Cloud penetration testing is a specific type of penetration testing that evaluates the security measures of cloud-based systems and services. With over 92% of organizations globally using some form of cloud infrastructure, they have become a major cybercriminals target. In fact, as per IBM, victims of cloud asset data breaches spend around $5 million on average to recover.
Despite cloud platforms having some sort of security features like scalable compute power, easily deployable backups, and technical support documentation, there are unique security risks associated with them that need to be addressed.
In this blog, we will get an in-depth knowledge of cloud penetration testing. Additionally, we’ll discuss common risks associated with cloud infrastructure, and how penetration tests can help secure cloud services and assets.
What Happens in Cloud Penetration Testing
In cloud penetration testing, pen testers or ethical hackers simulate cyber attacks against the organization’s cloud-native services, applications, and APIs to find any vulnerabilities present that cybercriminals could exploit. They also test corporate cloud components such as serverless computing platforms, federated login systems, and Infrastructure as Code (IaC) for security gaps.
A cloud penetration test provides a detailed report to the organizations that mention vulnerabilities found in their cloud infrastructure and their severity. Along with it, the report also mentions steps to remediate those vulnerabilities. By conducting regular penetration testing for cloud infrastructure, organizations can address potential cloud security risks and mitigate them before they are used for cyber attacks.
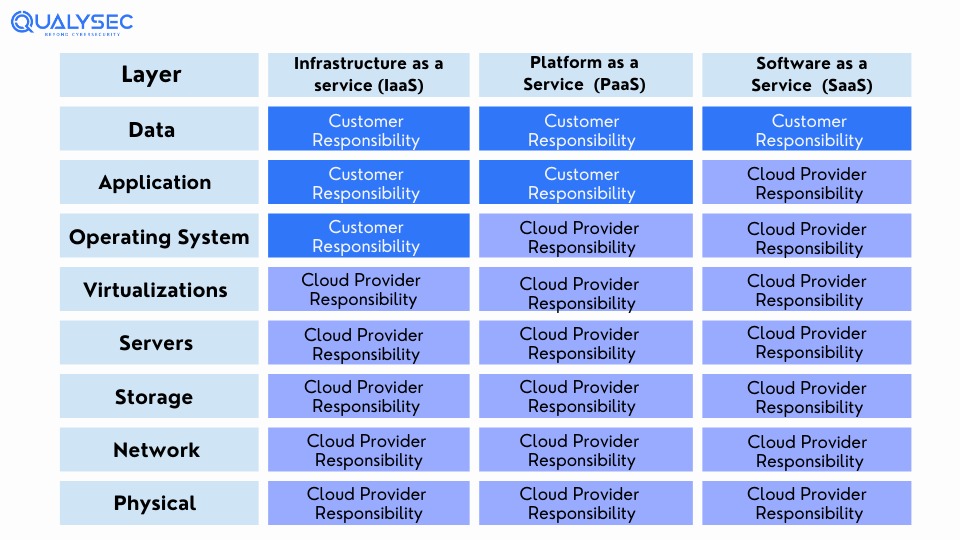
The Shared Responsibility Model of Cloud Services
Cloud services have 3 main models:
- Software as a Service (SaaS): It is a software delivery model where the vendor hosts an application in the cloud that can be used by its subscribers.
- Platform as a Service (PaaS): It is a platform delivery model that can be purchased and used for developing, running, and managing applications.
- Infrastructure as a Service (IaaS): An infrastructure delivery model where the vendor offers various computer resources over the internet such as virtualized servers, storage, and network equipment.
| Service Model | Vendor Responsibility | User Responsibility |
| SaaS | Application security | Endpoints, user and network security, misconfigurations, workloads, and data |
| PaaS | Platform security, including all hardware and software | Security of applications developed on the platform Endpoints, user and network security, and workloads |
| IaaS | Security of all infrastructure components | Security of any application installed on the infrastructure (e.g. OS, applications, middleware) Endpoints, user and network security, workloads, and data |
 What is the Purpose of Cloud Penetration Testing
What is the Purpose of Cloud Penetration Testing
Cloud penetration testing is a security exercise, designed to check the strengths and weaknesses of cloud systems and improve their overall security posture. The main purpose of cloud pentesting is to:
-
- Identify vulnerabilities, risks, and security gaps
- Impact of those vulnerabilities
- Determine how to use the access gained by exploiting those vulnerabilities
- Deliver clear and actionable remediation methods
- Provide best practices to maintain visibility
How Cloud Penetration Testing Secures Cloud Services
More and more companies are including a wide range of applications, data, and services in their cloud. For example, public web applications, file-sharing and business productivity applications, mobile app data, system backups, network monitoring data and log files, and both employee and customer data. As a result, the cloud environment has become a primary target for attackers.
