In today’s digital landscape, websites have become an essential component of any business or organization. They serve as the virtual face, facilitating communication, commerce, and data exchange with users. However, the rise in cyber threats demands stringent security measures to safeguard sensitive information and maintain the trust of users. This is where website penetration testing plays a crucial role. In this blog, we will delve into the significance of website penetration testing and explore its benefits for businesses.
Breaking Down Website Penetration Testing
Website penetration testing, also known as ethical hacking or “pen testing,” is a systematic process of evaluating the security of a website by simulating real-world attacks. It involves a comprehensive examination of the website’s vulnerabilities, weaknesses, and potential entry points for unauthorized access. The goal of penetration testing is to identify security flaws before malicious actors can exploit them, allowing businesses to take proactive measures to protect their website and the data it holds.
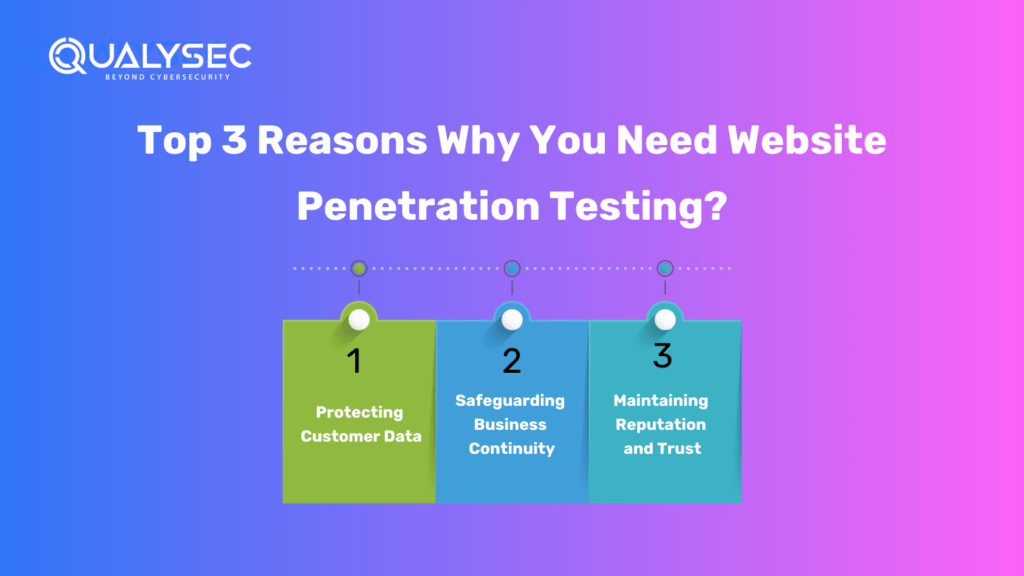
Top 3 Reasons Why You Need Website Penetration Testing?
Reason 1
Protecting Customer Data: Customer data is an asset that businesses must protect. A successful data breach can lead to severe consequences, including financial loss, damage to brand reputation, and loss of customer trust. Website penetration testing helps identify vulnerabilities that could be exploited by hackers to gain unauthorized access to sensitive data.
Reason 2
Safeguarding Business Continuity: A cyber-attack can disrupt the normal functioning of a website, resulting in significant downtime and financial losses. Website penetration testing helps identify vulnerabilities that may lead to service interruptions or denial of service attacks.
Reason 3
Maintaining Reputation and Trust: A security breach can tarnish a business’s reputation and erode the trust of customers. Website penetration testing helps organizations demonstrate their commitment to data security and customer protection. By proactively identifying and mitigating vulnerabilities, businesses can assure their users that their website is secure, and their information is safe. This instills confidence, strengthens brand reputation, and fosters long-term customer trust.
Methodology for Website Penetration Testing
Website penetration testing follows a structured methodology to ensure comprehensive coverage and accurate results. The process typically involves the following steps:
Planning and Reconnaissance
This phase involves gathering information about the target website, such as its infrastructure, technologies used, and potential vulnerabilities. Ethical hackers analyze publicly available information and perform reconnaissance to understand the website’s architecture and potential entry points. This can include conducting passive reconnaissance by searching for information on search engines, social media, and public databases. It also involves active reconnaissance, where testers interact with the website to identify potential vulnerabilities.
Scanning and Enumeration
In this phase, vulnerability scanning tools are utilized to identify weaknesses, misconfigurations, and open ports. These tools, such as Burp Suite and OWASP ZAP, scan the website’s components and perform automated tests to uncover common vulnerabilities. They can identify issues like insecure configurations, outdated software versions, and missing patches. Enumeration techniques are used to gather more detailed information about the target, such as the network structure, services running on the server, and user accounts. This helps testers understand the attack surface and potential entry points.
Exploitation
Once vulnerabilities are identified, ethical hackers attempt to exploit them to gain unauthorized access or escalate privileges. This step validates the severity and impact of the vulnerabilities and helps determine the effectiveness of existing security controls. Tools like Metasploit provide a framework for developing and executing exploit code against target systems. The objective is not to cause harm but to demonstrate the potential impact of a successful attack. By successfully exploiting vulnerabilities, testers can provide concrete evidence of the risks associated with the identified weaknesses.
Post-Exploitation and Reporting
After successful exploitation, ethical hackers document their findings, including the vulnerabilities discovered, their impact, and potential remediation measures. A comprehensive report is prepared, providing detailed recommendations for addressing identified weaknesses. The report includes an executive summary, detailed technical findings, and prioritized recommendations for mitigating risks. Additionally, the report provides guidance on the necessary steps to remediate the identified vulnerabilities and improve the overall security posture.
Website Penetration Testing Tools
Website penetration testing tools aid in automating and streamlining the testing process, enhancing efficiency and accuracy. These tools assist in identifying vulnerabilities, analyzing the security of web applications, and simulating attacks. Here are a few commonly used website penetration testing tools:
| Tool Used | About the Tool |
| Burp Suite | Burp Suite is a widely used web application testing toolkit. It includes features like scanning, intercepting, and modifying web traffic, identifying vulnerabilities, and exploiting them. It offers a user-friendly interface and comprehensive functionalities for testing web applications. |
| OWASP ZAP | OWASP ZAP (Zed Attack Proxy) is an open-source web application security scanner. It helps in finding common vulnerabilities and security issues, such as SQL injection, cross-site scripting (XSS), and insecure direct object references. It provides both automated and manual testing capabilities, allowing testers to customize the scanning process. |
| Nmap | Nmap is a powerful network mapping and scanning tool. It can be used to discover open ports, services running on the server, and potential vulnerabilities. It provides detailed information about the network infrastructure, aiding in vulnerability assessment and identification. |
| Metasploit | Metasploit is a widely used framework for developing and executing exploit code against target systems. It helps in identifying vulnerabilities and verifying their impact. Metasploit offers a vast collection of exploit modules, allowing testers to simulate various attack scenarios. |
It is important to note that while these tools provide automation and efficiency, the expertise of a skilled penetration tester is crucial for effective testing. The tester’s knowledge, experience, and ability to analyze results in-depth are essential for uncovering complex vulnerabilities and providing accurate insights into the security posture of the website. The combination of advanced tools and human expertise ensures a thorough and reliable website penetration testing process.
Website Penetration Testing Checklist
To ensure a thorough and comprehensive website penetration testing process, consider the following checklist:
- Identify the scope of the testing, including the target systems, applications, and infrastructure.
- Conduct proper reconnaissance to gather information about the target website.
- Perform vulnerability scanning to identify weaknesses and misconfigurations.
- Attempt to exploit identified vulnerabilities to assess their severity and impact.
- Test for common web application vulnerabilities, such as SQL injection, cross-site scripting (XSS), and insecure direct object references.
- Assess the effectiveness of authentication and access controls.
- Test for server misconfigurations and insecure file permissions.
- Evaluate the security of APIs and web services, if applicable.
- Assess the effectiveness of encryption and secure communication protocols.
- Validate the incident response capabilities by simulating a real-world attack.
Qualysec, The Best Solution Provider
Qualysec is a cybersecurity company specializing in providing VAPT services to organizations of all sizes. They have a team of highly skilled and certified security professionals who use the latest tools and techniques to identify vulnerabilities in your network and system infrastructure. Their VAPT services include both automated and manual testing, ensuring that all potential vulnerabilities are thoroughly identified.
What sets Qualysec apart from other service providers as they provide Website Penetration Testing along with their unique approach to cybersecurity and cloud security? They don’t just identify vulnerabilities; they provide comprehensive application security to address those vulnerabilities. They work closely with organizations to understand their unique needs.
Qualysec offers various services which include:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
Key Features
- Over 3,000 tests to detect and root out all types of vulnerabilities.
- Capable of detecting business logic errors and gaps in security.-
- Ensures zero false positives through manual pen testing.
- Compliance-specific scans for SOC2, HIPAA, ISO27001, and other relevant standards.
- Provides in-call remediation assistance from security experts
The solutions offered by Qualysec is particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by opting for Qualysec as a cloud security provider, businesses can ensure the safety of their data.
Conclusion
In today’s interconnected world, website security is of paramount importance. By conducting website penetration testing, businesses can proactively identify and address vulnerabilities before malicious actors exploit them. The benefits of penetration testing extend beyond risk mitigation, including improved incident response capabilities, compliance with regulations, and maintaining customer trust. Investing in regular website penetration testing is an essential step toward safeguarding sensitive data, protecting brand reputation, and ensuring long-term business success in the digital age.
There are several types of Website Security Testing Plans, Pen testing Solutions one might need, and vulnerability scanners, including network scanners, host scanners, application scanners, cloud scanners, and wireless scanners. Each with its own set of benefits and use cases. Additionally, both internal and external vulnerability scanners are necessary. These cover all devices and systems that are accessible from within and outside of an organization’s network. We are always ready to help, talk to our Experts and fill out your requirements.
Discover the significance of web application security testing in safeguarding your web applications along with your website here ” Safeguarding Your Web Application: The Importance of Security Testing “.
Frequently Asked Questions
Q. How often should website penetration testing be conducted?
Ans. The frequency of website penetration testing depends on several factors, including the website’s complexity, the criticality of data, and industry regulations. It is recommended to perform regular testing, such as annually or after significant changes or updates to the website.
Q. Can’t we rely on automated vulnerability scanning tools instead?
Ans. While vulnerability scanning tools are useful, they cannot replace the expertise and intuition of a skilled penetration tester. Automated tools can identify known vulnerabilities, but they may miss complex or zero-day vulnerabilities that require manual testing and analysis.
Q. Is website penetration testing legal?
Ans. Website penetration testing is legal when conducted with proper authorization and in adherence to ethical guidelines. It is crucial to obtain written permission from the website owner before conducting any testing to avoid legal issues.
Q. How long does a website penetration test take?
Ans. The duration of a website penetration test depends on various factors, including the website’s complexity, size, and scope of testing. It can range from a few days to several weeks, depending on the project requirements.




























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)
































































































































































































































































































































































































































































































0 Comments