API security testing comprises a detailed analysis of API endpoints to identify vulnerabilities such as those arising from fuzzy input, parameter tampering, or injection attacks. As the first line of defense, it examines the endpoints minutely to discover, resist, and fix any vulnerabilities before they are exploited by an attacker.
API security comes from a trinity of considerable importance: Regular Testing, API Threat Protection, and API access control, all with their own respective weaknesses and methods of testing.
Regular API security testing is crucial to protecting data from leaks, maintaining data integrity, and improving overall security posture. Before we discuss the procedure, let’s examine the specific vulnerabilities it helps you pinpoint.
Common Vulnerabilities Found in Various API Types
Here are some of the common vulnerabilities found in different API types:
1. REST APIs
REST APIs or RESTful APIs are stateless APIs that use simple HTTP requests to access and use data. It is one of the most used types of API due to its simplicity and flexibility of implementation in any language.
Common Vulnerabilities Found in REST APIs:
- Injection Attacks: Attackers insert malicious code into the requests to manipulate the APIs’ intended behavior. SQL Injection, Host-Header Injection, and Command Injection are some of the most common attacks.
- Session Management Issues: Inadequate Session Management issues can lead to Authorization vulnerabilities.
- For example, BIG-iP was recently affected by a session management vulnerability (CVE-2024-22389) in which deleted or updated API tokens could still be used on peer devices until they expire.
2. SOAP APIs
SOAP, or Simple Object Access Protocol, uses XML-based messaging to transfer data between the client and server. It is preferred when operations require repetitive or chained tasks as it is a stateful API that stores the information on the server.
Common Vulnerabilities Found in SOAP APIs:
- WSDL Exposure: If the WSDL file is exposed to the attacker’s insight, it provides him with detailed information on the API structure and operations. This, in turn, allows them to craft more targeted attacks.
- Cross-Site Request Forgery: Poor CSRF protection can lead to attacks via CSRF, thus granting attackers access to direct users to perform adopting the actions of their choice.
For example, the vulnerabilities present in the API of Cisco Expressway Series devices allow unauthenticated users to exploit CSRF on the affected components.
3. GraphQL
GraphQL is a flexible and efficient query language for APIs. It allows the client side to request the exact amount of data required to reduce data over- and underfetching.
Common Vulnerabilities Found in GraphQL APIs:
- Injection Attacks: Like REST, GraphQL APIs are also vulnerable to injection attacks, in which attackers insert malicious code into the requests to manipulate the APIs’ intended behavior.
- Introspection Attack: Generally speaking, GraphQL instances have the introspection system enabled by default, which allows the client to query the GraphQL schema in order to get information about it.
For example, in SuiteCRM, GraphQL introspection was enabled without authentication, allowing the attackers to understand the entire attack surface, including fields like UserHash.
4. JSON-RPC and XML-RPC
While offering related functionality through either JSON or XML, of itself is not an RPC remote call protocol-designed to deliver requests from a client to a server-it conveys an által command to the request a server running an RPC architecture and receives an HTTP response.
Common Vulnerabilities in JSON and XML RPC:
- Brute Force Attacks: This method involves trying numerous combinations of user credentials to gain unauthorized access. XML-RPC can be easily used as an entry point for attacks, and it can rapidly execute multiple login attempts, causing brute-force attacks.
- Remote code execution: attackers can execute bad code on the server from a remote connection.
For instance, in Snapcast, an attacker could obtain remote code execution by exploiting the functionality of Snapcast and creating a new stream using the JSON-RPC API.
Why Do You Need API Security Testing?
Maintaining API security is very important to sustain the security posture of your website and, subsequently, your organization. Here are some of the primary reasons why maintaining API security testing is a must:
1. Protection of Sensitive Data:
API vulnerabilities can reveal sensitive data like customers’ information, financial details, or intellectual property. Regular testing can help identify these flaws and rectify them before any kind of data breaches or leaks take place.
This protects data integrity and avoids potential reputational damage and the loss of customer trust.
2. Ensuring Service Availability:
Malicious actors can exploit vulnerabilities in the implementation of APIs in order to initiate DoS attacks, which is an attack that overwhelms the APIs and makes them unavailable to legitimate users.
Robust API penetration testing tools are excellent in exposing such weaknesses so that the organization is enabled to take measures for the elimination of the threats.
3. Maintaining Compliance:
Malicious actors can exploit vulnerabilities in the implementation of APIs in order to initiate DoS attacks, which is an attack that overwhelms the APIs and makes them unavailable to legitimate users.
Robust API penetration testing tools are excellent in exposing such weaknesses so that the organization is enabled to take measures for the elimination of the threats.
4. Improving Stakeholder Trust:
The fact that customers and partners trusted you with their data during API interactions establishes an opportunity for you to showcase your commitment through regular security testing to validate your data protection efforts, thereby building business relationships and generating customer trust in your services.
How to Perform API Security Testing?
Here is the detailed process on how to perform API security testing:
1. Planning and Scope Definition
Identify the APIs that require testing for security vulnerabilities. This includes determining the exact scope of testing, knowledge of the APIs and their functionalities, and knowledge of the data flow, as well as the identification of suitable tools to be utilized.
2. Vulnerability Assessment
This step is basically about the combination of the automated and manual techniques we can engage in order to pinpoint the severe faults and misconfigurations in our APIs under test. This includes the following processes:
a. API Input Fuzzing
Fuzzing means providing the API with random or unexpected data to the API to uncover vulnerabilities, if any. This can be done in various ways.
For numerical inputs, we can provide the API with large numbers, negative numbers, or even 0 to try to extract any information or view the error messages. Similarly, we can try adding SQL queries, system commands, or random special characters for string inputs.
We can make use of FuzzAPI in order to automate the whole process.
Step 1: Download and install Fuzzapi. Read this to know how to do that.
Step 2: After installing Fuzzapi, open your browser and navigate to localhost:3000. You will see something like the image below.
Step 3: Enter the URL you wish to scan in the field labeled URL. Pick your method from the drop-down menu. Optionally, enter in the Raw Headers and Parameters field. Otherwise, let them blank. Finally, click on the Scan button.
Step 4: Wait while the test continues. Once done, if the API is vulnerable, the final results will be shown in the image below.
b. Testing for API Injection Attacks
1. SQL Injection
SQLi attacks are successful when the database processes the unsanitized API input. Thus, testing your REST API for any SQLi bugs is important. Try providing SQL commands in the input like:
‘or 1=1–
“and 1=1–
If the API has an error based and/or is vulnerable to SQLi, it’s possible to add values within those parameters and successfully bypass restrictions when returning with 200.
www.xyz.com/api/auth-token/user=admin’or 1=1–
When the API suffers from a potential SQLi weakness but doesn’t necessarily follow by error based or being weak/SQLi sensitive, this usually means there can still be produced DBMS errors found within a given message as returning a 500 Internal Error shown below within Figure.
2. Command Injection
This allows various OS commands to inject API inputs, which can then be executed on the server. However, commands for different operating systems (Windows, Linux, etc.) would differ.
For example, a Linux system might allow the command “rm /” to remove the whole root directory. When encoded as part of the URL, this looks like rm%20/.
So, for example, if an API is being used to view a site’s contents, then malicious code can be executed as follows:
The semi-colon after the file.txt ends the input parameter and executes the OS command. However, be careful with this command because it can delete the entire directory. Try something a little less harmful, like:
However, if you wish to automatize the process, try using Commix.
c. Authorization and Authentication Attacks
Broken Authentication attacks occur through weaknesses in the authentication mechanisms, like ill-configurations, weak passwords, policies, or poor session management, for unauthorized access.
For instance, attackers can carry out Brute Force attacks, beginning with the discovery of the login endpoint.
POST /api/login
{
“username”: “admin”,
“password”: “admin123”
}
After which, a Brute Force tool like Burp Suite or Hydra can be applied to perform and set up.
d. Discovering Zombie APIs
Zombie APIs are the old or unused APIs that are still active but not updated or maintained. Since they are not maintained, zombie APIs can cause security risks and can be exploited for vulnerabilities.
To identify these Zombie APIs, you can perform an extensive scan of the API inventory to look for older and unmaintained APIs.
e. Unhandled HTTP Methods and Parameter Tampering
Web applications that communicate through API often use several HTTP methods to save, remove, or retrieve data. If a server does not support an HTTP method, it should typically show an error.
However, this is not always the case, especially for vulnerable APIs.
To test for such vulnerability, make a HEAD request to your API endpoint, which requires authentication. Using Python, add the following code to a Python script and run it:
import requests
x = requests.head(‘API-URL’)
print(x.headers)
Replace API-URL with the one you want to test.
3. Exploitation
This is a critical validation point in this phase; all the findings from the vulnerability assessment phase are meticulously leveraged and exploited to assess their potential impact, exploitability, and possible attack vectors.
Important tools used during this phase:
- Postman
- Burp Suite
- Zap
4. Reporting and Remediation
After successfully exploiting all the vulnerabilities, collect all the findings and prepare a detailed report on them, including their severity, steps to reproduce them, and, most importantly, recommendations for remediation.
Latest Penetration Testing Report

API Security Checklist
Below is the API security checklist:
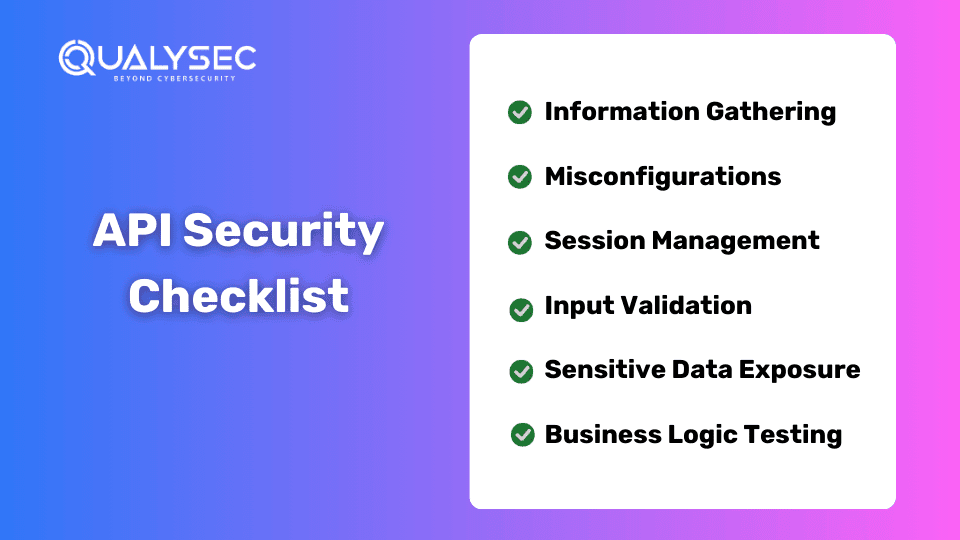
Information Gathering
- Identify API type. (REST, SOAP, GraphQL, etc.)
- List API endpoints
- Identify the HTTP methods
- Catalog must have headers and cookies
- Review of API resources and data flows
Misconfigurations
- Test error handling configurations.
- Test default configurations.
- Test Web Application Firewall rules.
- Test for open ports or unused services
Session Management
- Test session token generation and expiration.
- Test for cookies for correct security flags.
- Test for session hijacking vulnerabilities.
- Test for session fixation.
Input Validation
- Test for Injection attacks.
- Test for file inclusion attacks.
- Test output encoding in responses
- Test for file upload vulnerabilities
Sensitive Data Exposure
- Test for sensitive data in responses
- Test for excessive data in responses
- Test for encryption of data in transit (HTTPS)
- Test for secure encryption protocols
Business Logic Testing
- Test for flaws in logic of data flow and processes
- Test for validation in the proper process
- Test for unauthorized action by modifying parameters.
Conclusion
API security is one of the most important factors in helping you protect sensitive data and the integrity of the applications. A well-guided and planned test following each step is the key to a successful penetration test that can help uncover critical vulnerabilities or Broken Access Control.
Qualysec’s API security testing helps you minimize the risk of API-based vulnerabilities and meet regulatory compliance requirements. Contact now to learn more!
.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQs
1. What is the timeline for API Security testing?
The typical time span for an API security test is 5-7 days after onboarding. This period refers to the actual testing and reporting phase but might vary a bit depending on the scope of the test.
2. How much does API security testing cost?
API security testing costs anywhere between $349 and $1499 per scan or has different packages depending on the scope, number of assets, or number of scans required. Check out Qualysec’s pricing.
3. Why choose Qualysec for Security Testing?
Features including 1250+ tests, adherence to the global security standard, an intuitive dashboard with the dynamic visualization of vulnerabilities and its severity, remediation assistance together with a simultaneous security audit and multiple rescans give Qualysec an edge above all competitors.






























































































































































































































































































































































































































































































































0 Comments