To reduce an application’s security concerns, developers must ensure their applications can withstand rigorous security testing. Fortunately, technologies exist to ease and even automate these security tests. Best practices can also be used to guide and educate the testing process. This post will discuss the most frequent mobile app security testing and highlight popular vulnerabilities. We’ll also go about recommended practices for app security testing and tools for safeguarding mobile apps in a CI/CD pipeline.
Extensive penetration testing can prevent or minimize mobile app security errors (or breaches). As a result, app developers and businesses are using penetration testing to examine the IT infrastructure, database security, mobile applications, and other parts of the mobile app.
Mobile app security best practices consider itself an essential component of the entire app security strategy. If you do not have in-house experience in mobile app pen testing, we suggest that you work with a reputable penetration testing firm. In this article, we’ll go over the fundamentals of developing an effective mobile app pen testing approach.
What is Mobile App Security Testing?
Protecting valuable mobile applications and your online identity from fraudulent attacks is mobile app security. This covers key loggers, malware, tampering, reverse engineering, and other types of interference or manipulation. A complete mobile app security strategy includes best practices for use and corporate procedures, along with technological solutions like mobile app shielding.
Mobile app security has rapidly gained significance since mobile devices have become more commonplace in many nations and areas. An increase in mobile devices, apps, and users correlates with the trend toward more usage of mobile devices for banking services, shopping, and other activities. The good news is that banks are strengthening their security regarding customers using mobile devices for financial services with Android application penetration testing and iOS application penetration testing .
What are the Common Vulnerabilities in Mobile App Security Testing?
Mobile app security is critical because of the growing amount of sensitive data that mobile devices contain and our growing reliance on them. Organizations and users may safeguard their mobile apps proactively by being aware of prevalent threats and vulnerabilities.
The following are some Common Mobile App Security Threats:
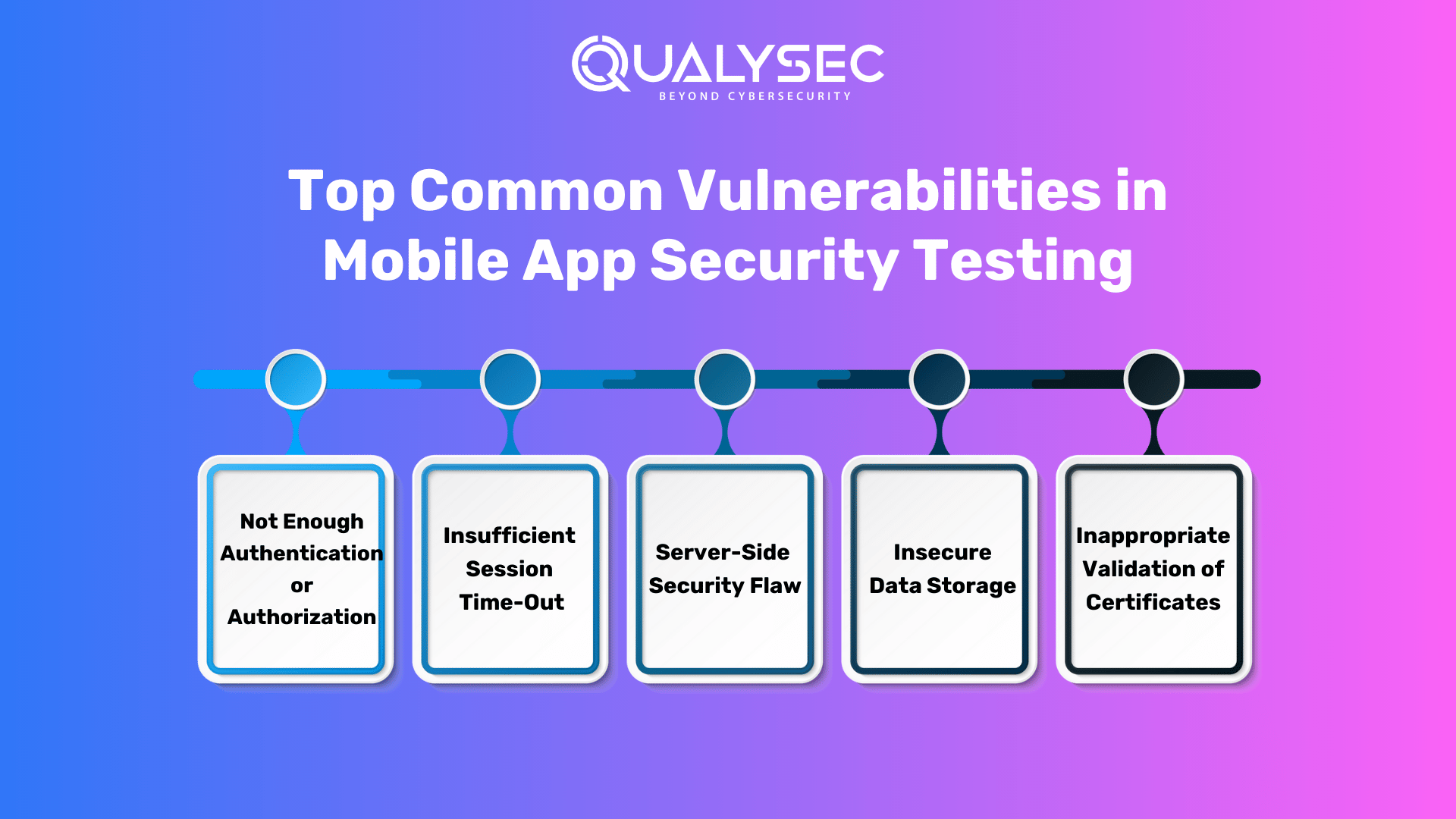
1. Not Enough Authentication or Authorization
Insufficient authorization occurs when an application does not carry out sufficient authorization checks to confirm that the user is carrying out a task or accessing data in compliance with the security policy. Authorization processes should keep an eye on what a user, service, or application is permitted to do.
Your efforts can be more at ease if you choose a tried-and-true authorization application that prioritizes policy-based configuration files over thorough authentication/authorization assessments.
2. Insufficient Session Time-Out
The identifiers get invalidate when a user logs out of the program. Even in such cases, other users may interrupt and act on behalf of the users if the server is unable to invalidate the session identifiers. You must ensure the program has a logout button and wait for the correct log-out until the session is correctly invalidated. The main point is that you should download apps with common sense.
3. Server-Side Security Flaw
Unauthenticated access may be avoided on the server side; nevertheless, input validation checks and limits must be integrated into the app architecture to lessen the strain on the server. The application should confirm the input data during the server processing phase and stop anomalous behavior. As you are aware, one can block some types of data from the app side and allowlist the required ones. Encryption should be used by both the app and the server when receiving and sending data.
4. Insecure Data Storage
Insecure storage of sensitive data on the device may lead to vulnerability. People must always remember that sensitive data saved on devices can potentially be stolen and that data stored on devices isn’t protected from theft. Furthermore, to prevent this problem, apps should save sensitive data in keychain pairs. The data must be encrypted if the app stores information in the form of data.
5. Inappropriate Validation of Certificates
The app may need to accurately verify the state, validate the SSL/TLS certificates, or refuse to. If the certificate cannot be confirmed, the client might choose to terminate the connection. If the data is not adequately verified, it may be utilized for illegal access. Furthermore, to cross-check whether a certificate is from a reliable source and whether it should come from a respectable certificate authority, you must make sure that the certificate validation in your application is completed correctly. For the best validation, you ought to be putting some recent standard forums into practice.
If your business is facing these vulnerabilities and you’re worried about your business infrastructure, don’t be. Qualysec’s expert security consultants are here to help! Schedule a call with them for FREE today!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
What Impact Can These Vulnerabilities Have on Your Business?
App security issues have both short-term and long-term effects. Immediate financial consequences and lost business may arise from the ensuing reputational harm. For this reason, a crucial element of mobile device management is application security.
Long-term effects can sometimes have greater significance than immediate ones. There are multiple ways an attacker can exploit security flaws in your app. For instance, they can carry out data theft and man-in-the-middle (MITM) attacks or use ports for unauthorized communication.
Statistics on Mobile App Hacking
The numbers around mobile app hacking are alarming. These are a handful:
- Over 12 million users’ login details were made public by the Slack mobile app hack.
- In the end, thirteen distinct Android apps exposed data belonging to as many as 100 million users.
- Up to 21 million users of the parking application were affected by the hack.
- A breach compromised the personal information of 650,000 users on the COVID-19 passport app.
Identifying Vulnerabilities in Mobile Apps: Key Penetration Testing Techniques
As the name implies, mobile app penetration testing simulates a real-world attack on the app to uncover security flaws. The mobile app pentesting strategy aims to detect flaws on the front and back end (or databases), binary compile concerns, and sensitive data storage.
Consider the severity of the harm in circumstances when sensitive data (e.g., username, password, etc.) is stored in the backend as normal strings. Hackers could also sell this sensitive information on the dark web. In the grand scheme of things, such a situation can be averted by making mobile app security testing a regular component.
Furthermore, pen testers expect to have in-depth knowledge of mobile app environments to design test scenarios that aid in the identification of security flaws in the app. A scalable mobile app penetration testing technique combines both human and automated testing.
Also Read: A Deep Dive into Mobile Application Penetration Testing
Why Conduct Mobile App Security Testing ?
Mobile app security is important to developers but has yet to be commonly understood. Aside from the increasing prevalence of mobile fraud, there are various reasons why businesses should prioritize mobile app security and commit to building a complete plan.
Consumers must be cautious about the information they disclose and the data they download when using the internet, but business professionals must also be cautious. Mobile devices are almost constantly on and close by, storing massive amounts of personal information, sensitive data, and documents. As a result, they might be a gold mine for attackers.
An assault on your app might be disastrous for your company. Security testing is critical to the development lifecycle for the following reasons:
- Makes your app conform to industry requirements.
- Gives your customers confidence in your offerings (for example, when your app is ISO 27001 certified).
- Aids in detecting and understanding flaws, allowing you to remove and prepare for dangers such as security breaches.
- Reduces the financial and reputational consequences associated with security events.
- Assists you in determining which components of your app’s application to modify: third-party code, your code, or your security personnel.
Also check: Key reasons why mobile app security testing is important for businesses
What is the Process of Mobile App Security Penetration Testing?
- Information Gathering & Planning: This stage gathers all the information about the application and plans a checklist for conducting the pentest.
- Auto Tool Scanning: Here, the plan is executed with the help of automated tools to find surface-level vulnerabilities. In this stage, you may find false positives.
- Manual Testing: This stage is critical in pentesting. The pentesters perform security tests manually by going deep into the app to find and mitigate vulnerabilities. Here, you’ll get zero false positives.
- Reporting: The pentesters now create a detailed and developer-friendly report that provides insights into all the vulnerabilities found, their severity, and reference on how to mitigate it
Check out our detailed and comprehensive report to learn how it looks and what perks you’ll get from the pen test report.
Latest Penetration Testing Report

- Remediation: This is the stage where the developer works on fixing the vulnerabilities. The testing team will help the dev team if they need help through a consultation call.
- Retesting: This phase is to test the application after the remediation so that testers find no further vulnerabilities, and the app is secure.
- LOA and Certification: This certificate of proof is provided by the testing company to ensure the application is secure for everyone’s use.
Read more: The Step-By-Step Guide to Penetration Testing
7 Best Practices for Performing Mobile App Security Testing
Now that we’ve covered the fundamentals of mobile application penetration testing let me go over the mobile app security best practices.
1. Create a Thorough Pentesting Strategy
Before you can begin executing penetration tests on the mobile application, you must first create a strategy that includes the following:
- Pentesting application
- Scenarios for testing
- Testing scenario prioritization
- Perspectives on Mobile App Applications
Some Android application penetration testing approaches in a mobile environment may be easily copied in other contexts. The techniques provided in the OWASP cheat sheet are a solid place to start when developing a strong mobile app pen testing strategy.
2. Use of SAST, DAST, and IAST Methods
Static application security testing (SAST), dynamic application security testing (DAST), and interactive application security testing (IAST) methodologies are used in the mobile application security testing process to give full coverage and insight into possible vulnerabilities.
SAST analyzes its source code or binary files without executing the application to uncover security flaws. DAST entails monitoring the app’s behavior during runtime to detect vulnerabilities that may not be visible during static analysis. IAST combines elements of SAST and DAST, delivering real-time feedback on potential security problems while also inspecting the code. When these strategies are used in combination, a wide range of vulnerabilities may be identified and remedied, resulting in a more secure mobile app.
3. Improve Authentication Mechanisms
Put in place robust user authentication procedures. A combination of username, password, and secondary verification, such as OTPs or biometric identification, can improve the security of your app. Implement multi-factor authentication (MFA), for example, which compels users to confirm their identity using two or more separate credentials.
4. Enforcing Security Policies Consistently
Securing mobile apps aids in the prevention of a variety of dangers that typically impact mobile applications. Policy enforcers for mobile application management verify that policies such as authentication, encryption, data loss protection, and access restrictions are in place. This contributes to the security of mobile applications and devices against a variety of security risks like malware assaults, data leakage, insecure authentication, rooting or jailbreaking, and unsecured APIs and third-party components.
5. Perform Multiple Layers of File Analysis
The OAuth protocol, along with other third-party APIs, is used by the majority of apps. You must guarantee that sensitive data is not kept on third-party servers as part of mobile application penetration testing. When performing binary and file-level analysis, it is necessary to perform frequent checks for buffer overflows and to evaluate the possibility of SQL-based injection attacks.
6. Testing for encryption
Strong Mobile App Security Penetration Testing Methods make it difficult for attackers to access an app and obtain important information. It should be noted that more than simply enabling encryption on authorization is required. As developers, we may need to remember to put it in our apps’ layers, which may contain sensitive information. Furthermore, consider the OSI model’s transport layer. Attackers may utilize the transport layer to eavesdrop and leak communication information and other activities. Furthermore, to verify that your application adheres to standard encryption practices, utilize SAST to confirm that robust encryption techniques are in place.
7. Implement Access Controls
Limit what each user may view or do within your app by using access controls. As one of the best mobile application penetration testing practices, this technique can prevent unwanted users from accessing important information. Use role-based access control (RBAC), for example, to configure permissions based on responsibilities within your business.
How Can Qualysec Help in Securing Your Mobile Application?
As digital technology and connected devices become more common, so does the need for robust monitoring and security applications. Organizations can reach QualySec to scan their devices, applications, and networks for inherent and new threats or vulnerabilities.
In addition, we provide specific security solutions via process-based mobile app security testing assessment. A process that employs a Hybrid testing strategy and a professional team with extensive testing expertise to ensure that the app meets the industry’s highest standards.
In addition, our pen testing services include a full range of automated vulnerability scanning and manual testing using in-house and commercial tools like Burp Suite and Metasploit. We actively assist firms in successfully negotiating difficult regulatory compliance settings such as GDPR, SOC2, ISO 27001, and HIPAA.
We assist developers in resolving vulnerabilities by delivering comprehensive and developer-friendly pentesting findings. Furthermore, this report includes all of the insights. Beginning with the location of the discovered vulnerabilities and ending with a reference on how to resolve them, i.e., you get a detailed step-by-step report on how to resolve a vulnerability.
We’ve successfully protected 250+ apps and served 20+ countries through a network of 100+ partners, and we’re proud to boast a zero-data-breach record. Contact QualySec right away for unrivaled digital security for your application and business.
Conclusion
Mobile App Security Testing is essential in today’s world since it assures that the application is safe from the standpoint of the end user. In this article, we discussed the ideal methods for mobile app pentesting.
Many mobile app developers and businesses choose to work with a company like Qualysec, a pioneer in providing process-based mobile application penetration testing services. Rather than developing an in-house team from the ground up, we advise that an experienced partner be brought on board to execute a mobile app pentesting plan at a faster speed.
- Combines manual & automated testing for accurate results
- Runs 200+ industry-standard test cases
- Zero false positives – all findings are manually verified
- CI/CD integration for smooth DevSecOps workflows
- Get a real-time dashboard to track and manage vulnerabilities
- Receive developer-friendly reports with clear remediation steps
- Share publicly verifiable pentest certificates
- Supports compliance with SOC2, ISO27001, PCI-DSS, HIPAA, and more
- Trusted by startups to enterprises in Fintech, SaaS, Healthcare, and beyond

FAQs
Q. What is penetration testing in mobile applications?
Mobile application penetration testing is the act of testing mobile apps to discover and uncover gaps or vulnerabilities. It’s done before they are exploited for malicious gain to assess the degree of the threat posed by them to the application. This can be done manually or automatically.
Q. What are mobile application testing types?
The three categories of mobile app testing are Black box, white box, and gray box testing. Every test has its own set of rules and testing environment.
Q. Does OWASP apply to mobile apps?
The OWASP Mobile Application Security Verification Standard (MASVS) is the industry standard for mobile app security. Furthermore, Mobile software architects and developers may use it to create safe mobile apps and security testers to guarantee test findings are full and consistent.
Q. What are the common security threats in mobile applications?
Spam, phishing, malicious applications, and ransomware are just a few of the risks that mobile device users face today. These attacks and strategies are becoming more complex each year.






























































































































































































































































































































































































































































































































0 Comments