Because of the extremely rapid development of the digital environment, cybersecurity has become an important concern for companies of any size. With the frequency and sophistication, the frequency of these cyber threats, organizations must ensure the security of their digital assets. For this, one of the best ways to achieve it is Vulnerability Assessment and Penetration Testing (VAPT). It consists of this comprehensive testing approach that can be used to identify, analyze, and mitigate security vulnerabilities in an organization’s IT infrastructure. Today, let’s go through the concept of the VAPT penetration test, how important it is, how it works, and how Qualysec Technologies can help businesses ensure robust cybersecurity.
Understanding the VAPT Penetration Test
VAPT stands for Vulnerability Assessment and Penetration Testing. Although commonly used in the same context, these two processes have separate purposes in the world of cybersecurity. VAPT is a consortium that offers a complete evaluation of an organization’s security posture, a combination of automated tools, and manual testing techniques.
- Vulnerability Assessment (VA): A systematic review of security weaknesses in an information system. However, it does not exploit the identified and quantified vulnerabilities.
- Penetration Testing (PT): It runs the type of real-world attacks, exploits vulnerabilities, and measures the possible effects of a security breach.
Why is the VAPT Penetration Test Essential?
Identification of Vulnerabilities
The first stage to secure any system is identifying the potential vulnerabilities. A VAPT penetration test is a test performed to imitate real-life cyber attacks by penetrating weaknesses in the system, application, or network infrastructure. Such a proactive approach therefore aids the discovery of vulnerabilities that would have gone unnoticed through regular security testing. Vulnerabilities in software applications (and web servers), and network configurations, count, and they need to be detected before attackers find them first.
Risk Management and Mitigation
VAPT helps organizations prioritize their remediation efforts once the vulnerabilities are identified and the risk these vulnerabilities carry to the business. However, a vulnerability in a critical system is not necessarily equal to the value of a vulnerability in the other system, although the latter may have more severe consequences than the former. VAPT allows security teams to prioritize the vulnerabilities, that need attention urgently, and those that can be addressed gradually.
Such a security risk-based approach complicates cybersecurity risk management in an organization by directing them towards areas that need immediate remedy and reducing the chances of a security breach. This is a strategic approach to reducing attack surface by diminishing availability to high-risk vulnerabilities and securing high-priority information and assets.
Compliance and Regulatory Requirements
There are for instance healthcare organizations, banks, and other finance organizations, and government regimens that need to follow standards such as the HIPAA, PCI-DS, and GDPR. These regulations often call for exhaustive security compliance, including vulnerability assessment and penetration testing, so that the sensitive data is not subject to anyone’s unauthorized access.
Penetration testing is important for businesses to meet these regulatory requirements, avoid hefty fines, and also to provide a decent reputation to the businesses with clients and stakeholders. Regular VAPT services, on the other hand, show the organization’s dedication to cybersecurity, and also to follow industry standards.
Protection of Reputation and Customer Trust
Loss of customer trust, financial losses, and legal consequences are some of the major downsides of an organization being breached. Companies must protect the personal and financial data of customers. Customers are harmed by a breach, and a breach can be bad for business, in the long term, by damaging an organization’s brand.
Penetration tests conducted regularly by an organization indicate that it is a serious player in cyber security. This indicates that they are taking the right steps to protect sensitive information, formulating a trusting relationship with the customers, and minimizing the risk of a data breach.
Proactive Security Strategy
Attacks are becoming much harder to prevent; new techniques to get around traditional security are thus being developed by attackers constantly. The ability to. buffer security measures until an attack occurs is no longer acceptable. Instead, organizations must adopt a proactive way to be proactive against cybercriminals.
Penetration testing is a part of a proactive security strategy. Organizations like to test their systems, networks, and applications continuously to keep ahead of new threats that could arise and fix them promptly before anyone can implement attacks. One of the ways to reduce the incidence of cyber-attacks and to make it less likely for attackers to succeed.
Enhanced Security Awareness and Training
The benefit of VAPT testing is not only to find out about and fix vulnerabilities, but it is also educational. Penetration tests help give security teams and employees a better handle on what cybercriminals use to attack. This knowledge shows that their defense strategies are better and that they should keep cybersecurity practices like strong password management, awareness of phishing attempts, and secure coding practices. Pen testing can also be used as a great training tool to help organizations identify the gaps in internal security policies and processes to strengthen an organization’s posture.
VAPT Penetration Test Key Components
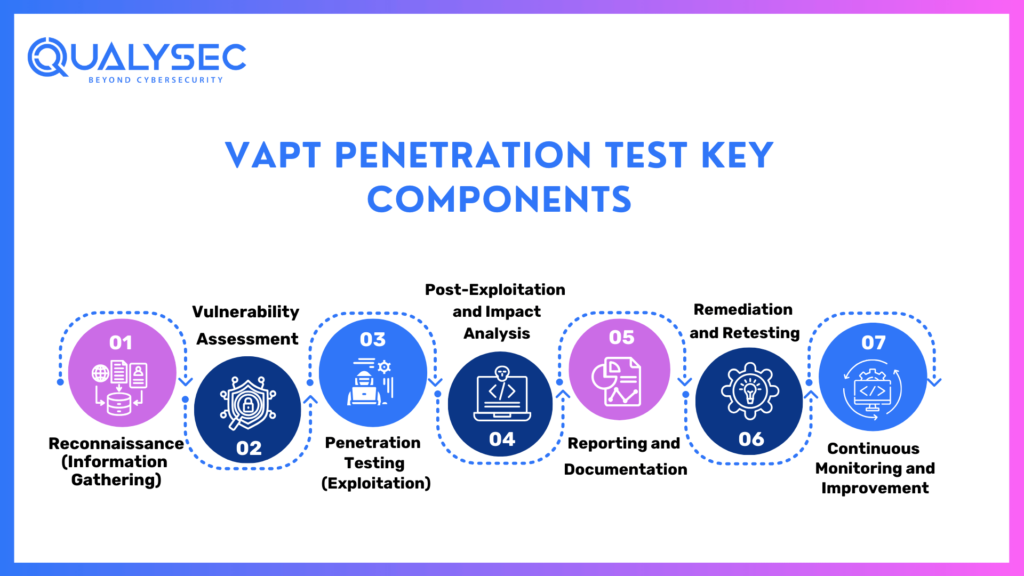
Reconnaissance (Information Gathering)
The first penetration test is the reconnaissance, also known as information gathering. In this phase, information that pertains to the target organization and its systems. One wants to learn as much as possible, without actually working with the target system. Such domains could include domain names, email addresses, network topographies through websites, social media DNS queries, etc.
Nevertheless, there are two types of reconnaissance.
- Active Reconnaissance – Engaging with the target without leaving any traces is the main requirement for the attacker to perform active reconnaissance.
- Passive Reconnaissance – This is Active Reconnaissance, where the tester becomes active with the target network or system by actively interacting with it to retrieve more specific details like open ports or available services.
Vulnerability Assessment
After getting information, we then determine what the vulnerabilities in the target systems are. Vulnerability assessment tools allow scanning of the network, applications, and infrastructure for existing security flaws, misconfigurations, outdated software, weak access control,s or just exploitable weaknesses. This is done mostly by automated tools, but the importance of people skilled in interpreting and reviewing the findings is crucial because these tools will detect only the simple vulnerabilities and may not catch the complex vulnerabilities that may be exploited.
In this phase, all the common vulnerabilities like SQL injection, SSXSS, etc. are identified with operating systems, web servers, and critical infrastructure weaknesses as well.
Penetration Testing (Exploitation)
The second part of VAPT is penetration testing. In this phase, the tester tries to break engaged vulnerabilities and assess how much damage an attacker can inflict if he succeeds with the penetration of the system. All of this is done in a controlled environment with the same attack scenarios as the organization runs in the real world and avoids real damage to the organization’s systems.
Tools and techniques used by penetration testers include simulating attacks on SQL injections, brute force attackers of passwords, etc. The question is if an attacker would be able to penetrate this far enough to penetrate this deep what assets would be compromised and how far would this attacker be able to escalate their privileges within the network?
Post-Exploitation and Impact Analysis
Once through the vulnerabilities, penetration testers measure the effect of the attack. The post-exploitation phase helps to understand the repercussions on the system if the exploit is used. That could be accessing sensitive data, running this in escalated privilege or even moving laterally from one network to another to get to other systems.
At this stage, testers evaluate the potential risks and consequences that would take place should the breach succeed. It is the analysis that allows businesses to understand the whole picture of the damage that could be caused and hence come out with more appropriate mitigation strategies.
Reporting and Documentation
The creation of a detailed report is the next key component of VAPT after testing is complete. The following summarizes the results of the vulnerability management software phases of the report as well as how they are detailed in the report.
- A list of vulnerabilities identified
- Exploits successfully executed
- The potential risks and impact of each vulnerability
- Recommendations for remediation or mitigation strategies
The report should be simple, smart, and operational. It acts as a planning document for IT and security teams to establish which fixes are most important and what can and should be done to enhance security efforts.
Remediation and Retesting
Organizations tend to concentrate on fixing vulnerabilities that were discovered in the test report. This may include the application of patches, closing of open ports, changing of weak configurations, or a change of the security policies.
After remediation is done, a retest of the fixes is made to determine that the measures were effective and no further vulnerabilities were introduced. This phase would make sure that the systems are secure as well as that any previously discovered vulnerability scanning software has been properly mitigated.
Continuous Monitoring and Improvement
VAPT report is not a one-time process. However, security in an organization always needs to be re-evaluated and monitored continuously because technology changes threats evolve, and new vulnerabilities arise. Penetration testing is performed regularly to test that defenses are strong and to test that none of the new attack vectors have been removed from the systems. However, this ongoing process is of particular significance to organizations as it allows them to stay up to date with suspected threats and continue to remain reliant, generally.
Latest Penetration Testing Report

How Qualysec Technologies Can Help in the VAPT Penetration Test
With constant changes in cyber threats, companies need all-inclusive solutions that can detect and resolve system, applications, and network vulnerabilities. Among all those, Qualysec Technologies is a prominent name when it comes to providing advanced Vulnerability Assessment and Penetration Testing (VAPT) services to border organizations regarding securing their digital assets. With Qualysec technologies rendering services for VAPT in cyber security, it can help you better your cybersecurity posture.
Expert Vulnerability Assessment and Risk Identification
Qualysec Technologies does a thorough vulnerability assessment, and that’s done via both automated and manual techniques to see if there are any potential security weaknesses. Experienced cybersecurity professionals on their team make the cyberattacks look real so that they can identify vulnerabilities that attackers would be likely to exploit. In Qualysec, nothing is left untouched – outdated software, misconfigurations, as well as weak access controls are all covered. This allows businesses to conduct proactive security of their environment, thus minimizing the risk of cyber attacks.
Comprehensive Penetration Testing Services
While Qualysec specializes in simulated penetration tests that replicate the techniques employed by hackers, it also provides retailers with services such as voluntary testing at POS systems, secure wipes, and point-of-sale system risk mitigation. The penetration tests that they focus on are all critical parts of the network infrastructure, web applications, mobile apps, and APIs. Qualysec can leverage its latest penetration testing tools and techniques to find and exploit vulnerabilities to find out how deep a penetration an attacker might need to achieve in your system. It is a hands-on approach that helps understand the whole gap in the business’s security and allows them to have a chance of strengthening the defenses all along.
Customized Solutions for Different Business Needs
There is no common security need for every organization. VAPT services provided by QualySec Technologies are tailored to the unique requirements of healthcare, finance, or any other sector. Flexible testing methodologies are offered, the delivery of which helps extend the penetration testing process to an organization’s environment, applicable regulatory standards, and associated risk tolerance. It is also a personalized process so that businesses get the most relevant insights as to their offline security posture.
Detailed Reporting and Remediation Guidance
Qualysec Technologies completes a penetration test and prepares a detailed report including the discovered vulnerabilities, and the impact of these vulnerabilities, addressing the remediation strategies that need to be exploited. The report is aimed to assist IT and security teams with prioritizing fixes by identifying the highest risk values and consequently reducing the risk of exposure. The actionable guidance provided here will allow an organization to quickly work to patch the vulnerabilities and reduce the probability of being attacked.
Continuous Support and Security Awareness
Pen testing is a never-ending process. New vulnerabilities arise with each software patch and whether or not you made a new modification to a system. Qualysec provides continued support to keep your business safe from current threats. Additionally, they supply training and security awareness programs to help employees know the best cybersecurity practices and from that, decrease the chances of human errors that can lead to security breaches.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
A good cybersecurity strategy includes the VAPT penetration test. It can help organizations determine the vulnerabilities, the impact, and how to put in place the necessary steps to handle such risks. It is important to constantly undertake regular VAPT testing as cyber threats become more and more sophisticated and when you have digital assets to safeguard or assets. Get in touch with Qualysec Technologies to achieve a strong cyber security posture using complete VAPT and penetration testing services. It is high time that you contacted us and if you haven’t, do so now to safeguard your business against ever-changing cyber threats!
































































































































































































































































































































































































































































































































0 Comments