IT security audits review the security measures of your Information Technology (IT) infrastructure. It also helps comply with the necessary industry standards for data protection. Since cyber threats always change with new vulnerabilities being discovered every time, organizations must have advanced security protocols to prevent data breaches and cyberattacks.
The global cybercrime cost is expected to reach US $10.5 trillion annually by 2025. As a result, small and big organizations are advised to perform security audits regularly to stay one step ahead of hackers.
In this blog, you will learn more about information security audits, their various types, and how you can choose the right company that provides you with these services.
Keep Reading!
What is an IT Security Audit?
An IT security audit is a comprehensive analysis of an organization’s IT infrastructure. These audits measure your IT systems’ security controls, identify existing vulnerabilities, and ensure compliance with regulatory requirements.
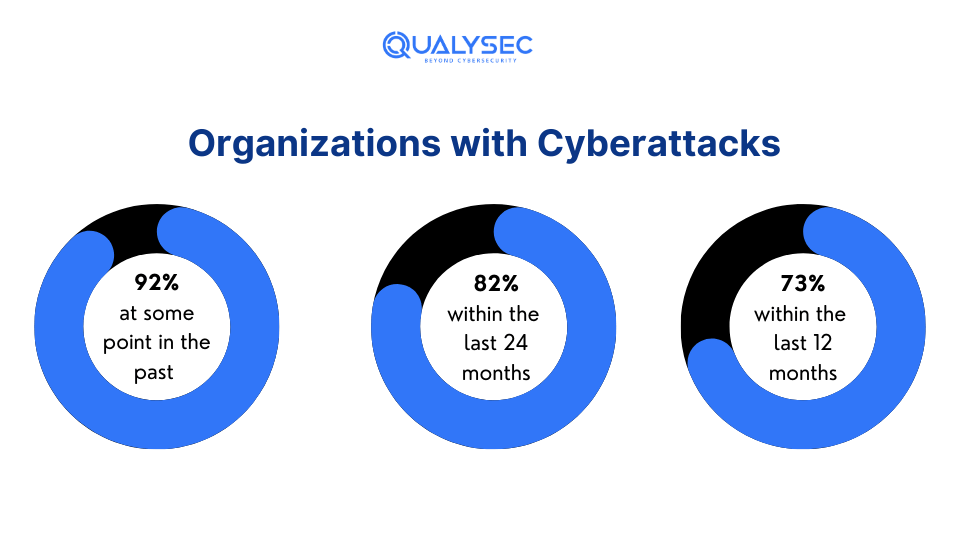
Information security audits are now essential for organizations due to new regulatory requirements like CCPA, CMMC 2.0, and GDPR. Also, since there is an average of 2,200 cyberattacks every day, it requires organizations to regularly check and improve their security.
Additionally, the modern supply chain is interconnected (for example APIs), which means that a vulnerability in one supplier can affect the entire network.
What is the Purpose of an IT Security Audit?
The main purposes of IT security audits are vulnerability identification, compliance, and protection of digital assets. Along with this, there are various other purposes. Here is a brief explanation:
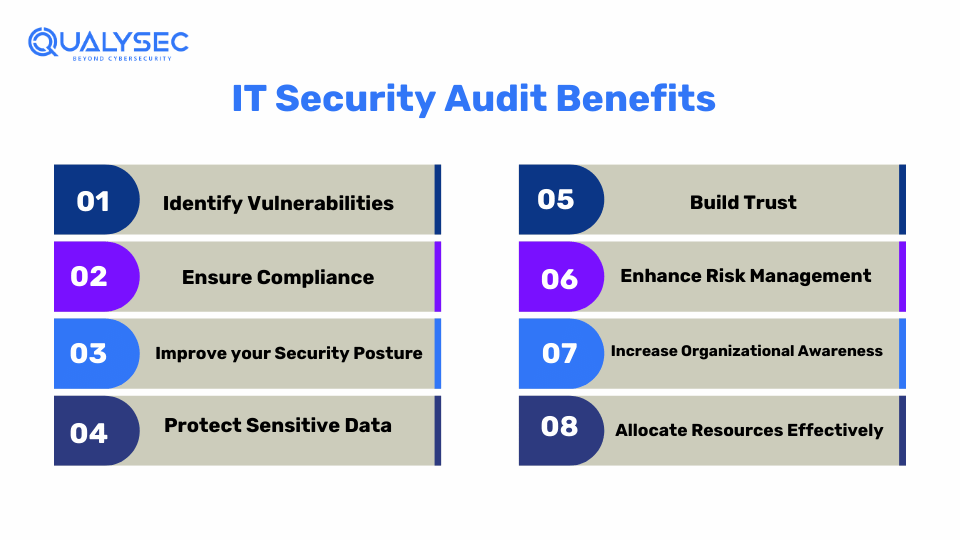
1. Identify Vulnerabilities
A security audit for IT infrastructure helps in uncovering security vulnerabilities that hackers could use for unauthorized access. By identifying them, organizations can take necessary steps to address them and improve their security posture.
