With the rise of cloud computing in business, the use of APIs (Application Programming Interfaces) has also increased. APIs allow apps to communicate and share data, making it easier for developers to create and integrate new programs. As APIs are the pipes that connect various applications and business services, they are obvious entry points for attackers.
API security testing involves checking vulnerabilities in the APIs to verify whether they are protected from cyber threats. Since APIs are the backbone of modern application architecture, their security is very important for businesses.
In this blog, you will know more about API security testing, how it is performed, and its different types. If you use APIs in any way, this blog is going to save you a lot of trouble.
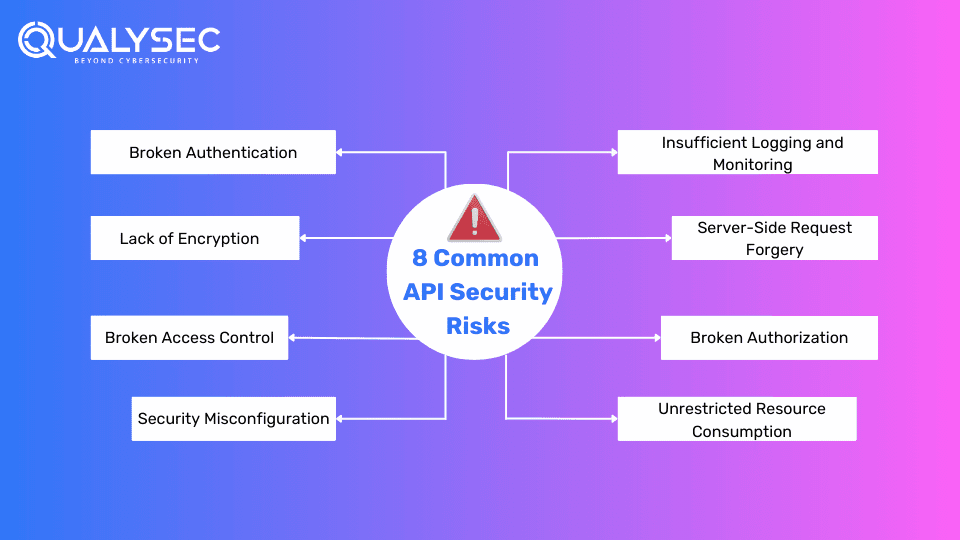
What is API Security Testing?
API security testing is the process of evaluating the defenses of APIs to ensure they are resistant to vulnerabilities and unauthorized access. It is also now a major part of the software development lifecycle (SDLC), where developers even test the API before they are deployed.
Businesses hire cybersecurity companies to perform API security testing to find vulnerabilities or weak points through which attackers can infiltrate the system. As a result, you can know where the security flaws lie and take the necessary steps to fix them.
API security testing is essential to enhance the overall security posture by finding and mitigating vulnerabilities in the APIs.
Importance of API Security Testing for Companies
The fast growth of digital changes and the widespread use of APIs have led to a new era where systems and services are more connected. However, relying more on APIs also brings new security challenges.
- Integration Demands: Integration is crucial as businesses change digitally. APIs help connect systems, but they can also expose sensitive information, so it’s vital to keep them secure.
- API Dependency: Cloud applications rely on APIs to share data and work together. If these APIs have security flaws, they can affect the safety of the whole cloud system.
- Unique API Vulnerabilities: APIs have their own security issues that traditional security methods might not handle well. This means we need specialized ways to keep APIs safe from attacks.
- Complex Ecosystems: With microservices, numerous interconnected systems communicate through APIs. This gives rise to an array of potential vulnerabilities.
- Threat Exposure: Using lots of APIs means more chances for cyberattacks. Each API endpoint can become a potential entry point for attackers, thus needing better protection.
- Diverse API Implementation: Different people make APIs differently, so not all are equally secure. It’s hard to keep all APIs safe and consistent.
- External Risks: Many companies depend on third-party APIs, introducing external security risks beyond their direct control. These risks can pose a significant threat to your organization.
Step-by-Step Guide to API Security Testing
While different cybersecurity companies follow different ways to conduct security testing, the core procedure remains the same. Here are the steps involved in API security testing:
1. Information Gathering
In the 1st step, the security testers gather as much information about the API environment as possible, either from the company or from publicly available web pages.
2. Planning
The testing company then creates a proper scope and strategy that lists the expectations from the testing process.
3. Automated Scans
Then the testers use automated vulnerability scanners to find as many vulnerabilities present on the surface level of the API.
4. Manual Penetration Testing
This is the step where the security testers use manual testing techniques to go deep within the API structure and find hidden vulnerabilities.
5. Reporting
Then the testers document the vulnerabilities they found, their impact level, and remediation steps, and share them with the company.
6. Remediation
The company then uses the remediation steps provided to fix those security flaws. If needed, the testing team will help the development team with fixing, online or over consultation calls.
7. Retesting
After all the fixing is completed, the testers retest the API to check whether the remediation processes actually worked or not.
8. LoA and Security Certificate
Finally, when all the vulnerabilities are fixed, the testing team issues a letter of attestation (LoA) and a security certificate. This certificate helps with client and compliance needs.
Want to see what a real API security testing report looks like? Just click the link below and download one in a few seconds.
Latest Penetration Testing Report

API Security Testing Requirements and Objectives
When we test API security, we’re making sure that the ways we connect systems and share data are safe from attackers. The main objective of API security testing is to find and fix any weaknesses in the APIs so that hackers can’t use them.
API Security Testing Requirements
- Authorization Checks: Ensure that only authorized users can access the API.
- Input Validation: Validate input data to prevent injection attacks.
- Authentication Mechanisms: Verify the identity of users and systems interacting with the API.
- Data Encryption: Encrypt sensitive information transmitted through the API.
- Error Handling: Implement proper error handling to avoid leaking sensitive information.
- API Tokens: Use tokens for authentication and authorization, and ensure they are securely generated and managed.
- Security Patching: Regularly update and patch API components to address known security vulnerabilities.
- Third-Party Integrations: Assess the security of third-party libraries and services used by the API.
API Security Testing Objectives :
- Identify Weaknesses: Check for areas where hackers could get in and cause harm.
- Protect Data: Ensure that sensitive information shared through APIs is kept safe.
