As businesses expand online, ensuring the security of web applications has become more crucial than ever. If you’ve wondered how to prevent cyber threats from infiltrating your systems, you’ve probably come across the term penetration testing. But what is it, really, and how do you carry it out effectively on web applications? Let’s walk through the essentials of web app penetration testing in a straightforward way.
What is Penetration Testing?
Think of penetration testing, or “pen testing,” as a friendly hacker trying to break into your system before the bad guys do. This method of ethical hacking identifies weak spots that real attackers might exploit. Imagine you’re the owner of a castle. You might have thick walls, a moat, and guards at the gate, but what if there’s a hidden tunnel you didn’t know about? A pen test is like hiring someone to find that tunnel before invaders do.
As more people rely on web applications for sensitive transactions (think online shopping, banking, and personal data), protecting them is non-negotiable. Data breaches can damage reputations, violate customer trust, and even lead to hefty fines if you’re found to be
non-compliant with industry regulations. With a solid web application security testing strategy, you can significantly reduce these risks.
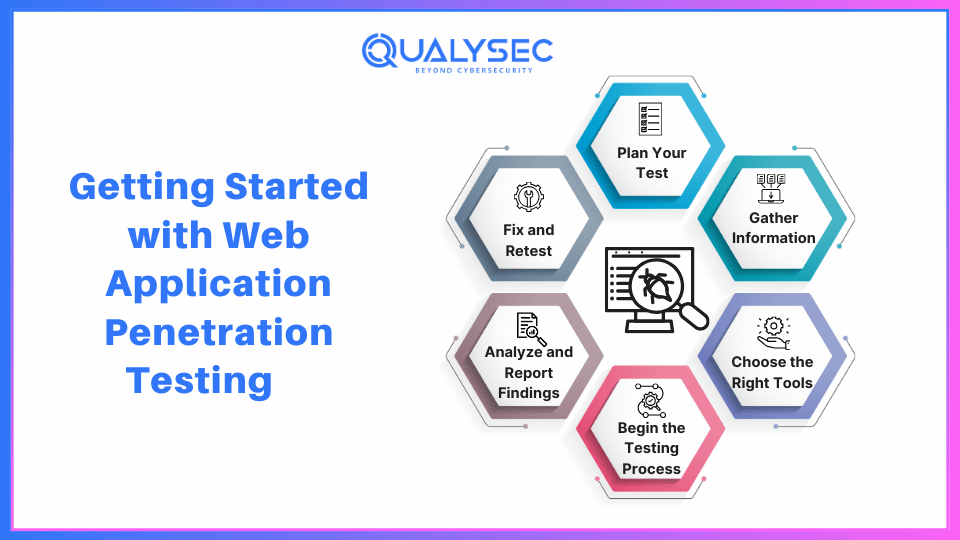
Getting Started with Web Application Penetration Testing
Step 1: Plan Your Test
The first step is to lay out a game plan. Before diving into testing, ask yourself these questions:
- What parts of my application will be tested? Maybe you have multiple modules, APIs, or mobile extensions, and you need to decide if all or just specific components will be tested.
- Who’s involved? Will this be an internal test, or are you hiring an external team? If it’s external, you’ll need to provide access without compromising any sensitive data.
- What are my goals? Are you looking to comply with a regulation, or are you aiming for a general security assessment?
By clarifying these aspects, you’ll make the pen testing process smoother, ensuring your team (or testers) understands exactly what’s needed.
Step 2: Do Your Homework – Gather Information
Now that you’ve set your scope, it’s time to dig deeper into your application. This phase, often called reconnaissance, involves gathering as much information as possible about your web app. This could include details about the app’s architecture, the coding languages used, third-party integrations, and server configurations.
Step 3: Choose the Right Tools
Once you’ve gathered information, it’s time to think about tools. Should you go with automated web application penetration testing tools, or do it manually? Ideally, a combination works best. Automated tools can efficiently identify common issues, while manual testing provides a more thorough, hands-on analysis.
Here are a few popular tools used in the field:
- OWASP ZAP: Known as the “Zed Attack Proxy,” this tool is excellent for beginners and offers easy-to-understand reports.
- Burp Suite: More advanced than OWASP ZAP, Burp Suite is widely used by professionals for its extensive scanning capabilities.
- Nikto: If you want a tool focused on finding outdated software, Nikto is a good choice. It’s less advanced than others but does the job if your focus is on version-based vulnerabilities.
Read Also: Top 5 Software Security Testing Tools that your organization needs
Step 4: Begin the Testing Process
Let’s get into the actual testing. Depending on your web app and goals, you might consider these types of testing:
- Black-Box Testing: Imagine an outsider trying to break into your application without any prior knowledge. This type of testing is useful for mimicking real-world attacks from anonymous users.
- White-Box Testing: Unlike black-box, here you provide the tester with full access, including source code. White-box testing allows a more in-depth review and is helpful when you want to cover every potential weak point.