2. Ensure Compliance
Ensure that your organization complies with various regulatory requirements and data protection laws such as ISO 27001, SOC 2, HIPAA, GDPR, PCI DSS, etc. This also helps you avoid legal fines and penalties.
3. Improve your Security Posture
Adopt industry best practices to enhance your current security measures for cyber threats. This may include updating your security policies, improving access controls, and ensuring all controls are up to date.
4. Protect Sensitive Data
A security audit checks whether you have the necessary measures to protect sensitive information like user details and financial details. It may check for encryption measures and secure access controls. By implementing these security testing measures, you can prevent data breaches.
5. Build Trust
By conducting IT security audits, you show your commitment to security and protecting valuable user data. This, in turn, builds the trust of customers, clients, and stakeholders. As a result, it can do well for your business and ROI.
6. Enhance Risk Management
By identifying and mitigating security vulnerabilities, you can implement strategies that will detect and respond to future security incidents in the best manner. This helps you prevent significant losses in the event of a cyberattack.
7. Increase Organizational Awareness
An audit can educate employees on possible security risks and best practices. It also makes them aware of their role in maintaining a secure environment in the organization. With remote and hybrid working arrangements being the new norm, employee awareness is crucial.
8. Allocate Resources Effectively
An IT security audit, which is also often called a “cyber security audit“, not only identifies vulnerabilities but also their impact on the organization once exploited. Hence, it will help you make informed decisions about where to allocate your manpower and budget first.
Tip: Start with the critical ones first.
What are the Different Types of IT Security Audits?
There are five different types of security audits for IT that you can choose as per your security needs.
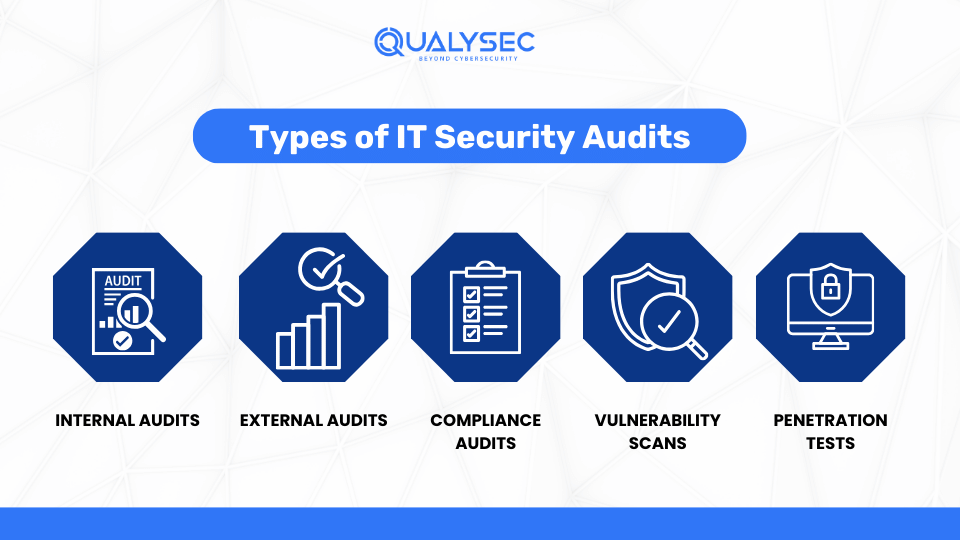
1. Internal Audits
It is conducted by your in-house IT security team that performs ongoing assessments. It helps identify vulnerabilities and suggests areas for improvement. An in-house security team maintains a high level of security for your organization, however, it can fail to mimic certain outsider attacks.
2. External Audits
This is conducted by independent or third-party security professionals. They bring an outside perspective and can find security issues that your internal teams might overlook. They help you ensure that your security measures are effective and compliant with regulatory requirements. When it comes to IT security audits, an external audit is the best choice.
3. Compliance Audits
It ensures your organization meets specific regulations like ISO 27001, SOC 2, HIPAA, PCI DSS, etc. Compliance auditors review security policies, processes, and systems to ensure that they meet regulatory compliance. By conducting compliance audits, you demonstrate that your organization adheres to industry best practices and standards.
4. Vulnerability Scans
This includes using software to scan for known vulnerabilities in assets like applications and the cloud. These automated software tools help identify potential security gaps quickly and efficiently. They also highlight areas that need improvement for better security posture.
5. Penetration Tests
This type of security audit involves ethical hackers trying to breach your systems to identify vulnerabilities. Penetration testing provides a real-world assessment of your security controls and how strong they are against cyberattacks. They provide detailed reports on the vulnerabilities identified, their severity & impact, and suggested remediation methods. This is the best method to check how a hacker would try to breach your security and how you can prevent them.
Want to conduct a penetration test? Book a call with our security expert and tell us your needs. We will create a customized plan that will secure your most prized digital assets. Don’t wait, secure your organization now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
What is the Difference Between an IT Audit and a Cybersecurity Audit?
There are quite a few differences between an IT audit and a cybersecurity audit. Let’s check the comparison.
| Aspect | IT Audit | Cybersecurity Audit |
| Focus | Evaluates overall IT infrastructure and processes. | Checks security measures to protect against various cyber threats. |
| Scope | Includes hardware, software, networks, and data management | Specifically focuses on cybersecurity controls and policies. |
| Objective | Ensure IT systems are efficient, reliable, and comply with regulations | Identify vulnerabilities, assess risk, and improve defenses against cyber attacks |
| Compliance | Ensures compliance with IT standards and regulations | Ensures compliance with security standards and frameworks like ISO 27001, HIPAA, SOC 2, etc. |
| Frequency | Typically conducted once a twice a year. | Same as an IT audit but is also conducted during significant security changes and in the event of an attack. |
| Tools & Techniques | Audit software, compliance management tools, and data assessment tools. | Specialized cybersecurity tools and techniques, such as automated vulnerability scanners and penetration testing. |
| Skills Required | Requires a strong understanding of IT governance principles (e.g. COBIT, ITIL) and risk management methodologies. | Requires expertise in ethical hacking, network security, encryption, endpoint security, etc. |
| Reporting | Reports on overall IT performance and compliance. | Reports on security posture, vulnerabilities, and mitigation strategies. |
| Outcome | Recommendations for improving IT efficiency and ensuring compliance. | Recommendations for enhancing security measures and reducing the risk of cyberattacks. |
How to Conduct IT Security Audits for Your Business?
IT security audits are usually conducted in eight steps, which are:
- Define Scope: 1st the scope of the audit is defined, which includes what areas to test. The audit company sets the objective of the audit and ensures everyone is on board.
- Information Gathering: Then the auditors gather as much information as possible about the assets that are to be audited (for example web application), such as its architecture.
- Automated Vulnerability Scanning: First the auditors use automated vulnerability scanners to test the asset for security issues.
- Manual Penetration Testing: Then the auditors use ethical hacking skills to conduct deep penetration testing to identify hidden vulnerabilities and also to verify the results of the scanners.
- Reporting: The results of the tests are documented in a detailed report. It includes all the vulnerabilities identified, their impact, and suggestions for remediation.
- Remediation: The development team uses this report to implement the suggestions provided. If needed, the audit team will help them locate and fix the vulnerabilities.
- Retest: Then the auditors will retest the asset to evaluate the total vulnerabilities fixed and those not fixed. A final report of this status is also shared with you.
- Letter of Attestation (LoA): This final document from the audit team is the summary of the audit. It includes start and end dates, total vulnerabilities identified & fixed, and current security status. This document is used for business and compliance needs.
Would you like to see a real penetration testing report? Click the link below and check how it is made!
Latest Penetration Testing Report

What are the IT Security Audit Checklists?
The IT security audit checklist is a series of procedures that should be followed to protect the IT infrastructure from various cyber threats. Here are 10 areas that IT security auditors must cover:
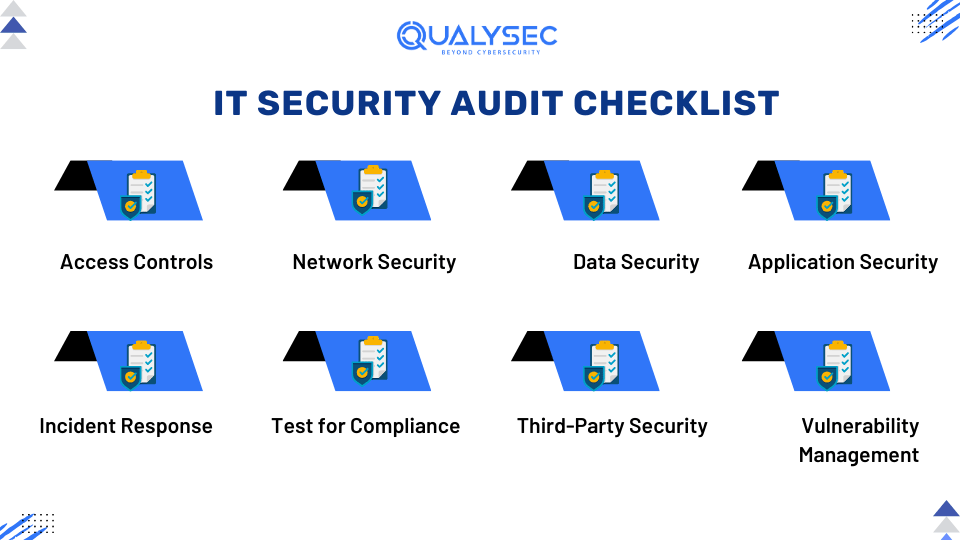
- Access Controls: Ensure that only authorized users can access critical systems and data.
- Network Security: Check if the network has adequate security measures, such as firewalls and secure configurations.
- Data Security: Ensure sensitive information is encrypted and that data backup and recovery processes are in place.
- Application Security: Review the security of software applications, including patch management, secure coding practices, and regular updates. Ensure they are free from vulnerabilities.
- Incident Response: Make sure the organization has an effective incident response plan, including procedures for identifying, reporting, and responding to security incidents.
- Test for Compliance: Check compliance with relevant industry-specific regulations and general data protection laws. Also, ensure the documentation and policies are up to date.
- Third-Party Security: Review the security measures of third-party vendors and check whether they comply with your security policies and standards.
- Vulnerability Management: Ensure regular vulnerability scans and penetration tests are conducted so that new security issues are promptly addressed.
How to Choose the Right IT Security Audit Company?
Consider these factors while choosing a security audit company for IT:
- Experience and Expertise: Look for an audit company that has experience and expertise in your industry and a good track record.
- Certifications: Ensure the company has relevant certifications, such as IT audit ISO 27001, CISSP, etc. This ensures that they will follow industry best practices.
- Reputation & Reviews: Check the company’s reputation through client testimonials, reviews, and case studies. Positive reviews from other organizations are a good sign.
- Comprehensive Audit Services: Choose a company that offers a wide range of audit services to cover all aspects of your security, such as vulnerability assessments, penetration testing, and compliance audits.
- Methodology: Inquire about what methodology the company uses for security audits. A systematic approach, aligned with industry standards ensures top-notch service.
- Post-Audit Support: Check whether the company supports implementing their recommendations. Ongoing support is crucial to improve security measures.
- Cost: Ensure that they have a transparent pricing structure. Also, check that they offer good value for the quality of the audit services provided.
- References: Ask for references from organizations that have directly worked with an audit company. They can provide real-time reviews of a security audit company’s working procedure.
Conclusion
IT security audits should be performed regularly (preferably 1 – 2 times a year) to protect your entire IT infrastructure from evolving cyber threats. Also, you should perform them if you need any compliance if your IT infrastructure has undergone any significant changes, or if you recently faced a cyberattack.
Since cyber threats and cyber attackers are growing exponentially, organizations need to have the latest patches and updated security measures to save themselves from huge financial and data loss.
FAQs
Q: What is the scope of the IT security audit?
A: The information security audit scope includes assessing areas like access controls, data encryption, secure coding practices, and compliance with industry standards.
Q: How Often Should Security Audits be Performed?
A: Security audits should be performed at least 1 – 2 times a year. Also, during significant changes, compliance requirements, and in the event of a cyberattack.
Q: What tools do IT auditors use?
A: IT auditors use a variety of automated vulnerability scanners and penetration testing tools, such as Burp Suite, Netsparker, Metasploit, Nessus, Nikto, etc.
Q: How Much Does an IT Security Audit Cost?
A: Usually, an IT security audit costs a few thousand US dollars. However, the cost depends upon the size of the organization, the scope of the audit, compliance requirements, etc.






























































































































































































































































































































































































































































































































0 Comments