Web application penetration testing is a critical part of any organization’s security program. With the rise of cyber threats, it is essential to ensure that your web application is secure and protected against any malicious attacks. In this blog, we will provide a complete guide on web application penetration testing, including why it is performed, what tools are used, the different types of web app penetration testing, and whether you should consider automated or manual testing.
Why is Web Application Penetration Testing Performed?
Web application penetration testing is performed for several reasons, including:
- To identify vulnerabilities in the web application before attackers do.
- To assess the effectiveness of the security controls in place.
- Therefore, to ensure compliance with industry standards and regulations.
- To gain a better understanding of the web application’s security posture.
- To improve the overall security of the web application.
What is the process of penetration testing for web applications?
A vulnerability scanner is typically used during penetration testing for online applications to look for and locate security flaws including misconfiguration, unpatched software, SQL injection, cross-site scripting, etc.
After that, manual pen-testers access your system to a) verify the veracity of the vulnerabilities discovered by the scanner and do further analysis.
Search for more complex flaws, such as payment gateway and business logic issues.
Once testing and exploitation are complete, the pen-testers create a pentest report that includes information on all the tests carried out, vulnerabilities discovered, data on their severity, and potential fixes. You may either hire a security team from within your organization or hunt for web application penetration testing services.
Tools Used in Performing Web Application Penetration Testing
Several tools are used in performing web application penetration testing, including:

- Burp Suite – a web application testing toolkit that includes several tools for testing different aspects of a web application.
- OWASP ZAP – an open-source web application security testing tool that can identify vulnerabilities in a web application.
- Nessus – a vulnerability scanner that can identify vulnerabilities in a web application and its underlying infrastructure.
- Nmap – a network scanner that can be used to identify open ports and services running on a web server.
- Metasploit – a penetration testing framework that can be used to exploit vulnerabilities in a web application.
Should You Consider Automated or Manual Pen Testing?
Whether to consider automated or manual penetration testing depends on the goals of the testing and the resources available.
Automated penetration testing
- Can be faster and more efficient than manual testing.
- Can detect known vulnerabilities and common misconfigurations.
- Could be easily repeated and automated.
- Can cover a wide range of vulnerabilities.
However, automated testing may not always detect new or unknown vulnerabilities and can sometimes generate false positives.
Manual penetration testing
- Can detect new or unknown vulnerabilities.
- Can provide a deeper analysis and understanding of the application’s security.
- Can identify application logic errors and business logic flaws.
- Can simulate real-world attacks more accurately.
However, manual testing can be time-consuming and expensive and requires highly skilled and experienced testers.
Qualysec is the best in pen-testing
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform that includes static and dynamic code analysis tools, vulnerability scanners, penetration testing tools, and more
- Vetted scans ensure zero false positives
- Our platform provides a centralized solution for discovering, handling, and rectifying vulnerabilities.
- Therefore, at Qualysec, we provide a wide range of security testing services to meet your needs. With our expert team of testers, we guarantee 100% reliable services that help you ensure the security of your application.
Top Notch Services provided by Qualysec:
Our services are specifically designed to help your organization comply with various cybersecurity standards, such as:
- PCI-DSS (Payment Card Industry Data Security Standard)
- GDPR (General Data Protection Regulation)
- HIPAA (Health Insurance Portability and Accountability Act)
- ISO/IEC 27001 (Information Security Management)
- SOC 2 Type I & Type II (Service Organization Control)
Why Choose Qualysec?
Qualysec is a penetration testing company that is transforming the cyber security testing industry with a Process-based approach and prevention-based cyber security techniques. Qualysec’s penetration testing service is a preferred choice among global enterprises for testing their web and mobile applications, IoT devices, Blockchain, and cloud infrastructure to ensure security.
Among the many key features that set Qualysec apart from other web application penetration testing is its approach to VAPT.
Qualysec follows a comprehensive methodology that involves a combination of manual and automated testing techniques to ensure maximum coverage of vulnerabilities. They also provide detailed reports that include a prioritized list of vulnerabilities, along with recommendations for remediation.
They work closely with organizations to understand their unique needs.
Qualysec offers various services which include:
- Web App Pentesting
- Mobile App Pentesting
- API Pentesting
- Cloud Security Pentesting
- IoT Device Pentesting
- AI /ML Pen-testing
The solutions offered by Qualysec are particularly beneficial for businesses that must adhere to industry rules or prove their dedication to security to clients and partners. So, by opting for Qualysec as a web application penetration testing service provider, businesses can ensure the safety of their web applications.
Hence, choose Qualysec for comprehensive and effective penetration testing services. Therefore the cost of penetration testing guide will help you make informed decisions and understand the various factors that impact the cost. Hence, protect your assets and enhance your security posture by choosing us.
Methodologies Used For Penetration Testing
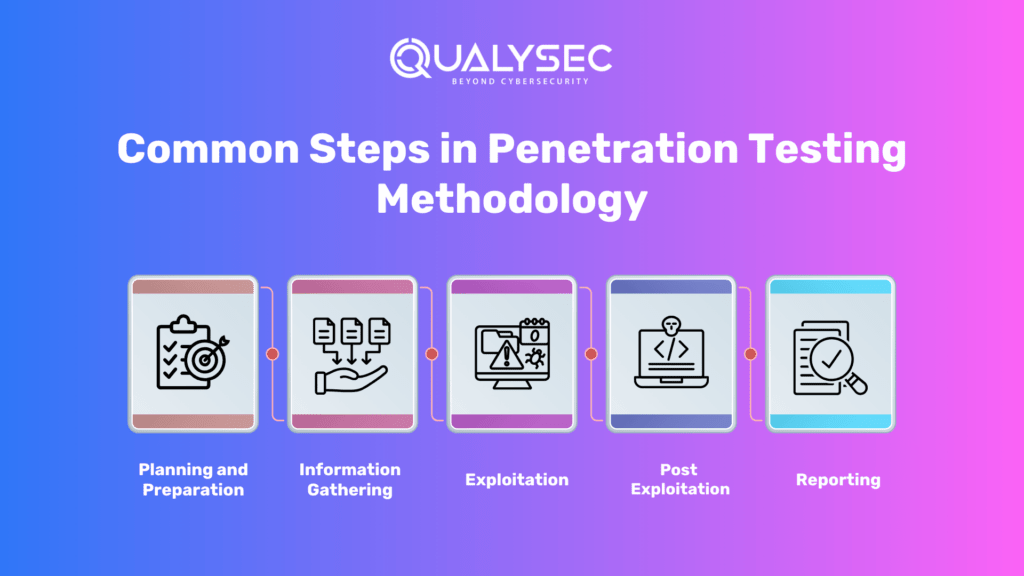
What are the different types of Web App Penetration testing?
- Network Penetration Testing
Network penetration testing is performed to identify vulnerabilities in the network infrastructure of a web application. Therefore, this type of testing aims to find vulnerabilities that could be exploited by attackers to gain unauthorized access to the network.
- Application Penetration Testing
Application penetration testing focuses on identifying vulnerabilities in the web application itself. This type of testing can uncover vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication bypass.
- Mobile Application Penetration Testing
This type of testing is performed on mobile applications to identify vulnerabilities, therefore that could be exploited by attackers to gain unauthorized access to the mobile device or data.
- API Penetration Testing
API penetration testing involves testing the APIs used by the web application to exchange data with other systems. Hence, the goal is to identify vulnerabilities in the APIs that could be exploited by attackers to gain unauthorized access to the application or data.
- Cloud Penetration Testing:
This type of testing is performed on web applications deployed on cloud platforms. Hence, the goal is to identify vulnerabilities that could be exploited by attackers to gain unauthorized access to the cloud infrastructure or data.
Conclusion
It is a critical part of any organization’s security program. It helps organizations identify vulnerabilities in their web applications before attackers do. By following the complete guide on web application penetration testing, organizations can ensure that their web applications are secure and protected against any malicious attacks. Hence, by understanding the different types of testing and the tools available, organizations can choose the appropriate method for their needs.
It is always best to perform a comprehensive vulnerability assessment and penetration testing (VAPT) for your web application before or after pushing it into production in order to identify the direct threats to your website/web application and ultimately to your business. Additionally, doing the VAPT scans for your web application on regular basis is a best practice to protect it from emerging cyber threats and possible zero-day exploits and attacks.
Wishing to know more, talk to our Experts and fill out your requirements.
Frequently Asked Questions
Q: What is web application penetration testing?
A: It is a process of testing web applications to identify security vulnerabilities that could be exploited by attackers.
Q: Why is web application penetration testing important?
A: It is important because web applications often contain sensitive data, and any vulnerabilities in the application can lead to data breaches or other security incidents.
Q: What are some common vulnerabilities found in web applications?
A: Therefore, the common vulnerabilities found in web applications include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), authentication and authorization issues, and insecure direct object references.
Q: What are the steps involved in web application penetration testing?
A: The steps involved in web application penetration testing include reconnaissance, scanning, enumeration, vulnerability assessment, exploitation, and reporting.
Q: Who should perform web application penetration testing?
A: It should be performed by experienced security professionals who have the necessary skills and knowledge to identify and exploit vulnerabilities in web applications.
































































































































































































































































































































































































































































































































1 Comments