Cloud penetration testing reports provide an accurate representation of the environment’s security posture, where the vulnerabilities lie, and what is its impact. Additionally, it showcases how resilient your cloud infrastructure is, against cyber attacks, unauthorized access, and data breaches.
 Here is How Cloud Penetration Testing Helps Secure Cloud Systems and Services:
Here is How Cloud Penetration Testing Helps Secure Cloud Systems and Services:
1. Identify Vulnerabilities before Hackers
Before real hackers break into your cloud system, you employ ethical hackers or cybersecurity professionals to check for potential entry points. Cloud penetration testing shows weaknesses present in your cloud infrastructure and allows you to address those security flaws before cyber attacks can exploit them.
2. Assess Cloud-Specific Risks
Cloud environments have unique security risks due to their shared responsibility models, different service models (SaaS, PaaS, IaaS), and complex configurations. Penetration testing services can be tailored to mitigate risks specific to cloud environments.
3. Prevent Data Breaches
Cloud-based applications and services store and manage a large amount of sensitive data. This is the reason why cybercriminals are drawn toward cloud environments. Penetration testing helps find weak points through which these criminals can enter your system. thus, saving the organization from severe data breaches,
4. Comply with Regulatory Standards
Many industries and jurisdictions have strict compliance rules to protect user information. For example DPR, PCI DSS, SOC 2, HIPAA, etc. Cloud penetration testing helps organizations meet these regulatory requirements and showcase their commitment to protecting user data and maintaining security controls.
5. Maintain Customer Trust and Reputation
Your customers or clients using your cloud services trust their confidential data is safe with you. If a data breach occurs, not only will it result in huge time and monetary loss, but also you will lose the trust of your customer. Additionally, your reputation in the industry will go down, resulting in less business revenue. Conducting cloud pentesting can help your organization avoid all of this and even gain you more customers, given that you prioritize data safety.
6. Validate Cloud Provider Security
Cloud service providers implement various security controls, but organizations need to verify these measures independently. Penetration testing is a great way to test the effectiveness of the security controls implemented by the cloud service providers.
7. Minimize Downtime and Losses
By addressing vulnerabilities before cybercriminals exploit them, organizations can reduce the likelihood of system downtime, data breaches, and potential financial losses.
8. Improve Security Awareness
When organizations conduct penetration testing, it shows that they prioritize cybersecurity a lot. As a result, it raises awareness among employees and stakeholders of the importance of security best practices. Additionally, it can lead to a better security-conscious culture within the organization.
9. Prioritize Risks and Allocate Resources Effectively
Cloud penetration testing reports provide a clear understanding of the severity of the security risks found during the process. This allows organizations to assess what risks are more important for their business and allocate their resources and efforts to fixing the most severe vulnerabilities first.
10. Adapt to Evolving Threat Landscape
The cybersecurity landscape is constantly changing, with new breaching techniques being developed by hackers. Regular penetration testing on cloud infrastructure helps organizations stay one step ahead of the new threats that may emerge in the cloud.
Want to protect your cloud services and the data present in them? Qualysec Technologies is a leading cloud penetration testing provider that follows a hybrid approach to find hidden vulnerabilities. Contact us now and secure your cloud environment from severe data breaches!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
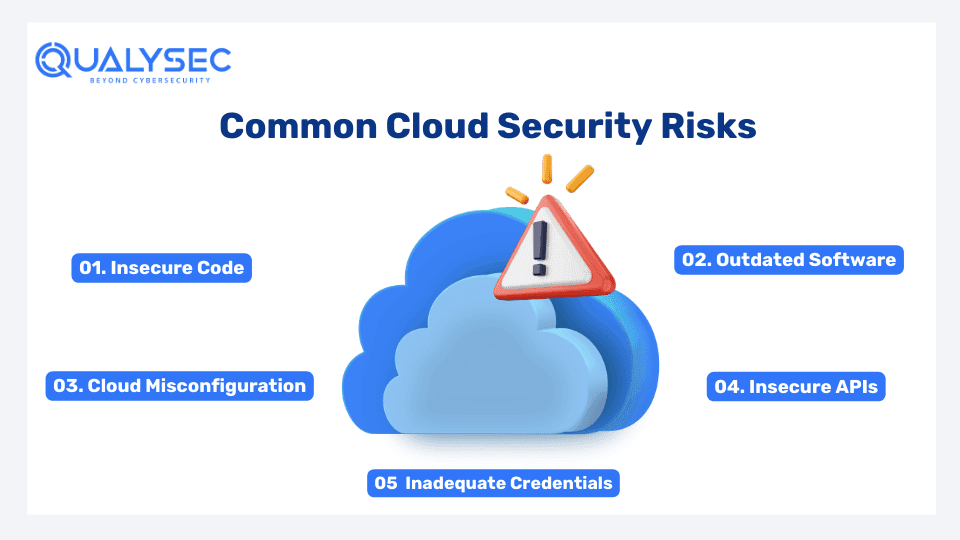
Common Security Risks in the Cloud Environment
Several generic and cloud-specific weaknesses can be exploited by cybercriminals for their gain. Here are some common vulnerabilities in cloud environments that can lead to cyber attacks:
1. Insecure Code
Most companies build their cloud infrastructure very cheaply. As a result, they face a lot of software problems like SQL, XSS, and CSRF. Some cybersecurity companies offer source code reviews under penetration testing. Make sure you ask your testing provider about this.
