing is a structured process that aims to uncover vulnerabilities and enhance the security of mobile applications. Here are the key steps involved in this meticulous process:
1. Planning and Preparation
The initial phase sets the foundation for a successful Mobile Application Penetration Test:
- Scope Identification: Define the scope of the testing, outlining the specific areas and functionalities of the mobile app that will be assessed. This includes identifying the platforms (iOS, Android, etc.) and versions to be tested.
- Testing Objectives: Establish clear testing objectives and goals. What are you trying to achieve through this test? What vulnerabilities are you most concerned about?
- Testing Plan: Develop a detailed testing plan that outlines the methodologies, tools, and techniques to be used during the assessment. This plan should also include timelines and resource allocation.
2. Discovery and Scanning
In this phase, automated tools are employed to scan the mobile application for potential vulnerabilities:
- Automated Scanning: Utilize automated testing tools to conduct a preliminary scan of the mobile app. These tools search for common vulnerabilities such as input validation errors, misconfigurations, and known security issues.
- Data Gathering: Collect information about the app, including its architecture, communication protocols, and dependencies.
3. Vulnerability Assessment
This step involves a more detailed examination of vulnerabilities identified in the previous phase, including manual verification:
- Manual Testing: Ethical hackers, or penetration testers, manually inspect the application to validate and assess the vulnerabilities found during automated scanning. This often includes analyzing the app’s user interfaces, server interactions, and data storage mechanisms.
- Severity Assessment: Evaluate the severity of each identified vulnerability. Prioritize them based on their potential impact and exploitability. Some vulnerabilities may have a higher risk associated with them, and these should be addressed urgently.
4. Exploitation and Reporting
In this final phase, testers simulate real-world attacks to determine the practical impact of vulnerabilities and provide a comprehensive report of their findings:
- Exploitation: Ethical hackers attempt to exploit the vulnerabilities in controlled environments to understand the extent of potential harm. This phase helps determine the real-world impact of these weaknesses.
- Reporting: After successful exploitation or verification, testers create a detailed report. This report should include a description of each vulnerability, its impact, steps to reproduce it, and recommendations for mitigation. It is crucial to provide clear and actionable insights for developers and stakeholders.
5. Remediation and Follow-Up (Post-Testing)
Once vulnerabilities are identified, the development team works to remediate them based on the recommendations in the report. After the fixes are implemented, the application may undergo a retest to verify that the vulnerabilities have been effectively addressed.
6. Continuous Testing
In an ever-evolving threat landscape, it’s essential to regularly perform Mobile Application Penetration Testing to stay ahead of emerging security risks. Continuous testing helps ensure that the mobile app remains secure as new features are added, technologies evolve, and threats change.
By following these steps, organizations can systematically assess and enhance the security of their mobile applications, mitigating potential risks and safeguarding user data.
Benefits of Mobile Application Penetration Testing
Mobile Application Penetration Testing offers a wide range of advantages that are essential for fortifying the security of mobile applications. One significant benefit is its ability to detect vulnerabilities early in the development process. By identifying security weaknesses before an application goes live, organizations can proactively address these issues, preventing potential threats and vulnerabilities from reaching production environments.
Firstly, it serves as an early warning system by identifying vulnerabilities in the development phase, enabling proactive mitigation, and preventing potential threats from reaching production environments. This proactive approach not only saves time and resources but also reduces the risk of costly security incidents.
Secondly, Mobile Application Penetration Testing is instrumental in safeguarding user data and privacy. By pinpointing vulnerabilities that could lead to data breaches, organizations can ensure that sensitive user information remains secure. This not only fosters user trust but also helps adhere to stringent data protection regulations such as GDPR and HIPAA.
Furthermore, this testing process contributes to legal and regulatory compliance. Many industries must comply with data security and privacy regulations. Mobile Application Penetration Testing assists organizations in meeting these requirements, ensuring the security of user data and avoiding potential legal repercussions.
Moreover, the practice of regular testing and maintenance is crucial. As mobile apps evolve and security threats continually emerge, ongoing Mobile Application Penetration Testing helps organizations stay ahead of new vulnerabilities. This proactive approach ensures that mobile applications remain secure and up-to-date with the latest security standards.
In addition to these core benefits, Mobile Application Penetration Testing enhances user trust by demonstrating a commitment to security. It can be a competitive differentiator, attracting security-conscious users and solidifying an organization’s reputation.
Overall, Mobile Application Penetration Testing is a proactive strategy that goes beyond identifying vulnerabilities. It is a vital practice that fortifies mobile app security, mitigates risks, and ensures compliance with regulations, all contributing to the success of mobile applications in an increasingly security-conscious digital landscape.
A Vital Role of Mobile Application Penetration Testing
Mobile Application Penetration Testing also plays a pivotal role in protecting user data and privacy. By identifying vulnerabilities that could lead to data breaches, organizations can ensure that sensitive user information remains secure. This not only safeguards user trust but also helps organizations comply with stringent data protection regulations.
Speaking of compliance, Mobile Application Penetration Testing is instrumental in helping organizations meet regulatory requirements. Many industries are subject to strict data protection and privacy regulations, such as GDPR, HIPAA, and PCI-DSS. By conducting penetration testing, organizations can demonstrate their commitment to securing user data and staying in compliance with these regulations.
Moreover, Mobile Application Penetration Testing can lead to cost savings. Addressing security vulnerabilities post-release can be significantly more expensive than identifying and resolving them during the development phase. By investing in security early on, organizations can reduce the financial burden associated with addressing security issues after a mobile app’s launch.
Today’s Competitive Mobile Application Penetration testing Landscape
In today’s competitive landscape, security can be a valuable differentiator. Organizations that prioritize security through Mobile Application Penetration Testing not only enhance their reputation but may also gain a competitive advantage. Security-conscious users are more likely to trust and engage with applications that have undergone rigorous security testing.
Finally, Mobile Application Penetration Testing is a dynamic process that adapts to emerging threats. As cybersecurity threats continually evolve, penetration testing helps organizations stay ahead by identifying and addressing vulnerabilities and attack vectors specific to the ever-changing threat landscape. This adaptive approach ensures that mobile applications remain secure and resilient over time.
Latest Penetration Testing Report

Conclusion
In conclusion, Mobile Application Penetration Testing stands as a critical process in the realm of mobile app security. Its significance lies in its ability to systematically identify vulnerabilities and weaknesses within an application’s security controls, thereby enabling organizations to take proactive steps in mitigating risks and fortifying their defenses.
By adhering to best practices, including selecting the appropriate testing methodology, engaging experienced penetration testers, and conducting regular testing and maintenance, organizations can ensure the effectiveness of their Mobile Application Penetration Testing efforts. This proactive approach not only helps protect sensitive user data and privacy but also aids in complying with regulatory requirements. In an era marked by increasing cyber threats, taking action now to safeguard your mobile app through thorough penetration testing is not just a best practice—it’s a necessity to enhance its security and bolster the trust of its users.
Qualysec has a successful track record of serving clients and providing cybersecurity services across a range of industries such as IT. Their expertise has helped clients identify and mitigate vulnerabilities, prevent data breaches, and improve their overall security posture.
When it comes to comprehensive cybersecurity audits, Qualysec is the organization to go with. Their cost of VAPT guide helps clients make informed decisions by understanding the various factors that affect the cost by clicking here.
FAQ’s
1. What Is Mobile Application Penetration Testing?
Mobile Application Penetration Testing is a comprehensive security assessment process that involves identifying vulnerabilities and weaknesses in mobile applications. It simulates real-world attacks to evaluate the application’s security controls, helping organizations uncover potential security risks and take corrective actions to enhance the app’s security.
2. Mobile Application Security Testing Framework?
A Mobile Application Security Testing Framework is a structured approach or set of tools and methodologies used to assess the security of mobile applications. These frameworks provide a systematic way to conduct Mobile Application Penetration Testing and ensure thorough coverage of security aspects.
3. Mobile Application Security Testing Checklist?
A Mobile Application Security Testing Checklist is a detailed document that outlines the steps and criteria for conducting security assessments on mobile applications. It serves as a guide to ensure that all relevant security aspects are examined during the testing process, helping testers and organizations maintain a comprehensive approach to security testing.
4. Mobile Application Penetration Testing Guide?
A Mobile Application Penetration Testing Guide is a comprehensive resource or document that provides guidance and instructions on how to conduct Mobile Application Penetration Testing effectively. It typically includes information on testing methodologies, tools, best practices, and steps to follow during the testing process.
5. Mobile Application Penetration Testing PDF?
A Mobile Application Penetration Testing PDF refers to a document, often in PDF format, that contains information, guidelines, or instructions related to Mobile Application Penetration Testing. These PDF documents can be valuable resources for testers and organizations looking to enhance the security of their mobile applications.
6. Mobile Application Penetration Testing Burp Suite?
Burp Suite is a popular web vulnerability scanner and security testing tool that is commonly used for web application penetration testing. While it primarily focuses on web applications, it can also be used in conjunction with other tools and methodologies for testing the security of mobile applications, especially when they interact with web services or APIs. Burp Suite helps identify vulnerabilities such as injection attacks, authentication issues, and more.





























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments