Using payment cards is now normal in most transactions, but fraudsters still choose them as a favorite way to steal information. Payment card data was found to have been the focus of breaches in 25% of the incidents reported by the 2024 Verizon Data Breach Investigations Report. The data concerning risk of cardholder information applies directly to those enterprises that store, process or transmit payment card details. PCI DSS is set up to ensure the safety of this personal information. Agreeing with PCI DSS isn’t limited to fulfilling recommendations made by auditors. You need to follow a scheduled and constant process for identifying and managing risks. To start, a PCI risk assessment is required.
A PCI risk assessment plays a role in protecting organizations:
- Finds out where their Cardholder Data Environment (CDE) is vulnerable.
- Learn about the possible effects and likelihood of every risk.
- Setup a plan to manage those risks before attackers can use them.
Poor attention to this process puts your firm at risk of facing losses, facing legal action, suffering damage to its reputation and being suspended from payment systems.
In this blog, we will look at what’s involved in a PCI risk assessment, walk you through its important steps, help you see its business value and give practical advice for following PCI DSS v4.0 in 2025.
What is a PCI Risk Assessment?
A PCI risk assessment is a planned process that helps companies find, evaluate and order security risks linked to their CDE. As the main part of Requirement 12.2 of PCI DSS, it provides the basis for all security measures with payment card data involved in a system.
It isn’t only meant to realize what risks already exist. Its purpose is to help organizations predict risks, evaluate their influence and plan responses to stop them from causing a data breach.
What Does It Involve?
PCI standard risk assessment includes the following items:
- Mapping the CDE to understand all systems, applications, databases, and users that interact with cardholder data
- Noticing risks and weaknesses that have the potential to harm the confidentiality, integrity or availability of data on payment cards
- Looking at the current security measures to check how much they minimize apparent risks
- Evaluating risk likelihood and impact using a structured model (such as qualitative or quantitative scoring)
- Documenting the risk levels and mitigation plans to ensure accountability and track resolution over time
Why It Differs from General Risk Assessments
General IT risk assessments consider all aspects of information systems, PCI-specific assessments look only at information related to payments. Integration of children’s development with economic development is quite narrow, but very significant. Thanks to this concentrated focus, businesses ensure their efforts meet PCI DSS requirements, while keeping audits clear.
PCI DSS v4.0 requires that organizations must do the following:
- Make sure to perform the assessment at least every year or after significant construction or reconstruction is carried out.
- Please record the steps taken, what was found, planned actions and those assigned.
- Use the outcomes in your routine work processes that deal with risk and compliance.
If a PCI risk assessment model is not followed, this leads to more issues and also makes your organization risk audit failure.
Why Is PCI Risk Assessment Crucial for Businesses?
For any organization that handles cardholder data, a PCI risk assessment is not just a best practice. It is an operational necessity. Without it, businesses risk violating compliance standards, exposing sensitive information, and facing costly disruptions.
Here are the primary reasons PCI risk assessment should be prioritized:
1. Ensures PCI DSS Compliance
PCI DSS Requirement 12.2 makes risk assessment mandatory for all entities that process or store cardholder data. Skipping this step can result in:
- Failed compliance audits
- Financial penalties ranging from $5,000 to $100,000 per month
- Potential restrictions or loss of access to card networks like Visa or Mastercard
A well-documented risk assessment also makes audits faster, smoother, and more defensible.
2. Detects Vulnerabilities Before Attackers Do
An effective PCI risk assessment goes beyond basic scanning. It helps identify vulnerabilities in:
- Unpatched software or outdated systems
- Improper data storage or transmission
- Weak access controls or password policies
- Third-party integrations such as APIs or payment gateways
If these gaps are noticed early, businesses are able to focus on resolving them before new risks appear.
3. Reduces the Financial Impact of a Data Breach
From the most recent Data Breach report, we discover that on average, businesses must pay $4.45 million for a data breach and in retail and finance, those that process card payments suffer losses of over $3 million each time. These charges make up the following amounts:
- Fines from governmental bodies
- Compensating the customers and notifying them
- The process of investigation and forensics
- There will be less money and people won’t trust businesses as much
Evaluating your payment systems through a PCI risk assessment decreases your chance of experiencing a data breach and limits the damages if one occurs.
4. Strengthens Business Continuity and Resilience
By evaluating the systems, you can be sure that backups, recovery systems and security measures are all working properly. Thanks to this approach, you can keep your business running smoothly through security events.
- Minimize downtime
- Quickly cut off systems showing signs of the virus
- Get critical services operating with as little disruption as is possible.
5. Builds Trust with Customers and Partners
Customers and vendors are more likely to work with organizations that can demonstrate strong data protection protocols. Regular PCI risk assessments:
- Show commitment to securing customer data
- Help retain long-term business relationships
- Reduce friction during third-party security evaluations
PCI DSS Risk Assessment Steps
A successful risk assessment focuses on the Cardholder Data Environment’s (CDE) scope and organizational details. These are the top steps needed for doing a PCI risk assessment successfully:
1. Scope Identification
To begin, you need to outline where the assessment is supposed to take place. The purpose is to see every system, network, application, service and endpoint involved in managing or sharing cardholder details.
What to include:
- All payment processing systems
- Databases that connect with each other plus internal application programming interfaces
- Remote access tools that vendors or employees depend on
- Secure your payment data by using backup servers or saving it to the cloud
- Business units interacting with cardholder data
Tip: Misidentifying or underestimating scope is one of the most common causes of non-compliance during audits.
2. Threat Identification
Once the scope is clear, the next step is to assess what could go wrong. Threats may be internal or external, technical or human.
Examples of threats:
- Social engineering or phishing attacks
- Insider misuse of access privileges
- Malware or ransomware targeting payment systems
- Unsecured physical access to servers or terminals
Understanding these threats helps you build a realistic threat model tailored to your environment.
3. Vulnerability Assessment
When risks are identified, the next action is to assess which areas of the system face the highest risk.
Techniques used:
- Vulnerability scanning
- When someone manually runs penetration tests.
- Evaluating code security
- Testing and audit of firewalls, computers and network equipment
QualySec team uses OWASP Top 10, SANS Top 25 and known CVEs to lead their analysis. It allows for the identification of often used weaknesses so they are fixed ahead of possible abuse.
4. Risk Rating and Prioritization
Experts rate every risk by considering how much it could impact the organization if it is used by attackers.
Factors to consider:
- Is the vulnerability publicly known or zero-day?
- Has it been previously exploited within your industry?
- How severe would the outcome be if exploited?
By sorting risks as low, medium, high or critical on a risk matrix, security teams can decide on the best action and use their time wisely.
5. Mitigation and Control Planning
Once the risks are rated, develop a remediation plan that addresses each one with the appropriate control.
Examples of mitigation strategies:
- Encrypting cardholder data in transit and at rest
- Implementing multi factor authentication for all system access
- Segregating network zones to isolate sensitive systems
- Updating or patching vulnerable software
- Educating employees on phishing and social engineering risks
Each mitigation strategy should have a timeline, responsible team, and defined outcome.
6. Ongoing Monitoring and Documentation
A PCI risk assessment is not a one-time event. Organizations must:
- Regularly revisit their assessments
- Update risk profiles after significant infrastructure changes
- Document each step of the assessment, including identified risks and how they were mitigated
Maintaining clear documentation not only prepares you for compliance audits but also builds accountability across teams.
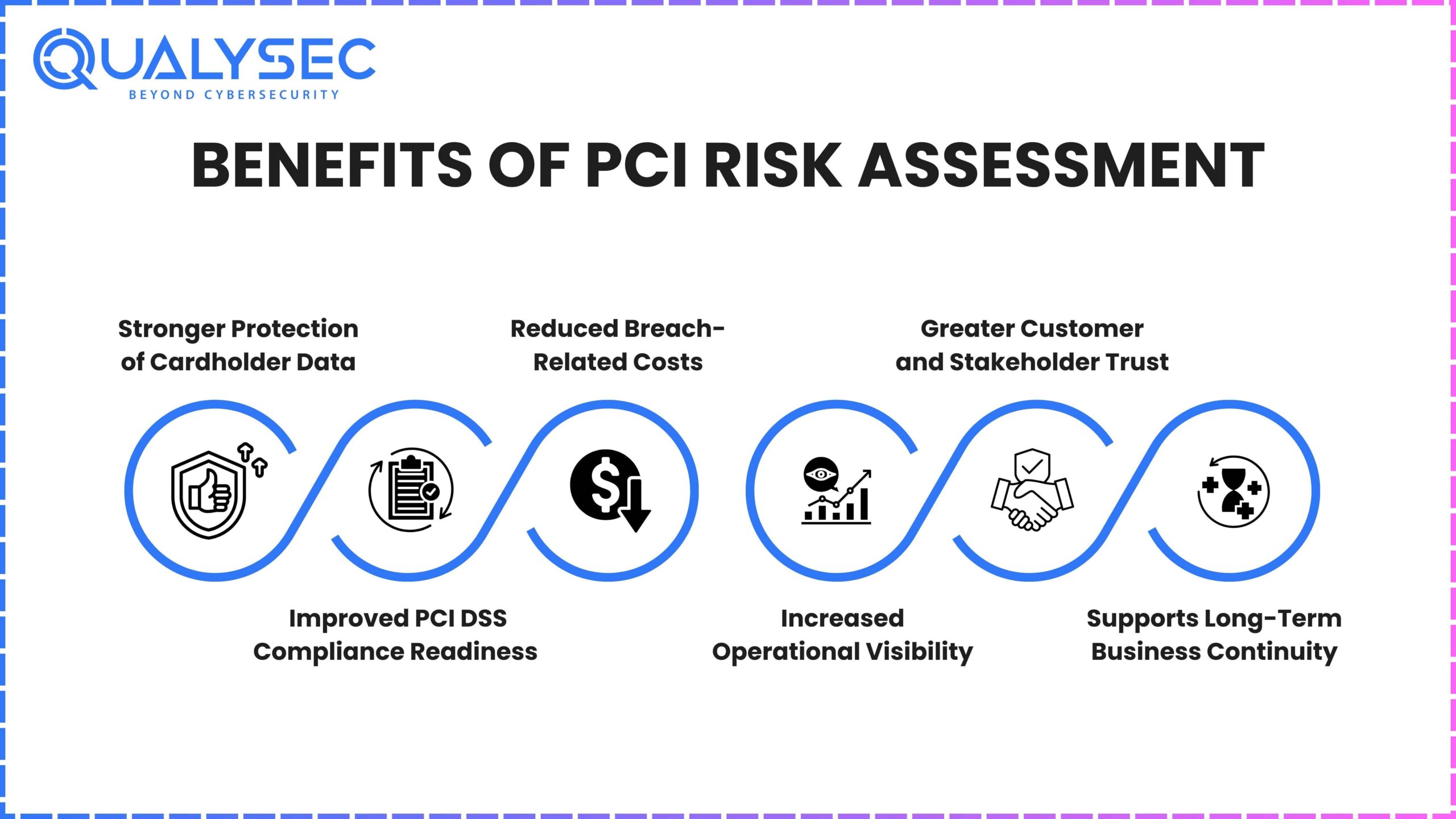
Benefits of PCI Risk Assessment
Performing a PCI risk assessment is more than simply reaching compliance obligations. Doing this strengthens both your company’s security and its ability to continue working smoothly.
Here are the key benefits:
1. Stronger Protection of Cardholder Data
A PCI risk assessment is valuable because it keeps sensitive data safe. When you fix issues in your systems, you make it less likely that unauthorized access, data stealing or service disruptions will occur.
Outcome: Fewer attack surfaces, stronger encryption protocols, and more secure data flows across systems.
2. Improved PCI DSS Compliance Readiness
All organizations processing card payments must do risk assessments, as directed by PCI DSS. Doing them systematically guarantees the stability of your business.
- Be ready for any audit at any time.
- Meets required time frames from regulators
- Can quickly respond to auditor requests with documented proof
Outcome: Faster audits and lower chances of fines or penalties.
3. Reduced Breach-Related Costs
Being proactive about risk management helps avoid the financial consequences of a breach. According to industry reports, the cost of a data breach in the financial sector can exceed $3 million per incident.
Outcome: Reduced likelihood of incidents and minimized recovery costs if a breach does occur.
4. Increased Operational Visibility
A risk assessment requires mapping out your entire Cardholder Data Environment. This improves your understanding of how payment data flows through your business and where the weak points are.
Outcome: Better visibility into systems, processes, and third-party dependencies.
5. Greater Customer and Stakeholder Trust
Clients and business partners are more confident in companies that take data protection seriously. Using a planned method for risk management proves that your organization values security and compliance.
Result: Customers remain loyal and partners get stronger in their relationship.
6. Supports Long-Term Business Continuity
Making risk awareness part of your systems, policies and team jobs helps you handle emergency situations better. If a security event happens, stepping in is much easier since your systems are organized.
Outcome:Decreased downtime and better ability to handle business disruptions.
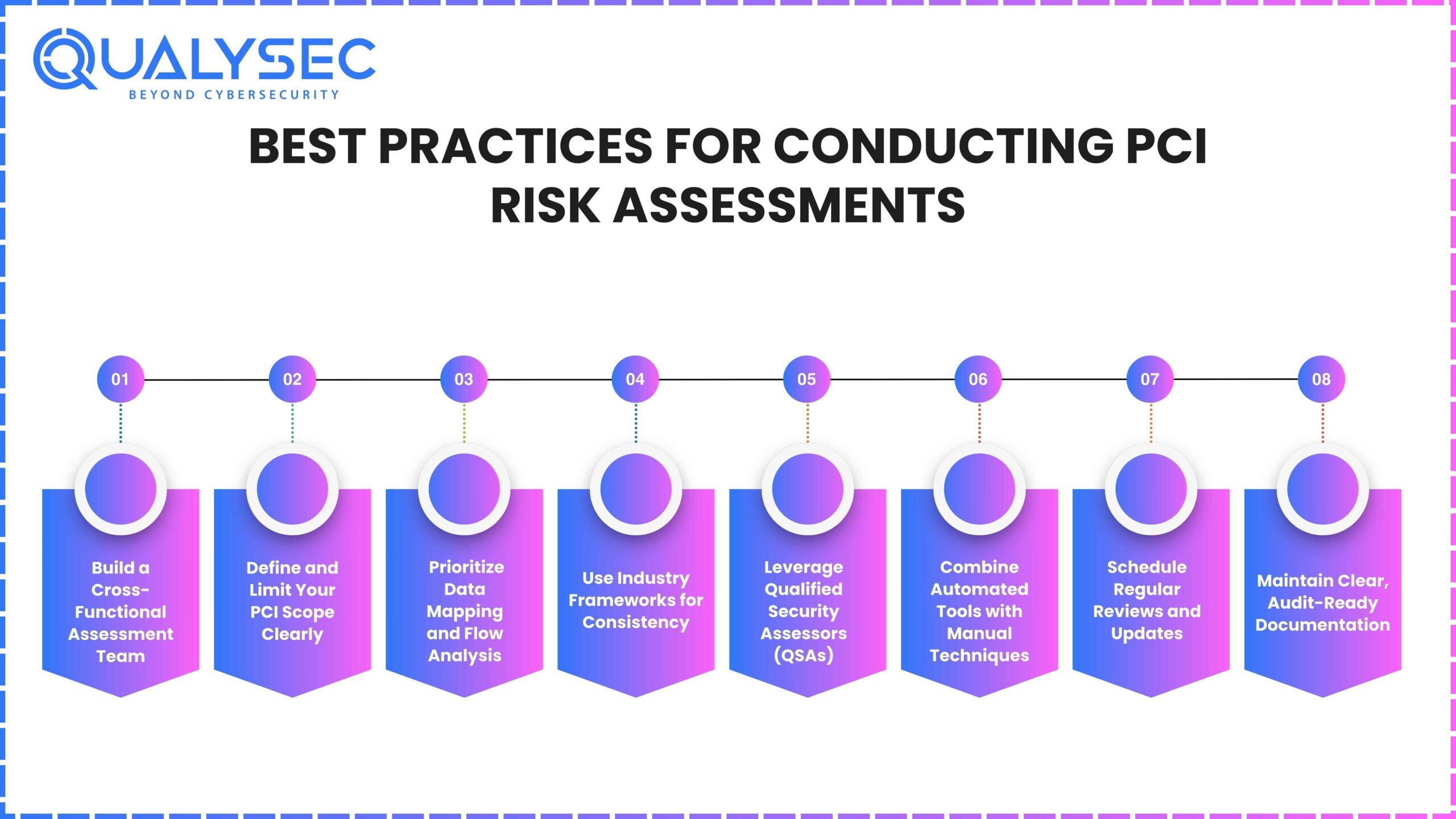
Best Practices for Conducting PCI Risk Assessments
Having a practical plan, instead of strict policy, makes conducting a PCI risk assessment much more effective. The following guidelines ensure your assessments are accurate, fast and suitable for an audit.
1. Build a Cross-Functional Assessment Team
Bring together representatives from security, IT, compliance, development, operations, and business units. All departments have individual knowledge of how cardholder information is managed and what could go wrong.
Why this is important: With a siloed view, important risks in business workflows or linked to third parties may be missed.
2. Define and Limit Your PCI Scope Clearly
Your first step should be to identify where and how your Cardholder Data Environment (CDE) is found. These include any systems that either hold, use or move cardholder data, as well as those that might change its security.
A good approach: Use data flow diagrams to visualize the movement of payment data within applications, networks and to vendors.
3. Prioritize Data Mapping and Flow Analysis
Knowing how cardholder data moves across your infrastructure helps uncover hidden vulnerabilities in systems like APIs, backup servers, third-party integrations, and legacy databases.
Action tip: Document each interaction point and label it based on sensitivity, access level, and encryption status.
4. Use Industry Frameworks for Consistency
Although PCI DSS sets the main guidelines, using frameworks like NIST SP 800-30, ISO 27005 or OWASP Risk Rating Methodology gives you a better way to look at possible threats.
Why it works: These models offer mature approaches to scoring risks based on likelihood and business impact.
5. Leverage Qualified Security Assessors (QSAs)
Working with PCI-certified QSAs like the specialists at QualySec ensures:
- Risk assessment methodology aligns with PCI DSS expectations
- Your findings hold up during official audits
- Vulnerabilities are interpreted through the lens of real-world exploitability
6. Combine Automated Tools with Manual Techniques
Automated scanners can flag known CVEs or outdated software. However, manual techniques such as logic testing, source code review, and scenario-based penetration testing uncover deeper flaws that machines may miss.
Tip: Prioritize hybrid testing approaches to cover all attack vectors.
7. Schedule Regular Reviews and Updates
CI DSS v4.0 requires all organizations to carry out annual risk assessments or when significant new infrastructure is added. Look at security as something you always work on rather than doing it only as a yearly obligation.
Include: Update your documentation, recheck your controls and update your training.