2. Outdated Software
Using old software can lead to serious security problems for your cloud services and assets. Most software companies don’t make updating easy, and many users turn off automatic updates. This makes cloud services outdated, which hackers can easily find using automated tools. So, if your cloud services use old software, they’re at risk of being hacked.
3. Cloud Misconfiguration
This is probably the most common cloud vulnerability that exists. When the organization fails to follow IT security best practices and neglects code reviews, it causes misconfiguration in cloud services. In fact, the National Security Agency (NSA) considers cloud misconfiguration as a top IT security threat. It is so common that amature attacks can even exploit it with automated tools.
4. Insecure APIs
API keys are used to identify and authorize organizations and third-party vendors. If you don’t keep them safe, someone might get access to them. To prevent this, organizations should not put API keys in a secure location where unauthorized people cannot access them. Cloud penetration testing can evaluate if you have proper or broken access controls so that your API keys are safe.
5. Inadequate Credentials
Password security has been a big concern for businesses since ever. If an attacker gets access to an employee’s login credentials, they can hack into the cloud and steal sensitive data. Penetration testing helps discover if the credentials are strong and unique enough to get unauthorized access.
How Cloud Penetration Testing is Performed
There is no 1-step process of cloud penetration testing that every cybersecurity company follows. However, the basic procedure remains the same, which is:
-
- Information gathering
- Defining the scope of the test
- Using automated tool scanning
- Manual penetration testing
- Providing report
- Remediation
- Retesting
- Final report/security certificate
Conclusion
With the increased usage of cloud products and services, the risk of cyber attacks targeting these environments has also gone high. Cloud penetration testing helps organizations identify vulnerabilities, assess risks, and strengthen existing security measures to protect against potential breaches and data loss.
By conducting regular penetration tests, organizations can proactively address security weaknesses, comply with regulatory standards, and maintain customer trust and reputation. Additionally, penetration testing enables organizations to validate the effectiveness of their cloud service provider’s security controls and allocate resources effectively to mitigate the most vital risks.
FAQs
Q: What is Cloud Penetration Testing?
A: Cloud penetration testing is the process of testing an organization’s cloud-native services, applications, and APIs to find any vulnerabilities present that cybercriminals could exploit.
Q: How do I start cloud penetration testing?
A: Follow this process to start cloud penetration testing:
-
- Identify the cloud services you use
- Understand the rules, regulations, and liabilities
- Understand the cloud’s security controls
- Prepare a pentest plan
- Implement all the necessary techniques and tools for pen test
- Produce the pentest report
- Help the organization with remediation plan
Q: Common tools used for cloud penetration testing?
A: Penetration testing is a manual process conducted by skilled cybersecurity professionals. However, some automated tools are used to scan for vulnerabilities on the surface level, such as:
-
- Pacu
- CloudBrute
- Mimikatz
- AWS inspector
- S3 Scanner
- Nessus
- Prowler
- Cloud enum
- Scout suite
Q: What is Azure and AWS penetration testing?
A: Microsoft Azure and Amazon Web Services (AWS) are the two most popular cloud service providers. Penetration testing is performed on AWS and Azure to test their security strengths and find any vulnerabilities that could be exploited by cybercriminals.







 What is the Purpose of Cloud Penetration Testing
What is the Purpose of Cloud Penetration Testing
















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments