Mobile application security audit reveals if the apps are vulnerable to any security threats. It is an essential part of a secure application development life cycle that identifies the areas that require security investments. There are over 6 million apps combined in the Apple Store and Google Play Store and research says that over 76% of these apps have at least one security vulnerability.
The frequency of cyberattacks is increasing, along with their cost. Despite this, many app companies still do not value cybersecurity as it should be. This blog discusses the importance of mobile app security audits and what are the best practices for mobile app security.
Why Mobile Application Security Audit is Crucial?
A mobile application security audit helps identify flaws that a hacker may use to breach the app’s security. It is essential to ensure the safety of the apps users use daily. These audits help detect and fix mobile security vulnerabilities that can be exploited to steal sensitive info, such as personal data, financial details, and login credentials.
Every day thousands of apps are installed that handle our data. Regular security audits ensure that new threats are effectively addressed in the apps. In short, mobile application security audits keep both users and developers safe from potential security risks.
By conducting regular security audits, developers can protect their mobile apps from evolving cyber threats, maintain user trust, and comply with industry standards. With an average of 2,200 cyberattacks happening every day, securing your applications is now more important than ever.


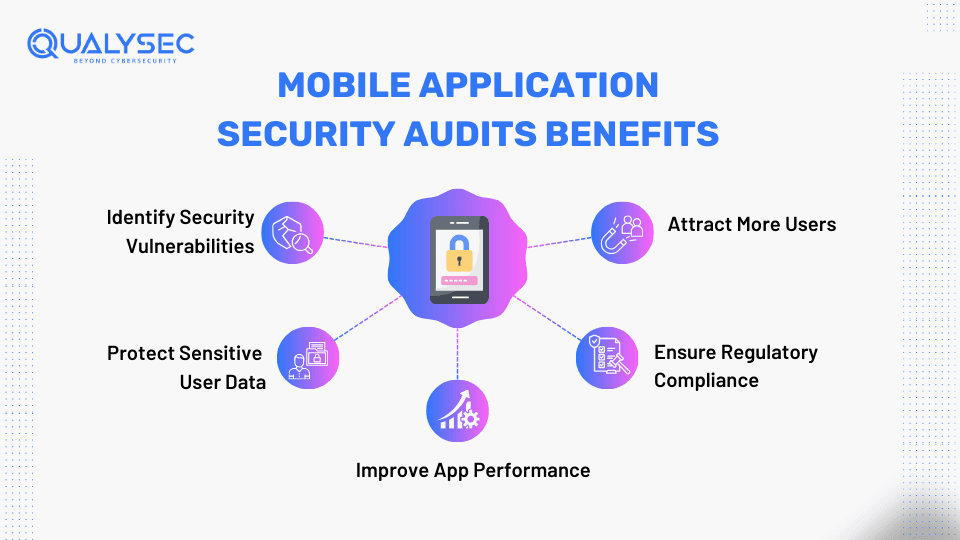
Key Benefits of Mobile Application Security Audits
While some organizations may see security audits as a costly and time-consuming task, the trust is that they can help you save a lot of money and headaches in the long run. By identifying and addressing security issues early on, you can avoid costly damages from data breaches and other cyberattacks.
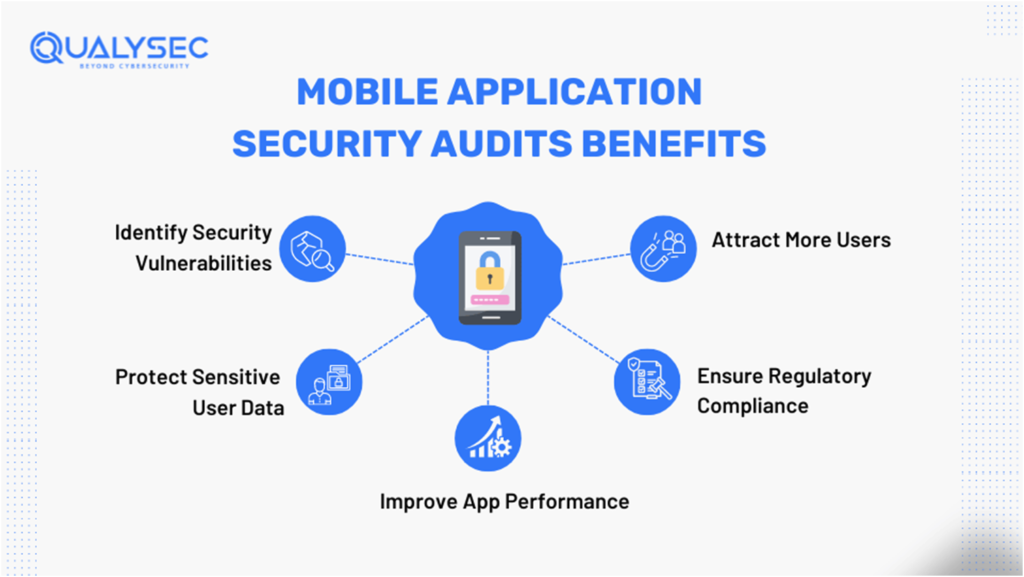
1. Identify Security Vulnerabilities
Mobile app security audits help identify potential vulnerabilities that hackers could exploit for unauthorized access. Through a mobile app security assessment, they can uncover weak points in the app’s code, architecture, and design. By uncovering these weaknesses early, developers can implement necessary security fixes to ensure the app remains secure and less prone to cyberattacks.
2. Protect Sensitive User Data
A single data breach incident can be a huge setback for your business. Security audits ensure that sensitive user data, such as personal information and financial details, are well-protected. This reduces the risk of data breaches and enhances user confidence in the app’s security measures.
3. Improve App Performance
Nobody likes a slow app or features that don’t work properly. Audits can reveal security issues that impact the app’s performance. Addressing these issues not only enhances security but also improves the app’s speed, reliability, and overall user experience.
4. Ensure Regulatory Compliance
Many industries have rules in place to protect user data online, such as PCI DSS, HIPAA, GDPR, ISO 27001, etc. Regular security audits help ensure that the app complies with these industry regulations and standards. This is crucial if you want to avoid legal issues and fines and maintain the app’s reputation in the market.
Explore more : https://qualysec.com/compliance/
5. Attract More Users
Users are more likely to use those apps that are secure and perform like a breeze. Regular mobile app security audits show that the company is serious about user safety, which helps in maintaining and building user trust. As a result, users will continue using the app and also recommend the app to their friends.
Mobile App Security is Especially Recommended for:
- Banking and Payment Apps: Uses that trust you with their financial details should be assured that they are properly secured.
- Instant Messengers: If it is possible to communicate with others through your app, the data should be encrypted and protected from breaches.
- E-commerce Apps: These apps are more likely to face price manipulation, coupon code modification, customer data leakage, and payment gateway bypass.
So, do you need a mobile application security audit? Qualysec Technologies provides comprehensive security testing services with a process-based approach. We have secured over 450 applications for more than 110 clients. Tap the link below and talk to our cybersecurity expert now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Components of a Comprehensive Mobile Application Security Audit
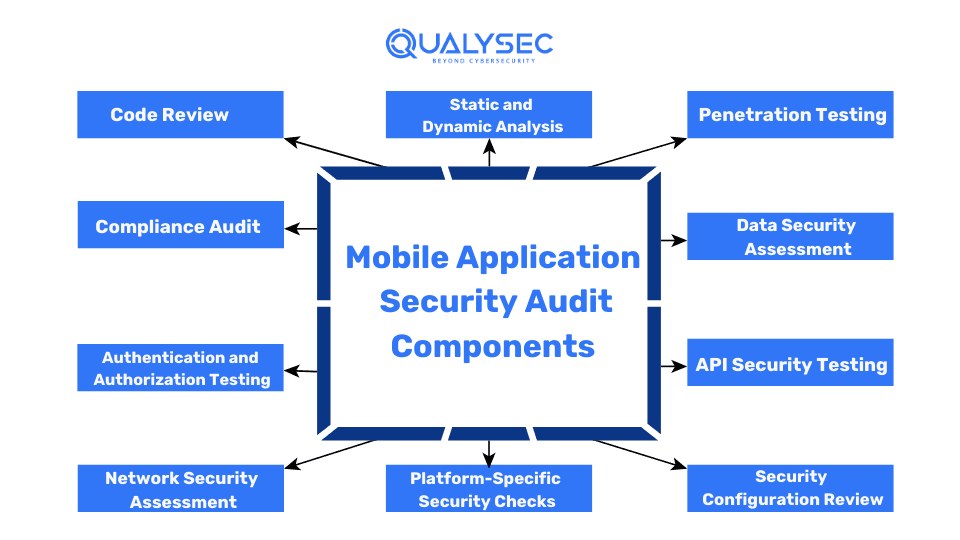
Most mobile security audit vendors claim to offer comprehensive services, but in reality, they just scan the app using a tool. So, to avail of proper mobile app security, you need to know its various components.
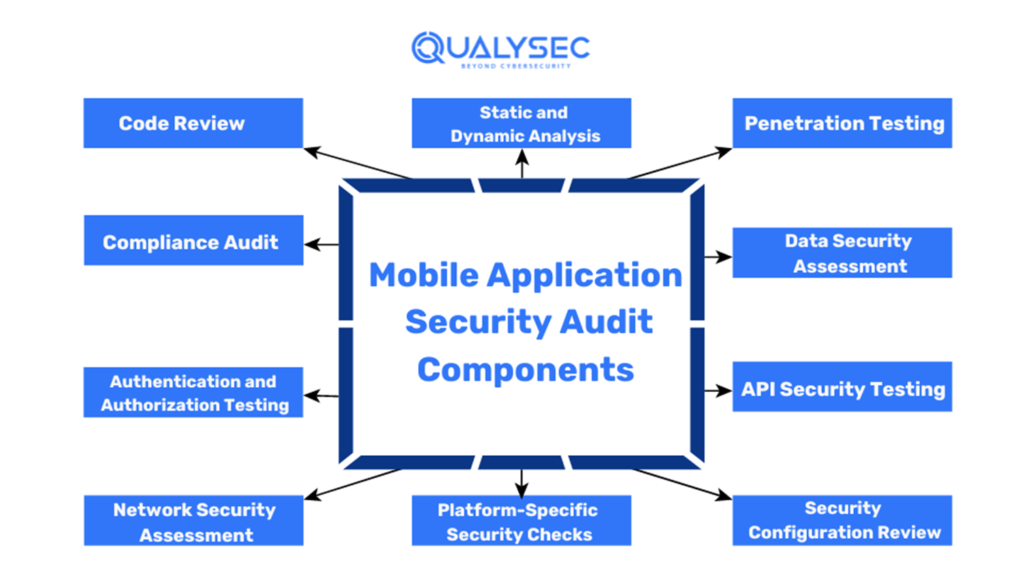
1. Code Review
A thorough examination of the app’s source code is conducted to identify any security flaws. It helps detect issues like insecure data storage, hardcoded credentials, code injections, etc. By reviewing the source code, developers can fix the problems early and build a secure app.
2. Static and Dynamic Analysis
Static analysis tools are used to examine the app’s code without running it. Dynamic analysis tools are used to test the app in a live environment. This dual-testing approach helps detect various security issues, such as code errors and runtime vulnerabilities, providing comprehensive app security.
3. Penetration Testing
This is a security testing process where testers perform simulated attacks on the app to find security weak points. This is a hands-on approach that helps developers see how the app behaves during an attack and reveal vulnerabilities that need fixing. Mobile app penetration testing provides practical insights to improve the app’s defense against real-world cyber threats.
4. Compliance Audit
One of the main reasons why companies do security audits is to comply with industry regulations of data protection. Based on the industry and region the app belongs to, it needs to comply with standards like HIPAA, PCI DSS, GDPR, ISO 27001, etc. This ensures the user data in the app is collected, stored, and processed securely. Additionally, it helps organizations avoid legal fines and penalties.
5. Data Security Assessment
This evaluates how the app handles sensitive user data and ensures it is protected both while at rest and in transit. This process involves checking encryption mechanisms and data storage practices. Proper data security protocols help prevent unauthorized access and data breaches.
6. Authentication and Authorization Testing
Check the app’s security measures for verifying user identities and access controls to resources. This includes checking strong password policies, multi-factor authentication (MFA), and secure session management. Robust authentication and authorization protect the app from unauthorized access.
7. API Security Testing
This checks the security of APIs that are integrated with the mobile app. It ensures that these APIs are protected against common threats like injection attacks and lack of authentication. APIs are the backbone for the app and its security is crucial for the app’s functionality.
8. Network Security Assessment
This assessment analyses the security of the app’s network communications. It ensures that the data is transmitted securely using HTTPS protocols and certification validation is properly implemented. Protecting network communications helps in preventing man-in-the-middle (MITM) attacks and data breaches.
9. Platform-Specific Security Checks
This is done to ensure that the app follows security best practices specific to the mobile device platform, i.e. Android or iOS. Each platform has specific security policies, and this process ensures that the app adheres to these guidelines. As a result, it helps address unique platform-specific vulnerabilities.
10. Security Configuration Review
This involves reviewing the app’s security configuration settings. This includes data storage settings, varying permissions, and other configurations that impact app security. robust configuration helps prevent security misconfigurations and data loss.
If you want to see a real mobile app security audit report, click on the link below and download one right now!
Latest Penetration Testing Report

Best Practices for Mobile Application Security in 2024
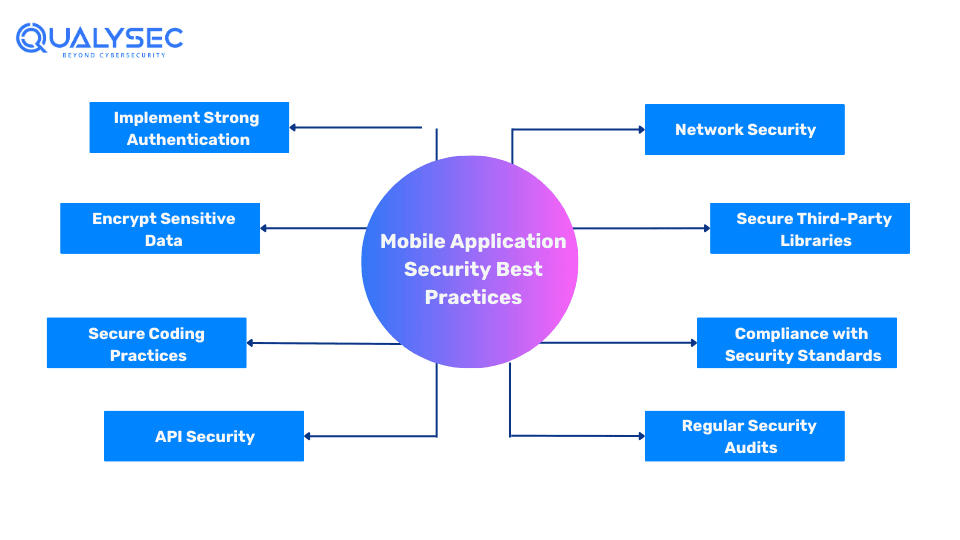
With cyberattacks increasing at an unprecedented rate, companies should take the required steps to secure their valuable apps. Here’s an expanded look at the best practices for mobile app security in 2024:
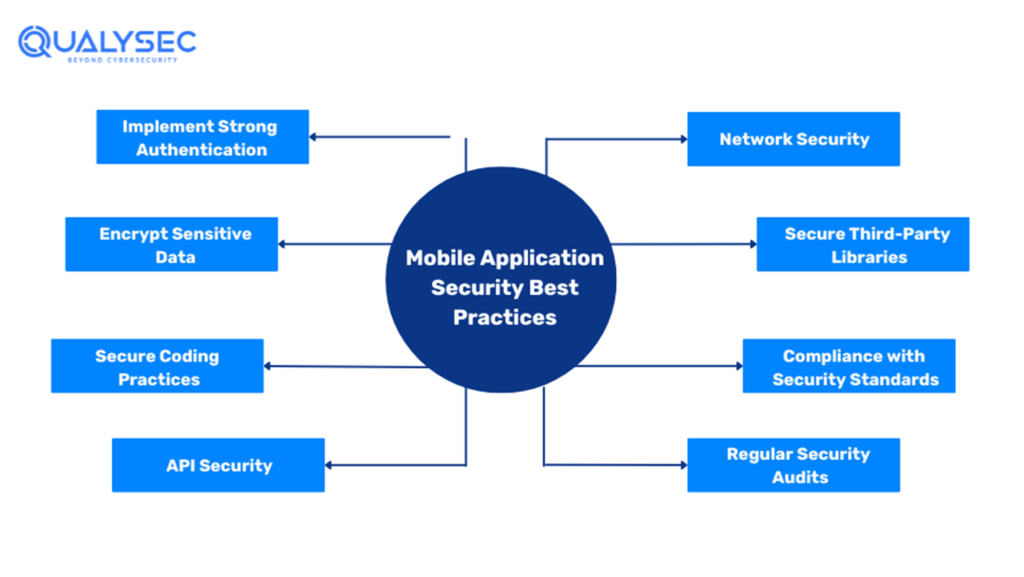
- Implement Strong Authentication: Use multi-factor authentication (MFA) to secure user access. MFA requires users to verify their identity before they access any app resources using multiple methods, such as passwords and authentication apps.
- Encrypt Sensitive Data: Protect user information by encrypting it both in transit and at rest. Use strong encryption measures like AES-256 for stored data and TLS for data transmitted over networks to prevent unauthorized access.
- Secure Coding Practices: Educate developers to write secure code and conduct code reviews to identify and fix security issues early in the development cycle.
- API Security: Ensure all APIs integrated into the app are secure by using strong authentication, authorization, and encryption methods. Regularly review and update APIs to prevent unauthorized access.
- Network Security: Ensure the app communicates with the servers securely by using protocols like HTTPS. Implement certificate pinning to prevent man-in-the-middle attacks.
- Secure Third-Party Libraries: Regularly review and update third-party libraries and SDKs used in the app. Ensure they are sourced from reputable providers and do not bring any vulnerabilities.
- Compliance with Security Standards: Ensure the app complies with the required security standards and frameworks such as HIPA, PCI DSS, and OWASP Mobile Security Project. Regularly review and update security practices according to industry best practices.
- Regular Security Audits: Conduct security audits and penetration tests regularly (at least once a year) to identify and fix security vulnerabilities. Regular testing helps protect the app from new threats.
Conclusion
The global average of data breaches in 2023 was $4.45 million. Just think about the consequences if your business faces a data breach. If it scares you, it is better to conduct a mobile application security audit for your most valuable product. It will help you identify and fix vulnerabilities, protect sensitive data, and ensure compliance with industry standards using mobile app security tools.
Additionally, you need to know that a security audit is not a one-time thing. Since cyber threats are continuously changing, the best way is to conduct them regularly. Just remember, investing a small amount in prevention is better than spending a huge amount recovering from a cyberattack.
FAQ
Q: What is a mobile app security audit?
A: A mobile app security audit is a security practice that evaluates the app’s security measures and identifies weak points that need fixing. Additionally, it helps secure user data and complies with industry standards.
Q: Why is a mobile app security audit important?
A: A mobile app security audit is important to prevent unauthorized access, data breaches, and other security incidents on the app.
Q: Why mobile application security is important?
A: Since most mobile applications store and transfer user data, and also handle financial transactions, its security should be a top priority.
Q: What is mobile audit in cyber security?
A: Mobile audit in cyber security checks the strength of security measures in mobile apps, such as encryption mechanisms, authentication & authorization measures, API security, network security, and coding practices.






























































































































































































































































































































































































































































































































0 Comments