- Prevent Unauthorized Access: Ensure that only authorized users and systems can use the APIs.
- Detect Vulnerabilities: Find any potential weaknesses in the API code or configuration.
- Maintain Compliance: Ensure that the APIs meet security standards and regulations.
- Minimize Risks: Reduce the chances of cyberattacks or data breaches through the APIs.
- Enhance Trust: Build confidence among users and stakeholders by demonstrating robust security measures.
- Continuously Improve Security: Regularly test and update security measures to stay ahead of emerging threats.
7 Types of API Security Testing
API security testing (particularly API penetration testing) is the process of finding, exploiting, and fixing vulnerabilities present in the API before real-world attackers use them for their gain. So, here are 7 types of testing involved in API security:
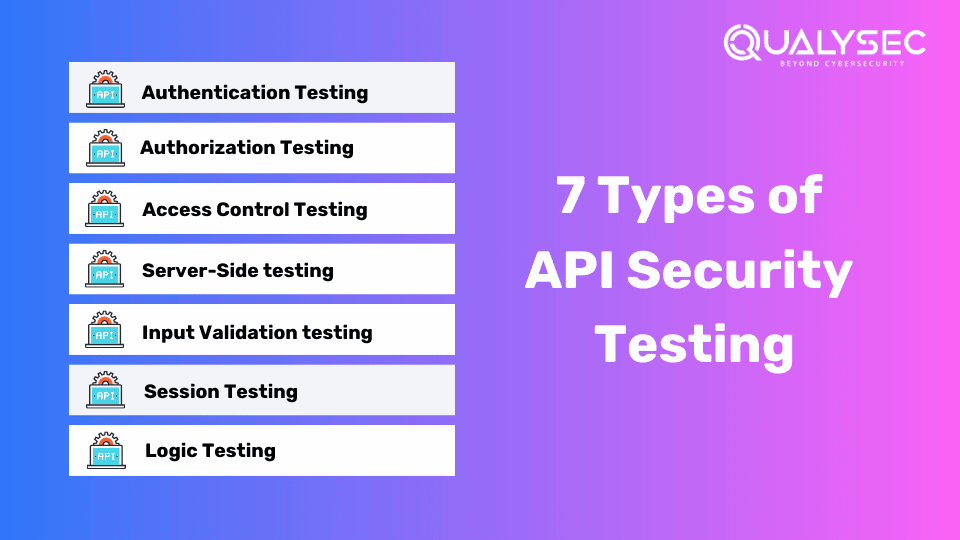
1. Authentication Testing
Verifying that the system accurately recognizes and confirms users’ identities, preventing unauthorized access, and keeping sensitive data safe.
2. Authorization Testing
Ensuring that only users have access to the resources and functionalities they’re allowed to use. It prevents unauthorized actions and safeguards sensitive information.
3. Access Control Testing
Checking that the system properly restricts access to sensitive data and features based on user roles and permissions.
4. Input Validation Testing
Validating that the system properly handles and sanitizes user inputs to prevent security vulnerabilities like injection attacks.
5. Server-Side Testing
Assessing the security of the server components and backend infrastructure to prevent unauthorized access and data breaches.
6. Session Testing
Confirming that user sessions are securely managed and terminated after a period of inactivity to prevent session hijacking.
7. Logic Testing
Verifying that the system’s logic and business rules are implemented correctly to prevent unexpected behaviors and security vulnerabilities.
Want to secure your APIs from cyberattacks? Qualysec Technologies offers hybrid penetration testing services that include all the above-mentioned testing procedures. Secure your APIs and your business from security risks at once. Schedule a meeting now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
APIs are the medium through which applications communicate and share data, streamline development, and integrate business operations. However, these abilities have made them prone to various cyberattacks. API security testing (especially penetration testing) is a critical process that involves identifying and rectifying vulnerabilities within APIs to safeguard against cyber threats.
With cyber threats on the rise and the impact of cyberattacks increasing every year, it is important to find the right API security testing provider. Check whether the testing provider uses manual techniques and offers retesting options, as these are rare but effective steps.
Want to secure your APIs and your business from evolving cyber threats? Choose Qualysec as your security testing partner!
FAQs
Q: What is the API security process?
A: The API security process refers to finding, exploiting, and mitigating vulnerabilities present in an API. Additionally, it is essential to protect the sensitive data present in the API.
Q: How to measure security in API?
A: Measure security in API by conducting penetration testing. This is because API pen testing reveals the weak points in the API architecture that attackers can exploit to gain unauthorized access.
Q: Who conducts API security testing?
A: A cybersecurity company or a third-party penetration testing company performs API security testing. Moreover, they have certified ethical hackers who know all the tools and techniques to find hidden vulnerabilities.
Q: What are the benefits of API security testing?
A: Benefits of API security testing include:
-
- Identification of vulnerabilities
- Improving overall API security posture
- Complying with industry standards
- Building trust among customers and stakeholders
- Maintain market reputation
- Meeting client needs































































































































































































































































































































































































































































































































0 Comments