In the world of cybersecurity, penetration testing plays a vital role in identifying vulnerabilities and assessing the overall security posture of a system or network. Two popular approaches to penetration testing are manual and automated testing. Both methods have their advantages and disadvantages when it comes to factors such as accuracy, flexibility, time efficiency, and coverage. In this blog, we will delve into the pros and cons of each approach to help you understand their strengths and weaknesses
What is Penetration Testing?
Penetration testing, often referred to as pen testing, is a proactive security assessment methodology that simulates real-world attacks to identify vulnerabilities in a system, network, or application. The objective is to uncover weaknesses before malicious actors exploit them, allowing organizations to strengthen their defenses and mitigate potential risks.
What is Manual Penetration Testing?
Manual penetration testing involves human intervention and is often conducted by skilled ethical hackers. Testers use their expertise, creativity, and critical thinking to identify vulnerabilities. They analyze the target system within its broader context, considering factors such as business logic, user behavior, and real-world scenarios.
Manual Penetration Testing
Manual penetration testing involves human intervention and is often conducted by skilled ethical hackers. Here are some advantages and disadvantages of manual penetration testing:
Advantages
- Accuracy: Manual testing allows testers to apply critical thinking, intuition, and creativity to uncover complex vulnerabilities that automated tools might miss. Human testers can adapt to changing conditions and adjust their approach accordingly.
- Flexibility: Manual testers can explore the system or network thoroughly, trying different attack vectors and techniques based on their expertise and intuition. They can prioritize areas that are more likely to be exploited, based on an understanding of the target environment.
- Contextual Analysis: Manual testers can analyze the target system within its broader context, considering business logic, user behavior, and real-world scenarios. This perspective helps identify potential security gaps that automated tools may overlook.
Disadvantages
- Time-Consuming: Manual penetration testing can be time-consuming, especially for complex systems or networks. Testers need to go through various steps, including reconnaissance, vulnerability identification, exploitation, and reporting, which may require significant effort and resources.
- Skill and Expertise Dependence: Manual testing heavily relies on the skill and expertise of the tester. Not all testers possess the same level of knowledge and experience, which can lead to variations in the quality and effectiveness of the tests.
- Limited Coverage: Due to time constraints and resource limitations, manual penetration testing may not cover the entire system or network comprehensively. Certain areas or vulnerabilities may be overlooked, leading to potential security gaps.
What is Automated Penetration Testing?
Automated penetration testing involves the use of specialized tools and software to simulate attacks and identify vulnerabilities. These tools follow predefined scripts and procedures to scan systems and networks rapidly. They are efficient in identifying common vulnerabilities and provide a high-level overview of potential risks.
Automated Penetration Testing
Automated penetration testing involves the use of specialized tools and software to simulate attacks and identify vulnerabilities. Let’s explore the advantages and disadvantages of this approach:
Advantages:
- Time Efficiency: Automated testing can rapidly scan large systems or networks, performing repetitive tasks more quickly than manual testing. It can efficiently identify common vulnerabilities and provide a high-level overview of potential risks.
- Consistency: Automated tools follow predefined scripts and procedures consistently, reducing the likelihood of human error. This ensures that tests are reproducible and can be easily repeated.
- Broad Coverage: Automated tools can scan a wide range of systems and networks, making it possible to assess the security of a large-scale infrastructure. They can quickly identify common vulnerabilities, saving time and effort for manual testers.
Disadvantages:
- Limited Contextual Analysis: Automated tools lack the ability to understand the broader context of the target system. They may not consider business logic, user behavior, or specific scenarios, potentially missing more sophisticated vulnerabilities.
- False Positives and Negatives: Automated tools may generate false positives or false negatives, leading to inaccuracies in vulnerability identification. This can result in wasted time and resources as testers sift through large amounts of data.
- Lack of Creativity: Automated testing relies on predefined scripts and known attack vectors. It may struggle to identify new or zero-day vulnerabilities that have not been previously documented or included in the tool’s database.
Table: Manual Penetration Testing vs. Automated Penetration Testing
| Factors | Manual Penetration Testing | Automated Penetration Testing |
|---|---|---|
| Accuracy | High | Moderate |
| Flexibility | High | Low |
| Time Efficiency | Low | High |
| Coverage | Moderate | High |
| Contextual Analysis | Yes | No |
| Skill and Expertise | Critical | Moderate |
| Dependence | ||
| Creativity | High | Low |
| False Positives/Negatives | Low | Moderate |
Factors to Consider Before Choosing a Penetration Testing Service Provider
When considering the cost of manual and automated penetration testing in India, it’s important to take into account several factors that can influence the overall pricing. Here are some key factors to consider:
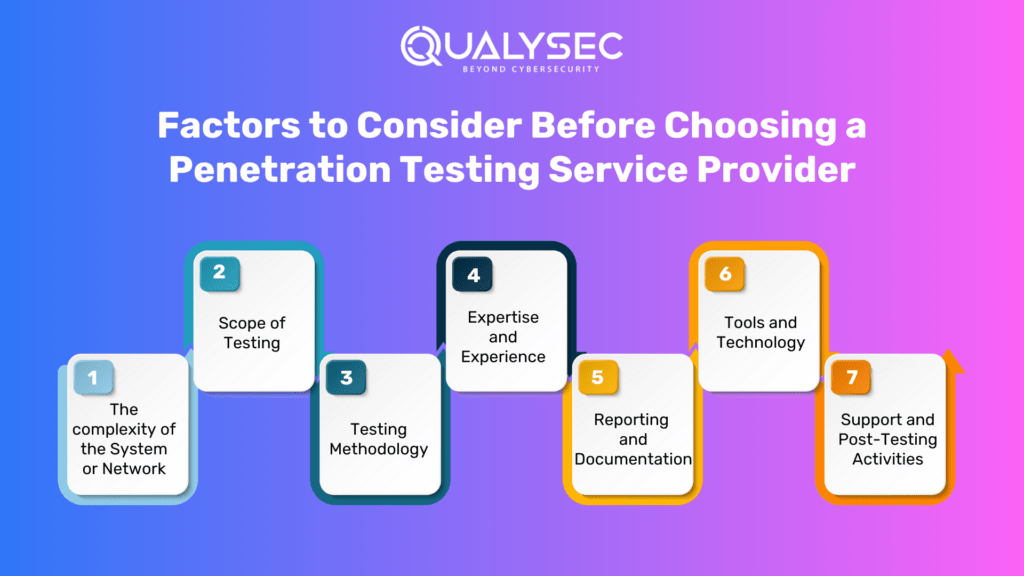
The complexity of the System or Network
The complexity of the system or network being tested is a significant factor in determining the cost. Highly complex environments with multiple layers, interconnected systems, and intricate configurations may require more time and effort, thus increasing the cost.
Scope of Testing
The scope of the penetration testing project plays a crucial role in determining the cost. A broader scope that includes a larger number of systems, applications, or network segments will naturally require more resources and time, resulting in higher costs.
Testing Methodology
The testing methodology employed by the penetration testers can affect the cost. Different methodologies may require varying levels of effort, expertise, and time. For example, a comprehensive and thorough methodology that includes extensive manual testing may be more time-consuming and, therefore, more expensive.
Expertise and Experience
The qualifications, expertise, and experience of the penetration testers also impact the cost. Highly skilled and experienced testers with specialized knowledge and certifications often command higher rates. Their expertise can ensure more accurate and effective testing, reducing the risk of missing critical vulnerabilities.
Reporting and Documentation
The level of reporting and documentation required can influence the cost. Detailed reports with in-depth analysis, recommendations, and remediation steps may incur additional charges. The complexity and comprehensiveness of the reporting deliverables should be considered when assessing the cost.
Tools and Technology
For automated penetration testing, the cost of licensing or acquiring the necessary tools and technologies should be taken into account. Some tools may have higher upfront costs, while others may have ongoing subscription fees. It’s important to evaluate the features, capabilities, and support provided by the tools to determine their value for the specific testing requirements.
Support and Post-Testing Activities
Consideration should be given to any additional support or post-testing activities required. This may include clarifications, retests, or assistance with vulnerability remediation. These services may be provided at an additional cost, so it’s essential to discuss and understand the terms and pricing for such support.
It is recommended to engage in discussions with reputable cybersecurity firms or consultants to obtain accurate and customized cost estimates. They can assess your specific needs, understand the intricacies of your environment, and provide transparent pricing details tailored to your organization’s requirements and budget.
Qulaysec, The Reputed Penetration testing Service Provider
Qualysec, A Cybersecurity company founded in 2020 is a leading cybersecurity provider. Qulaysec is also known for its renowned cutting-edge technology and expertise in cybersecurity assessments. With a team of skilled professionals, Qulaysec offers a comprehensive range of services, including various vulnerability assessments and penetration testing.
What sets Qulaysec apart is its commitment to staying ahead of the curve in terms of emerging threats and advanced hacking techniques. They employ state-of-the-art tools and methodologies to ensure thorough and accurate assessments. Qulaysec’s team of experienced professionals brings a wealth of knowledge and a human touch to their engagements. This in turn helps foster collaboration and deliver actionable insights.
Technicians at Qualysec can detect flaws that fraudsters could abuse. After these flaws have been found, Qualysec collaborates with the organization to establish a plan to address them and boost the company’s overall security posture. Among the several services available are:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
Hence, choose Qualysec for comprehensive and reliable Penetration Testing Service Provider. Also, their penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
Qualysec is a recognized Penetration testing provider. They offer comprehensive penetration testing services tailored specifically for various environments, ensuring the security of your cloud infrastructure and applications. Their expertise, tools, and methodologies can help organizations identify vulnerabilities and implement effective security measures.
Conclusion
Both manual and automated penetration testing approaches offer unique advantages and face specific limitations. While manual testing allows for in-depth analysis, creativity, and contextual understanding, it can be time-consuming and relies heavily on tester expertise. On the other hand, automated testing provides speed, consistency, and broad coverage but may lack the ability to assess complex vulnerabilities or understand contextual nuances.
To achieve comprehensive security testing, organizations often employ a combination of manual and automated approaches. By leveraging the strengths of both methods, businesses can enhance their security posture and minimize the risk of exploitation. Ultimately, the choice between manual and automated penetration testing should be based on the specific needs, resources, and objectives of each organization.
Qualysec has a successful track record of serving clients across a range of industries such as IT. Their expertise has helped clients identify and mitigate vulnerabilities, prevent data breaches, and improve their overall security posture.
When it comes to comprehensive penetration testing, with the current trend in the cybersecurity industry around cloud penetration testing and Qyalysec is best at it. Qualysec is the organization to go with. Their cost of VAPT guide helps clients make informed decisions by understanding the various factors that affect the cost by clicking here.






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments