As businesses increasingly rely on cloud computing for scalability, cost-efficiency, and convenience, securing cloud infrastructures has emerged as a top priority. With cyber threats becoming more sophisticated, cloud infrastructure security is vital to safeguard sensitive data, maintain business continuity, and ensure compliance with evolving regulations.
Recent statistics reveal alarming trends:
- According to a 2025 report by Cybersecurity Ventures, 88% of data breaches now involve cloud environments.
- IBM estimates the average cost of a data breach has surged to $4.45 million, with breaches in cloud environments costing businesses significantly more due to complexity and scale.
This blog gets deep into the fundamentals of cloud infrastructure security, its critical components, advanced techniques, and the best tools to fortify your cloud environment in 2025.
What is Infrastructure Security in Cloud Computing?
Infrastructure security in cloud computing is the practice of safeguarding virtual environments, applications, and sensitive data from cyber threats. It employs advanced technologies, robust policies, and effective techniques to detect, prevent, and mitigate risks such as data breaches, unauthorized access, and malware attacks.
“For a detailed guide, check out Cloud Security Vulnerability and Cloud Vulnerability Management.
Key objectives of cloud infrastructure security include:
- Data Protection: Safeguard sensitive data across its lifecycle—at rest, in transit, and in use.
- Access Management: Enforce strict controls to limit access to authorized users only.
- Real-Time Threat Detection: Monitor activities to identify and neutralize emerging threats promptly.
- Compliance: Ensure adherence to regulatory standards like GDPR, HIPAA, and ISO 27001.
- Business Continuity: Minimize downtime by mitigating risks and enhancing disaster recovery mechanisms.
Did you know? More than 95% of global organizations use cloud services in some capacity, highlighting the need for robust cloud infrastructure security to ensure smooth operations.
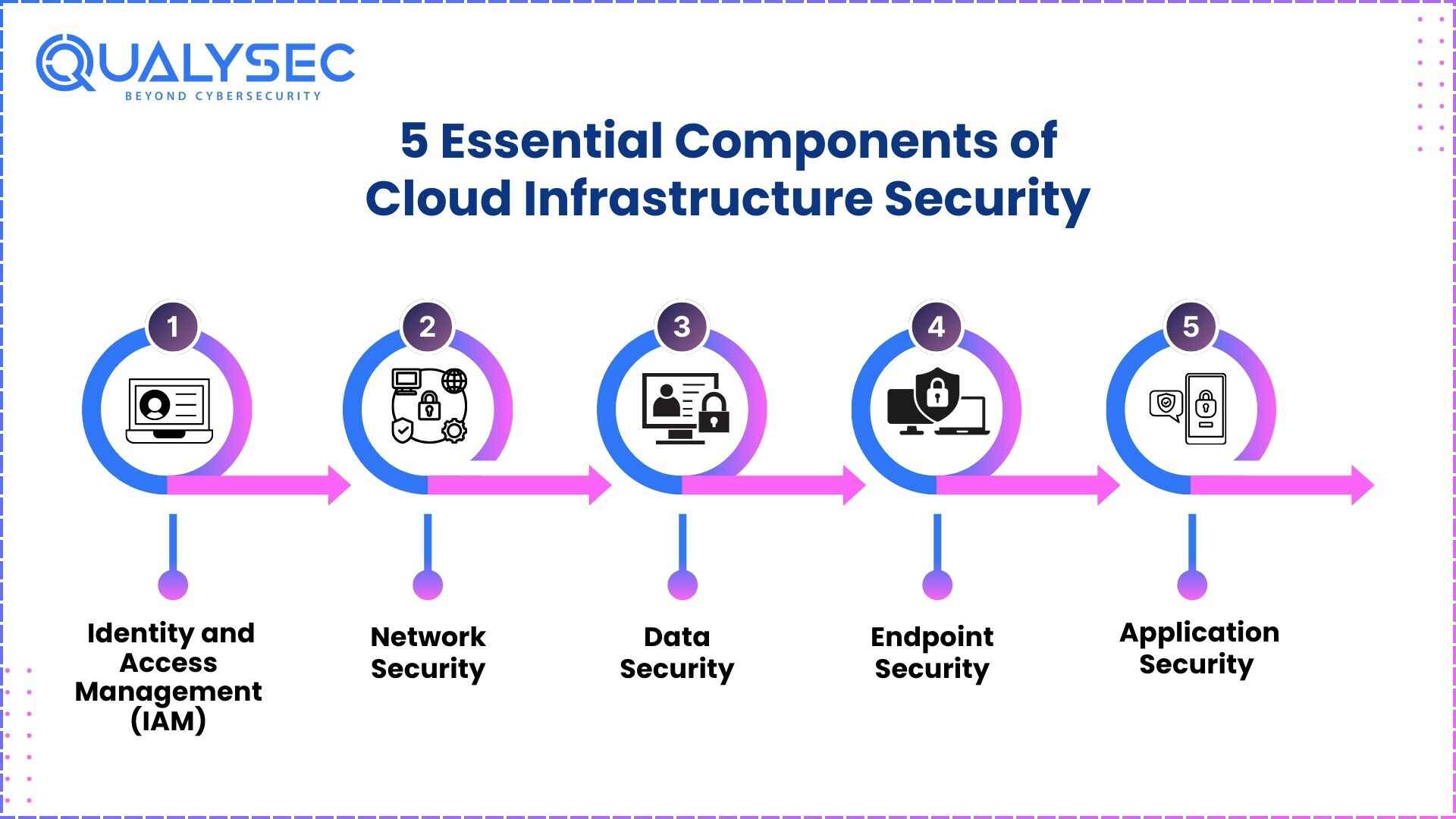
5 Essential Components of Cloud Infrastructure Security
To secure cloud environments effectively, organizations must adopt a multi-layered approach that includes the following components:
1. Identity and Access Management (IAM)
IAM governs who has access to cloud resources and what actions they can perform. This ensures that access is granted only to authorized individuals and prevents unauthorized activity.
Key IAM Features in 2025:
- AI-Powered Behavioral Analytics: Detect unusual login attempts in real time.
- Zero-Trust Architecture: Enforce least privilege principles for tighter security.
- Adaptive MFA: Use context-aware multi-factor authentication (MFA) to reduce risks.
2. Network Security
Cloud network security ensures secure communication between users and cloud resources. With data traveling over public networks, securing it against interception and tampering is critical.
Top Measures for 2025:
- Software-Defined Networking (SDN): Allow dynamic network segmentation for enhanced security.
- Advanced Firewalls: Incorporate AI-driven firewalls for better threat detection.
- TLS 1.3 Encryption: Ensure secure data transmission with the latest protocols.
“Explore our insights on Cloud Security Network.
3. Data Security
Data security involves protecting sensitive information stored or processed in the cloud. Encryption, secure key management, and tokenization are foundational techniques.
New Trends:
- Post-Quantum Encryption: Prepare for quantum computing threats with stronger encryption methods.
- Data Sovereignty Tools: Ensure compliance with regional data protection laws.
4. Endpoint Security
As organizations embrace remote work and BYOD policies, endpoints have become a significant attack vector.
Modern Endpoint Security Techniques:
- EDR/XDR Tools: Endpoint Detection and Response solutions provide proactive monitoring and remediation.
- Zero-Trust Device Management: Continuously assess the security posture of devices accessing the cloud.
5. Application Security
Cloud applications face risks such as SQL injection and XSS attacks. Application security involves safeguarding these assets through secure development practices and runtime protections.
2025 Trends in Application Security:
- DevSecOps Integration: Embed security into the development lifecycle.
- RASP: Runtime Application Self-Protection to detect and prevent threats during runtime.
“To dive deeper into cloud-based application protection, refer to Cloud Security VAPT.
Qualysec’s cloud pentest gives you results—no endless emails, no digging through PDFs, no guesswork.

Advanced Techniques for Cloud Infrastructure Security (Expanded)
Below are some techniques to ensure robust cloud infrastructure security. These methods not only mitigate risks but also strengthen your cloud environment’s resilience.
1. AI-Driven Threat Detection
Artificial Intelligence (AI) and Machine Learning (ML) have revolutionized cybersecurity by enabling faster and smarter threat detection.
- Predictive Analytics: AI models analyze patterns of historical data and user behavior to predict potential security risks. For example, unusual access patterns or login attempts can be flagged before they escalate into breaches.
- Real-Time Anomaly Detection: AI-powered systems continuously monitor network traffic and user activities to identify anomalies in real time. This is crucial for detecting zero-day attacks or insider threats.
- Automated Response: AI can automate responses to low-level threats, such as isolating compromised devices or accounts.
- Threat Intelligence Integration: These systems aggregate and analyze threat data from multiple sources to provide actionable insights to preempt cyberattacks.
Examples of AI-driven tools: CrowdStrike Falcon, Darktrace, Microsoft Defender for Cloud.
2. Cloud Penetration Testing
Penetration testing (pentesting) simulates cyberattacks to identify vulnerabilities in a cloud environment. Modern advancements in this field include:
- Red Teaming Exercises: These go beyond traditional pentests by simulating sophisticated, multi-step attacks that mimic real-world adversaries. Red teams work to exploit vulnerabilities, while blue teams (defenders) improve their detection and response capabilities.
- Data-Driven Testing Models: Combine automated tools with manual testing along with data-driven methodologies for a complete assessment of cloud infrastructure, including APIs, databases, and identity systems.
- Compliance-Focused Testing: Pentests now align with regulatory standards like GDPR, PCI-DSS, or HIPAA, ensuring not only security but also adherence to legal requirements.
- Cloud-Specific Pentesting: Cloud platforms like AWS, Azure, and GCP require specialized pentesting techniques to account for shared responsibility models and unique configurations.
Benefits of pentesting:
- Identifying misconfigurations in cloud storage buckets or access policies.
- Detecting exploitable vulnerabilities in APIs and applications.
- Strengthening overall cloud security posture.
Latest Penetration Testing Report

3. Cloud-Native Security Platforms
Cloud-native security platforms are designed to address the unique challenges of cloud environments. These platforms integrate security measures directly into the development lifecycle and operations of cloud-based systems.
- Identity and Access Management (IAM): Platforms like Okta and AWS IAM help enforce least-privilege access and implement robust authentication protocols (e.g., MFA, SSO).
- Workload Protection: Tools like Prisma Cloud and Lacework provide runtime protection for containers, Kubernetes, and serverless workloads.
- Threat Detection and Response: Cloud-native tools offer advanced features like automated incident response, forensic analysis, and threat hunting.
- Integrated Compliance: Many platforms include compliance monitoring and auditing tools for frameworks like SOC 2, ISO 27001, and CCPA, simplifying regulatory adherence.
These platforms deliver seamless integration across hybrid and multi-cloud environments, ensuring unified visibility and control over all cloud assets.
4. Immutable Backups
Immutable backups are an essential line of defense against ransomware attacks and other data manipulation threats.
- Ransomware Resilience: Immutable backups cannot be altered or deleted, even by administrators or unethical hackers.
- Versioning: Multiple versions of the same data are stored, allowing organizations to recover previous states in case of corruption or accidental deletion.
- Encryption at Rest and in Transit: Protect backups from unauthorized access while maintaining compliance with data protection regulations.
- Cloud-Native Solutions: Services like AWS Backup Vault Lock, Azure Immutable Blob Storage, and Google Cloud Archive Storage provide easy-to-implement immutable backup capabilities.
By incorporating immutable backups, businesses ensure rapid recovery and continuity even in the face of severe security breaches.
5. Continuous Compliance Monitoring
Compliance is a critical aspect of cloud security, especially for industries handling sensitive data (e.g., healthcare, finance). Continuous compliance monitoring ensures that your cloud infrastructure adheres to regulatory and industry standards at all times.
- Automated Audits: Automated tools like AWS Config and Azure Policy continuously monitor and report on the compliance status of your cloud resources.
- Drift Detection: Detects and remediates configuration drift—changes that deviate from established compliance baselines.
- Custom Policies: Organizations can define custom policies to meet specific business needs while staying compliant with regulations like GDPR, HIPAA, and ISO 27001.
- Real-Time Alerts: Immediate notifications of compliance violations help mitigate risks before they become major issues.
With continuous compliance monitoring, organizations not only meet regulatory requirements but also minimize risks associated with non-compliance penalties and reputational damage.
Top Tools for Cloud Infrastructure Security in 2025
Here are some of the best tools available for cloud security:
- AWS Security Hub: Centralizes security management with actionable insights and automated compliance checks.
- Microsoft Defender for Cloud: Offers continuous security monitoring, advanced threat intelligence, and integration across hybrid environments.
- Google Cloud Security Command Center: Provides real-time visibility into security risks with advanced detection mechanisms.
- Palo Alto Prisma Cloud: Complete cloud-native security platform that covers IaC scanning, workload protection, and compliance.
- IBM Cloud Pak for Security: AI-driven analytics and automation for faster threat detection and response.
Conclusion
Securing cloud infrastructure is no longer optional in 2025; it is a business-critical mandate. With the growing reliance on cloud computing, organizations must adopt proactive measures to safeguard sensitive data, ensure compliance, and maintain customer trust.
By focusing on key security components, leveraging advanced techniques, and adopting the latest tools, you can significantly reduce risks and enhance the resilience of your cloud environment.
Need expert help to secure your cloud infrastructure? Our team specializes in comprehensive cloud penetration testing to uncover vulnerabilities and strengthen your security posture. Contact us today to learn more!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQs
Q: What do you mean by infrastructure security in cloud computing?
A: Infrastructure security in cloud computing refers to measures to protect critical assets and resources in the cloud from potential security threats.
Q: How to secure cloud infrastructure?
A: You can secure cloud infrastructure by implementing certain security measures, such as:
-
- Cloud penetration testing
- Data encryption
- Identity and access management (IAM)
- Cloud firewalls
- Versioning and Logging
- Continuous cloud monitoring
Q: What is the infrastructure of cloud computing?
A: Cloud infrastructure refers to the components present/required to provide various cloud computing services. For example, storage, networking, computing power, and an interface that allows users to access virtual resources.




























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments