Cloud security testing helps protect the cloud environment by identifying and mitigating vulnerabilities. Almost every business functioning online uses the cloud in some other way. Be it for scaling, business operations, or data storage, cloud computing offers an array of benefits for business growth. However, they are not immune to cyber threats and need constant protection from attackers.
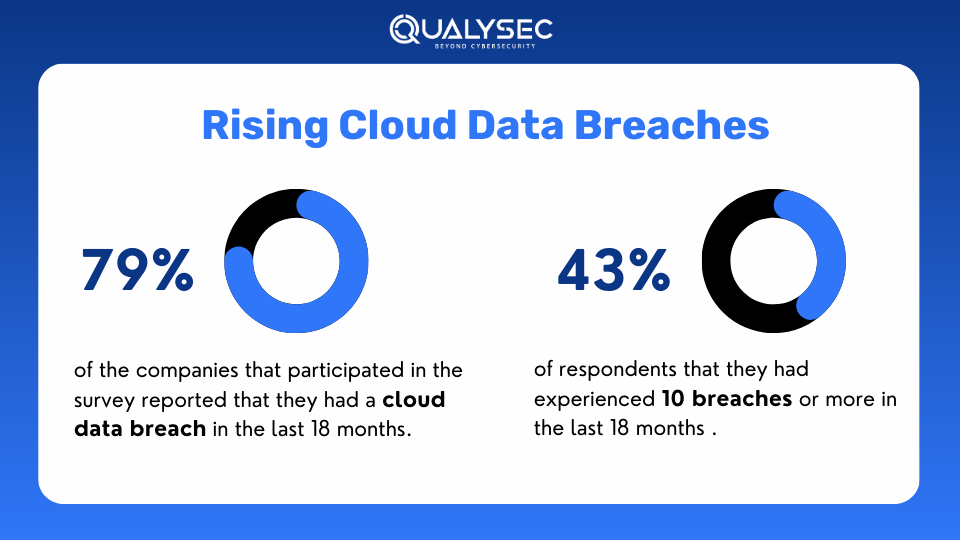
According to a recent survey, 45% of breaches are cloud-based. This comes along with the fact that over 80% of companies have faced at least one cloud attack in the past year itself, where 27% of them experienced a public cloud security incident.
So, if your organization uses cloud services, such as Amazon Web Services (AWS) or Google Cloud Platform (GCP), this blog is for you. Here, we will discuss cloud security testing, how can it help protect your cloud infrastructure, and how to do it effectively.
What is Cloud Security Testing?
Cloud security testing is a type of cybersecurity testing done on the cloud infrastructure to find vulnerabilities and security loopholes that hackers could exploit. It is done to ensure that the data and resources present in the cloud are protected from cyberattacks.
It also examines the cloud provider’s security policies, procedures, and controls. Then it attempts to find security weaknesses that could lead to data breaches and other security incidents. It is often performed by third-party security auditors or penetration testing providers.
Security testers perform this task using various automated and manual testing techniques. The results of the testing are used to enhance the security measures of the cloud infrastructure. Along with this, the testing certificate also helps the business achieve the necessary compliance with their respective industry standards.
Why is Cloud Security Testing Important?
The main reason to conduct cloud security testing is to protect the data and resources in the cloud from attackers. Additionally, it offers a wide range of benefits, such as:
- Identify and mitigate security vulnerabilities
- Enhance cloud security measures
- Comply with industry standards like SOC 2, ISO 27001, HIPAA, etc.
- Prevent data breaches and financial loss
- Build customer trust by showing your commitment to cloud security
- Ensure smooth cloud operations
Types of Cloud Security Testing
There are quite a few types of cloud security testing services that collectively help secure the cloud environment, such as:
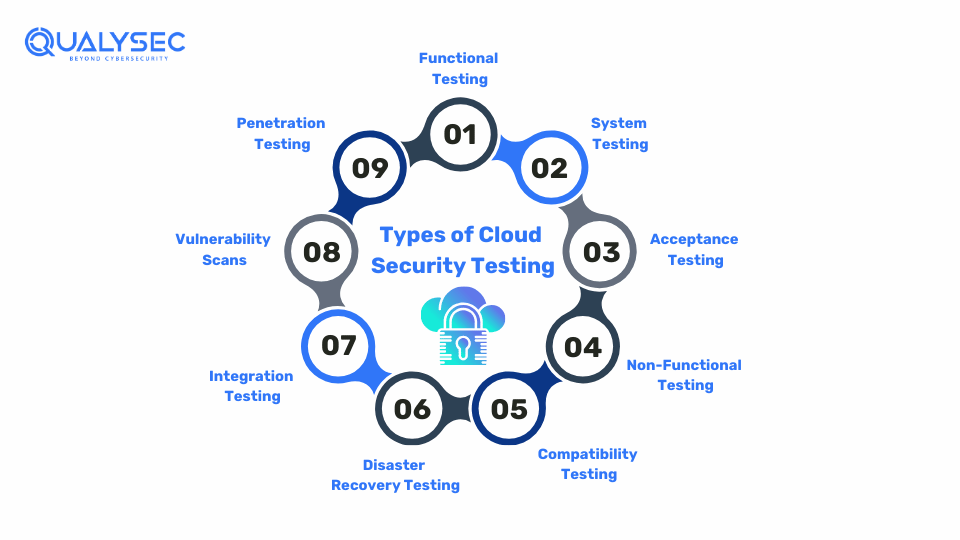
1. Functional Testing
Functional testing involves testing your application’s performance. By evaluating each function according to its pre-defined requirements, you can ensure that the application operates as it is intended.
2. System Testing
System testing provides a comprehensive look at the entire software system. It goes beyond individual components, assessing the complete system to ensure all requirements and functionalities work together effectively. Security testing is an essential part of this process, ensuring that vulnerabilities are identified and addressed.
3. Acceptance Testing
Acceptance testing ensures your cloud security solution meets your business needs. It’s the final check to confirm that the software aligns with your organization’s goals.
4. Non-Functional Testing
Non-functional testing focuses on the user experience beyond just functionality. It carefully evaluates service quality, reliability, usability, and response times to ensure the software provides an excellent experience.
5. Compatibility Testing
Compatibility testing ensures software works smoothly in different environments. It checks that the software operates well across various cloud platforms and operating systems.
6. Disaster Recovery Testing
Disaster recovery testing checks how well an application can recover from unexpected security issues. It measures recovery time to ensure the application can quickly bounce back with minimal data loss enhancing application security.
7. Integration Testing
Integration testing checks for issues that may occur when different software components work together. It ensures these modules communicate and collaborate effectively, creating a seamless software ecosystem.
8. Vulnerability Scans
These security scans use automated software or tools to test the cloud for known vulnerabilities, providing valuable insights by identifying potential security gaps through vulnerability scanning.
9. Penetration Testing
Penetration testing involves ethical hackers simulating attacks on the cloud to find hidden vulnerabilities. This helps in checking the cloud’s strength in preventing cyberattacks and also helps in improving them.
How to do Cloud Security Testing?
While there are a few different ways to do cloud security testing, the best option is to combine automated vulnerability scanning with manual penetration testing. Here’s how it should be done:
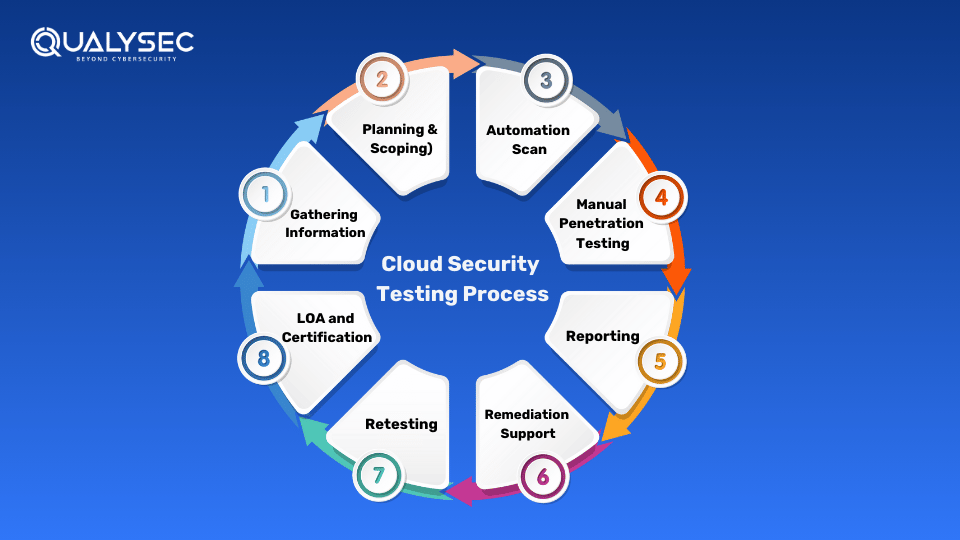
- Define Scope: 1st the testing team defines the goals and objectives of the test. They determine which areas of the cloud to test and ensure that everyone is on board.
- Information Gathering:Then the testing team gathers all the necessary information about the cloud environment to help understand it.
- Automated Vulnerability Scanning: The testers first use automated vulnerability scanners to test the cloud for known vulnerabilities.
- Manual Penetration Testing: Then the testers use their ethical hacking skills to deep dive into the cloud environment to find hidden vulnerabilities. They also verify the results of the automated tools.
- Reporting: The results and findings of the tests are documented in detail and shared with the development team for remediation.
- Remediation: The development/security team uses the pen test report to fix all the vulnerabilities present in the cloud.
- Retesting: The testing team retests the cloud environment to check the number of vulnerabilities fixed and those not fixed. This helps the cloud user to know the current security status.
- Letter of Attestation (LoA): This final document summarizes the entire testing process. It also includes the total number of vulnerabilities identified and fixed and the current security posture of the cloud. The LoA helps the organization with various business and compliance needs.
Want to see a real cloud security testing report? Click the link below and download one right now!
Latest Penetration Testing Report

What are the Best Cloud Security Testing Tools?
There is a wide range of cloud security testing tools that are used worldwide. However, only a handful of them provide the desired results, such as:
- AWS Inspector: It is an automated security assessment tool that helps identify vulnerabilities and checks whether your AWS environment follows the best practices.
- Nessus: A comprehensive vulnerability scanner that detects potential threats and security issues across your cloud infrastructure.
- CloudBrute: It is a tool that helps discover cloud resources and potential exposures by scanning for public cloud services and assets.
- PACU: It is an AWS penetration testing or exploitation framework that allows security professionals to test the security of their AWS environments by simulating various attack scenarios.
- S3Scanner: S3Scanner scans Amazon S3 buckets for misconfigurations and potential vulnerabilities to ensure your data is securely stored.
- Mimikatz: It is a post-exploitation tool that helps security testers extract sensitive information, such as passwords and tokens, from memory to assess potential vulnerabilities.
Best Practices for Cloud Security Testing
For a comprehensive review, it is important that your cloud security testing covers essential areas, such as:
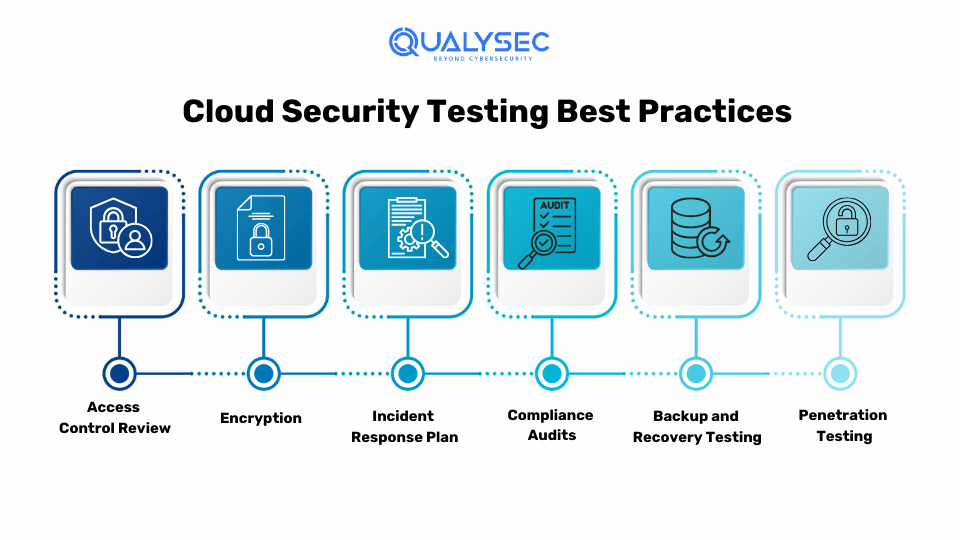
1. Access Control Review
Check who has access to your cloud resources and data. Ensure only authorized users have permission to access them to minimize the risk of unauthorized access. Use measures like least privilege, where users are given minimum access needed for their roles as part of a cloud security assessment.
2. Encryption
Encrypt data both at rest and in transit to protect it from unauthorized access and tampering. Use strong encryption standards to ensure that sensitive information remains protected. Encryption is an extra layer of security, making it harder for attackers to access your data even if they breach your defenses.
3. Incident Response Plan
Develop an effective incident response plan for responding to security incidents. Ensure that all team members know their roles and can act quickly to mitigate any potential damage. A well-prepared incident response plan helps minimize impact and restore normal operations efficiently.
4. Compliance Audits
Regularly conduct compliance audits to ensure your cloud environment meets industry regulations and standards, for example, PCI DSS, ISO 27001, HIPAA, etc. These audits help identify vulnerable areas and provide guidance on necessary improvements. Staying compliant not only enhances security but also builds trust with customers and partners.
5. Backup and Recovery Testing
Test your backup and recovery procedures to ensure you can quickly restore data in case of a security incident. Effective backup and recovery strategies help minimize downtime and data loss during a breach. Regular testing ensures that your backup systems are reliable and can be depended upon when needed.
6. Penetration Testing
Perform simulated cyber-attacks on your cloud environment to identify security weaknesses. Cloud penetration testing helps uncover potential entry points for hackers and tests your defenses. This practice helps improve your security posture by finding and fixing vulnerabilities that can cause data breaches and other security incidents.
Interested in penetration testing? Qualysec has secured over 500 applications, both web and cloud-based for 110+ clients. Talk to our security experts today and start securing your cloud environment and business today!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Challenges in Cloud Security Testing
While cloud security testing provides numerous benefits there are a few challenges testers face, such as:
- Dynamic Environments: Cloud environments are always changing. This can be challenging for testers as they have to keep up with new changes and secure new components.
- Shared Responsibility Model: In the cloud, security responsibilities are shared between the provider and the customer. It can be challenging to understand where the provider’s responsibilities end and where yours begin.
- Complex Configurations: Cloud services often involve complex configurations across multiple platforms and services. Misconfigurations can lead to severe vulnerabilities. Ensuring all configurations are correct can be a tedious task.
- Data Privacy: Ensuring data privacy in a cloud environment can be challenging due to shared infrastructure. It’s vital to use strong encryption and access controls to protect sensitive data from unauthorized access or breaches.
- Limited Visibility: Cloud providers may not offer full visibility into their infrastructure. As a result, itmakes it difficult for security testers to perform comprehensive security testing.
Conclusion
The complex structure of a cloud environment and the unique threats it faces require regular security testing if you want to protect its data and resources. Cloud security testing not only helps you fix security issues but also helps with achieving compliance and building customer trust.
To properly secure your cloud infrastructure, you need a good cloud security testing provider like Qualysec. You can check our track record, our methodologies, our certifications, and our customization options before you choose us. In the end, it is all about protecting the very data your business relies upon.
FAQ
Q: What is a cloud security assessment?
A:A cloud security assessment identifies vulnerabilities, configuration issues, and potential threats in the cloud infrastructure. Additionally, it analyses the configuration of the cloud service provider and reviews potential threats from the internet.
Q: What is cloud application security testing?
A: It is a process of testing cloud-based applications to identify vulnerabilities that attackers cold exploit for unauthorized access and data breaches.
Q: What are the 3 categories of cloud security?
A: The three categories of cloud security are:
- Provider-based
- Customer-based
- Service-based
Q: Who provides cloud security testing services?
A: A third-party security testing or penetration testing provider provides cloud security testing services. This is because a security certificate from an independent provider is more trustworthy than in-house testing.




































































































































































































































































































































































































































































































































0 Comments