- Gray-Box Testing: This approach is a blend of both, giving testers limited access while still simulating a somewhat external threat. It’s ideal when you want a realistic scenario while still revealing vulnerabilities deep within your system.
Step 5: Analyze and Report Findings
After testing, it’s time to make sense of the results. This stage is crucial because raw data on vulnerabilities doesn’t mean much without proper context. Categorize your findings based on severity—some issues might need immediate action, while others can be addressed later.
Great report should:
- Prioritize vulnerabilities: Rank issues based on their potential impact and the likelihood of exploitation.
- Offer clear recommendations: Don’t just say “fix this”; provide actionable steps for remediation.
- Be easy to understand: Keep the technical jargon to a minimum, especially if non-technical stakeholders are reviewing the report.
Step 6: Fix and Retest
Testing alone isn’t enough. After identifying issues, the next step is remediation. This could mean applying patches, rewriting code, or improving access controls. Once these fixes are in place, retesting ensures that the vulnerabilities are fully resolved.
Latest Penetration Testing Report

Common Mistakes to Avoid in Web Application Penetration Testing
Penetration testing on web application sounds straightforward, but a few common pitfalls can lead to ineffective results:
- Skipping the Planning Phase: Diving into testing without defining the scope can lead to wasted time and missed vulnerabilities.
- Relying Solely on Automated Tools: Automation is helpful, but it can’t catch every vulnerability. Combine automated tools with manual testing for thorough coverage.
- Not Retesting: Fixes need validation. If you skip the retesting phase, there’s no way to ensure vulnerabilities are truly resolved.
- Failing to Update Testing Tools: Cyber threats evolve, and so do the tools that counter them. Make sure your tools are up-to-date to detect the latest vulnerabilities.
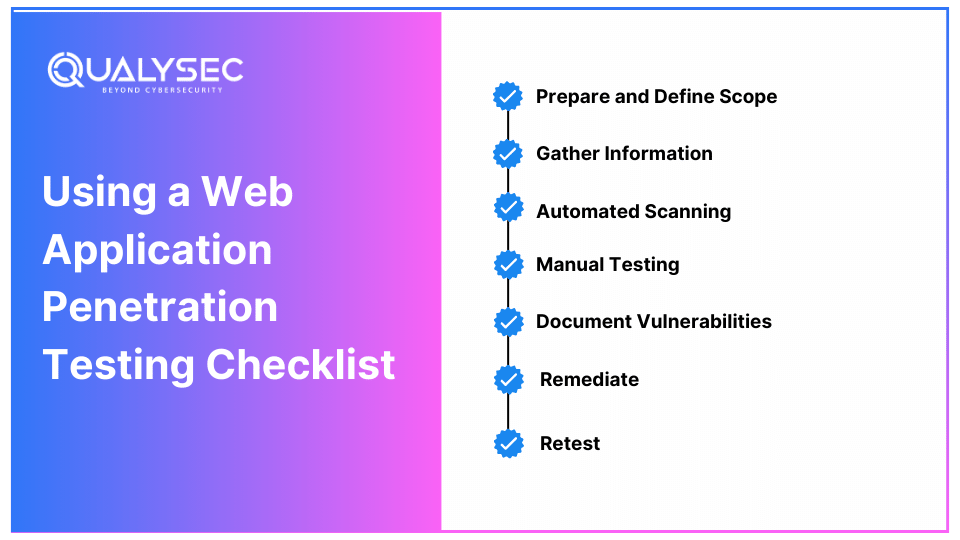
Using a Web Application Penetration Testing Checklist
Creating a checklist for penetration testing on web applications is one of the best ways to stay organized and ensure thorough testing. Here’s a sample:
- Prepare and Define Scope: Ensure everyone’s clear on what will be tested.
- Gather Information: Understand the application architecture.
- Automated Scanning: Run initial tests to identify basic vulnerabilities.
- Manual Testing: Dive deeper into complex issues.
- Document Vulnerabilities: Keep a record of all findings.
- Remediate: Apply fixes as needed.
- Retest: Confirm that issues are fully resolved.
This checklist can guide you through the process systematically, so you don’t overlook any critical steps.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
The Bottom Line: Security is a Continuous Journey
Penetration testing on web applications isn’t a one-and-done task. As long as cyber threats exist, ongoing testing is essential. Security is a continuous journey, not a destination. With the right approach, consistent efforts, and the help of automated tools and manual testing, your applications can remain secure and resilient.
protecting your digital assets, regular web application security testing is key to maintaining a strong defense. Remember, it’s always better to find and fix vulnerabilities before the hackers do.
So, whether you’re a developer, a security professional, or simply someone interested in protecting your digital assets, regular web application security testing is key to maintaining a strong defense. Remember, it’s always better to find and fix vulnerabilities before the hackers do.























![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments