As a business, you are using networks and devices extensively. But are you aware of the potential risks associated with it? In fact, the cost of cybercrimes is expected to grow by $10.5 trillion annually by 2025, with networks being the prime target. As alarming as it is, it is also a reminder to secure your networks before you become a victim.
Fortunately, you can secure your networks and associated devices from security risks by conducting external network penetration testing. Penetration testing is where cybersecurity experts breach your systems with your permission to find vulnerabilities in their security.
In this blog, we will explain what external network penetration testing is, its benefits, and how it is carried out. Read the entire blog if you want every detail on protecting your networks.
What is External Network Penetration Testing Exactly?
In external network penetration testing, cybersecurity professionals (often referred to as ethical hackers) attempt to penetrate the organization’s network from the outside. They use a variety of tools and techniques to identify vulnerabilities in the network configuration, software, or user authentication mechanisms.
The main goal of external network penetration testing is to uncover potential security flaws before they can be exploited by cybercriminals. By identifying vulnerabilities, organizations can take proactive measures to strengthen their defenses and mitigate the risk of unauthorized access or data breaches.
It is particularly important for organizations that have public-facing servers, for example, web servers or email servers to prioritize penetration testing. This is because, it is an important process that enhances the cybersecurity posture, protects sensitive information, and maintains the trust of customers and stakeholders.

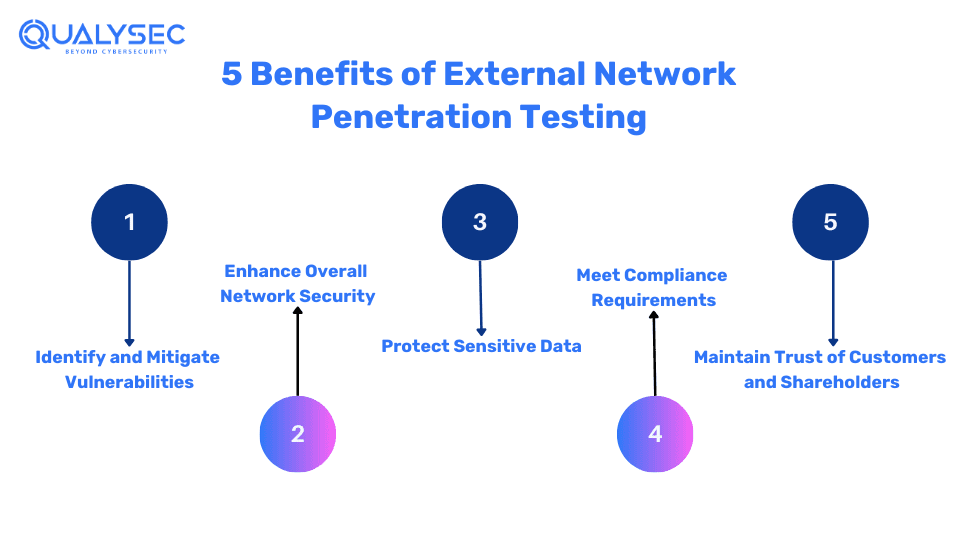
Benefits of External Network Penetration Testing
Now that you know what external penetration testing is, let’s discuss why organizations should not ignore it in these conditions. Here are the benefits of conducting regular external network penetration testing:
1. Identify and Mitigate Vulnerabilities
In a nutshell, external network penetration testing finds the vulnerabilities present in external-facing systems such as websites, servers, and network infrastructure systems, along with their impact severity. You can use these insights to mitigate these vulnerabilities before they are exploited by cybercriminals for unauthorized access and data breaches.
2. Enhance Overall Network Security
By finding and mitigating potential vulnerabilities, you can implement targeted security measures to enhance your network defenses. These defenses may include patching software, reconfiguring network settings, or strengthening access controls. As a result, you can reduce the likelihood of cyberattacks significantly.
3. Protect Sensitive Data
Data is gold for IT organizations and needs the best security. Penetration testing helps in securing sensitive information, such as customer data and intellectual property, from falling into the wrong hands. By detecting and addressing potential entry points for attackers, you can maintain the confidentiality of your data assets.
4. Meet Compliance Requirements
Many industries have regulatory requirements that mandate regular security assessments (including penetration testing) to protect customer info. By conducting external network penetration tests, organizations can fulfill their compliance requirements, and thus avoid legal penalties and huge fines.
5. Maintain Trust of Customers and Shareholders
Once a trust is broken, it is very difficult to get back. This is not a philosophy, but what happens with every organization. Even a small cyber attack on your network can hamper the trust that you have built among your customers and shareholders. By conducting pen tests, you can show your commitment to security and assure your customers that their information is safe with you. Showing the world your testing certificate not only maintains the trust but also helps you acquire new customers.
Do you also want to secure your network from cyber threats? Choose Qualysec for the best network penetration testing and have peace of mind. We follow a hybrid process-based pentest approach that will strengthen your overall network security. Don’t wait, click below to contact us now!
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
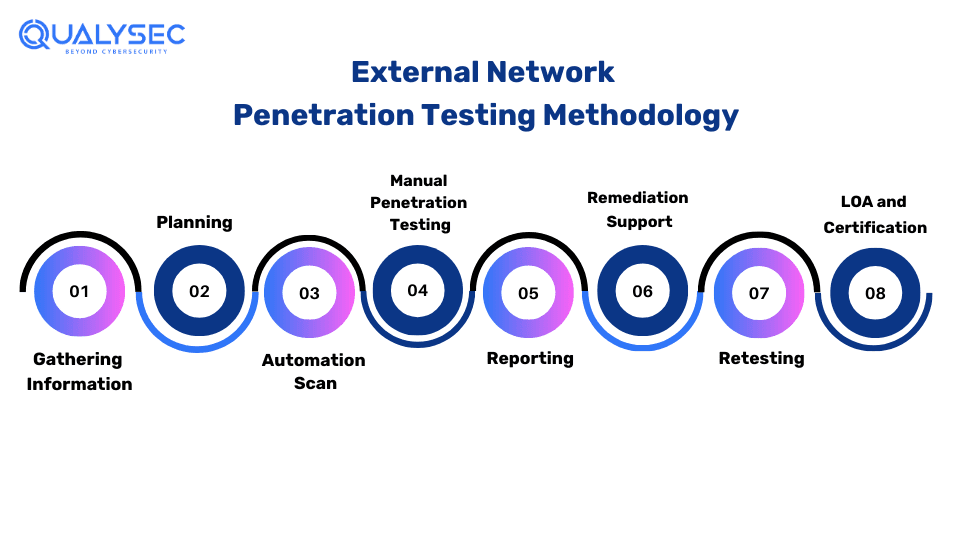
External Network Penetration Testing Methodology
Though different cybersecurity firms may take different approaches, the majority follow a similar approach. Here is the basic external network penetration testing process:
1. Information Gathering
In the 1st step, the penetration testers gather as much information about the network as possible. For example, IP addresses, domain names, and network architecture. Either they get information from the client or publicly available web pages.
2. Planning
In the 2nd step, the testers determine the scope of the test, including which systems and networks will be assessed. They make it clear to you which attacks they are about to conduct on your network and which vulnerabilities they will try to exploit. Additionally, they will explain the tools and techniques they are going to use.
3. Automated Vulnerability Scanning
Here, the pen testers use automated scanners to find vulnerabilities present at the network’s surface level. This is a quick process to find vulnerabilities. However, since automated scanners use a specific script to operate, it might generate false positives. This means it may miss many vulnerabilities that can be exploited by hackers.
4. Manual Penetration Testing
This is where proper vulnerability testing happens. Ethical hackers or pen testers use manual techniques to penetrate your network infrastructure. They check where the weaknesses lie and what is the severity of their impact. Since it is conducted by human specialists, the accuracy is as high as possible.
5. Reporting
After all the scanning and testing are completed, the penetration testing company then documents the entire process and findings. The report will include all the vulnerabilities identified, their impact level, and their remediation methods.
Ever seen a real external network penetration testing report? If not, then here’s your chance. Click on the link below and download one now!
Latest Penetration Testing Report

6. Remediation
The penetration testing report will include the remediation methods to fix the vulnerabilities detected. Additionally, if your development team needs any kind of assistance while fixing them, the cybersecurity firm may help them online or over consultation calls.
7. Retest
This is something most organizations look for while selecting a penetration testing company. after the development team has made the necessary patches, the pretesting company retests the network structure to check whether the remediation worked or not. This is an important step to confirm that your network is now secure.
8. LOA and Security Certificate
Finally, the penetration testing company gives a letter of attestation (LOA) and a security certificate to the organization. This certificate proves that you have successfully conducted external network penetration testing and helps you with your security and compliance needs.
Difference Between Internal and External Network Penetration Testing
Simply put, internal network penetration testing is done by the organization’s in-house security team to detect vulnerabilities in internal network security, like routers. On the other hand, external network penetration testing is done by a third-party cybersecurity company to identify vulnerabilities in public-facing network systems, like servers.
| Aspect | Internal Network Penetration Testing | External Network Penetration Testing |
| Scope | Assess security within the organization’s internal network and systems. | Assess security from outside the organization’s network perimeter. |
| Focus | Identify vulnerabilities in internal network systems, applications, and user accounts. | Identify vulnerabilities in external-facing systems, such as servers and network devices. |
| Perspective | Mimics attacks that are done from within the organization’s network by an insider threat, like employees. | Mimics attacks that are done from outside the organizations by cyber attackers or hackers. |
| Goal | To check the effectiveness of internal security measures and controls. | To check the resilience of public-facing network systems against external threats and attacks. |
| Timeframe | Quick, as it is conducted by the in-house team | Takes time, as it is conducted by an external penetration testing firm. |
| Cost | Expensive, as maintaining an in-house team costs more. | Less expensive, as you have to appoint an external team every once in a while. |
Conclusion
Once your network is hacked, all your other digital assets will also be at risk. This is the reason why you must prioritize network security. External network penetration testing is a foolproof practice that will help you identify the vulnerabilities present in your network architecture so that cyberattacks don’t happen.
Additionally, choosing the right penetration testing provider is also equally important. You need to confirm that the firm provides both automated and manual penetration testing for broad and accurate results. Also, you must check whether they are offering a retesting option as a part of their process. This is because it will confirm that all the vulnerabilities are fixed.
Do not take network security lightly, keep yourself updated on evolving cyber threats and perform regular penetration tests for comprehensive cybersecurity!
FAQs
Q: What is the methodology of external pentest?
A: The external pentest methodology includes:
-
- Information Gathering
- Planning
- Automated Vulnerability Scanning
- Manual Penetration Testing
- Reporting
- Remediation
- Retest
- LOA and Security Certificate
Q: Why is external network penetration testing important?
A: Conducting external network penetration testing helps organizations prevent breaches in the network infrastructure. Additionally, it also prevents data breaches, service disruptions, and regulatory penalties.
Q: What are the types of external penetration testing?
A: Common types of external penetration testing that organizations opt for are:
-
- External network penetration testing
- External web application penetration testing
- External mobile application penetration testing
- External API penetration testing
- External cloud penetration testing






















![Top 20 Network Security Companies in USA [2025 Updated List]](https://qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)































































































































































































































































































































































































































































































0 Comments