8. Maintain Clear, Audit-Ready Documentation
Every risk assessment should produce a report that includes:
- Scope definition
- Threat and vulnerability list
- Risk ratings
- Mitigation strategies
- Responsible owners and deadlines
This documentation proves due diligence and speeds up PCI audits.
Latest Penetration Testing Report

Common Mistakes to Avoid
Even well-intentioned risk assessments can fall short if they are rushed, mis-scoped, or poorly documented. Mistakes organizations commonly make during PCI risk assessments and the ways to prevent them are detailed below:
1. Unclear or Incomplete Scope Definition
Failing to properly define the Cardholder Data Environment (CDE) often results in systems or processes being excluded from the assessment.
What this causes:
- Missed vulnerabilities
- Inaccurate compliance status
- Potential audit failures
Fix: Map out all systems that store, process, transmit, or have access to cardholder data. Include third-party services and cloud assets.
2. Using Outdated System Inventories or Data Flows
Many organizations rely on outdated asset lists or forget to update data flow diagrams after changes in infrastructure.
What this causes:
- Blind spots in security assessments
- Ineffective controls
- Incomplete risk treatment plans
Fix: Maintain current inventories and validate data flow maps before each assessment cycle.
3. Treating It as a One-Time Task
Some businesses conduct a risk assessment once per year and do not revisit it until the next audit.
What this causes:
- Missed emerging threats
- Lack of visibility into new systems
- Delayed risk mitigation
Fix: Conduct risk assessments regularly and after significant changes in systems, vendors, or architecture.
4. Over-Relying on Automated Scans
Automated tools are useful for identifying known vulnerabilities, but they cannot detect all security gaps.
What this causes:
- Missed logical flaws or access control weaknesses
- Overlooked configuration errors
- Incomplete risk profile
Fix: Supplement automated scans with manual testing and expert validation.
5. Lack of Executive Involvement
When senior management is not engaged, security initiatives may lose support or fail to gain priority.
What this causes:
- Budget constraints for remediation
- Limited enforcement of security controls
- Poor visibility into business risk
Fix: Involve executives early. Present security risks in terms of business impact such as cost, downtime, and compliance penalties.
6. Poor Documentation and Tracking
Without proper documentation, even a thorough risk assessment can lose effectiveness over time.
What this causes:
- Missed follow-up actions
- Incomplete audit trails
- Reduced accountability
Fix: Maintain clear reports, assign remediation tasks with deadlines, and track closure of identified risks.
How QualySec Helps with PCI Risk Assessment
QualySec simplifies the PCI risk assessment process by offering a structured, compliance-ready approach tailored to your business needs. Here’s how:
- PCI-Aligned Methodology: Each assessment is mapped to PCI DSS v4.0 requirements, covering scope definition, threat analysis, risk scoring, and mitigation planning.
- Manual + Automated Testing: Combines scanner-based checks with expert-led manual testing to uncover deep security gaps and eliminate false positives.
- Clear, Actionable Reports: Delivers prioritized risks, technical insights, and executive summaries to guide both IT teams and business leaders.
- Remediation Support & Retesting: Helps validate fixes, suggest compensating controls, and prepare you for audits.
- Cross-Industry Expertise: Supports fintech, ecommerce, SaaS, and healthcare companies with assessments tailored to their infrastructure.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
PCI risk assessment only as a routine does not serve its purpose. It helps you look for weaknesses in your system, reduces the chance of data breaches and lets you meet PCI DSS requirements without worry.
Evaluating your Cardholder Data Environment, choosing to prevent mostly likely threats and following PCI DSS v4.0 guidance saves your business from penalties and helps it grow and remain trustworthy.
If you aren’t sure if your systems comply with PCI or need advice on getting started, our experts will assist you.
Schedule a free consultation with QualySec to understand your risks, get tailored recommendations, and access a sample PCI pentest report to see how we work.
Start protecting your payment infrastructure today with a partner that understands both compliance and real-world security.
























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments